Data Theft and the Nefarious Market for Stolen Information
Vade Experts
—February 13, 2024
—3 min read

Data has become every organization’s most prized asset. It’s also emerged as their single greatest liability. Data theft, or the unauthorized extraction of information, presents big risks to companies of all sizes. From hefty financial losses to significant disruptions and downtime, lawsuits and regulatory fines, the consequences of data theft can be crippling. But they’re not only an organizational problem—they affect an ecosystem of stakeholders that includes consumers.
In this post, Vade threat analysts take you behind the scenes to explore how personal records are marketed and leaked by nefarious actors.
Data breach: the precursor to data theft
Naturally, data theft follows a data breach. A data breach is when confidential information is accessed and retrieved by a third party without authorization. Data breaches often occur after hackers compromise an account and gain entry to a protected network.
According to IBM’s Cost of a Data Breach Report 2023, the cost and frequency of data breaches have surpassed historic markers, ushering intended victims into a new age. The global average cost of a data breach reached $4.45 million (USD) in 2023, beating any other year on record. Among the initial attack vectors used to facilitate a breach, phishing carried the highest price tag and cost victims an average of $4.9 million over this period. And large enterprises weren’t the only companies targeted.
For organizations with 500 or fewer employees, the average cost of a data breach rose by 13.4% year-over-year (YoY) in 2023 to reach $3.31 million (USD).
For consumers, the downstream impact of these events was particularly hard felt. Corporate and institutional data breaches victimized more than 360 million people through the first eight months of 2023, according to a recent report from Apple. Russia accounted for the highest number of estimated breached accounts with 49 per 1000 people, followed by France (25), and the US (24).
According to IBM, healthcare data breaches are the costliest kind for organizations and consumers, averaging nearly $11 million per organization. In Q3 2023 alone, data breaches led to leaks of more than 6.4 million records health records globally.
Data leaks: The common outcome of data theft
Data leaks, or the unauthorized sharing of stolen information on public or private networks, is a typical afterlife of stolen data.
And data leaks are surprisingly easy to discover.
A simple Internet search of “leaks” can allow anyone to locate stolen records for sale. While that spells danger for potential victims, new malicious tools are making it easier than ever for hackers to find sensitive information.
Vade researchers recently uncovered a Telegram channel that sends hackers a feed of leaks from the latest data breaches. This provides hackers with convenient and timely access to every leak via a direct link.
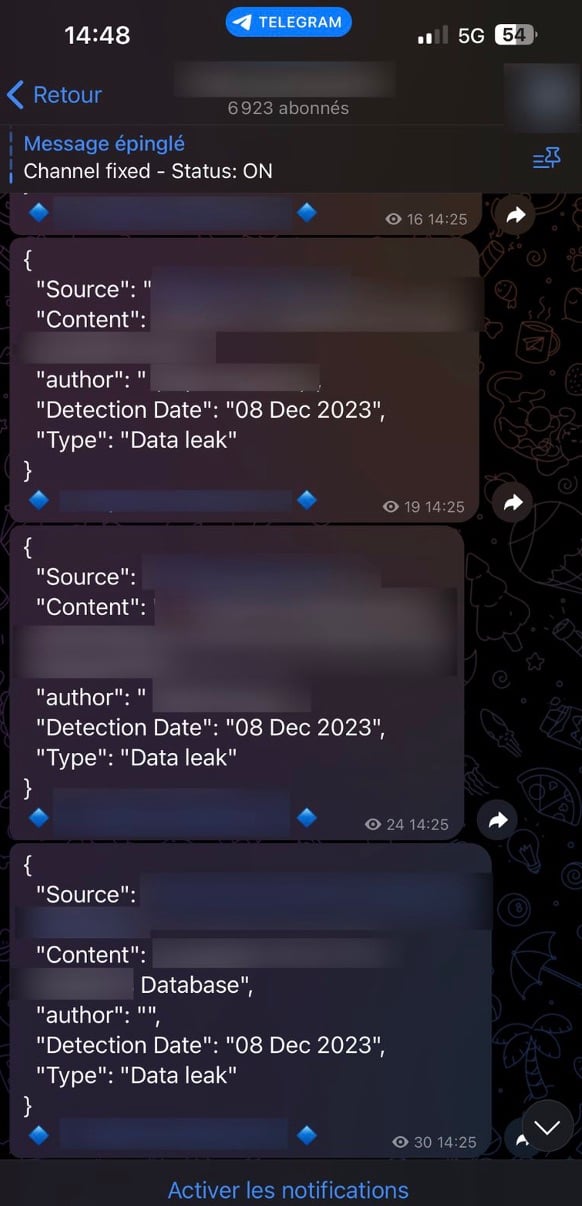
Automated leak Telegram channel
At the same time, Internet forums provide free and paid access to data leaks. The images below show data leaks for three organizations in Mexico and France.
