Table of Contents
- Phishing definition
- Types of phishing attacks
- Spear phishing vs phishing
- The anatomy of a phishing email
- Phishing examples
- Free phishing tools
- Corporate phishing attacks
- Phishing: the most targeted industries
- Phishers’ Favorites Year-in-Review
- Vade for M365
- Phishing techniques
- Phishing prevention
- Ready to choose Vade?
- FAQs
Types of phishing attacks
Email phishing. Email phishing is the most common type of phishing. It occurs when hackers impersonate a well-known brand and send an email containing malicious links or attachments to an intended victim. These attacks use social engineering techniques to entice the recipient to click a phishing link or download a harmful attachment. Hackers may use email phishing to harvest a victim’s credentials, infect a device with malware, carry out a subsequent cyberattack, and more.
Spear phishing or business email compromise (BEC). A highly targeted form of phishing, spear phishing impersonates individuals rather than businesses. Most often, the spoofed individual is someone known by the victim. While spear phishing attacks don’t typically use malicious links or attachments to compromise targeted recipients, they rely on effective social engineering techniques and extensive research about the impersonated individual and intended victim. The next section provides a more comprehensive definition of spear phishing and how it compares to email phishing.
Quishing. Also known as QRishing or QR code phishing, quishing hides malicious links or attachments in QR codes to bypass detection by email filters. Beyond the techniques used to evade detection, quishing attacks attempt to achieve the same outcome as standard email phishing threats.
Whaling. Whaling is a type of spear phishing that targets senior executives, often to facilitate a financial scam such as wire transfer fraud. Whaling attacks rely on the same social engineering techniques as spear phishing attacks. The difference is largely the individual targeted, rather than how it occurs. According to the National Cyber Security Centre (NCSC), whaling attacks primarily focus on financial institutions and payment services, while cloud storage sites, online services, and e-commerce organizations can also be commonly affected.
Social media phishing. Social media phishing is one of the most common types of email phishing. It impersonates social media brands and targets users with fake notifications, alerts, and other messages. Often, emails direct users to malicious websites designed to steal their credentials and use them to login to their social media accounts. If hackers are successful in compromising an account, they can surveil their victims, facilitate an account takeover (ATO), as well as impersonate the victim and target friends, family, and other connections. Since 2020, Facebook has remained the top #1 or #2 most impersonated brand by hackers. Other brands, such as Instagram and WhatsApp, commonly feature among the most impersonated brands.
Clone phishing. In this attack, hackers clone a legitimate email and modify it by substituting benign links and attachments with malicious ones. They then resend the email to the original recipient with the assumption that the intended victim is more likely to trust the content and sender based on their past experiences.
Vishing or voice phishing. Vishing occurs primarily or strictly through voice communication. Vishing attacks attempt to manipulate the intended victim into divulging sensitive information over the phone. This attack method can incorporate other channels of communication such as email or occur entirely over the phone. According to CISA, advanced vishing attacks often leverage Voice over Internet Protocol (VoIP) solutions so hackers can spoof legitimate callers.
Smishing or SMS phishing. Smishing, or SMS (short message service) phishing, occurs via text message. Like email phishing, smishing impersonates a known and established brand and sends the intended victim a text message containing a malicious link, request for information, or phone number controlled by the hacker for a vishing attempt. The aim of smishing is the same as email phishing.
Angler phishing. Angler phishing takes place on social media platforms. Hackers create fake profiles and pose as customer service representatives. They then target individuals on the platform that have posted complaints about the brand. As a fake gesture of goodwill, hackers may offer a refund, free giveaway, or another enticing offer that directs the targeted user to a malicious and illegitimate site.
Search engine phishing. Also known as search engine optimization (SEO) poisoning, search engine phishing is when hackers use SEO techniques to rank a malicious site in the top results for a search term. Designed to appear legitimate, the site is intended to harvest credentials or infect devices.

