Top Email Security Predictions for 2024: How to Stay Ahead of Hackers
Todd Stansfield
—November 02, 2023
—6 min read

2024 planning is well underway. As businesses budget and plan for the upcoming year, questions about cybersecurity loom large. How will the threat landscape change in the year ahead? What new attacks and techniques will surface? And how will their cybersecurity strategy need to adapt to provide protection?
To provide clarity as you prepare for the year ahead, we recently polled Vade’s cybersecurity analysts about their top email security predictions. Here’s what they had to say.
1. Quishing threats will continue
If you pay attention to the news, you probably noticed the media coverage of QR code phishing, otherwise known as Quishing or QRishing. Quishing is a technique where hackers embed malicious links or files in QR codes to evade detection. The threat can bypass email filters that lack QR code detection or reading capabilities. It can also make it more challenging for users to diagnose a threat, unlike emails containing a visible link or attachment.
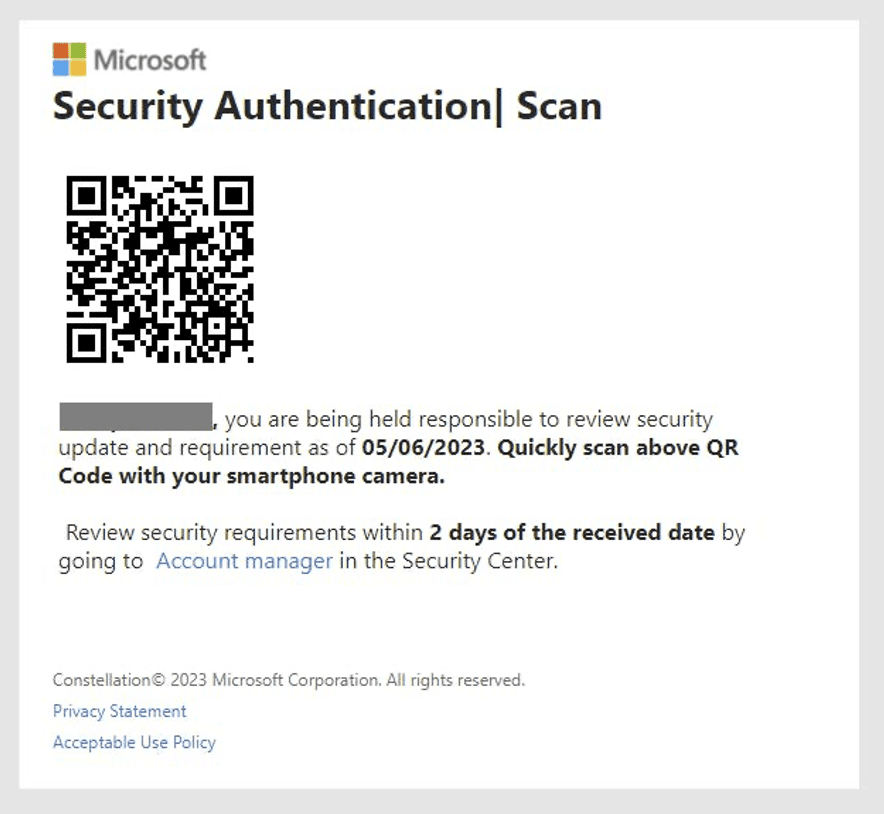
M365 Quishing email detected by Vade
Vade has detected a significant increase in Quishing attacks in 2023, with most threats targeting Microsoft 365 users. One example is a recent Quishing campaign we reported this week, which appears to be linked to the phishing-as-a-service (PhaaS), Greatness.
Despite all the recent attention, Quishing isn’t a new threat; Vade experts detected it as early as 2017. Its reemergence, however, suggests that hackers are finding success with the attack method.
“I expect QR code phishing to be on the rise,” said Sebastien Goutal, Chief Science Officer at Vade. “It’s challenging for vendors to leverage Computer Vision at scale to scan QR codes and extract links.”
Computer Vision algorithms view the world as a human would, scanning emails for image-based threats. These algorithms are trained to recognize malicious behaviors, including obfuscated URLs, URL redirections, remotely hosted images, manipulated images, and more. They can detect and analyze malicious links or files embedded in QR codes, rendering the technique obsolete.
Still, scanning a high volume of QR codes with Computer Vision requires significant memory and processing power and slows down the processing of emails. Some email security solutions overcome this limitation by analyzing other email features before using Computer Vision. Those that can detect advanced attacks while reducing demands on Computer Vision models are increasingly important amid the increase in Quishing threats.
