Common Types and Prevention of Brute Force Attacks
Adrien Gendre
—December 08, 2022
—3 min read

According to IBM’s Cost of a Data Breach 2022 Report, stolen or compromised account credentials are the most common cause of a data breach, costing businesses on average $4.35 million (USD) globally in 2021. While hackers use a variety of techniques to achieve a successful data breach, one of the most common methods is a brute force attack.
According to research from Google Cloud, brute-force attacks are now the most common cyberattack for cloud service providers, making up just over half of all attacks. And with recent advancements in Graphics Processing Units (GPUs), threat actors can use even a relatively simple GPU to perpetrate a brute force attack and crack over 95% of passwords in just a few days. Needless to say, this kind of attack needs to be top-of-mind when it comes to optimizing cybersecurity defenses. To effectively combat this increasingly common and sophisticated cyberthreat, it’s important to first understand it.
In this blog, we examine brute force attacks and how you can protect against them.
What is a brute force attack?
A brute force attack is when someone aims to gain unauthorized access to an account or encryption key.

In this type of attack, hackers attempt to guess password combinations until they crack the code. When executed successfully, this attack technique can be used to harvest data, spread malware and ransomware, and divert website traffic.
What are the different types of brute force attacks?
Brute force attacks come in a variety of shapes and sizes, and each one relies on different methods to target and steal sensitive information. Knowing each type is important to protecting your organization and clients from compromise. Here are some common brute force attacks to keep on your radar.
Credential stuffing
In a credential stuffing attack, hackers use compromised login combinations to infiltrate one or multiple systems. They target users who recycle usernames and passwords for multiple applications, as this gives hackers a golden opportunity to gain access to multiple accounts with just one password. If a cybercriminal gets their hands on one legitimate username and password, they’ll attempt to use the same combination on other sites.
Simple brute force attacks
As its name suggests, simple brute force attacks are basic compared to other brute force techniques and involve a threat actor trying to guess a user’s password. Hackers will often default to inputting commonly used entries for passwords or personal information that they’ve obtained. These attacks are easily preventable if users maintain complex and unique passwords across sites.
Dictionary attacks
A dictionary attack is when a person tries to perpetrate account takeover fraud by guessing a user’s login credentials. It’s similar to a simple attack in that the hacker will try multiple login attempts using common passwords, such as 123456, abcdef, or password. Oftentimes, hackers will simply cycle through words from a dictionary until they gain access, hence the name of the attack.
Reverse brute force attacks
A reverse brute force attack is similar to a dictionary attack but is often more successful in gaining unauthorized access. In this attack, a threat actor obtains a valid password and attempts to match it to a legitimate username. The compromised password may be a commonly used entry or one that was leaked in a separate data breach.
Hybrid brute force attacks
Hybrid brute force attacks combine different elements from dictionary and simple attacks. They occur when an individual uses known login credentials to gain further access across other platforms. Knowing that people will often add a series of numbers or special characters to the end of their passwords, hackers combine dictionary and simple attack techniques to generate login credentials.
How can you fend off an attack?
Preventing these prevalent security threats is easier than remedying attacks after they occur. While brute force attempts can vary in their complexity and success rate, there are measures every organization can take to minimize the likelihood of falling victim to one. Let’s highlight some best practices.
Adopt and enforce password policies
Hackers are more successful in compromising accounts with easy-to-guess passwords. That’s why your organization should set and enforce a strict password policy. This means ensuring your employees use long and unique passwords for each of their accounts and regularly update them. Adopting and enforcing password policies can help you prevent attackers from compromising an initial account or gaining access to subsequent ones in the event of a successful hack.
Limit login attempts
When organizations permit unlimited login attempts, a hacker can continue guessing username and password combinations until they gain access. That’s why it’s important to set limits for login attempts, which prevents hackers from cycling through an infinite combination of login credentials. Setting these limits can also block the IP addresses of users who consistently exceed the limit, helping to prevent future attempts and brute force attacks by malicious actors.
Require multi-factor authentication
With multi-factor authentication (MFA), users must confirm their identity using two or more login methods, such as answering security questions or entering unique codes sent to mobile phones or email addresses. While MFA is not a silver bullet against brute force attempts, it provides an added layer of protection that minimizes the likelihood of exploitation.
AI-threat detection and response
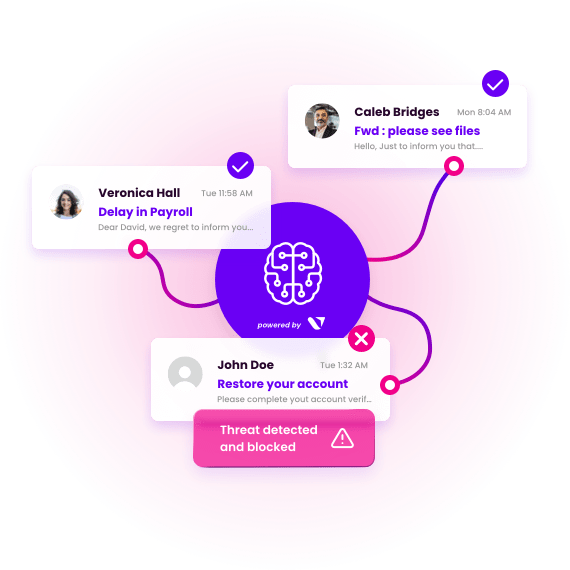
Once hackers gain unauthorized access to an account, they can launch insider attacks through phishing campaigns, spear phishing attacks, and other email-borne threats. That’s why your organization should adopt AI-threat detection and response technology, which enables you to limit the consequences of a compromised account. Vade for M365, for example, uses a core set of AI technologies to detect and neutralize all email-borne threats, including those not yet seen in the wild. Because the solution integrates with Microsoft 365, it provides protection within the productivity suite against internal threats and insider attacks.
Tackle brute force attacks head on
Prevention is key when it comes to brute force attacks. By investing in the solutions explored in this article, you can protect your organization, clients, and employees from exploitation. You can also protect your ability to concentrate on running your business and creating value for your bottom line.




