DMARC: The Limitations of Sender Authentication
Romain Basset
—March 05, 2020
—4 min read

Both phishing and spear phishing emails are designed to deceive victims into believing they’re receiving an email from a trusted source, such as a brand or an acquaintance. It’s made possible by email spoofing, a technique that requires little to no technical hacking skills but causes massive amounts of damage when done right.
DMARC (Domain-based Messaging, Authentication, Reporting, and Conformance) is widely regarded as the answer to the spoofing problem. While it’s true that it’s effective against exact domain spoofing, it doesn’t solve the problem of close cousin spoofing and display name spoofing (we’ll get into that later). Let’s take a closer look at DMARC and what it does and doesn’t solve.
What is DMARC?
DMARC is based on DKIM (Domain Keys Identified Mail) and SPF (Sender Policy Framework). SPF prevents spammers and other malicious senders from sending emails on behalf of a domain. An organization publishes their SPF record to tell other systems which servers can send emails from their domain, and the receiving domain will block the sender if the server is not approved.
DKIM authentication blocks unauthorized senders by adding an encrypted DKIM signature to emails from authorized senders. The receiving system checks the email for the DKIM signature and, if present, the email is approved for delivery.
Together, SPF and DKIM form the building blocks of DMARC. The DMARC record is a policy that tells a server how to process emails that are not easily managed by either DKIM and SPF. Once published, a DMARC record is published in a DNS and can be modified for adjustments. And that’s where things get difficult.
Sender authentication is a two-way street
Implementing DMARC to prevent spoofing of your own brand is an important step to ensuring your domain isn’t abused. However, it doesn’t prevent a hacker from spoofing another brand that hasn’t published DMARC and sending phishing and spear phishing emails to your employees.
Large, reputable brands have no doubt published DMARC to protect their domains, but this isn’t the case for all businesses, which might lack the IT resources needed to manage DMARC, which brings us to the biggest problem with DMARC.
Technical complexity
Deploying DKIM, SPF, and DMARC is complex and requires resources. Again, that might be feasible for large organizations but less so for SMBs. Additionally, a DMARC record must be maintained and constantly updated to accommodate new senders. Each time a business adds a new service, such as SaaS vendor, all notification senders must be added to the DMARC record, and the same goes for services that are cancelled. With the explosion of digital services, managing DMARC can become a nightmare.
DMARC doesn’t have an answer for close cousins and display name spoofing
An inexperienced hacker might try and fail to spoof the Microsoft domain, but skilled hackers know better. A brand like Microsoft most certainly uses DMARC and is protected from exact domain spoofing. Instead, hackers turn to two creative spoofing techniques that require little to no technical skill but can be extremely difficult to detect.
Before we look at these spoofing techniques, let’s look at an example of a spear phishing email detected by Vade. This hacker clearly had neither the time nor the patience to bother covering his tracks. They spoofed the display name (which we’ve concealed for privacy reasons), but the hacker’s email address is visible and a tell-tale sign of spoofing.
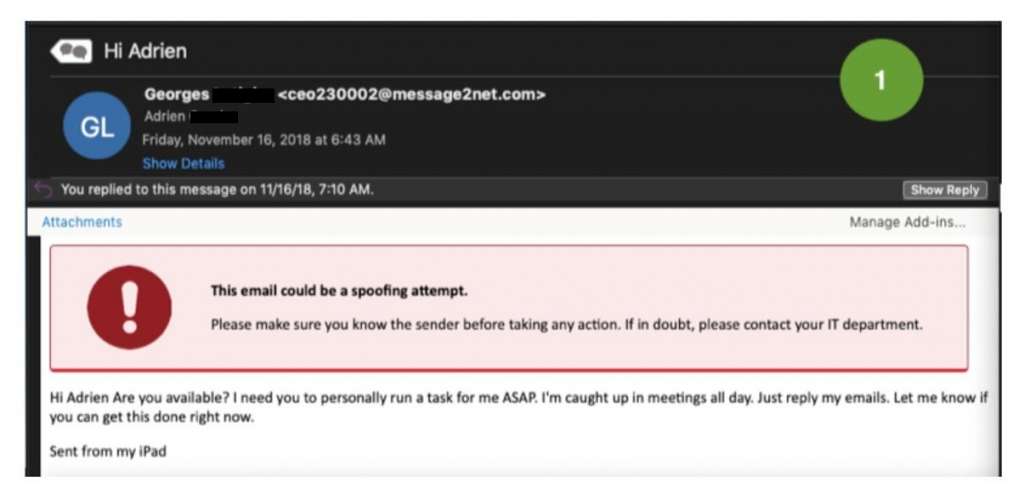
However, if the recipient had viewed the email on their mobile phone, the email address might be hidden unless expanded. This could explain the hacker’s lack of interest in creating a more believable email address. According to Verizon, this UI feature of many mobile devices is why 18 percent of clicks on phishing emails occur on mobile. Additionally, mobile users are more distracted as they are not stationary, and the likelihood that they’ll notice that the entire email header isn’t showing is quite small.
