Office 365 Phishing
Adrien Gendre
—December 14, 2017
—3 min read

Like a fisherman hoping for his next big catch, cybercriminals attempt to lure users with legitimate-looking mass emails in what’s known as a phishing attack. The goal is to fool users into handing over login credentials, downloading malware or visiting a malicious website.
Predictive Email Defense Required for Office 365 Phishing Attacks
This seemingly simple attack is both prevalent and stunningly effective.
According to a 2017 Dark Reading survey, 55% of organizations surveyed were victims of a phishing attack in 2017.
The fact is that most organizations don’t have adequate email security measures in place to protect against Office 365 phishing attacks.
Tricking Email Users is Easy
Office 365 phishing attacks are easy for cybercriminals to pull off. They design counterfeit emails and websites to look like they come from a trusted brand—perhaps a big-box retailer or a technology company whose software your business uses. Busy users recognize the brand and fail to notice slight differences that give away the imposter. (In their defense, those differences can be as small as a minor difference in the URL.)
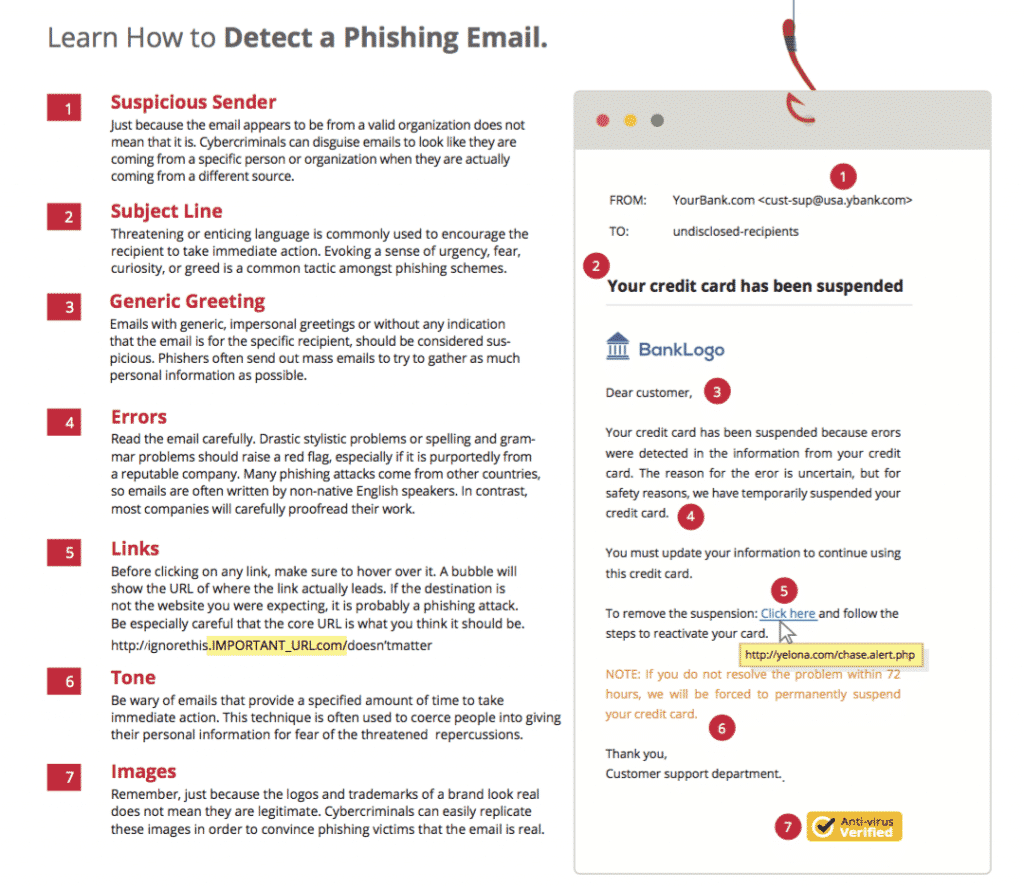
Once users click through a phishing email, they are directed to a web form where the sky is the limit. Attackers might request:
- Access credentials to corporate resources like your ERP system or cloud-based applications
- Access credentials to the users’ personal accounts (which users often reuse across multiple accounts including your corporate accounts)
- Sensitive financial information, either the users’ own or that belonging to the company
- Corporate proprietary information
Whatever data the attacker successfully collects can then be used to conduct additional attacks. For example, attackers might use access credentials to break into and move around the corporate network or sell the sensitive and confidential data they’ve obtained on the dark web.