2. Spear Phishing/Business Email Compromise (BEC)
Spear phishing continues to be a top threat for organizations—a trend Goutal expects to continue. “Spear phishing is very difficult to detect due to the scarcity of this kind of attack, and the absence of a URL or attachment payload. The payload is the textual content, which may appear innocuous or ‘business as usual’ to the recipient,” he said.
Goutal pointed out that spear phishing has existed for many years in the US. But in other countries, including France, the threat is relatively new and likely to persist in 2024.
When asked about the underlying trends in spear phishing, Goutal referenced a minor trend uncovered by Vade researchers: the indirect impersonation of law firms. The attack uses both lawyer and CEO fraud.
It starts with an illegitimate email from a law firm requesting payment of an invoice to avoid legal action. The email is sent to a hacker impersonating the CEO of a company, who then forwards the email to employees of that organization. Typically, the impersonated law firm is real, making the threat appear more credible to the intended victim.
“In terms of social engineering, it leverages the authority manipulation principle twice,” said Goutal. “First, the CEO, being the authority of the company. And second, the law firm, being an authority in legal matters.”
3. Emerging spear phishing technique
Goutal isn’t the only expert at Vade who names spear phishing as a top threat to watch out for in 2024. As users become more proficient at diagnosing spoofing attempts, hackers are honing their techniques. One example is an emerging cybersecurity threat where hackers engineer a fake email thread and forward the exchange to the intended target. Michael Posey, Technology Evangelist, has noticed an increase in this attack method.
