Malware Defense: Protect Against Metamorphic and Polymorphic Malware
Adrien Gendre
—August 01, 2017
—5 min read

The threat of a cyber-attack is a serious concern for many organizations. Both huge enterprises and smaller SMBs can become victims of these devastating attacks. Malware is consistently one of the largest cyber threats. Symantec’s 2017 Internet Security Threat Report found that 1 in every 131 emails sent contained malware and there were 357 million new malware variants discovered in 2016.
There were 357 million new malware variants discovered in 2016!
The biggest challenge is that threats are constantly evolving and increasing in number, making it difficult for security solutions to keep up. Malware that evolves in this way is called metamorphic or polymorphic malware. These types of malware are a significant threat to businesses because they are undetectable by the signature-based security systems that most organizations rely upon.
What is Polymorphic Malware and Metamorphic Malware?
Both metamorphic and polymorphic malware are types of malware that slightly change and evolve to slip past security defenses. How they change is what differentiates the two.
Polymorphic Malware
Polymorphic malware is defined by TechTarget as “harmful, destructive, or intrusive computer software such as a virus, worm, Trojan, or spyware that constantly changes, making it difficult to detect with anti-malware programs”. It usually contains two different components, one of which stays the same, while the other changes its code slightly to evade anti-virus solutions. These changes can occur through compression or encryption of the code utilizing different keys. Although the code may look different with each iteration of polymorphic malware, the main function remains the same.
Polymorphic malware makes slight code changes to evade standard signature-based email security systems.

Metamorphic Malware Definition
Metamorphic malware completely rewrites its code with every iteration, making it even harder to detect than polymorphic malware. Similar to polymorphic malware the essential function of the malware remains the same even as the code itself changes. The longer this malware remains in a computer or device the more iterations it creates, each one getting increasingly complicated. This constant change makes it nearly impossible for anti-virus solutions to detect, quarantine, and eliminate.
Metamorphic malware completely rewrites its code with every propagation, making it nearly impressible for anti-virus solutions to detect, quarantine, and eliminate.
Metamorphic malware automatically recodes itself with every propagated distribution, essentially removing any type of signature that traditional systems would look for. It uses a variety of code transformation techniques including:
- Register renaming
- Code permutation
- Code expansion
- Code shrinkage
- Garbage code insertion
Remember Ransomware is Malware
In cybersecurity, ransomware is often touted as the biggest threat to organizations, but remember that ransomware is just a subset of malware.
Ransomware is simply a specific type of malware that, in most cases, locks users out of their devices and demands ransom payments to return their data. Other types of malware include:
- Spyware
- Virus
- Worm
- Adware
- Rootkit
- Trojan
- Crime ware
- Keystroke logging
Ransomware is just one specific type of malware.
So everything we just said about metamorphic and polymorphic malware also applies to metamorphic and polymorphic ransomware.
Metamorphic and Polymorphic Malware Families
With consistent functionalities regardless of code, malware is often grouped into families so security teams can look for similar functions and code segments in efforts to protect their organizations. Some of the most well-known malware families include:
Locky
Locky is delivered to victims in unsuspecting .doc file attachments often disguised as an invoice, resume, receipt, or other business documents. The .doc file is filled with scrambled text that are actually macros (single coding instructions that automatically expand to perform a specific task). Users are instructed to enable macro settings to “unscramble the text” but instead, the macros automatically download the malicious software, which then starts encrypting files. Back in May, a variant of this malware, called Jaff, made headlines during a worldwide 99 country infection.
Locky malware utilizes macro laden .doc files to permeate computer drives and begin file encryption.
CryptoLocker
This polymorphic malware targets computers running Windows and is delivered through ZIP files. The ZIP file contains an executable file that is disguised with a PDF icon. Once the file is opened the payload installs itself into the profile folder and adds a registry key that prompts it to run at computer startup. Once this process is completed it contacts the command server, which generates a 2048-bit RSA key repair and is sent back to the computer. Local and accessible files with certain extensions (including CAD files, Office docs, etc.) are encrypted.