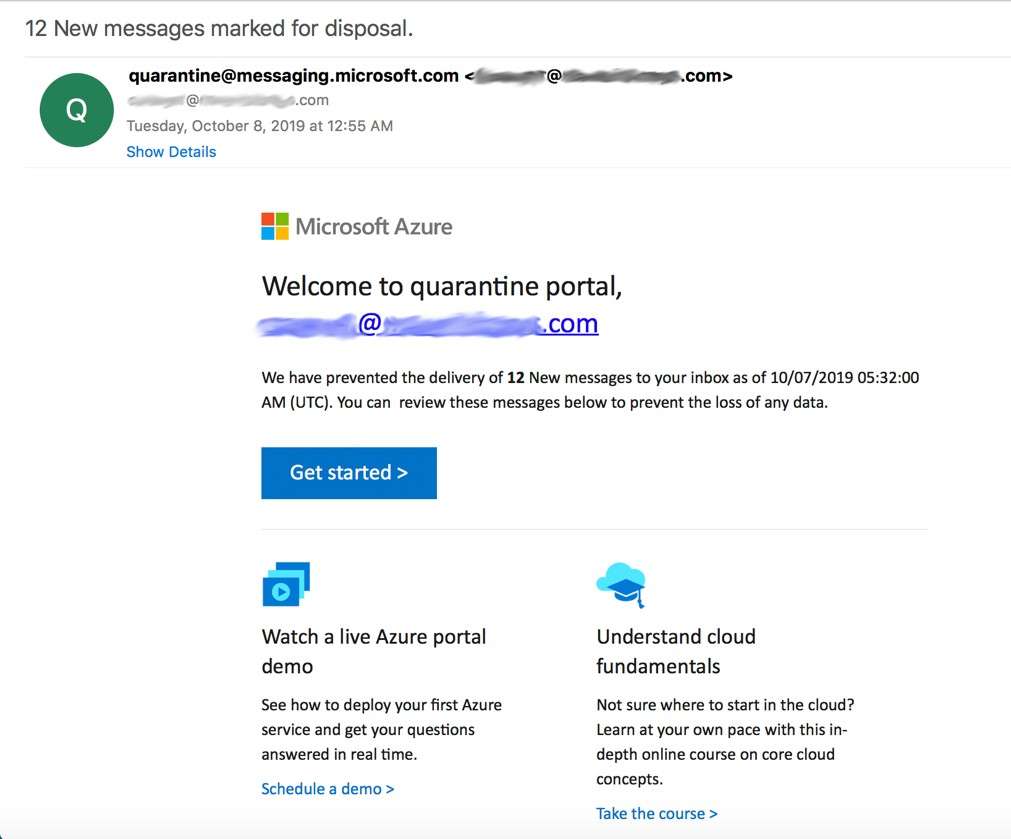
Display name spoofing
In this technique, a hacker reveals only the display name in the sender field. The display name can be anything they choose, from a fake but legitimate-looking email address or a variation of a brand name.
