

Sécurité de l’email en 2023 : les 4 tendances à connaître
Votre entreprise se doit de suivre les dernières tendances de la sécurité de l’email. En effet, Hornetsecurity a détecté plus de 440 millions d’emails de phishing ou contenant des malwares au 1er semestre 2022, un chiffre impressionnant qui montre bien que les cybercriminels restent extrêmement actifs et motivés. Pour vous aider à vous en prémunir, les experts de Hornetsecurity vous présentent leurs prédictions annuelles. Découvrez les menaces et tendances qui seront sur le devant de la scène en 2023 !
Les attaques de phishing vont se concentrer sur les services de MFA et autres services légitimes
L’autorisation à plusieurs facteurs (MFA) n’est plus une nouveauté pour les organisations. Il s’agit aujourd’hui d’une mesure de sécurité très répandue, qui consiste à utiliser au moins deux méthodes de connexion différentes pour authentifier un utilisateur. À ce titre, la MFA constitue donc un maillon essentiel de la cybersécurité. Malheureusement, les hackers sont capables de la contourner. Pour ce faire, ils tirent parti de l’excès de confiance des organisations dans ce mécanisme, qu’elles considèrent bien souvent comme une panacée.
D’après Romain Basset, Director of Customer Services chez Hornetsecurity, « De plus en plus de campagnes de phishing vont être capables de contourner la MFA en se faisant passer pour le système d’authentification ou en dupant des utilisateurs lassés par la multiplication de ce type de demande ». Ce dernier point fait référence à une attaque de septembre 2022 lors de laquelle un hacker a pu compromettre les réseaux internes d’Uber en profitant de cette lassitude vis-à-vis de la MFA.
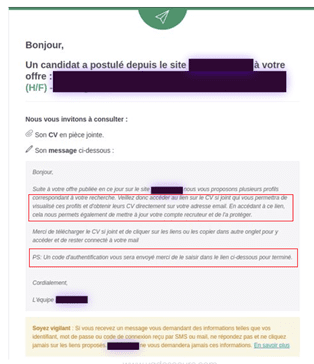
Pour Romain Basset, les campagnes de phishing utilisant des services légitimes pour distribuer des liens malveillants vont aussi augmenter. « Les récentes attaques contre un organisme d’accompagnement des demandeurs d’emploi en France sont un excellent exemple de l’utilisation d’un site légitime à des fins malveillantes», explique-t-il. Dans cette attaque, les hackers ont postulé à des offres d’emploi et utilisé l’infrastructure légitime du site pour transmettre des liens de phishing aux entreprises qui recrutent des candidats. Hornetsecurity a détecté le premier scam de ce genre en septembre 2022.
Malgré l’avènement de nouveaux types de scams, l’équipe des experts en cybermenaces (CTE) de Hornetsecurity invite les organisations à rester vigilantes, car les techniques éprouvées des hackers restent d’actualité. « Les campagnes de phishing liées aux impôts, mais aussi les scams de paiement et de livraison de colis restent efficaces, pertinents et fréquents. Les attaquants continuent de les utiliser, tout en améliorant le contenu et les techniques de leurs attaques. Ils testent jour après jour les filtres de messagerie pour détecter leurs faiblesses et les exploiter. »
L’équipe CTE nous donne l’exemple d’une récente campagne de phishing dont les emails tiraient parti du partenariat entre Capital One et Authentify, un service de vérification en ligne. Cette campagne commençait par un email de phishing invitant les victimes à se rendre sur un site WordPress compromis, qui leur demandait d’envoyer des copies du recto et du verso d’une pièce d’identité.

Les techniques liées à la supply chain et au détournement de conversations vont se multiplier
Les techniques liées à la supply chain et au détournement de conversations vont se multiplier
Les organisations musclent leurs investissements dans les formations de sensibilisation au phishing afin de renforcer le maillon faible de leur cyberdéfense, l’humain. Pour Michael Posey, ingénieur avant-ventes chez Hornetsecurity, cette bonne nouvelle s’accompagne toutefois d’un risque, celui de voir les méthodes des hackers évoluer.
