Predictive Email Defense for Office 365 Ransomware Attacks
Adrien Gendre
—January 21, 2018
—3 min read

It’s the big day. In a couple hours, you’re scheduled to present a report to upper-management that could put you in good standing for a promotion. You’re putting the last touches on your report when you receive an Excel spreadsheet (seemingly from a colleague) that contains the last few numbers you need. Moments later, your computer freezes. A ransomware message pops up:
Stop Office 365 Ransomware Attacks with Predictive Email Defense

Your documents, photos, databases, and other important files have been encrypted. A private decryption key is stored on a secret Internet server. Nobody can decrypt your files until you pay and obtain the private key. You only have 24 hours to submit payment. If you do not send the money within the provided time, all your files will be destroyed. Warning! Do not try to get rid of the program yourself. Any action taken will result in the permanent deletion of your files. The only way to keep your files is to follow the instructions below…
Congratulations. You’re another victim of ransomware delivered by an Office 365-based email.
What do you do? Do you pay the price? Or report it to the IT department? If you are the IT department, or at least in it, you risk your reputation—you should’ve known better than to fall victim to ransomware. If you aren’t in the IT department, are you sure that you haven’t done anything negligible?
According to Cybersecurity Ventures, the global cost of ransomware damage is expected to exceed $5 billion in 2017—up from $325 million 2015.
Experts advise organizations not to pay ransoms, as it only rewards attackers and encourages them to continue using ransomware. But what’s a user to do when they’re under pressure to deliver at work or their own online behavior may be questionable? Your best option is to prevent ransomware in the first place with predictive email defense.
What is Ransomware?
Before we get into prevention measures, let’s take a closer look at what we’re dealing with. Ransomware is malicious software that attackers use to encrypt files on a victim’s computer or device, rendering them inaccessible. The attacker demands a ransom to be paid in exchange for the decryption key. The attacker may also add an additional blackmail threat, as in the above example. Most often, ransomware is delivered via phishing or spear phishing emails. Cloud-based email systems like Office 365 are as vulnerable as any email system without adequate protections.
Research by IBM reveals that 59% of ransomware attacks originate with phishing emails.

Attackers use phishing and spear phishing tactics to entice users to open an email attachment or visit a web page that has been infected with ransomware. These attacks, while relatively simple, are successful because users are busy and tend to want to help one another. If Sam receives an urgent email that looks like it is from his manager, he’s unlikely to question it but is more likely to follow through on the request—even if that means sending his “manager” a password or opening an infected document.
The number of emails infected by ransomware increased 6,000 percent from 2016 to 2017, according to a review by IBM Security.
Ransomware has proven to be a lucrative business—so much so, in fact, that ransomware creators now sell their technology, making it accessible to virtually anyone. Ransomware-as-a-Service is a means by which ransomware creators can provide their code to less experienced attackers for a fee. The “customer” can deploy the ransomware and customize its features, colors, and countdowns, via a portal. Depending on the service, the customer either makes a payment upfront or the provider takes a cut of the collected ransom payments.
The Challenge of Preventing Ransomware
The best way to reduce the risk of ransomware is to stop it from landing in your users’ inboxes in the first place. Unfortunately, standard email filtering systems don’t have the technology to effectively block advanced ransomware. Even Microsoft’s built-in email security and filtering tools for Office 365, Exchange Online Protection (EOP), is designed to only protect against known attacks. It’s not capable of providing the level of protection organizations require to stop the phishing and spear-phishing attacks that deliver ransomware.
Cybercriminals bypass signature-based filtering systems like EOP by constantly changing the code in their malicious software. Because the systems don’t recognize the codes “signature” as being malicious, ransomware and other malware is delivered to inboxes where users must become the last line of defense. Eventually, variant signatures are recognized and stopped by systems like EOP. However, this is only after ransomware has claimed numerous victims.
Putting an End to Ransomware
Organizations need a robust predictive email security solution that complements Microsoft EOP to defend against Office 365 ransomware. Such a solution should utilize artificial intelligence, predictive analytics, and machine learning to predict future threats, like polymorphic or metamorphic ransomware variants.
This is the approach we use at Vade. Our 24/7 global threat detection center analyzes the context of inbound emails according to: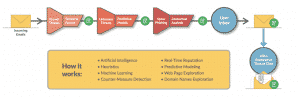
- IP addresses
- URLs
- Style
- Previous context
- User interactions
- Domain names
- And more
Analyzing global threat data, this analysis can actually stop unknown threats before they’re delivered to Office 365 users. With the help of artificial intelligence and predictive analytics, we discover 120,000 types of malware and 150,000 phishing URLs—every day. Our artificial intelligence can reliably identify one-off spear-phishing emails, sensitive data requests, time-bombed URLs, and zero-day malware hidden in executable files, PDFs, Office documents, and more.
Vade has successfully detected every variant of ransomwares Locky and CryptoLocker over the past several years with 100% accuracy.
Contact us to learn more about protecting against Office 365 ransomware attacks with Vade.