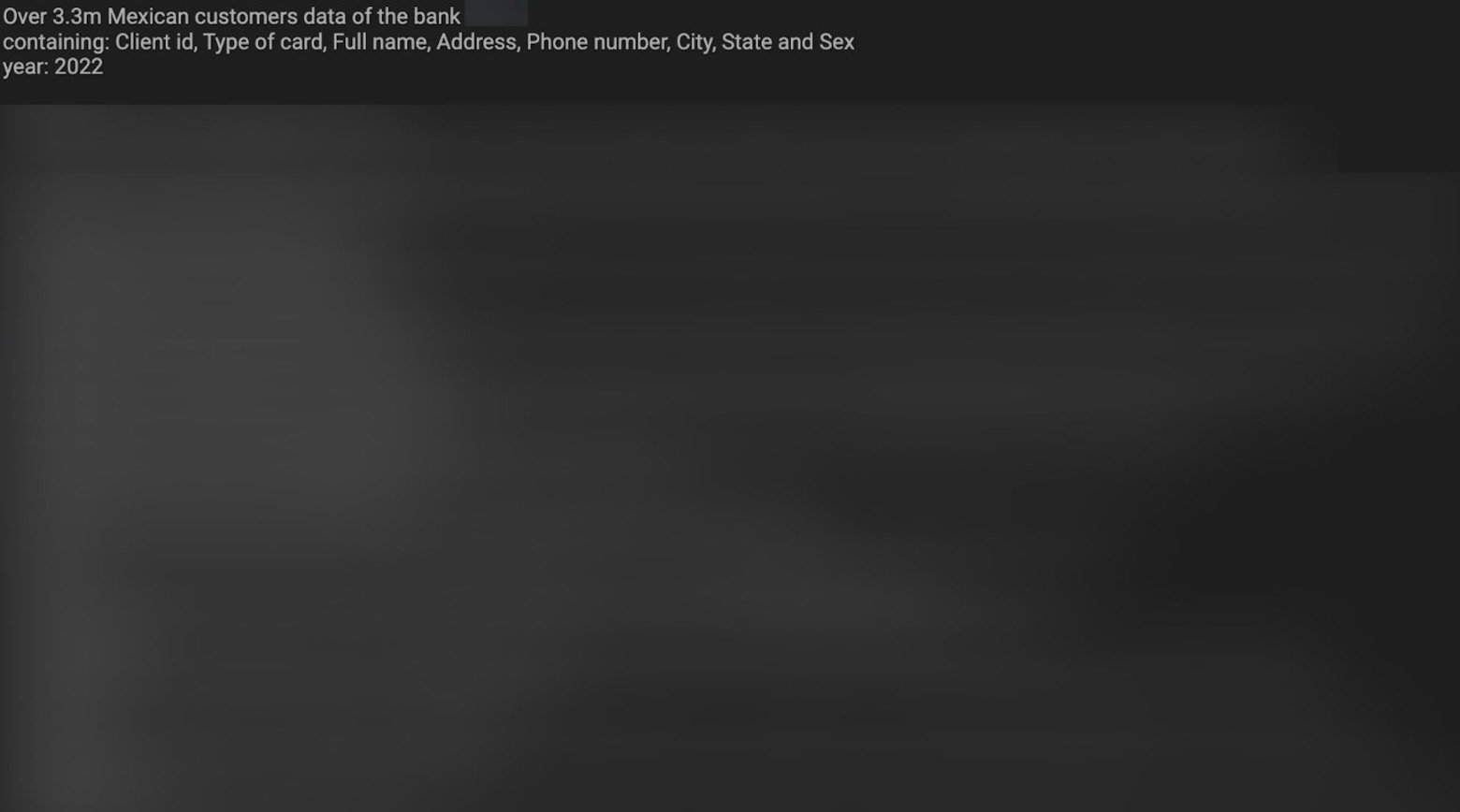
Mexican bank data leak
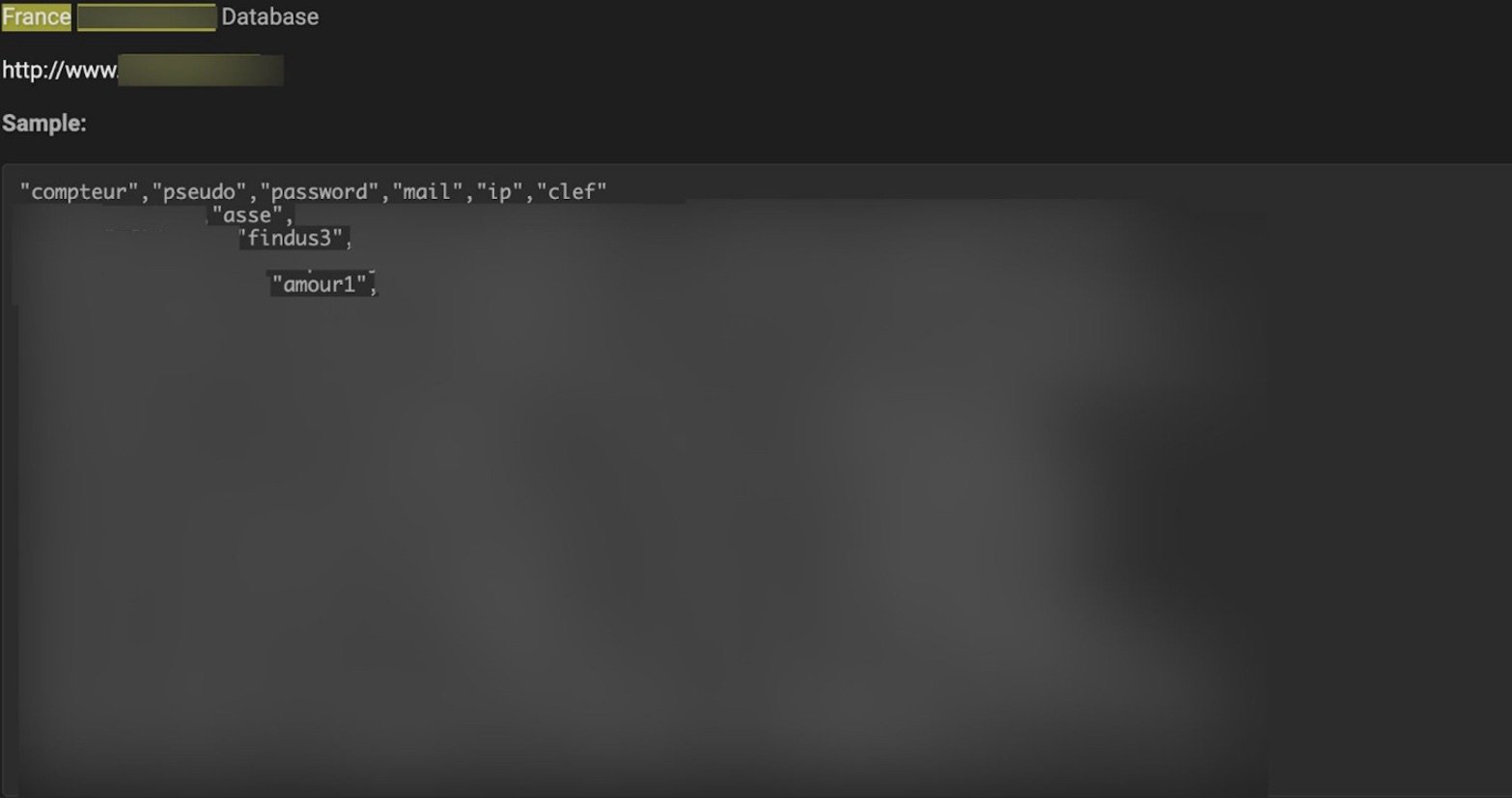
French company data leak
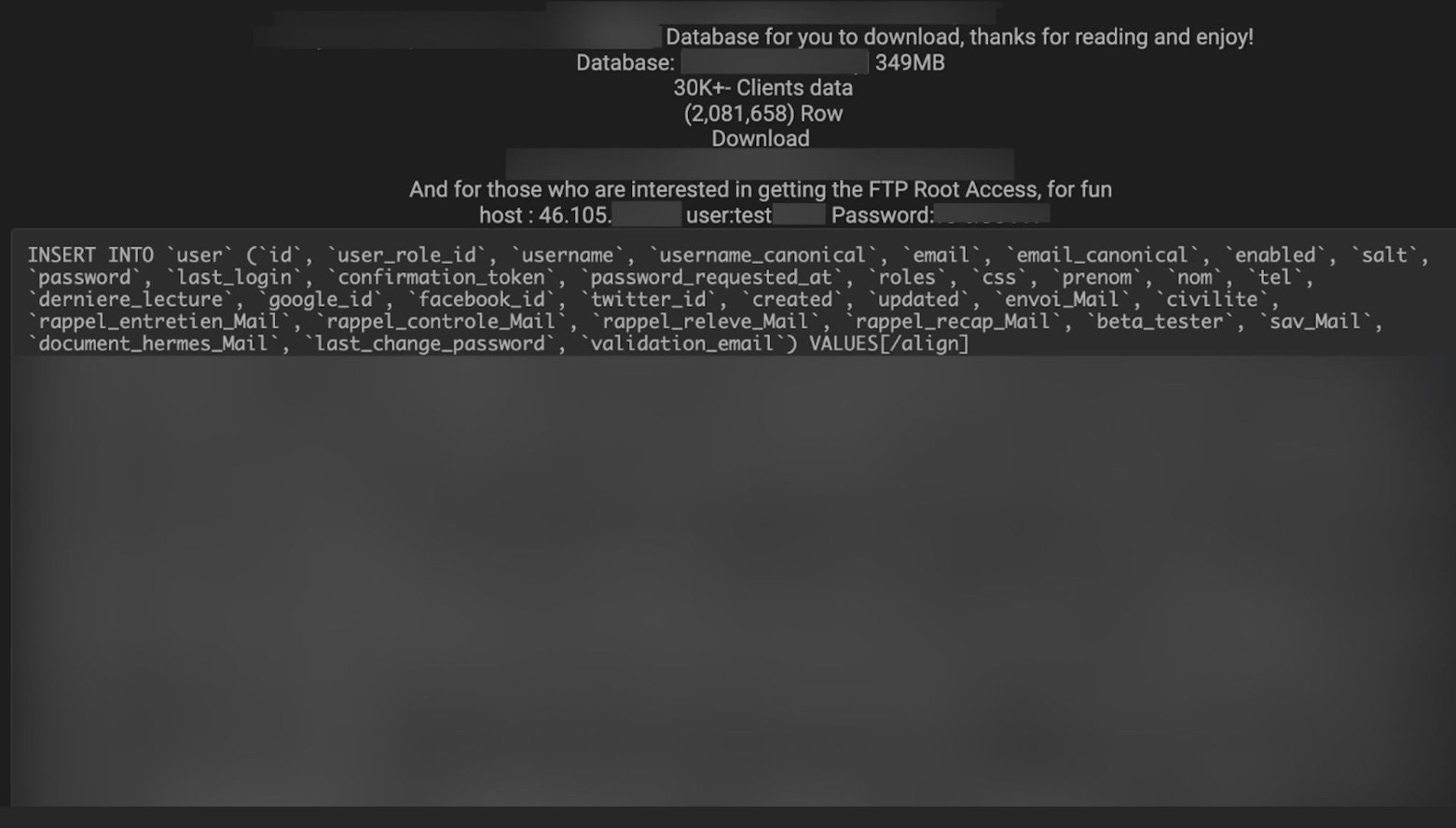
French company data leak
As these examples show, hackers need not travel to the Darknet to acquire stolen data. They simply need to use the tools readily available to anyone with access to a laptop and Internet connection.
Data leaks: When scammers get scammed
Data leaks have become a lucrative business for malicious actors. So lucrative, in fact, that it’s not uncommon for hackers to attempt to scam their peers. While the sale of real stolen data remains commonplace among the dark corners of the Internet, the same is true of fabricated records.
A recent case involving Europcar provides evidence. Hackers published an ad on a data leak site, where they claimed to have stolen the personal information of 50 million of the company’s customers. They included a sample as proof of their claim. According to Europcar, the data breach turned out to be a sham. The company claimed that the sample data didn’t match any of its customer records and at least some of the personal information was fabricated. Some customer addresses and zip codes didn’t exist, for example.
