Office 365 Phishing Attacks: How Hackers Get Access to Your Business
Adrien Gendre
—July 02, 2020
—4 min read

Why phishers love Office 365
Microsoft was the second most impersonated brand in phishing attacks in 2021—thanks to Office 365. A multisystem platform, Office 365, now Microsoft 365, combines email, file storage, collaboration, and productivity applications, including OneDrive and SharePoint. Together, they represent a wealth of sensitive data and files, making Office 365 phishing attacks a lucrative business for hackers and the need of advanced Office 365 ransomware protection a priority.
More than one million businesses use Microsoft 365 worldwide. Whether corporate trade secrets or financial information, the productivity and collaboration suite houses business-critical data that, if exposed, could cause irreparable damage.

With a single set of legitimate Office 365 credentials, a hacker can move on to phase two of the attack: spear phishing, which is ultimately about the financial payout. Moving freely within Office 365, the hacker can impersonate employees to request wire transfers and gift cards, demand ransoms, and more. Moreover, they’re able to acquire more Office 365 credentials and spread across other organizations.
Why users fall for Office 365 phishing attacks
Attackers mimic the protocols and appearance of Office 365 messages and interfaces to trick users into disclosing their login credentials. In some cases, phishers take advantage of the Microsoft Azure Binary Large OBject (BLOB) storage as a means to build landing pages with Microsoft-signed SSL certificates and a windows.net domain. With credential-stealing pages literally built on the same platform used by the recipient, it’s easy to trick users.
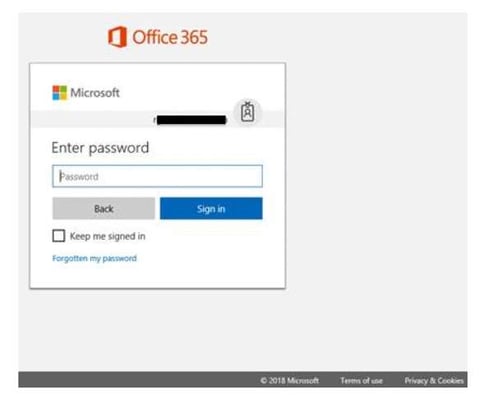
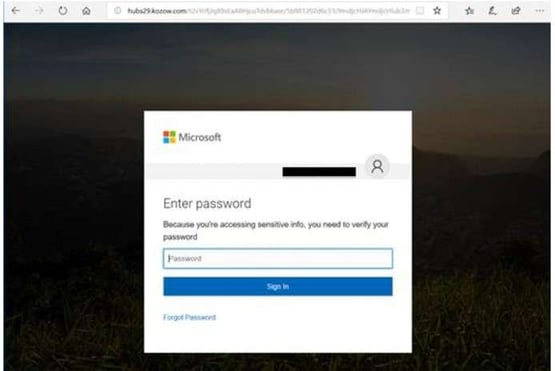
Once they’ve gained access to legitimate Microsoft credentials, attackers are able to conduct multiphase attacks from within Office 365. Through internal spear phishing emails, attackers impersonate users and trick employees into releasing wire transfers, sharing employee data, purchasing gift cards, and more.
Types of Office 365 phishing attacks
Sophisticated, innovative, and relentless, attackers use a number of Office 365 phishing techniques to conduct attacks. Phishing overall is more targeted than in the past, with hackers sending much lower volumes of email (it’s rare for a single attack to target hundreds or thousands of recipients anymore). They’re also more dynamic than ever, with many attacks using a unique sender/IP, URL, image, and subject line for each message. Below are just a few of the techniques Vade has detected in Office 365 accounts.
The voicemail attack
Outlook for Office 365 indicates you have an email. The subject line reads: “Incoming: You received a voice message from +1 508 *** - 250 seconds.” It’s personalized with your first name in the body of the message. Along with the realistic-looking phone number, the email contains a phishing link you can click on to hear your message.
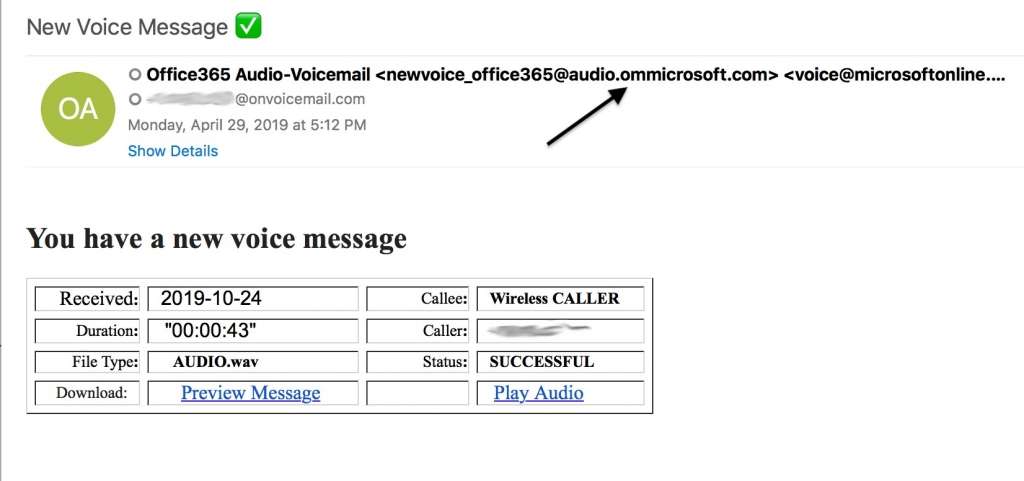
In one example of a voice message attack, the email sender’s name is displayed as “voice-mail service” in Outlook, and the sender’s domain address contains “microsoft.com.” This looks like a Microsoft system message, right? It isn’t.
The Microsoft phishing link could send you to a Microsoft login screen that looks perfectly real, except it’s not. It’s a phishing site designed to steal your Office 365 login credentials.
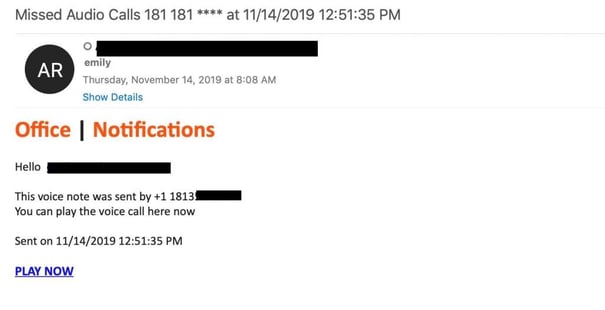
In an alternative version of this attack, the message comes from an address like “no_reply@myverizon-voices.net” The message may include a link to a PDF hosted on a compromised SharePoint site. The PDF takes you to another phishing site. In the below example, the phishing link in the missed voicemail message contains malware.
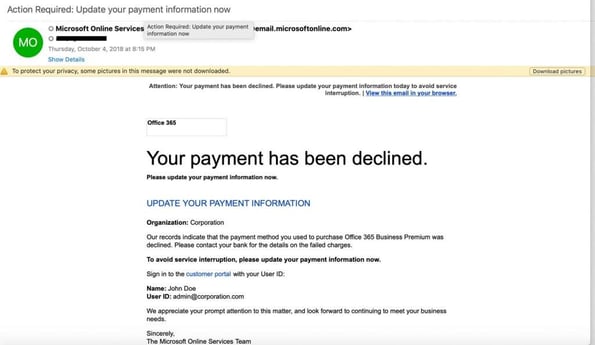
The “Action Required” attack
The message arrives with a subject line indicating that the user must take immediate action, whether to update their account credentials or payment information. Often, this is in the form of a Microsoft account security alert email. The message includes a Microsoft phishing link that is generally hosted on a legitimate although hacked website to bypass reputation-based email filtering systems, such as email fingerprinting.
This is a phishing technique to get you to disclose your Office 365 login credentials. This could be the first step in a multiphase attack, providing the attacker with all they need to begin conducting lateral attacks within your organization using the compromised Office 365 account.
The shared file attack
In a shared-file attack, you receive a file-sharing notification in an email message from a common name, such as “John” or “Julie.” You’re then redirected to a fake OneDrive login page where the phisher then harvests your account credentials. You assume you’ve been logged out. The phisher is counting on you to sleepwalk through your use of Office 365. That way, you won’t question what’s happening.
The phisher may get into attack position by signing up for a free Office 365 trial account. This is fast and easy. Once set up with a trial account, the phisher can access SharePoint and upload malware or credential-grabbing files. He or she shares these files with victims and asks them to “edit” them, then the phisher steals their credentials.

