Color Schemes: Detecting Logos in Phishing Attacks
Sébastien Goutal
—December 05, 2019
—4 min read

If a staff member correctly identifies and reports a phishing email, it’s your lucky day—you and your business just dodged a bullet. Unfortunately, even phishing attacks that are reported and blocked can reappear, even in the same user’s inbox, and more than once.
Frustrated users assume their reports are being ignored, while businesses get the impression that their anti-phishing solution isn’t doing its job. The truth is that to a user, it’s clearly the same email, but to a filter, it is quite unique. Why?
Email filters continually analyze email content, such as metadata, HTML content, attachments, etc.. What they can’t do is see what is apparent to everyone else.
Phishers’ techniques
When phishing attacks are detected by filters, the email content is analyzed, and email signatures, phishing URLs, or domains are extracted and added to blacklists. This effectively blocks the phishing email from being delivered in the future. Code obfuscation and Bayesian poisoning are hackers’ ways around this.
From adding invisible text to the underlying code; to adding a URL redirect or shortener; to adding new, legitimate links to the email, there are a number of clever ways to confuse a signature or statistical-based technology.
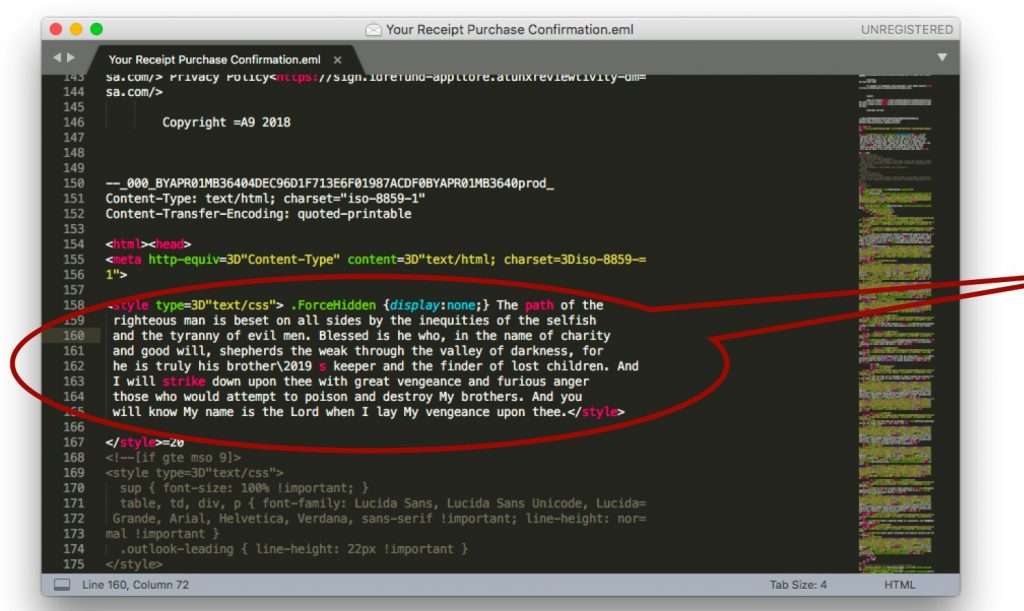
Below are two examples of filter bypassing techniques. In the first example, the hacker inserted a dialogue from the film Pulp Fiction: this is known as a Bayesian poisoning attack, where data is inserted to disturb statistical based filters such as Bayesian filters:
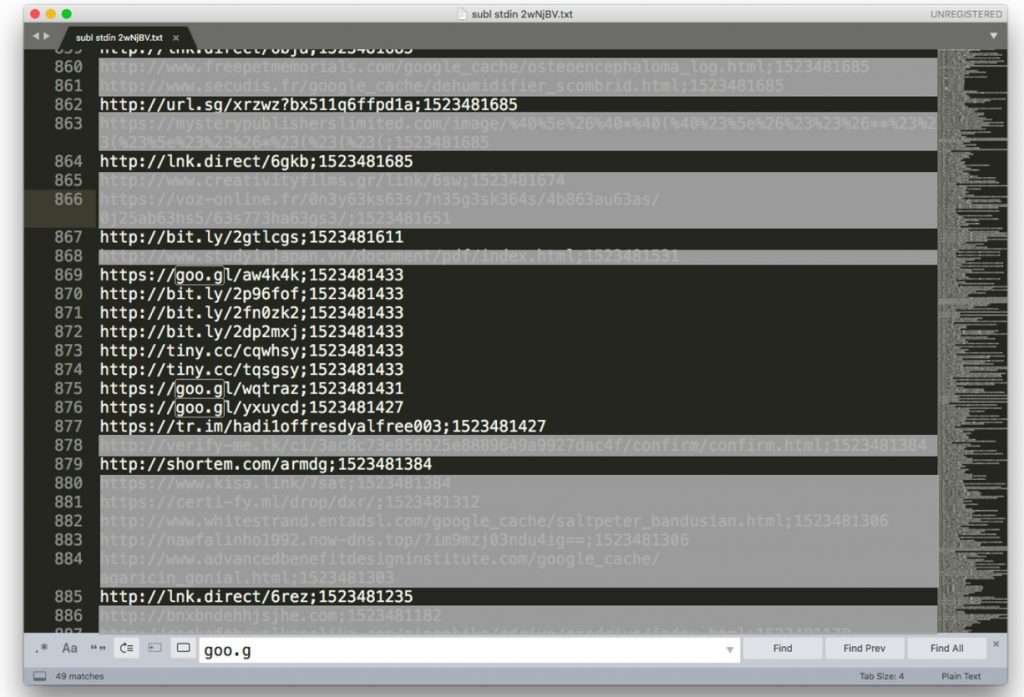
The second example includes a series of URL shorteners that have been used to hide a phishing link:
[Related] 4 Ways Hackers Break Through Fingerprint and Reputation-based Email Security
A primer on phishing images
To impersonate brands in a convincing way, phishers add brand logos and images to their phishing pages. The better the quality of the image, the more convincing the phishing page is to the recipient. Below is an example of a Microsoft login page. When asked to identify the real page from the Microsoft phishing page, most users make the wrong selection:

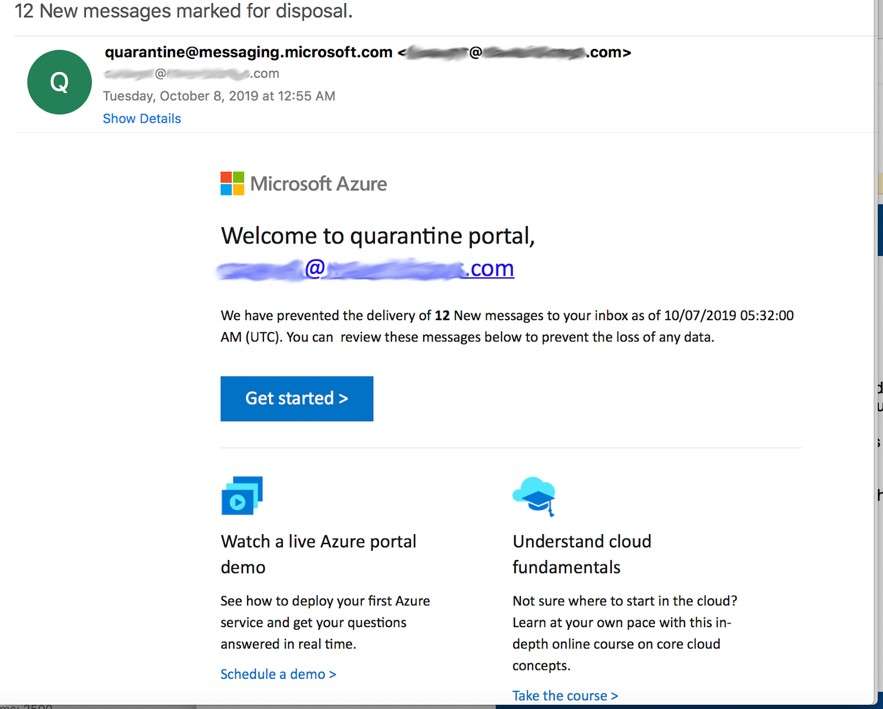
We’ve all received a poor phishing email that was clearly crafted by an amateur. But when both the text and the images are flawless, the phishing attack becomes more difficult to detect. The Microsoft Azure email below, detected by Vade, is an example of a clean, error-free email with good branding.
