Announcing File Inspector for Threat Intel & Investigation
Natalie Petitto
—February 09, 2022
—1 min read

The latest feature for the beta of Threat Intel & Investigation is now live in Vade for M365. Vade partners and customers who are using the beta have full access to the new release.
What’s in the latest release?
The latest release includes a new feature that allows you and your team to use Vade for M365 email data to conduct threat investigations across your networks. Combined with the Log Export feature included in Threat Intel & Investigation, which allows you to export your Vade for M365 email logs to any SIEM, XDR, or EDR, the latest feature enables you to fully integrate email into your XDR strategy.
Say hello to File Inspector
Powered by Vade’s PDF and Microsoft Office parsers, File Inspector reveals details about malicious characteristics and elements of PDF and Microsoft Office files and attachments, including:
- Hash
- Extensions
- URLs
- Images
- Objects
- Scripts
- Embedded files
You can also analyze suspicious files that originated outside of email by uploading files to File Inspector from the Toolbox in your Vade for M365 menu. Accepted file types include PDF, doc, docx, xls, xlsx, ppt, and pptx.
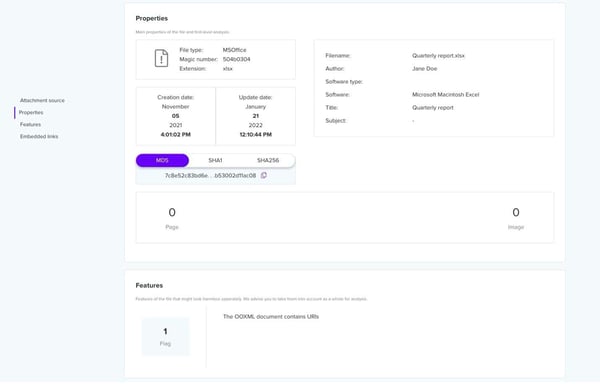
Evidence collected by File Inspector’s file and attachment analysis can be used to cross-check threats, including malware code and suspicious links, and determine whether they have spread to other areas of a network.
Threat Intel & Investigation will continue to evolve with new features, so stay tuned for the latest updates. File Inspector is available to all beta users of Threat Intel & Investigation. To learn more about Vade for M365 and Threat Intel & Investigation, you can request a demo below.