“Hackers are doing this to show reason and authority,” said Posey. “What makes this sort of attack dangerous is that it passes all security checks (DKIM, DMARC, SPF) and does not directly impersonate anyone as the sender.”
Posey referenced a recent example in which hackers forwarded a fake conversation to a target company. The conversation appears to be between a legitimate employee and a representative of a non-profit organization. The company’s employee agrees to participate in a fundraiser and requests the non-profit to send an invoice to their colleague. The non-profit does, forwarding the previous email exchange and asking for payment. Yet the email thread doesn’t exist; it’s nothing more than text creating the illusion that a conversation took place.
Below is the thread, including a total of four emails. Only the last is real.
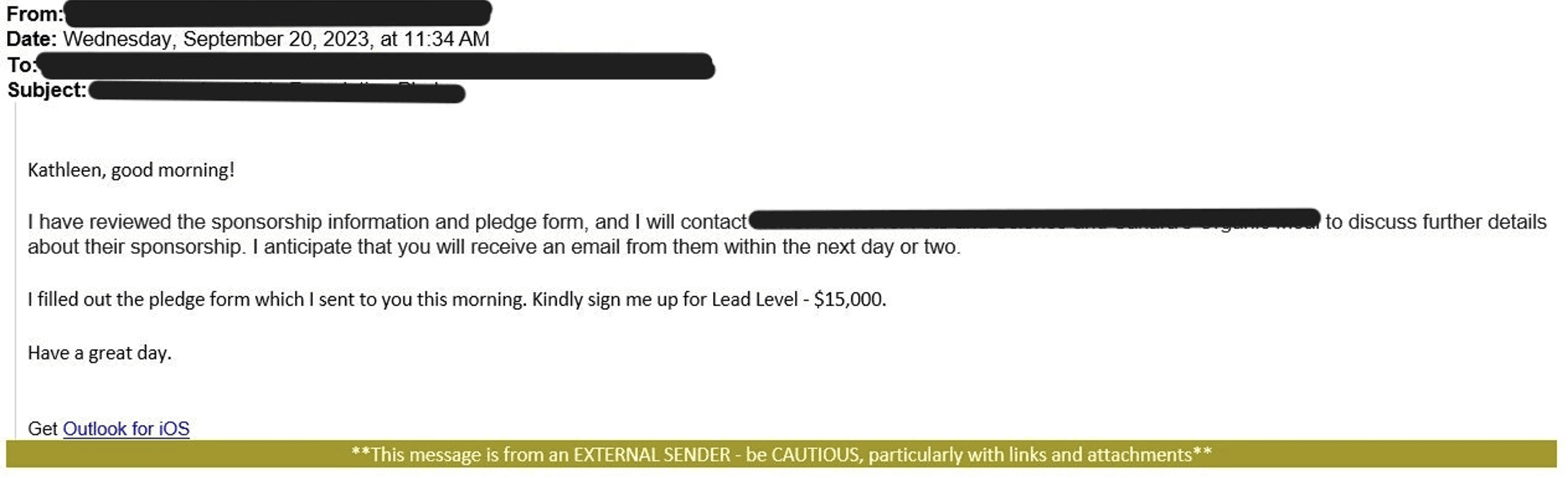
Malicious email 1
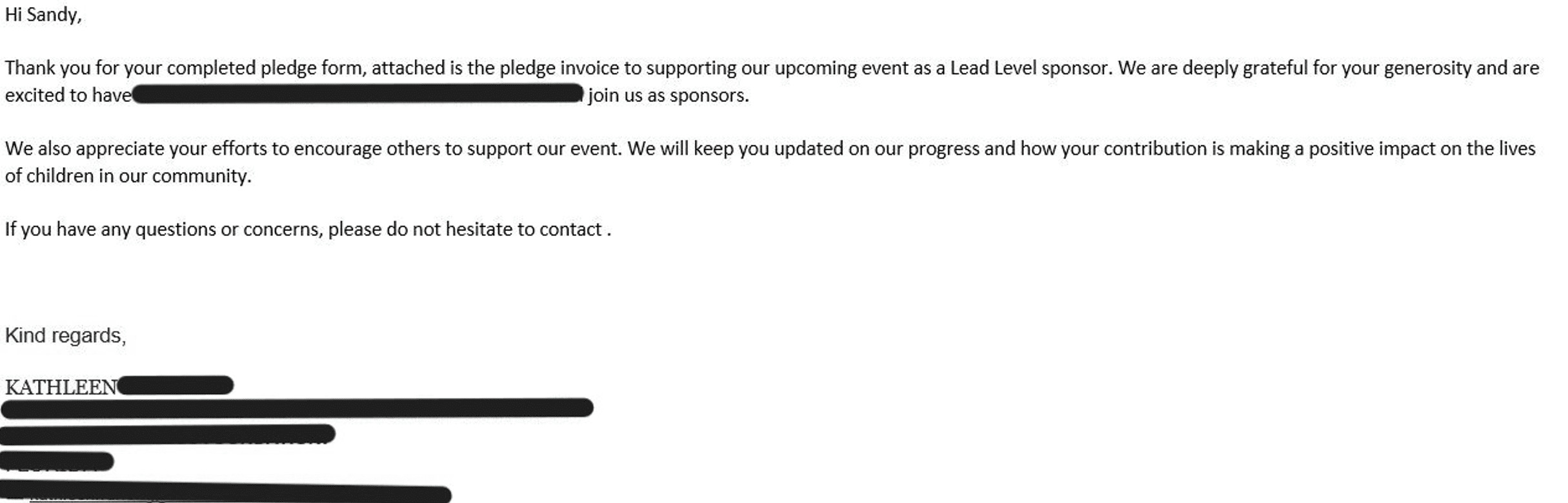
Malicious email 2

Malicious email 3

Malicious email 4
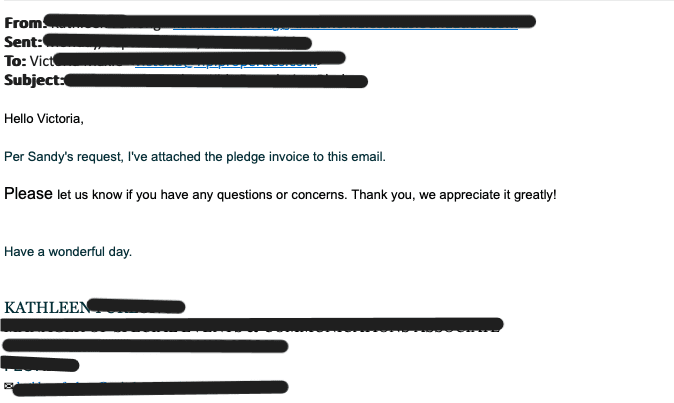
While the attack used impersonation, it only did so indirectly, as Posey mentioned. The employee supposedly responsible for the donation never directly communicated with the intended victim, making it different from other spear phishing attacks. In a typical spear-phishing scheme, hackers impersonate a sender who is known and trusted by the recipient.
Posey confirmed that the domain for the non-profit company was created a day before the real email message was sent. This enabled it to pass the authentication protocols. However, he noted that the dates of the fake email exchange occurred before the domain was registered.
Posey and his team have observed an increase in this type of attack, including this specific scheme on multiple occasions. “I’ve come across this same attack on multiple domains in the US and it presented much the same way, so this instance was somewhat easy to find,” he said.