Phishing email impersonating Bank of America
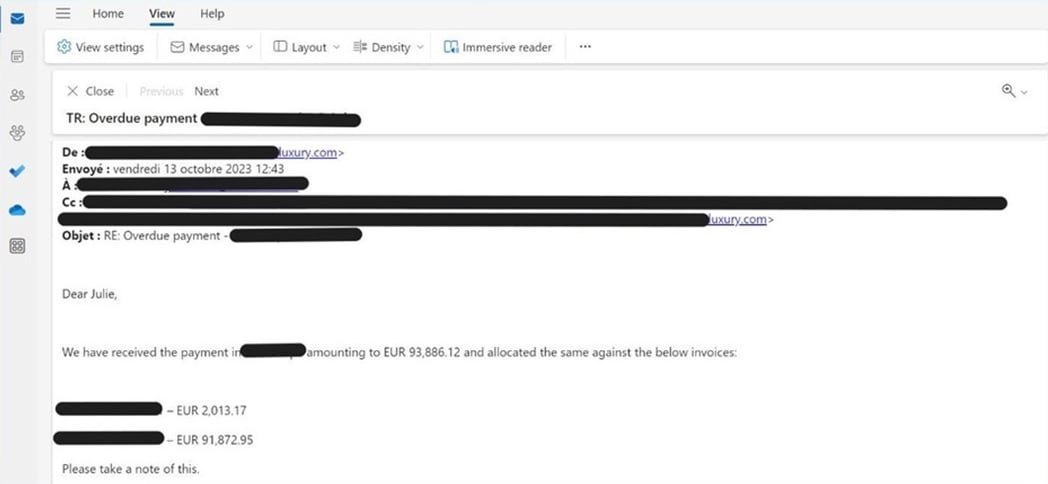
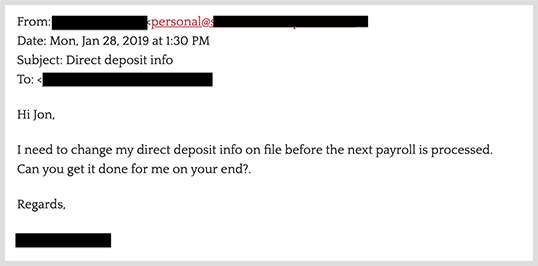
Spear phishing email
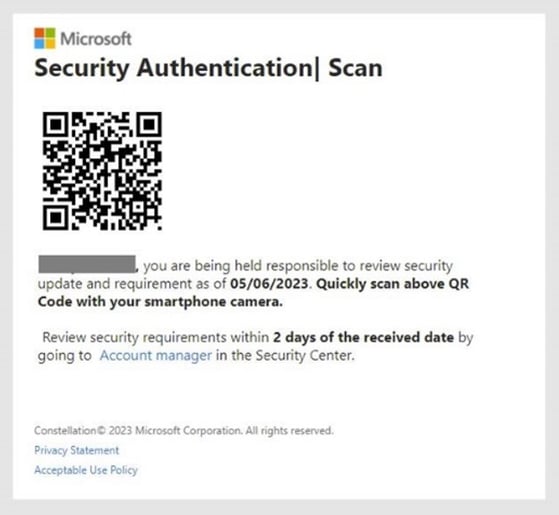
Quishing email impersonating Microsoft
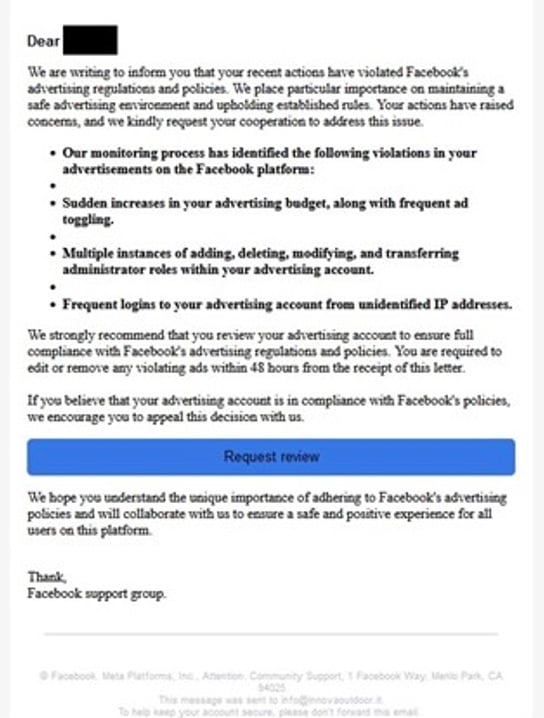
Social media email impersonating Facebook
Phishing vs spear phishing
What is spear phishing?
Spear phishing is a type of cyberattack that uses targeted emails to exploit intended victims. In spear phishing attacks, hackers impersonate individuals who are known to the victim, such as bosses, colleagues, friends, or other acquaintances. These threats use social engineering techniques and manipulation to trick recipients into disclosing sensitive information, wiring funds, making purchases, and more.
Spear phishing attacks are often financially motivated, with hackers seeking a quick payout. In most cases, attackers use publicly available information (such as company websites and social media profiles) to craft highly convincing messages that appear credible at first glance. Spear phishing emails also don’t contain malicious links or attachments, making them seem harmless even to a cautious recipient.
The anatomy of a phishing email
Subject line
A crucial element of a phishing email, the subject line is designed to entice, alarm, or frighten the victim into opening the email. In the age of more personalized attacks, hackers often write highly targeted subject lines to entice victims into opening emails. The “targeting” can even be as simple as adding “urgent” to the subject line, or referencing real invoices or other email threads to seem legitimate.
