Email Security powered by AI

Better than AI alone
Vade’s email security suite of products combine artificial intelligence with adaptive algorithms that incorporate real-time human feedback for an unbeatable layer of cybersecurity protection. Vade’s AI engine analyzes email and webpages to detect known and unknown phishing, BEC/spear-phishing, malware, ransomware, and other cyberattacks before they reach your users.
More than that, Vade’s technology incorporates user feedback to improve the AI engine, allowing us to adapt to zero-day exploits and emerging threats faster than any other email security suite on the market.
mailboxes protected worldwide
emails analyzed per day
items blocked by Computer Vision per day
algorithms updated per minute
Integrated email security for Microsoft 365
Cybercriminals are targeting users of the world’s most popular email and collaboration suite. Vade’s integrated email security solution for Microsoft 365 catches the advanced threats that bypass Microsoft and unburdens your IT team from cybersecurity complexity.

Email security you don’t have to think about
Vade’s integrated email security suite requires no MX record changes, no prolonged changeovers, and no need to disrupt user workflows. Email security is just the start – Vade’s expanding security suite can protect users when they click email links and browse, while integrating seamlessly with your existing SEIM, XDR, or EDR tools.
For MSPs, Vade’s email security suite enables you to manage all your clients from one portal and remediate malicious threats from multiple tenants in just a few easy clicks.
Businesses around the world trust Vade












Recognized by G2
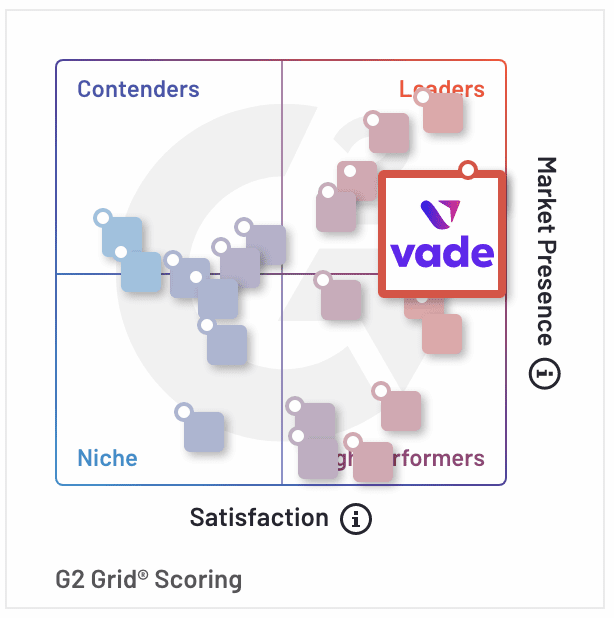
Vade recognized by G2 as a Leader in Email Security and More
Vade has been named a Leader in the G2 Grid® for Email Security, Cloud Email Security and Anti-Spam based on high customer satisfaction and substantial market presence.
Key takeaways:
- 100% of users rated it 4 or 5 stars
- 100% of users believe Vade is headed in the right direction
- 97% of users said they would be likely to recommend Vade