Ransomware Protection: how to protect your organization effectively
Adrien Gendre
—December 15, 2017
—3 min read

Ransomware is a serious threat to all organizations. According to the 2017 Verizon Data Breach Investigations Report, there was a 50% increase in ransomware attacks over the last year. Effective ransomware protection has become critical for organizations.
How to defend your organization against ransomware
These attacks are constantly evolving to slip past the security solutions you already have in place. In order to provide your organization with the best ransomware protection, you need a solution that provides predictive defense so the malicious software doesn’t enter your employees’ inboxes in the first place.

What is Ransomware?
Ransomware is a subset of malware (derived from the term “malicious software”), in which a victim’s files and data are encrypted and held hostage until a ransom is paid. It is the biggest threat to businesses and it continues to grow. According to IBM security, this year alone the number of emails infected with ransomware increased 6,000% and American organizations are the #1 ransomware target in the world.
Ransomware is a subset of malware in which a victim’s files are data are encrypted and held hostage until a ransom is paid.
How Ransomware Works
Ransomware is able to infiltrate a device when a victim downloads (knowingly or unknowingly) a malicious payload. Once installed on the target device, the ransomware encrypts all of the files and then locks down the computer. The only way to get the decryption key and regain access to your files is to pay a ransom. In order to pressure victims to pay out, cybercriminals may threaten to release or delete sensitive data.
The threat to organizations continues to grow as cybercriminals get increasingly sophisticated with their software and delivery techniques. Continuous evolutions of the malicious software, like metamorphic and polymorphic malware, make it difficult for standard email security solutions to keep up with the best ransomware protection solutions.
Delivery Methods
Ransomware, regardless of type, is often delivered through generalized mass phishing emails or targeted spear phishing emails.
- Phishing: These generalized emails attempt to trick recipients into disclosing personal information or clicking on websites and attachments to deliver ransomware. The emails often appear legitimate and may come from websites you would typically trust like DocuSign or Google Docs. Since the emails include familiar company logos or duplicated login pages, many users end up falling for the attack.
- Spear Phishing: Also known as whaling or the business email compromise (BEC), this delivery method will target specific individuals using highly customized attack messages to dupe users into falling for attacks. The emails usually appear to come from trusted senders like customers, partners, or C-Suite executives. In some cases, cybercriminals will email back and forth to establish trust before asking for confidential information or sending booby-trapped attachments.
Although there are numerous attack vectors for ransomware, email is by far the most popular. 91% of all malware, and therefore ransomware, is delivered via email, according to IBM security. Organizations must place extra emphasis on ensuring this business vulnerability is protected against threats, with effective and proven ransomware protection solutions.
91% of all malware, and therefore ransomware, is delivered via email.
Traditional Security Measures Are No Longer Sufficient
Traditional security methods are no longer sufficient to protect against these advanced attacks. These typical methods rely on “signatures” which must get recognized as malicious multiple times before solutions blacklist them. That means there is a chance the ransomware will get through these initial precautions and devastate an organization before it is recognized as a ransomware variant. Even just one malicious email can have irreversible consequences.
Organizations Need Predictive Email Security
Predictive security is required to catch threats before they become problems. Signature-based solutions don’t adapt fast enough to the constantly changing threat landscape. Predictive email security, like the Vade solution, makes it possible to catch malicious emails from their very first iteration. Organizations don’t have to worry about training their employees to catch these emails. Instead, you can prevent the emails from ever entering their inboxes.
Like standard email security approaches, Vade checks the IP, headers, and content of the email. However, Vade goes further and checks additional contextual elements utilizing over 10,000 heuristic algorithms. This means that even if emails have unsuspecting headers and content, they will still be blocked based on the contextual elements. Machine learning further improves this ransomware protection technology by understanding individual sender tendencies to catch malicious emails in the event that an account has been compromised.
Organizations need predictive email security backed by artificial intelligence to truly protect themselves.
For example, if the CEO of your organization John Smith always signs off on emails using the phrase “Best, John” and suddenly an email gets sent using the phrase “Thanks a bunch, John,” then the solution will flag this email as suspicious. Of course, if John simply decided to switch up his sign off and it really was him, there are tools in place to ensure that emails get to the correct recipients.
Ransomware protection software: the Vade solution
The Vade solution features an artificial intelligence engine that taps into a massive database to successfully identify brand new families and variants of ransomware and other emailed threats.
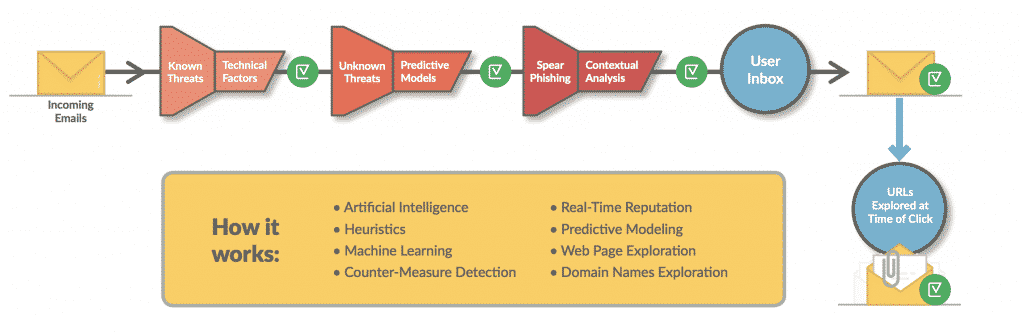
Using 10,000+ heuristic algorithms with eight levels of analysis, Vade scans billions of emails across the globe every day to detect known and unknown threats such as zero-day malware, ransomware variants, and even sophisticated social engineering attacks embedded in phishing emails. This global analysis is then combined with local and behavioral analysis to study organizational and individual styles and behavior and thereby identify suspicious patterns.
Interested in learning more about ransomware protection? Download the complete eBook: Protecting Your Company from Ransomware.