Advanced Phishing Attacks Increase Risk
As bad as phishing sounds, it actually gets worse. While phishing attacks are conducted against a large population of users, spear-phishing attacks target specific individuals. Spear-phishing attacks are specifically crafted to appeal to an individual using relevant details and posing as trusted colleagues, friends, or even members of sporting societies or charitable boards. These attacks have even higher success rates than generic phishing attacks and present a much bigger problem for organizations as they often target critical gate keepers like executives and even IT professionals.
Phishing and spear phishing are the primary delivery methods for ransomware.
The social engineering behind spear phishing is easy, inexpensive, and mind-bogglingly effective.
Studies show that roughly half of all users will click on virtually any link sent to them with even minor customization. Even after security training.
 Organizations need a technical backstop to prevent users from getting an opportunity to click on those oh-so-tempting links or helpfully responding to a Business Email Compromise (BEC) attack by wiring $100k to a fraudulent vendor. Sadly, too many organizations rely solely on Microsoft’s built-in email security and filtering tools known as Exchange Online Protection (EOP). However, while a good tool in many ways, EOP is not capable of providing robust email protection on its own.
Organizations need a technical backstop to prevent users from getting an opportunity to click on those oh-so-tempting links or helpfully responding to a Business Email Compromise (BEC) attack by wiring $100k to a fraudulent vendor. Sadly, too many organizations rely solely on Microsoft’s built-in email security and filtering tools known as Exchange Online Protection (EOP). However, while a good tool in many ways, EOP is not capable of providing robust email protection on its own.
The basic email security features and capabilities in Office 365 can’t stop every phishing and spear-phishing attack.
EOP is a signature-based solution. That means it identifies attacks based on known patterns. This is an effective approach for blocking known threats that are circulating the Internet. Once someone falls victim to a phishing attack and the email or attachment is identified as malicious, a signature file is created and used to protect other users. As long as your organization isn’t amongst the first to fall victim to a phishing attack, the malicious email will be caught before it hits your user’s inbox.
Attackers Outsmart Signature-based Filters
But cyber attackers don’t simply call it quits once a signature is created for their attack. Instead, they continually alter the code so that the malicious software no longer matches the known signature in an attempt to avoid detection and bypass signature-based controls. And it works. Microsoft EOP scans the email, doesn’t recognize it for what it is, and sends the message to the user’s inbox, where it waits like a ticking time bomb.
 Furthermore, some spear-phishing attacks don’t contain malware or links at all. Attackers simply pose as the recipient’s colleague or partner, asking for them to send sensitive information such: “Hey, I’m on the golf course with a customer, the CEO just texted me asking for the financial pro-formas… can you send them to me ASAP!” Because such emails look valid to most filters, they will never match a signature file.
Furthermore, some spear-phishing attacks don’t contain malware or links at all. Attackers simply pose as the recipient’s colleague or partner, asking for them to send sensitive information such: “Hey, I’m on the golf course with a customer, the CEO just texted me asking for the financial pro-formas… can you send them to me ASAP!” Because such emails look valid to most filters, they will never match a signature file.
Another way that attackers get past standard email filters is to “time-bomb” links. The link is totally innocuous when it is scanned by the filters but resolves into a malicious site once it is sitting in the user’s inbox. The only way to get past this trick is to scan the links both when they arrive and when the users click on them.
In order to defend against Office 365 phishing attacks, you need predictive email security that complements Microsoft EOP. Advanced threat defense is predictive rather than reactive and can spot new variants of email threats.
Only a next-generation security solution provides predictive threat defense.
Next-generation security solutions leverage artificial intelligence, predictive analytics, and machine learning to stop unknown threats. These technology providers analyze global threat data to evaluate the context of the inbound email according to multiple factors, such as:
- IP addresses
- URLs
- Style
- Previous context
- User interactions
- Domain names
- And more
This is the approach we use at Vade. Our 24/7 global threat detection center analyzes billions of emails on a daily basis. With the help of artificial intelligence and predictive analytics, we discover 120,000 types of malware and 150,000 phishing URLs—every day. Our artificial intelligence can reliably identify one-off spear-phishing emails, sensitive data requests, time-bombed URLs, and zero-day malware hidden in executable files, PDFs, Office documents, and more.
The proof?
Vade successfully detected every variant of Locky and CryptoLocker over the past several years with 100% accuracy.
Contact us to learn more about protecting against Office 365 phishing attacks with Vade.



