What is Spear Phishing?
Quick and to the point, spear phishing emails are easy to create and hard to spot. Learn why they’re so effective and how to protect your business.

What is spear phishing ?
A form of social engineering, spear phishing is a malicious email that impersonates an individual for the purpose of tricking a recipient into completing a desired action—typically financial in nature. Often, a hacker will impersonate a victim’s acquaintances, such as colleagues, executives, clients, or vendors.
The continuum of email spoofing
To trick recipients into thinking they’re reading an email from a trusted sender, spear phishers use a technique called “spoofing” that allows them to impersonate a legitimate sender and email address. There are three primary methods of email spoofing :
Display Name Spoofing
Display name spoofing impersonates the sender’s name but not the email address. This is effective because many users will trust the sender immediately upon seeing the name. It’s also effective because many email clients, especially on mobile, show only the sender’s name but not the email address.
Domain spoofing
This method is more sophisticated than display name spoofing but also easier to detect by SPF (Secure Policy Framework), DMARC (Domain Message Authentication Reporting), and DKIM (Domain Keys Identified Email). With domain spoofing, a spear phisher can specify the email address they want to spoof. When an email address is an exact replica of a trusted sender, users are unlikely to recognize that the email is spoofed.
Cousin Domain
A close cousin email address is nearly identical to a legitimate one, with only a slight modification. In the past, close cousin spoofing attempts were more obvious, such as mIcrosoft.com instead of microsoft.com. Today, attempts are more advanced and difficult to spot, such as user@mycompanyltd.com instead of user@mycompany.com. These subtle changes can be extremely difficult to spot for busy staff who quickly read and respond to emails, especially when they are urgent in nature. Moreover, DMARC and SPF are ineffective against close cousins because they only protect exact domains.
Spear phishing vs phishing
Spear phishing and phishing attacks both leverage impersonation to commit fraud. The difference between the two is that spear phishing emails impersonate people, while phishing emails impersonate brands. Unlike phishing, spear phishing targets a single individual, includes no links or attachments in the email, and typically features a request for a wire transfer, gift cards, or direct deposit change, rather than account credentials. Below are just two examples of a phishing vs spear phishing email:
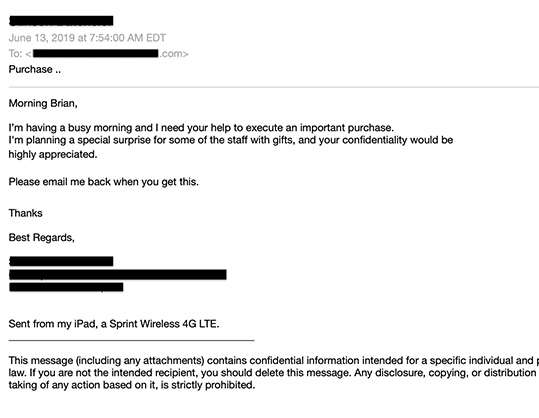

Phishing/social engineering accounted for 52% of cyberattacks against SMBs in 2018 - Keeper/Ponemon

Spear Phishing Examples
There is no shortage of ways to trick people into giving up sensitive data and credentials. However, there are some well-honed attacks that spear phishers turn to time and again.
- Direct Deposit Changes
In one version of this scam, a hacker posing as an employee sends an email to an HR assistant, requesting to change their bank account for their payroll direct deposit. In another version, a hacker posing as a vendor emails a staff member in accounting, informing them that the company’s bank account and routing number has changed, and future payments should be sent to the new account. - Gift Card Requests
Posing as an executive, a hacker asks an employee to purchase multiple gift cards and send them the codes on the back of the cards. Often, a hacker will say that they’re in a meeting or away from their office. This adds to the believability of an executive writing an email from a personal email address, such as Gmail or Yahoo. - W-2 Spear Phishing
A spear phisher posing as an executive emails a staff member in the HR department, requesting employee W-2s, a US tax form reflecting employee earnings and tax deductions. Tax time is particularly stressful for accounting and HR departments, and the pressure, in addition to the time constraints, makes them vulnerable to making the mistake of falling for this type of attack. - Multiphase Attacks
A common method for hacking into Microsoft 365, multiphase attacks begin with phishing and evolve into spear phishing. A hacker sends a phishing email to an employee, impersonating Microsoft. The victim unknowingly gives up their Microsoft 365 login credentials on a phishing page. Armed with the victim’s username and password, the hacker enters the business’s Office 365 ecosystem where they launch spear phishing attacks using legitimate Microsoft 365 email addresses. - Wire Transfer Requests
Also known as business email compromise (BEC), this spear phishing variant is one of the most costly. A hacker posing as a top executive makes a request for funds in the form of a wire transfer. In many high-profile cases, businesses were completely unaware that millions of dollars had been sent to fraudulent bank accounts.
Spear Phishing Techniques
A one-off, text-only spear phishing email might look unsophisticated on the surface, but there are social engineering techniques at work that reveal a sophisticated level of psychological manipulation. Below are some examples :
Engaging in pretexting
- Spear phishers prime their victims by first sending a friendly email and engaging in small talk, such as “how was your vacation?” or “congrats on the promotion.” This lowers the victim’s guard, prepping them for the spear phisher’s eventual request, which might not come for several more emails.
Making urgent requests
- Often, spear phishers will convince their victims that they have only hours—or even minutes—to send a wire transfer, change their bank account information, or purchase gift cards for clients..
Sending emails via mobile :
- Spear phishers posing as executives often claim to be out of the office, even out of the country, and urgently need the victim’s help. Adding “sent from my iPad, iPhone, or Android device” adds to the believability of such a claim and also excuses mistakes in the email, such as typos. It also creates an excuse for using a non-corporate email address like Gmail.

Spear Phishing Prevention
The absence of URLs and attachments makes spear phishing extremely difficult to detect. Traditional email security solutions use outdated methods to block threats, and most are ineffective in the fight against spear phishing. Optimal spear phishing protection requires advanced methods.
Traditional Email Defense
- Reputation
Reputation-based threat detection blocks known, malicious email senders (IP addresses) and phishing URLs. A reputation-based filter will block bad senders known to the filter but will miss new threats.
- Signature (Fingerprint) :
Signature-based threat detection blocks threats with a known “signature,” such as malware code.
- Sandboxing
Sandboxing sends suspicious emails to a controlled environment for analysis. It’s ineffective against spear phishing emails that do not include attachments or links.
- Secure Email Gateways :
Secure email gateways (SEG) rely on reputation and signature-based detection. A SEG sits outside of Microsoft 365 architecture, disabling Exchange Online Protection (EOP) and leaving Microsoft 365 unprotected against insider attacks.
Predictive defense
With predictive defense, artificial intelligence (AI), including a combination of supervised and unsupervised machine learning models, work together to identify the telltale and difficult-to-detect signs of spear phishing :
- Supervised Learning :
Algorithms are trained with malicious and legitimate and emails to recognize specific features of spear phishing emails, such as mobile signatures and email addresses from public domains.
- Unsupervised Learning :
Natural Language Processing and Unsupervised Anomaly Detection recognize abusive patterns in spear phishing emails, including urgency, flag words, and email addresses that do not match senders in a business’s entity model.
- User Feedback Loops :
Users report spear phishing emails to the security operations team (SOC), which analyzes the email and improves the algorithms.
Vade for M365
Vade for M365 blocks advanced attacks from the first email thanks to machine learning models that perform real-time behavioral analysis of the entire phishing email, including any URLs and attachments. Leveraging data from more than 1.4 billion inboxes, our AI-based threat detection stops threats before, during, and even after phishing attacks.