Preventing Office 365 phishing attacks
Office 365 phishing attacks slip past many of the standard security countermeasures offered in Exchange Online Protection (EOP). Two approaches to risk mitigation are working when it comes to Office 365 phishing attacks. One is phishing awareness training.
The more alert and informed your users are about Microsoft phishing, the more likely they will be to spot a phishing attack. Additionally, training shouldn’t be relegated to periodic training sessions or simulated phishing exercises. It should be an automated phishing training solution—when users click on email threats—to make the training more memorable and meaningful.
The second is to add an additional security layer of email security that sits natively inside Office 365 through an API to complement EOP. A native Office 365 solution layers with EOP, rather than sitting outside the architecture like secure email gateways, enabling the API solution to scan internal email to detect insider and multiphase attacks.
A solution that leverages artificial intelligence (AI), including machine learning (ML), uses real-time behavioral analysis to protect from unknown threats, whereas traditional fingerprinting and reputation methods detect only known threats, including bad senders and IPs and known malware.
With this predictive approach, AI-based technologies leverage huge amounts of data to identify abnormal behaviors and inconsistent characteristics in the ways emails are built and sent to identify a potential new threat.
To remain secure, organizations must augment Office 365 security with purpose-built countermeasures while also increasing their employees’ awareness around Microsoft phishing attacks. Together, people and technology form the ultimate barrier.