Email spoofing
Email spoofing involves creating an email address that looks like that of a trusted business. Two of the most common forms of email spoofing are display name and close cousin spoofing. Display name spoofing replicates the spoofed business name in the display name field. Close cousin spoofing uses a domain name that is a near-replica of the legitimate address. Both forms of spoofing bypass email authentication protocols, although display name spoofing appears as the primary identifier when emails are viewed on a mobile device. That’s because mobile devices hide the domain address of an email sender by default.
Brand impersonation
Phishing emails almost always contain brand and product logos, as well as other visual elements of an organization’s identity. These elements play an essential role in brand impersonation.
Phishing link
Phishing emails often contain one or more malicious links. While hackers typically position them within the body of the email, they can also hide them in a QR code (quishing), attachment, or a hosted file on a service like OneDrive or SharePoint. Hackers often choose the latter techniques to avoid detection from email filters. Phishing links direct users to a phishing page designed to harvest sensitive information or infect their device with malware.
Attachment
While not featured in all phishing emails, attachments are commonly used to conceal phishing links or deliver malware or ransomware. Often in the form of a Word document, PDF, or .zip file, the attachment appears to be legitimate business correspondence, such as an invoice. The link might lead to a phishing website or result in an automatic download of malware or ransomware. According to Verizon’s Data Breach Investigations Report 2023, Microsoft Office documents are the most common type of attachment delivering malware.
Phishing page
A phishing page is a fraudulent webpage that impersonates a brand. Unsophisticated pages are easy to spot, but advanced phishers use real CSS from brand webpages to make their webpages identical to the real version. Phishing pages impersonate login pages where victims enter their username and password to access their account. Once divulged, hackers harvest the credentials.
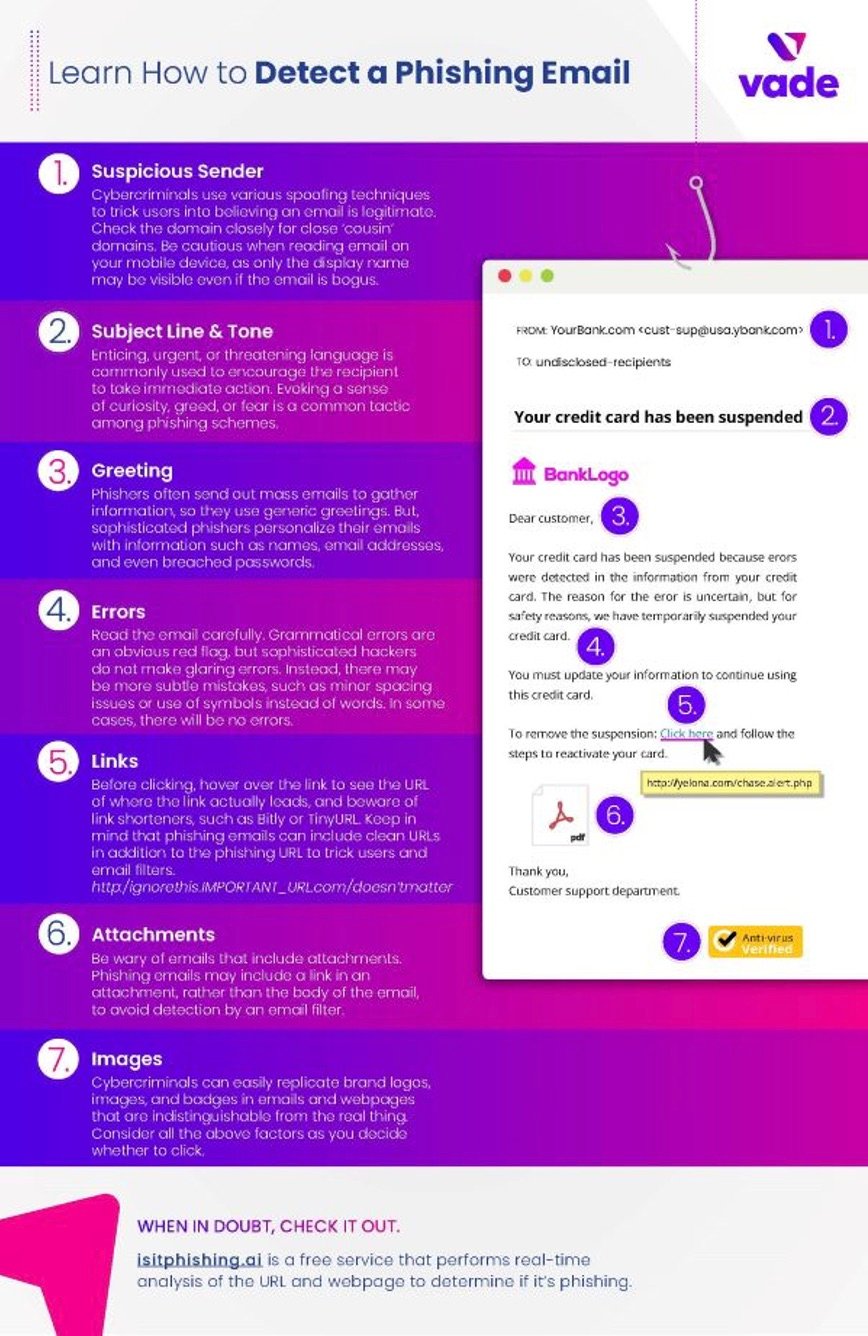
How to detect a phishing email infographic
Phishing examples
Urgency is at the essence of phishing. Hackers use a variety of scams to create a sense of concern and even fear to motivate users to click on links and divulge credentials and sensitive information. Below are common types of phishing scams:
Verify/update account
This email alerts the user that they must verify their account or reset their password, whether as a matter of routine or because of an issue with an account. The following TrustWallet scam notifies the intended victim that they need to verify their cryptocurrency wallet. The scheme is designed to redirect the user to a phishing page designed to harvest their credentials for an account takeover (ATO).
