The Evolution of Sextortion Emails
Adrien Gendre
—April 23, 2020
—3 min read

Image Credit: Dado Ruvic, Reuters
There were 43,101 reports of digital extortion in the US alone in 2019, resulting in $107,498,956 in losses, according to the FBI. However, despite the global rise in sextortion, neither sextortion the crime nor the volume of sextortion emails received are formally tracked by any official criminal justice organization. What is known is that sextortion has evolved from one-off, low-tech scams to sophisticated, highly targeted attacks designed to break through email filters.
The continuum of sextortion
Sextortion emails extort victims by threatening to release compromising photos and videos of a sexual nature. In some cases, sextortion is a highly personal attack. Hackers pose as suitors on social media sites with the goal of coaxing victims, often children, into sharing compromising images. Once the victim agrees, the extortion demand is made.
The mere suggestion that a cybercriminal is in possession of these materials is often enough to evoke fear in the user, resulting in an extortion payment. Often, cybercriminals will claim to have infected the victim’s computer with malware and obtained the compromising images—usually webcam footage—over the course of the infection. In most cases of sextortion, however, hackers possess no such sensitive information.
The rise of high-tech sextortion emails
Just as sextortion types have evolved, so too have sextortion emails, including the level of sophistication. In the past, the emails were sent in high volumes, with mass waves sending clear signals to email filters that something was awry. Hastily detected and blocked, these emails also typically featured links to Bitcoin sites, the URLs providing yet another “signature” for email filters to recognize. As sextortion scams became more difficult to pull off, hackers became more creative. Now, we’re seeing a host of new techniques that are succeeding.
Using text-based images
The first sextortion emails were text only, but as filters got better at identifying keywords common in sextortion, hackers changed their methods. Text-based images have emerged as a particularly difficult to detect method of bypassing filters. In the below example of a sextortion email, the text is not part of the email body—it’s an image-as-text attachment.

We’re also seeing text-based images in brand phishing campaigns. In the example below, the image itself links to the phishing page.
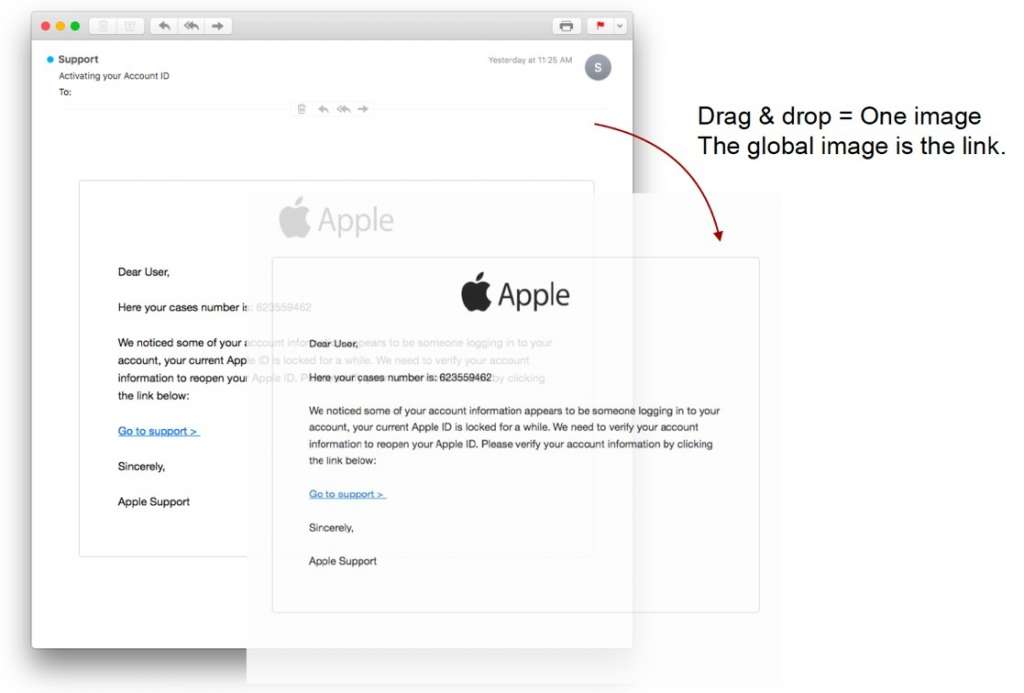
The above examples point to the emergence of image manipulation in email threats, particularly phishing and sextortion. Email filters scanning for signatures like URLs and malware code cannot see images.