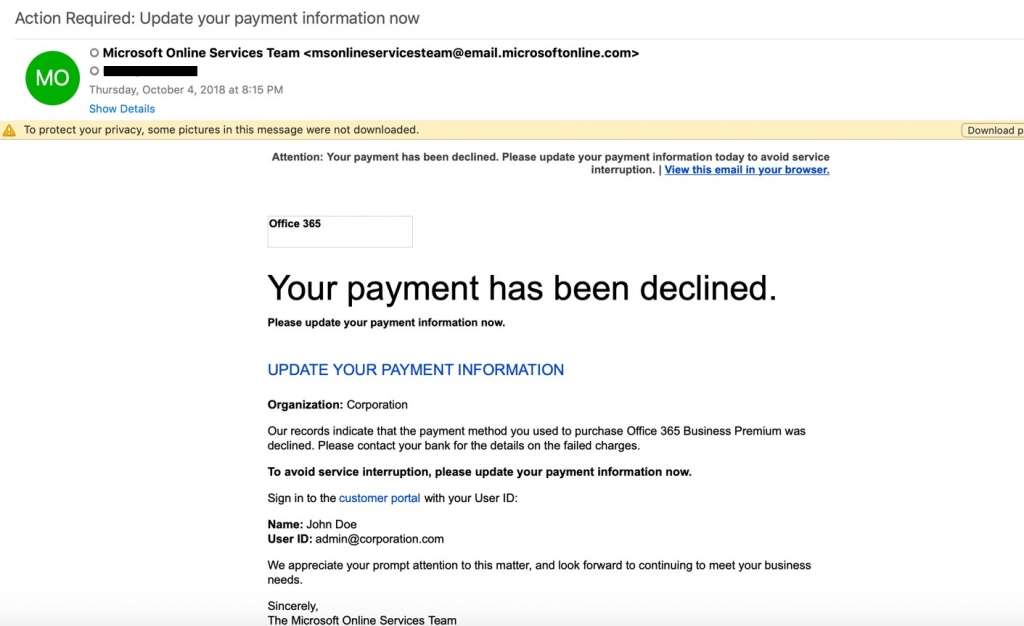
Close cousins
Like display name spoofing, close cousins rely on a combination of creativity and psychological manipulation. A close cousin email address might look like a replica of a legitimate email address, but often they include additional or fewer characters that aren’t noticeable at first glance, or they might feature Cyrillic characters that aren’t recognizable to the naked eye. Some feature extensions, such as company, .co, .global, or .ca.
DMARC wouldn’t stop any of the above emails from being delivered because they don’t abuse domains. It makes close cousins and display name spoofing optimal choices for phishing and spear phishing emails.
Close cousins and display name spoofing are difficult but not impossible to block. Because there’s no way to manually block every possible variation of a domain, it requires advanced technologies.
AI-based spoofing detection
Natural Language Processing (NLP) and Computer Vision analyze and detect anomalies and behaviors common to phishing and spear phishing emails. NLP is an AI-based field that works to understand the meaning of text and uses text clustering to recognize patterns.
Applied to spear phishing, NLP overcomes the difficulty of analyzing a text-only email by recognizing the intent of an email, which could be a request for a wire transfer or request for account credentials. Anomaly detection algorithms detect close cousins and display name spoofing by recognizing anomalies or inconsistencies, including email addresses that don’t match those in an organization’s entity model. Together, NLP and anomaly detection fill the gaps in signature-based detection by analyzing behaviors, patterns, and text to identify spear phishing.
A phishing email with a spoofed email address could pass a filter on a first scan, making URL scanning an effective countermeasure. Machine learning algorithms scan URLs in real time, exploring an unknown phishing URL and webpage. At the time of click and without latency to the user, an algorithm can detect obfuscation techniques like URL redirects and shorteners, and malicious behaviors on phishing pages.
Finally, if you’ve ever blacklisted an email only to see it appear in your inbox a few days later, it could be because your filter cannot see images. To bypass filters, hackers will send image-based emails with slight variations, which changes the hash of the email and renders a blacklisted phishing email a new, clean email to the filter.
Computer Vision, fairly new to the email security realm, answers this problem by analyzing images rather than text. Properly trained, a Computer Vision algorithm can detect images that have been distorted by hackers just enough to fool an email filter that is looking for a signature.

A layered approach
DMARC is an important step in protecting your business, but like any cybersecurity solution, DMARC should be combined with other technologies to provide optimal protection. A layered approach to email security should combine DMARC, AI-based protection, and user training. Finally, you should have documented processes in place so that your users know what do when they receive a suspicious message, including reporting suspicious emails and verifying financial requests over the phone or via another channel.