4. The malicious use of generative AI and large language models (LLM)
2023 was the year of generative AI and large language models (LLMs). The sophisticated capabilities of ChatGPT simultaneously captured imaginations and stoked fears of AI’s potential as a technology. That was especially true for cybersecurity, where most attention focused on ability to create content—from producing phishing templates to malicious code and more.
According to Adrien Gendre, Chief Product and Technology Officer at Vade, those fears are warranted, but not in the way we expect. Content creation, while a risk to cybersecurity, is one that our modern solutions can address. The real threat is generative AI developing the ability to plan and orchestrate attacks. If that were to happen, it would mean that AI could design and execute attacks on the fly—and do so using information on the Internet. This includes details that may expose our vulnerabilities, cybersecurity solutions, and more. And the threat would only increase over time. Each failed attempt would be an opportunity for AI to learn and immediately improve.
This amounts to a nightmare scenario for organizations, one that would fundamentally transform the threat landscape.
“Generative AI promises to erase the greatest advantage we have over our adversaries: the time and resources required for sophisticated attacks,” said Gendre. “If generative AI can orchestrate attacks, it would shift the balance of power dramatically. Today, it takes hackers weeks to discover our vulnerabilities. Tomorrow, AI could do the same in a matter of second or minutes. And rather than requiring a team of hackers with diverse skillsets, it could only take just one person working with AI.”
Gendre doesn’t know when generative AI will reach the level of sophistication required to orchestrate attacks. Still, he cautions organizations to stay on alert. “The same way we saw ransomware-as-a-service (RaaS) in 2014, we could see a similar trend emerge with LLM for the darknet. It is a plausible threat.”
5. Sustained rise of malicious business models
Gendre referenced the growth of RaaS in 2014. Phishing-as-a-service (PhaaS) has also grown significantly in recent years, allowing anyone to buy a phishing kit. Phishing kits include everything needed to launch a sophisticated attack, allowing even novice hackers to deploy advanced threats.
PhaaS has likely contributed to the significant increase in the volume and sophistication of attacks detected by Vade. Over the past two years, Vade has detected more than 1 billion phishing emails annually. This is more per year than ever before, and with this mark being surpassed two years in a row, it may prove to be a very alarming trend indeed.
Analysts from Vade’s Threat Intelligence and Response Center (TIRC) expect the popularity of PhaaS to increase next year—even amid crackdowns on PhaaS operators, including the August shutdown of 16Shop. “We may see a successor of 16Shop arise,” said one analyst.
History continues to prove that hackers will always be eager to fill a void left by a previous operator. That’s especially true when it offers the potential for a highly lucrative scheme.
Fortify your email security for 2024 and beyond
As you plan for 2024, refining your cybersecurity strategy should remain a priority. History is proving that the threat landscape is becoming more malicious and active than before. As hackers upgrade their attacks, you should look to do the same with your security measures. Here are a few ways to stay protected.
User Awareness Training
Consider implementing or upgrading your user awareness training. Look for solutions that personalize instruction and administer it automatically whenever users need to learn. Additionally, train users on the below tips and encourage them to report any threats they encounter.
- Stay vigilant when opening emails that contain QR codes.
- Always inspect the URL path of any link or scanned QR code before clicking or tapping it.
- Verify the legitimacy of any sender and inspect emails for any signs of foul play.
- Stay cautious of emails that convey a sense of urgency and are financial in nature.
- Stay vigilant when asked to provide personally identifiable information and scrutinize websites asking you to furnish this information.
Email security
Microsoft 365’s native security features, while valuable, are not enough to protect against emerging threats. If you haven’t already, strongly consider upgrading your email security and adopting an integrated solution from a third party.
Look for solutions that use Machine Learning, Computer Vision, and Natural Language Processing (NLP) models to scan for malicious behaviors and anomalies. While Computer Vision is needed to protect against Quishing attacks, NLP provides protection against spear-phishing attacks. NLP models can detect malicious textual patterns and anomalies, including flag words and malicious phrasing. That makes it an effective complement to image-based detection.
Additionally, look for email security solutions that offer robust protection over the entire lifespan of an email. This begins with detection but also covers incident response, threat investigation, and remote browser isolation (RBI)—the latter important for guarding against browser-based exploits that originate from email. A well-balanced email security solution can help you build a multi-layered defense against threats.

.png?width=625&height=125&name=Vade%20Webinar-Emerging%20Threats%20and%20Trends%20That%20Will%20Define%202024%20(1).png)


