Word Document Malware: OLE Exploited in Zero-Day Attack
Adrien Gendre
—May 01, 2017
—3 min read

A recently discovered Microsoft Office vulnerability has allowed a new type of Word document malware to infiltrate PCs. Hackers are using booby-trapped Word documents to deliver malware to unsuspecting victims. The malware exploits Windows Object Linking and Embedding (OLE) features, which allow users to link to documents and other objects – in this case, a malicious remote server.
Currently, this attack only affects PC users because of the features exploited to achieve malware delivery, but hackers could easily develop a version for Mac users in the near future.
How it Works:
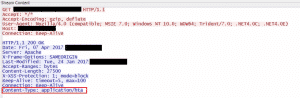
- A malicious Word doc containing an embedded OLE2link is sent via email
- When the email is opened, the embedded winword.exe exploit code connects the PC to the attacker’s server
- Once connected a malicious HTML application is automatically downloaded and disguised as a rich text format Word document
- The application executes as a .hta file, which then downloads additional payloads from well-known malware families
- After the payloads are downloaded the exploit closes the original malicious Word document and opens a fake one in an effort to cover up the attack that just occurred
This unique Word document malware exploits Windows Object Linking and Embedding (OLE), an important feature of the Microsoft Office Suite.
It appears that the Word malware can install on completely patched computers and makes anyone using any version of Word a possible victim. {Update: Patch available as of April 11}
But doesn’t Microsoft Office include some security features?
Yes, but since .hta files are executable the hacker has arbitrary code execution access to the victim’s machine. This access gives hackers the ability to bypass the memory-based mitigations that have been developed by Microsoft.
What makes this malware unique?

Emails with malicious attachments are a common tactic hackers use to trick victims into downloading malware, ransomware, and other viruses. However, this Word malware is different in a few ways:
- It is able to bypass the mitigations that have been designed by Microsoft to defend against similar attacks
- It doesn’t require victims to enable macros, the Word document malware starts downloading once the document has been opened
- Once infiltration is complete, the malware opens another decoy document to hide evidence of the attack
This Word malware doesn’t require users to enable macros, the software downloads automatically.
So how can you defend against this Word malware?
First, you should always keep your software up to date. Developers often include important security updates to defend against threats within regularly scheduled updates.
Second, you should never open files from unknown senders. Even if the file looks like it is coming from someone you know, it is important to double check the sender’s authenticity as malware and ransomware are almost always delivered through spear phishing emails. If it’s necessary to open a potentially risky document take advantage of Microsoft Office Protected View.
Most importantly as of April 11th, Microsoft released a patch to defend against this attack (which you should download immediately) – but is important to understand there will be more attacks. Hackers continuously morph their software to get past all types of security defenses.
91% of malware attacks are delivered through email.
The fact is, there will always be vulnerabilities in popular software that hackers exploit. Once hackers figure out how to exploit a vulnerability they develop malware and try to spread it to as many victims as they can via email before it gets patched. It all starts with email. So the best way to defend against this attack is to start at the source by getting advanced email protection.
Advanced Email Protection
Vade provides advanced email protection that defends your organization against known and unknown threats including:
- Malware
- Ransomware
- Zero-day attacks
- Spear Phishing
Don’t just defend against some threats, defend against all threats – including the ones that haven’t been blacklisted by standard spam filters yet.

Our layered security approach, backed by artificial intelligence, analyzes, identifies, and isolates malicious software before users have a chance to engage. We analyze for known threats with two different anti-virus scanners and defend against unknown threats by using extensive technical and behavioral analysis.
If your organization had Vade this Word document malware threat wouldn’t be an issue. Our AI-powered email security was detecting and sandboxing this threat from the time of the initial release by looking at the behavior of the malicious file as opposed to trying to match it to a specific signature-based pattern. It is this method that helps us detect and defend against all types of zero-day attacks.
Want to learn more about the Vade Email Security Suite?
We would be happy to answer any of your questions or give you more information about how our software is able to defend against these advanced threats. Contact us today!