Cerber
This malware is traditionally delivered through malicious links in phishing emails but uses a variety of delivery tactics making to particularly difficult to track. It is utilized in the ransomware-as-a-service (RaaS) model, making it easy for non-technical cybercriminals to make some money. This polymorphic malware can encrypt a range of file types and has been known to encrypt individual machines as well as entire enterprise databases. Plus, there has been a consistent trend of Cerber specifically targeting Office 365 users.
Cerber is regularly utilized in the ransomware-as-a-service model, providing everyone with the tools they need to become a cybercriminal and make some money.
Crysis
Once installed, Crysis encrypts all the files on the initial device and then propagates to other removable and network drives. This quick infiltration throughout an entire organization makes this malware particularly devastating. It works by exploiting remote desktop protocols (RDPs), which provides hackers with the opportunity to utilize privileged escalation techniques to gain administrative access and permeate more servers and devices.
Kelihos Botnet
Also known as Hlux, this botnet is known for sending massive amounts of spam emails (up to 4 billion messages per day) and stealing bitcoins. It uses a peer-to-peer server method, meaning each botnet node is able to act as the command center for the entire botnet. With traditional botnets, nodes receive instructions from a set of servers and if any of those are taken down then the botnet will shut down. By utilizing the peer-to-peer method, this botnet is able to continue to function even if one of the servers is shut down.
The Kelihos Botnet uses a peer-to-peer server method allowing it to continue to propagate even if one of the servers is shut down.
CryptXXX
More recently recognized as WannaCry, this malware made headlines in May after worldwide attacks shut down business operations across Europe. This malware was the result of hacker group the “Shadow Brokers” exposing a major Windows vulnerability in conjunction with a list of cyber espionage tools previously used by the NSA to spy on individuals. It propagates via an SMB v1 (Server Message Block) vulnerability that allows users to share resources over a network, like files and printers, allowing it to quickly spread throughout entire organizations.
Petya
Petya polymorphic malware has been making news headlines since its major worldwide attack at the end of June. This software propagates via EnternalBlue (an SMBv1 exploit), PsExec (an administration tool that allows commands to be executed on remote systems), and WMI (Windows Management Instrumentation – another remote tool). Although initially thought to be part of the CryptXXX family this malware arrived in multiple waves using different delivery tactics each time.
Petya polymorphic malware uses a range of Windows exploits and was the force behind the worldwide attack that occurred in late June.
The best malware defense? Predictive Email Security.
Given that 91% of all malware is delivered via email, the best way to protect your organization is to seal off this critical attack vector. 
The vast majority of email security are all essentially signature-based email security systems. That’s problematic, because signature-based systems rely on code signatures to block malware… but with the constant evolution of malware variants, these systems can’t defend against new variants until some victims have already been infected and the new variant is identified and added to the black list. It’s a never-ending game of whack-a-mole with the inevitable losers facing ransomware extortion, data breaches, or worse.
To defend against polymorphic and metamorphic malware, your organization needs predictive email defense that protects against both known and unknown malware variants.
Signature-based can only defend against known malware, leaving you vulnerable to all polymorphic malware variants.
Vade provides advanced comprehensive email security that utilizes artificial intelligence (AI) and data from a global 24/7 threat detection center. This allows us to defend against all email threats, including polymorphic and metamorphic malware variations from these families. We use multiple layers of analysis to determine the safety of emails before they end up in your employees’ inboxes.
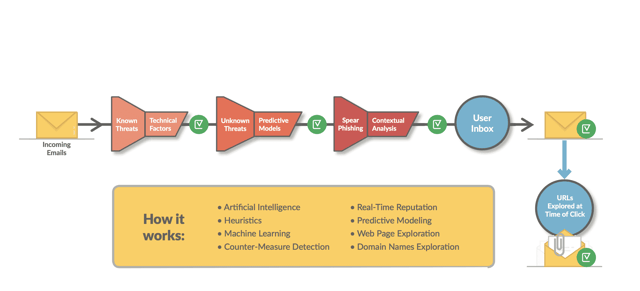
The Vade solution utilizes artificial intelligence and data from our 24/7 global threat detection center to protect against all types of threats including polymorphic malware variants, ransomware, spear phishing, and other zero-day attacks.
Want to learn more about how our advanced predictive email security solution can protect against polymorphic malware? Contact us for a demo or proof of concept.