[Related] Phishers’ Favorites: After Five Quarters, Microsoft Is Unseated by PayPal
The emergence of image manipulation in phishing attacks
An image can be identified by a fingerprint, such as cryptographic hash. However, if the image changes slightly—even by a single bit—the cryptographic hash changes dramatically. But changes to the image itself are so subtle that there is no visible difference to a human from the original. Theoretically, a previously identified phishing email with a new, altered logo could easily bypass a filter that uses a blacklist of images’ cryptographic hashes.
In addition to the above example, phishers use a number of other techniques to bypass filters leveraging traditional Computer Vision algorithms, such as template matching algorithms. In the example below, the phisher has inserted a barely visible gray Microsoft logo onto a blue background. Template matching algorithms are not resilient to a small change in color setup or geometry and thus will not able to detect this variant of Microsoft logo.

Another example is use of QR codes, widely used in sextortion emails to redirect the victim to the Bitcoin URL to pay the ransom. Because URLs can be easily parsed and extracted by an email filter, hackers insert QR codes, such that only technologies leveraging Computer Vision and QR code extraction will be able to extract and analyze the URL.
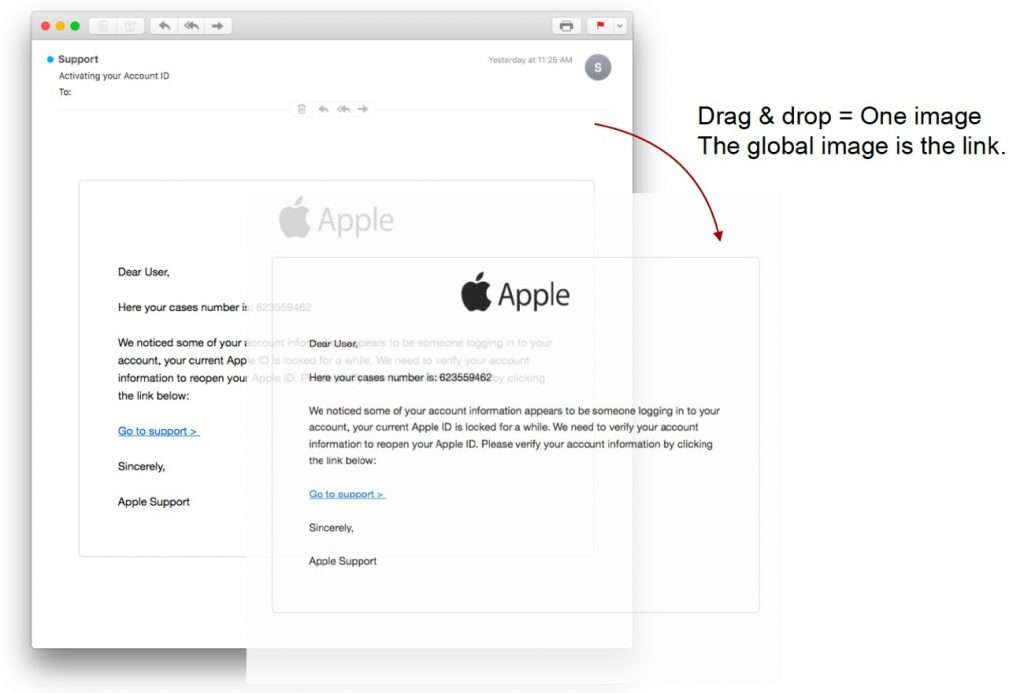
Text-based images are also emerging in phishing attacks to evade URL-scanning and code-based detection. In the example below, a hacker has inserted an image of an Apple email into the body of the email. The image is hosted on a website and the image is a clickable phishing link:
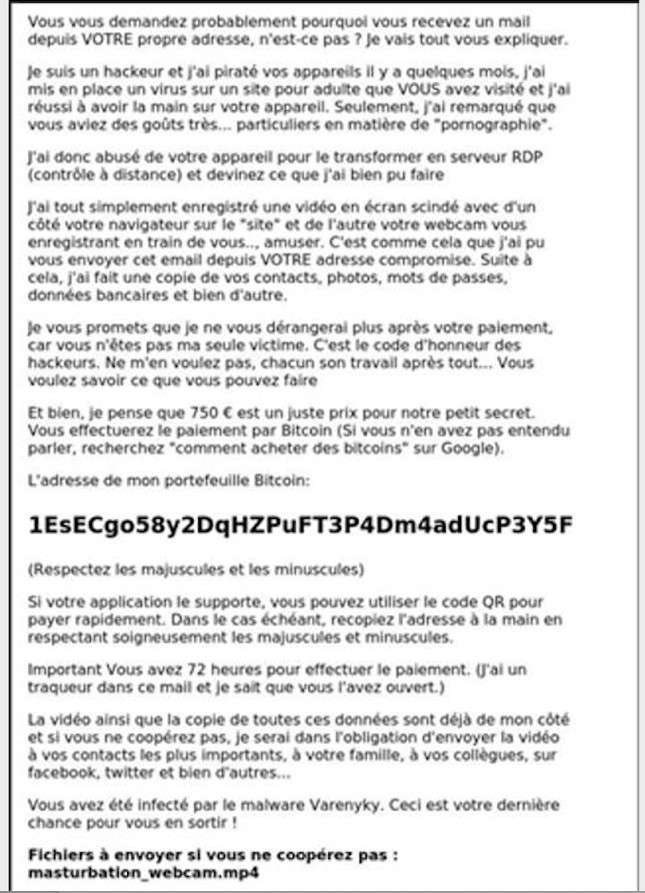
Below is a sextortion email detected by the Vade team in France. Like the Apple example above, the email is a text-based image—a screenshot—disguised as body text:
[eBook] SC Magazine Expert Focus: Defending the Inbox
Computer Vision and image detection
Computer Vision algorithms based on Convolutional Neural Network (CNN) interpret and view images as humans see them. Vade Computer Vision engine was developed with VGG-16 and ResNet CNN—two of the most popular CNN models—to detect logos of the top phished brands. The decisions of both models are combined with a proprietary algorithm to achieve maximal accuracy. The goal is to improve phishing detection accuracy, automate Security Operations Center activity, and alert brands who are unknowingly being impersonated in phishing attacks.