« À mesure que les utilisateurs sauront repérer et signaler plus efficacement les techniques de phishing classiques visant les marques connues, les hackers vont s’adapter, notamment en se faisant passer pour des fournisseurs ou des clients. Je pense que nous allons voir une augmentation des attaques contre la supply chain et du détournement de conversations ».
Les attaques contre la supply chain consistent à infiltrer les systèmes d’une organisation en se faisant passer pour un fournisseur y ayant accès ou en compromettant directement ce fournisseur. Le détournement de conversations consiste quant à lui à utiliser des comptes compromis pour rejoindre des échanges par email ou en créer. Une fois insérés dans la conversation, les hackers peuvent alors lancer des attaques de phishing ou de spear-phishing.
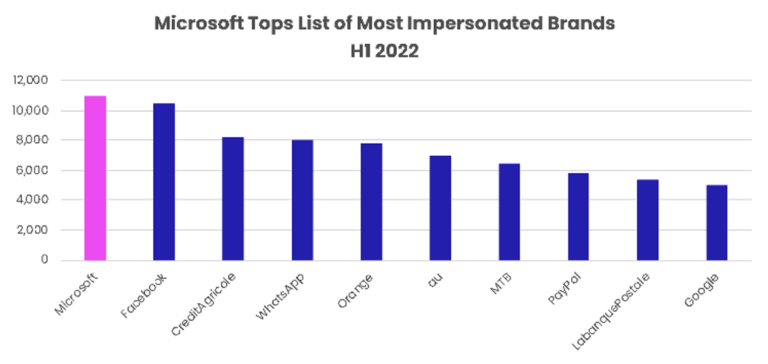
Pour autant, il estime que les campagnes de phishing se faisant passer pour de grandes marques comme Facebook et Microsoft vont perdurer. Le rapport de Hornetsecurity publié au 1er semestre 2022, qui met en lumière les principales marques usurpées par les hackers, conforte sa vision. C’est en effet Microsoft dont l’identité a été la plus usurpée au 1er semestre 2022, avec 11 041 URL de phishing uniques. Facebook s’arroge la seconde place avec 10 448 liens de phishing. Le Crédit Agricole, WhatsApp et Orange ferment le top 5.
Les emails de phishing ont longtemps touché tous les internautes sans discrimination, mais les campagnes récentes témoignent d’un basculement vers un ciblage renforcé. En juillet, Hornetsecurity a détecté une campagne de phishing Instagram qui a montré que les hackers se renseignent sur leurs victimes avant de déployer des attaques hautement ciblées.
Les attaques de ransomwares vont rester dévastatrices
Les attaques de ransomwares ont souvent fait les gros titres en 2022, et notre équipe CTE estime qu’elles vont continuer à infliger des dégâts considérables aux organisations. « Comme l’année dernière, les ransomwares devraient gagner en sophistication. Ils sauront se faire plus discrets et évolutifs, et exploiteront de nouvelles vulnérabilités pour se propager. Des groupes d’acteurs malveillants comme BlackCat ne cessent d’affûter leurs stratégies. »
Deux facteurs vont contribuer à maintenir le nombre d’attaques de ransomwares : le Ransomware-as-a-Service (RaaS) et la double extorsion. « Le RaaS est une source de revenus centrale pour les hackers. Tant que cette situation perdurera, ils resteront actifs. Il permet aussi aux criminels moins compétents d’engranger de l’argent à l’aide de ransomwares sophistiqués. »
« La double extorsion offre un levier supplémentaire aux criminels. L’exfiltration de données et la menace de divulguer des informations sensibles incitent les organisations à accéder à leurs demandes pour tenter d’échapper aux conséquences réglementaires, légales ou réputationnelles de l’attaque. Nous avons observé cette stratégie chez des groupes comme Hive, en particulier dans le secteur de la santé. »
Comme pour les autres menaces, l’équipe CTE estime que les hackers vont continuer de concentrer leurs attaques de ransomwares sur les petites organisations. « Nous constatons déjà que les hackers privilégient les PME et les MSP au détriment des grandes entreprises. Ces structures ne disposent pas des mêmes ressources et budgets pour assurer leur cybersécurité et sont donc plus vulnérables. »
Pour l’équipe CTE, les hackers semblent préférer la simplicité et l’efficacité des attaques contre les petites entreprises aux récompenses plus importantes qu’ils pourraient obtenir en s’en prenant à de gros poissons.
