Phishing News: Gmail Phishing Attack
Adrien Gendre
—January 26, 2017
—3 min read

We wish there was a more positive forecast for phishing attacks in 2017, but unfortunately it looks like things are only going to get worse. With millions of phishing emails sent out daily, it should be no surprise that there are new and increasingly-advanced attacks reported by major news sources all the time. This week, Mark Maunder of WordFence (security plugin for WordPress sites) uncovered an alarmingly advanced Gmail phishing attack.
At least 156 MILLION phishing emails are sent out every day.
How It Works
The Gmail phishing attack begins with a hacker sending an email to your Gmail account. The email may come from a known contact (who had their account hacked using the same method), and contains what looks like an image of an attachment that you recognize.
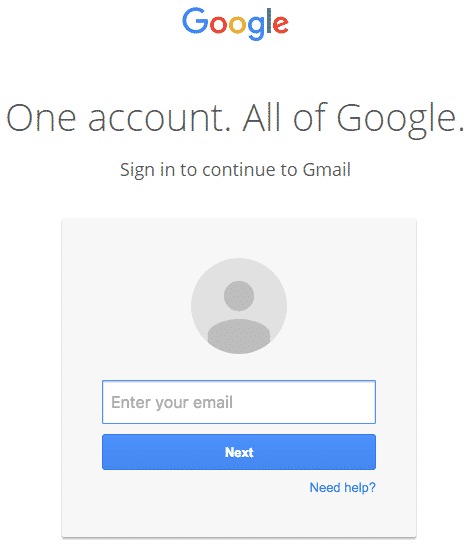
When the attachment gets clicked, you would normally get a preview of the image, but instead are lead to a counterfeit Gmail login page. Since the URL contains the standard accounts.gmail.com, most people login – unaware that they have just compromised their account.

Hackers immediately login to the compromised account once they obtain the credentials. They then probe your email to send fraudulent attachments to your contacts, making them the next victims. The attacker goes through your email to find attachment names and subject lines to send convincing emails to your contacts. Then the scam starts all over again.
Hackers use your subject lines and attachment names in fake emails to continue their attacks.
Advanced Techniques
What makes this hack particularly difficult to spot is the techniques used to make the attachments and login page look legitimate. White space hides the URL from the file attachment name, making it look like a convincing PDF. Hackers are able to use a data URL scheme to embed the file in the browser location bar that only executes once the attachment is clicked.
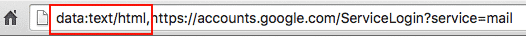
By not triggering googles HTTPS security notifications and utilizing a standard google domain, even trained individuals are falling for this attack.
Although the URL address does include an additional URL prefix (data:text/html) the root of the URL is the standard “accounts.google.com”, so many people don’t notice the difference. In addition, the URL doesn’t trigger the normal red/green insecure/secure HTTPS security indicators that google utilizes. The uniform process throughout is what makes the attack so effective.
Warning Signs
Even though this attack does utilize advanced techniques, there are some warning signs that you can look out for to protect yourself.
- Fuzzy attachment image: people who have spotted this phishing attack have reported that the traditional PDF attachment image within the email is low-resolution and looks “fuzzy”. What is actually being shown is a preview image of what a normal Gmail PDF attachment looks like to trick people into
- Low-resolution Google logo: others have reported that the counterfeit login page contains a low-resolution Google logo. Unfortunately, this small change to an otherwise perfect replica goes unnoticed, convincing people to unknowingly forfeit their credentials.
- URL prefix and green lock: Even though this attack does utilize the correct core URL (accounts.google.com) the lack of a green HTTPS security lock plus the use of a strange URL prefix (data:text/html) should be red flags that something isn’t quite right.
Standard email security systems are unable to defend against attacks like this.
The Big Picture
The fact that this hack has tricked even advanced technical users is a reason to worry. Many individuals don’t pay attention to things like URLs and image resolution. Variations on this basic technique could be used to steal credentials from other email platforms and websites. That is why it is crucial to have advanced email protection.
Advanced email security is important to protect you and your organization from advanced phishing attacks.
If your organization uses Gmail for business, your organization is still at risk from this particular hack. Even if you don’t, due the unfortunate habit of many users to reuse credentials, you still might at risk as users give up their personal credentials that also work on your corporate systems…
One solution is Vade artificial intelligence powered email security solution. Vade provides companies with the security they need to avoid all types of phishing attacks. Our advanced software finds and eliminates threats like this attack before it ended up in your employee’s inbox. (And yes our engineers verified that we caught this specific threat from day-zero just as we have with virtually all recent phishing, spear phishing, ransomware, and other email attacks.)
Ready to see how Vade can protect your organization from even the most advanced attacks? Start a FREE trial today!



