Why It’s So Hard to Spot a Spoofed Email
Adrien Gendre
—June 11, 2020
—3 min read

Email spoofing is single most common feature between phishing and spear phishing emails. The methods hackers use to impersonate email addresses is growing in sophistication, stumping email filters and users alike. With slight variations on company names and nearly invisible text changes, a spoofed email can be extremely difficult to spot. Here are just a few reasons users don’t catch them.
Display name spoofing is deceptively simple
Display name spoofing is one of the most common forms of spoofing. It’s also relatively easy to do but difficult for users to spot and email filters to catch. Here’s how it works.
The sender field of an email shows both the sender’s name and their email address. In Microsoft Outlook, an email address is surrounded by angle brackets (< >). Instead of attempting to spoof the exact domain, which is difficult to get past an email filter because of DMARC, hackers use a sender name and email address in the display field that looks legitimate.
In the below example, the hacker uses a spoofed SharePoint email address in the display name field:

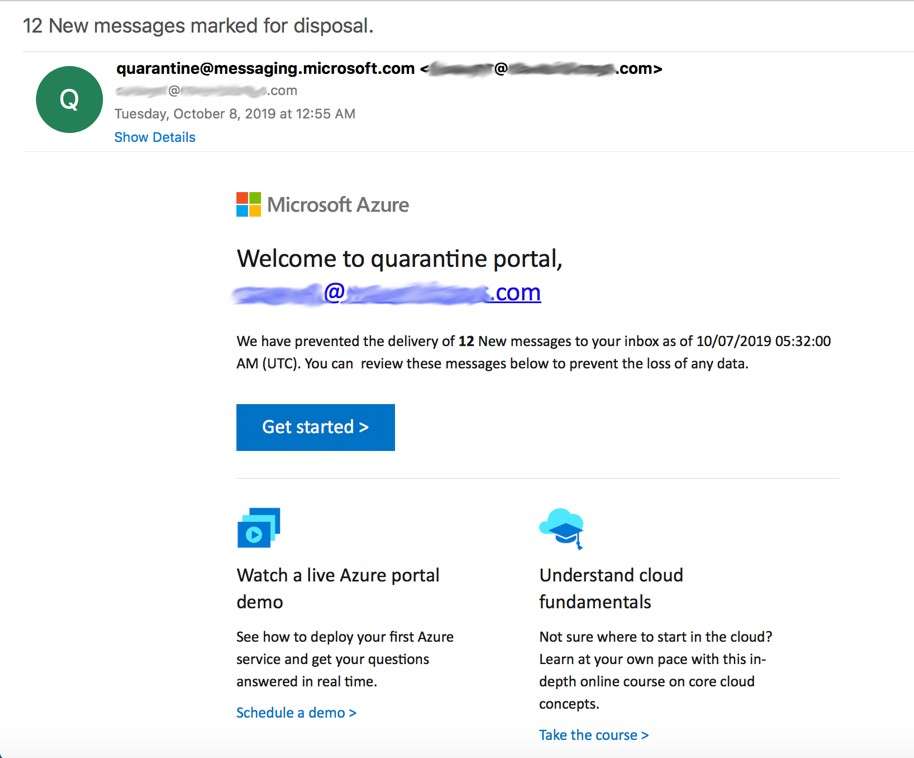
In the below example of display name spoofing, the hacker used a fake Microsoft email address in the sender field, instead of the brand name. What’s clever about this display name is that the keyword “quarantine” in the spoofed email address matches the message of the email—a common trick in display name spoofing. This could make the email itself seem more believable in the eyes of the user, who might also overlook the oddity of an email address appearing in the sender field.
Notice that the hacker didn’t bother creating a spoofed email address in the email field, which we’ve blurred. This is common in display name spoofing. Either the hacker couldn’t be bothered to do so or they were hoping the user would focus on the display name and not the email address. Another possibility is that the hacker was hoping a user would view the email on a mobile device. This is optimal for the hacker because email addresses in Outlook mobile are hidden unless expanded.
Cousin domains are nearly impossible to see
Americans spend an average of three hours per day checking work email. In the UK, it's closer to two hours per day. Users are so inundated with email that the chances of users scrutinizing email addresses for signs of spoofing is unlikely. This is why cousin domains are so effective.
A cousin domain, also known as a look-alike domain, is not an exact replica of a legitimate email address but a variation on an email address that can be nearly impossible for the naked eye to see—at least at first glance. There are three main tricks used in cousin domain spoofing that we see:
1. Cyrillic characters: With around 133,000 characters available in 139 languages and scripts, Unicode is a common spoofing tool for hackers, and Cyrillic characters are among the most popular and effective. To create a cousin domain of a brand domain, such as microsoft.com, hackers will replace a Latin character, such as “o,” with its Cyrillic look-alike “о”. The result? Micrоsоft.cоm. The Cyrillic “o” is invisible to the naked eye and difficult for email filters, which struggle with Unicode, to detect.
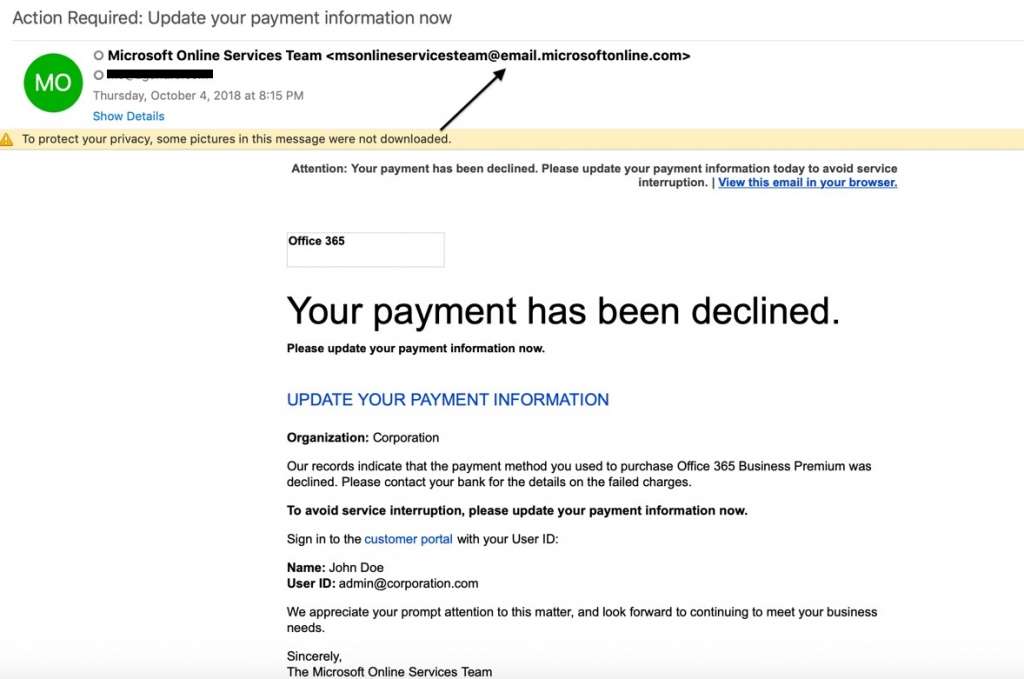
2. Extensions: Using random domain extensions and additional sections and subdomains to the URL is a common method of creating cousin domains. They meld with the surrounding text and are difficult to see if you’re not scrutinizing the email.
Additionally, because many phishing emails are disguised as security alerts and other notification-type emails, users expect the email addresses to be different from other communications with the known brand. .exe, .ca, .co, .company, and email are all common extensions used in cousin domains.
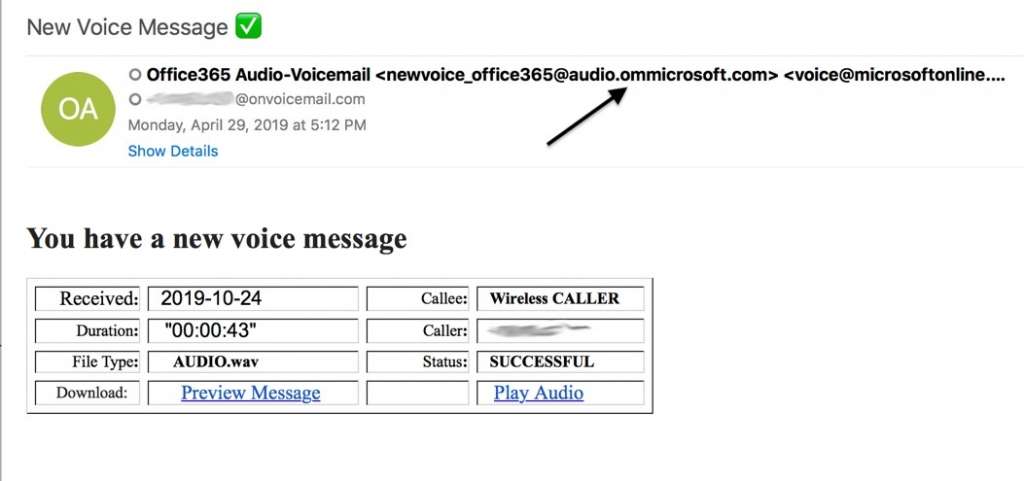
3. Additional/fewer characters: Adding or subtracting a single character from an email address is another simple but effective method used in cousin domains. While some are poorly executed and blatantly obvious, others are better designed and more difficult to spot. Random capitalization is also common and difficult to spot if not scrutinized.
Spoofed emails and spear phishing
Spear phishing is particularly difficult to spot because it involves impersonating people, not brands. Because of this, the emails are simpler and include few visual components and cues. Low quality phishing emails often include obvious signs of email spoofing and poorly designed graphics. Spear phishing emails, however, typically include only text.
The below spear phishing email features a cousin domain with the extension “global”. This personalized email is purportedly sent from an employee requesting a supplier payment.

When an email is sent from a person, the recipient often disregards the email address and instead focuses on the display name. If it is someone they recognize, and especially if they aren’t trained to spot spear phishing, they tend to trust that the email is legitimate.
Stopping spoofed emails
DMARC is the standard in spoofing protection, but it’s limited to blocking exact domain spoofing and doesn’t have an answer for cousin domains and display name spoofing. Despite its limitations, DMARC is effective at stopping certain types of spoofed emails and protecting your own domain’s reputation.
Ultimately, DMARC should be layered with other anti-spoofing technologies that use artificial intelligence, including machine learning and natural language processing, to block phishing and spear phishing emails. Tactics like using Cyrillic characters and extensions, and making other slight modifications to domains are difficult to detect, requiring behavioral analysis of the email to catch these and other anomalies, both in email traffic and in email addresses.