La sécurité des suites bureautiques remplacera la sécurité de l’email en 2023
L’email fait partie intégrante des systèmes, processus et services internes des organisations. Adrien Gendre, Chief Technology and Product Officer et cofondateur de Hornetsecurity, estime que la sécurité de l’email va tenir compte de cette réalité en allant au-delà des seules boîtes de réception et d’envoi. « Les attaques deviennent plus nombreuses et sophistiquées. Pour y faire face, les PME et MSP devront miser sur une technologie étroitement intégrée aux suites de productivité modernes comme Microsoft 365 et Google Workspace, et offrir des informations complètes sur les menaces », explique-t-il.
Il estime que contrairement aux passerelles de messagerie sécurisées, qui séparent la sécurité de l’email des réseaux internes, les solutions basées sur des API sont l’avenir de la sécurité de l’email. « Les organisations doivent pouvoir tirer parti des informations sur les menaces issues des emails pour protéger les applications de partage de fichiers et autres outils de collaboration, comme la messagerie instantanée. Elles doivent également pouvoir exploiter des informations comme les profils des utilisateurs, leurs contacts et leurs habitudes de communication pour se prémunir des attaques hautement ciblées, comme celles qui visent aujourd’hui la supply chain. »
D’après l’équipe CTE, l’email donne aux hackers un net avantage sur leurs victimes en leur permettant de camoufler leurs activités. « Les hackers tirent parti du nombre astronomique d’emails échangés chaque jour, car il impose aux organisations d’analyser des quantités considérables de données pour détecter les menaces. Si l’on ajoute à cela la nécessité d’éliminer les vulnérabilités de leurs systèmes et d’assurer une protection continue, les organisations ont du mal à rester au niveau. »
La technologie est la clé permettant de combler cette lacune. « Les organisations auront besoin de solutions capables de détecter des menaces peu diffusées qui touchent les utilisateurs ou leurs clients et pouvoir y remédier rapidement depuis une interface unifiée. Les PME et les MSP n’ont pas les moyens de gérer 15 produits à partir de 15 consoles », explique Adrien Gendre.
Renforcement de la sécurité de l’email pour 2023 et les années à venir
Cette année, les cybercriminels ont lancé des attaques plus ciblées et créatives. Alors que les organisations investissent toujours plus dans la cybersécurité et la sensibilisation de leurs utilisateurs, il est probable que les hackers redoublent d’efforts. Ils vont miser sur la MFA, le détournement des conversations, la supply chain, la double extorsion et bien d’autres activités malveillantes. Quelle que soit leur approche, l’email restera le principal vecteur des cybermenaces. « La majorité des attaques commencera toujours par un email, car il s’agit du moyen le plus efficace et direct d’atteindre le maillon faible des organisations, à savoir les utilisateurs finaux », affirme l’équipe CTE.
Pour faire face aux hackers, les organisations ont besoin d’une technologie de détection et de réponse basée sur l’IA et capable de les défendre contre les menaces connues, émergentes ou encore jamais étudiées véhiculées par emails. Il est important qu’elles se mettent en quête de solutions déployées dans leur environnement et offrant une protection contre les menaces issues de comptes compromis ou se déplaçant au sein de leurs suites de productivité. Elles doivent également miser sur une technologie générant en temps réel des informations sur les menaces qu’elles peuvent exploiter facilement et efficacement.