Using the above techniques, hackers can send the same sextortion or phishing email dozens, even hundreds of times. If the email is blacklisted, the hacker can simply distort the image slightly, and the email filter will no longer recognize the threat.
Use of text-based images highlights the need for image detection in addition to standard URL and content scanning. Unlike Machine Learning algorithms that analyze text, Deep Learning algorithms with Computer Vision analyze images, recognizing subtle changes to color, tone, and size—features that hackers distort to bypass signature scanning technologies.
Hiding URLs and QR codes in attachments
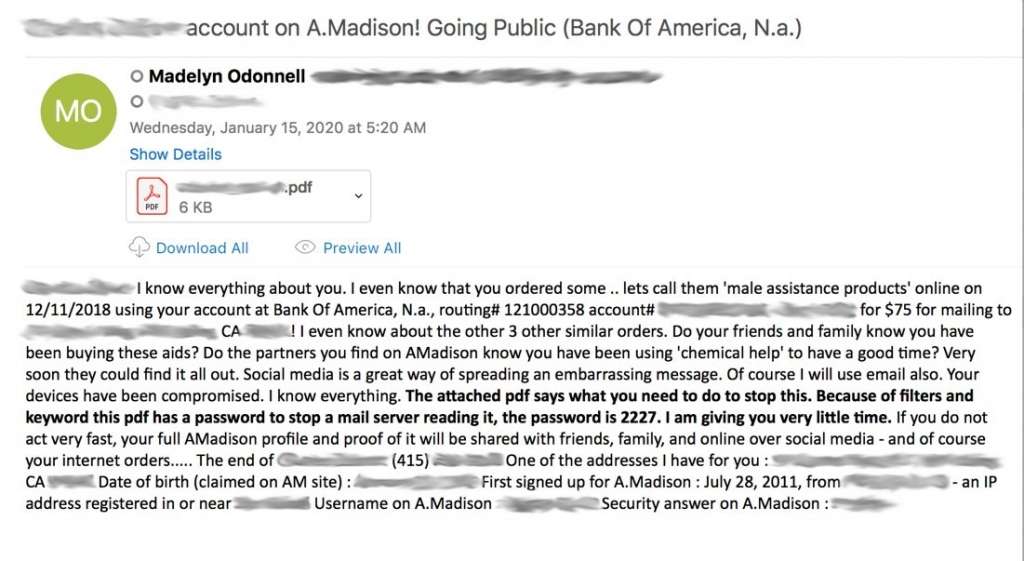
While Bitcoin URLs are still prevalent in sextortion emails, they’re easily detected by email filters looking for signatures. Fully aware of this, hackers have shifted to using QR codes, which cannot be parsed by many filters. Below is a recent example of an Ashley Madison sextortion email in which the QR code is hidden in an attached PDF file.

In the below example, the sextortion email contains only an attachment. For email filters that scan for malicious content but cannot parse PDFs, the email could appear harmless. Attachments are also being used to spread malware as phase one in sextortion campaigns. The malware download allows the hacker to take control of a computer, including a webcam, which provides the blackmail content for the eventual sextortion email.
Capitalizing on current events
Data breaches are the ultimate source of ammunition for both phishing and sextortion campaigns. While hackers have always flaunted usernames and passwords as proof they had compromising information on their victims, they’ve found creative ways to touch another nerve by contextualizing their attacks around current events.
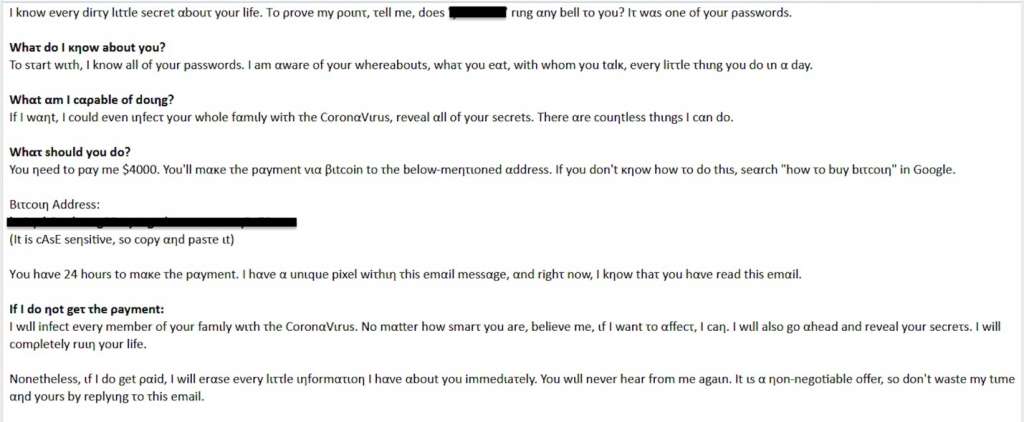
In below example, the hacker flaunts the victim’s password and threatens to infect the victim’s family with the coronavirus. Note that the hacker also uses Cyrillic characters throughout the message to bypass detection by an email filter.