Vade’s Research team applied transfer learning to fine-tune pre-trained VGG-16 and ResNet models. First, thousands of images were collected and labeled manually. Then images with logos in different configurations were generated algorithmically, using different graphical resources, such as logos, background images, fonts, texts, color palettes, etc.. Finally, the images were augmented artificially with different transformations, such as cropping, down sampling, blurring, modifying HSV color space, etc., to reduce overfitting—in other words, to increase the models' resilience to changes. The final corpus of ~200,000 images was then used to fine-tune the models.
This process teaches the models to recognize a combination of techniques phishers use to conceal images from algorithms that are looking for an exact or close match. Below are just two generated images that were used to train the models. Like the Microsoft phishing email example above, the logos are placed on top of other images to train the model to recognize a logo in an unexpected configuration (position, background, presence of text near the logo):


The fine-tuning of the models on a specific corpus of 2D images also shows that the detection of logos by Vade's Computer Vision technology performs better in many situations than more general-purpose logo detection technologies such as Google Vision. For example, during internal benchmarking against Google Vision, Vade’s Computer Vision engine detected these well-known logos (blue bounding box for Vade, green bound box for ground truth), while Google Vision surprisingly did not:


The future of phishing
Phishing attempts get better by the day. To keep up with the latest threats, anti-phishing technology must match their sophistication. Vade outperformed Google Vision’s API logo detection feature, recognizing more phishing logos in benchmark testing.
The Computer Vision Engine is constantly being updated with new images and new logos, based, for instance on phishing threats reported to Vade and via IsItPhishing.ai, our free service where users can paste a URL in a search bar and automatically learn whether the link is legitimate or if it is a phishing link.



