Cybersecurity: 2017 retrospective
Adrien Gendre
—January 29, 2020
—2 min read

It a good time to recall the key facts in this cybersecurity 2017 retrospective.
Cyber-attacks have grown more sophisticated.
2017 is the year that we became aware of this. A collective acknowledgment which has demonstrated to us that a cyber-attack can now stop a company’s production tools, whatever their size or their location in the world.
2017 was the year that digital arms proliferated.
In April, the “shadow brokers” hacker group distributed tools taken from the NSA.
The “shadow brokers” distributed a second batch of computer programs taken from the NSA on April 14, 2017.
This act was significant in the IT and cyber security world.
For the first time, sophisticated operating tools for Windows operating systems are no longer the exclusive prerogative of a country.
The technological barrier was stormed, allowing any hacker group to launch a large-scale cyber-attack.
It was only a few weeks later that WannaCry appeared, which was developed using two vulnerabilities found at the NSA, called “eternal blue” and “double pulsar.”
In May, “Jaff” ransomware, distributed by the Necurs botnet, targeted corporate email clients.
As you saw last may in our dedicated article, the Vade filter stopped 633,920 emails containing Jaff ransomware in 48 hours.
Distributed by the Necurs botnet, this malware, which was very similar in design to Locky ransomware, targeted many companies within a very short period.
Using a 0-day fault from the Microsoft Office suite, this malware was able to download a malicious program when opening an attachment.
Microsoft took several days to publish a corrective action, leaving users who had no filtering solution with unprotected emails.
Find our contribution to this subject on the broadcast by Tech & Co. on BFM Business (video).
WannaCry hit companies and people in May 2017.
Due to WannaCry, companies including FedEx in the US, Renault and Saint Gobain in France, were required to stop their production for several days.
Using faults which had not been known, WannaCry affected thousands of companies in more than 150 countries, infecting 300,000 machines using the Windows operating system.
This ransomware was covered so often by traditional media that the term “ransomware” became a trending search for several weeks on Google.
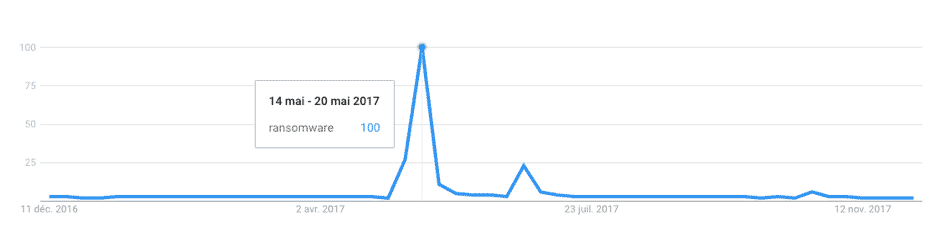
According to recent estimates, WannaCry had a financial impact estimated at between 900 million and 1.5 billion dollars around the world.
In 2017, the volume of malware sent by email grew significantly.
Even though WannaCry, Jaff, Locky and Bad Rabbit made a lot of noise in 2017, the cumulative volume of these different ransomwares is a drop in the bucket compared to the volume of malware stopped every day.
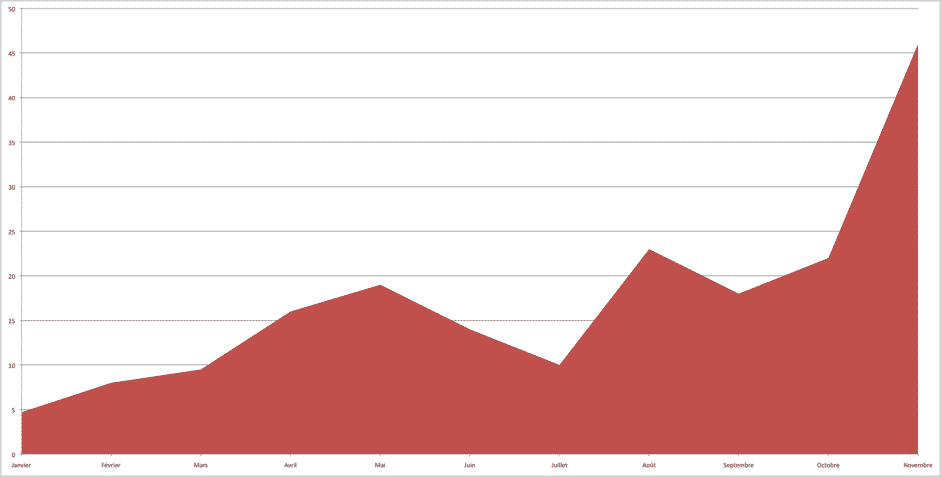
As shown in this graph, the volume of malware sent by email significantly increased in 2017, doubling from August to November 2017.
The Vade filter detected and stopped 46 million emails containing malware.
In 2017, email remained the prime target for cyber attackers.
It is estimated that cyber attackers used email 91% of the time as their distribution medium.
Personal data leakage has always been more significant.
2017 saw a record year in terms of the volume of corporate data leaked to the Internet.
- Equifax: 143 million accounts: Leaks of American citizens’ financial data
- Uber: 57 million accounts: Leaks containing driver’s licenses and information about drivers.
- Deloitte (not communicated): Leak containing the accounting reports of their customers.
- Paradise Papers: 13.5 million confidential documents about offshore companies.
What is the impact of these data leaks?
These data leaks promote more sophisticated spear phishing attacks.
In addition, with the application of the general rules for data protection (RGPD) in May 2018, companies must integrate data protection in each of their services offered.
This level of data protection includes securing employees against phishing and spear phishing attacks to avoid involuntary leaks.