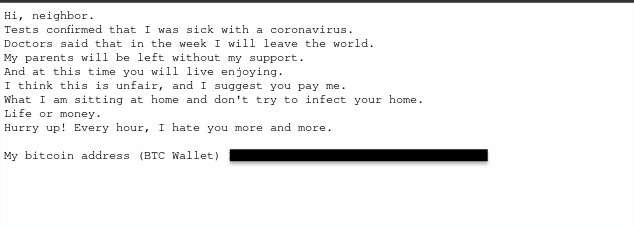
Threats like these began appearing almost immediately in the wake of the COVID-19 pandemic. With a current event of this scale and people across the globe experiencing collective anxiety and economic hardship, it’s not surprising that hackers set out to capitalize on the situation. We see similar event-based email attacks during the holiday season and in the weeks leading up to major sporting events.
Hacking IoT products
In one particularly creative sextortion campaign detected by Vade in 2018, hackers sent sextortion emails via hacked IoT products. Using a command line in the products’ Linux operating systems, hackers were able to deliver the emails without the use of webmail clients.
Over a period of three months, Vade detected 600,000 of these emails, many of them sent from auto-generated Hotmail and Outlook email addresses.
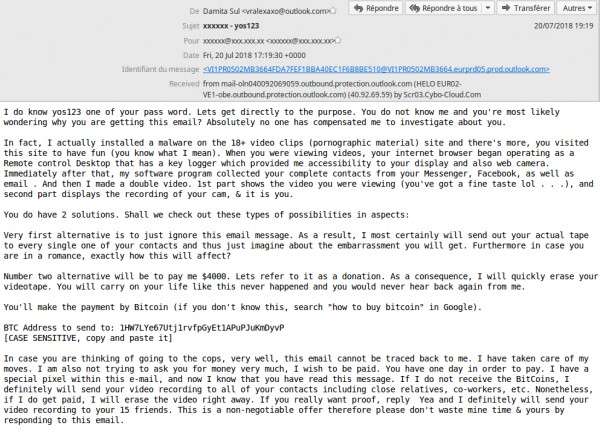
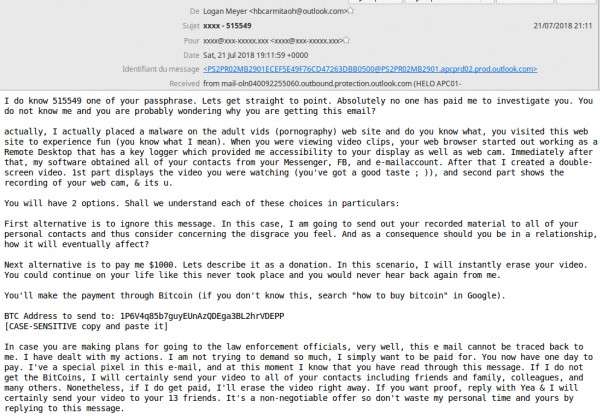
Adapting to the changes
Hackers are well educated on the systems they’re trying to breach. More than ever, they adapt their campaigns to bypass the email filters trying to stop them. Both sextortion and phishing campaigns tend to be sent in waves—when one fails another emerges. Each time a threat is blocked, hackers develop new methods of bypassing the filters that blocked them.
To keep up with the latest threats, technology must also adapt. The emergence of AI in email security has opened new possibilities in threat detection. With a combination of Machine Learning and Deep Learning algorithms, AI-based email security can detect the signature-bypassing methods hackers use to deliver sextortion emails.



