Email Threat Intelligence
Threat Intel & Investigation provides the integrations, intel, and tools to investigate and respond to email-borne threats transiting through your networks.
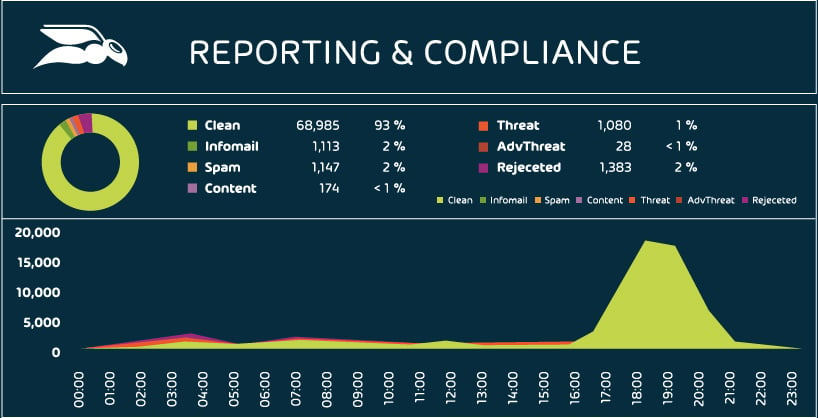
Unify disparate email security data
Threat Intel & Investigation provides the email threat intelligence that SOCs need to gather forensic evidence, cross-check threats across their networks, trigger automation playbooks, and develop incident response processes.
Investigate and respond
There’s more to email than text and images. Underneath the hood, they feature critical metadata and code that reveal their true intent and potential payload. Threat Intel & Investigation gives you access to Vade’s filtering technology to conduct a forensic analysis of email headers, metadata, objects, URLs, attachments, and more.
Investigate and remediate user-reported emails
Emails reported as either phishing or spam by end users via the Outlook or Gmail add-in must be reviewed by admins so they can be quickly triaged and remediated. Vade aggregates user-reported emails in a single interface in Vade for M365 and Vade for Google Workspace. Sets alerts for user-reported emails and remediate a single reported email or a group of similar, unreported emails from one central location—with just a few clicks.
Features
Inject email and event logs
into any SIEM, XDR, or EDR for improved threat intelligence, investigation and response.
Deconstruct files and attachments
to collect forensic evidence of malware and phishing—without exposing administrators to risk.
Triage and remediate
user-reported emails and similar unreported email clusters. Set alerts and never miss a user report.
Add-On for Splunk
Integrate Vade for M365 or Vade for Google Workspace email logs with Splunk without the need for custom software development.
THREAT INTEL & INVESTIGATION
Benefits
- Integrates email into your XDR strategy
- Unifies disparate email data
- Improves threat intelligence and visibility
- Improves SOC perimeter
- Integrates email into defensive posture
- Decreases time to respond to events
Threat Intel & investigation
Powerful M-SOAR capabilities
It takes only one malicious email to halt operations. Combining Threat Intel & Investigation with Vade for M365 or Vade for Google Workspace offers Mail Security Orchestration and Automated Response (M-SOAR) capabilities that empower your SOC or IT team with the email threat intelligence to respond quickly to phishing, spear phishing, and malware attacks.