While it’s not clear how the records were produced in this case, there are numerous methods hackers can use to create fake data. That includes exploiting the tools used by software developers to generate large and relevant data sets, which they use for legitimate application testing. It may also include the use of generative AI, which could theoretically produce fake data.
Still, the practice of false data leaks nonetheless has important implications for aspiring hackers and the targeted organizations. The latter may find themselves forced to reassure customers, verify whether a breach occurred, and publicly address false claims.
Data theft: how to protect your organization
The value of data—and their vulnerability to compromise—has given rise to an underground market where sensitive information is readily shared and easily accessible. Malicious actors, often organized, exploit these sensitive data for various criminal activities, including identity theft, financial fraud, and extortion. The Dark Web offers numerous forums where cybercriminals can exchange information, tools, and even specialized services.
For businesses, the risks associated with data breaches are significant. Customer data, financial information, and intellectual property may be compromised, resulting in severe issues that threaten business continuity. Phishing, a common method to access sensitive information, often involves social engineering attacks where attackers impersonate legitimate entities to obtain confidential information.
As an organization, you need to implement robust cybersecurity measures, including data protection protocols, security awareness training for employees, and phishing prevention solutions. Deploying advanced threat detection technologies and continuous monitoring is crucial to quickly identify any suspicious activity and mitigate risks. Ultimately, data protection should be a major priority for businesses, requiring constant vigilance against the persistent threats of a threat landscape that has recognized the value of exploiting data.