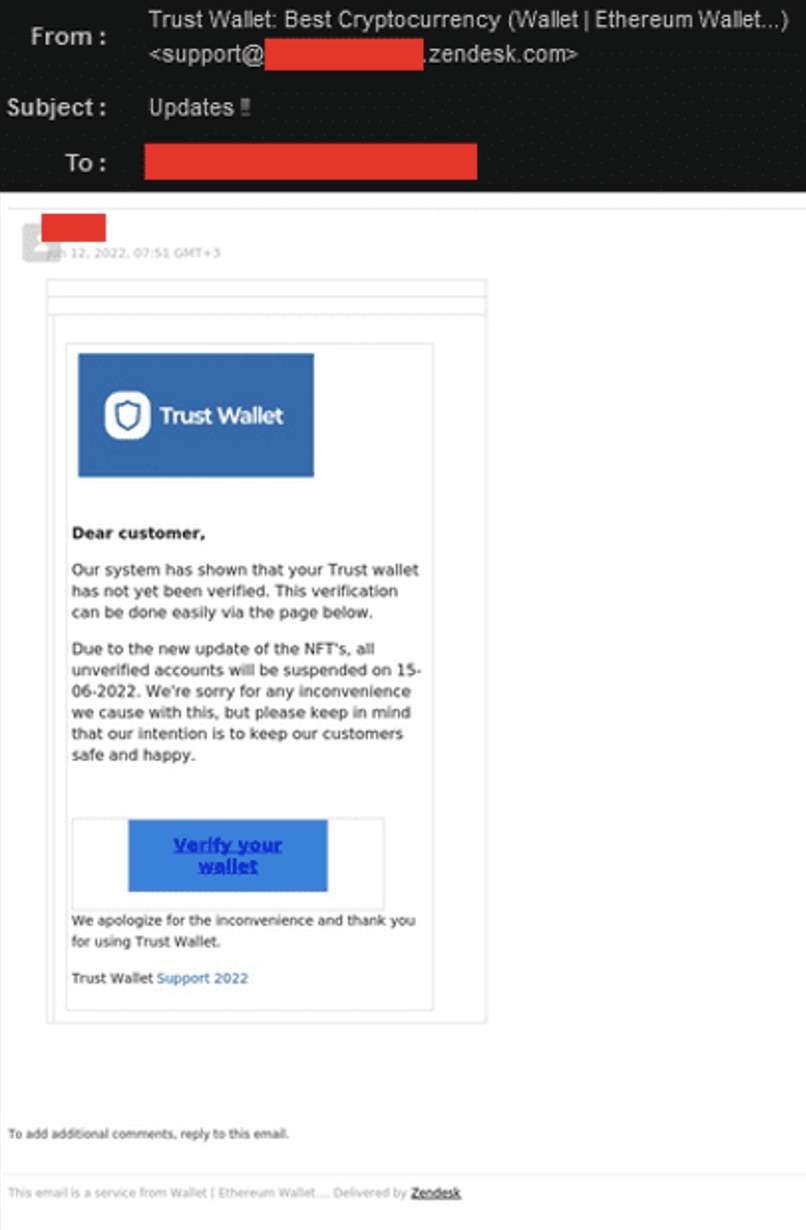
TrustWallet phishing email
Update payment alert
The victim is informed that their current form of payment, typically a credit card, is either not working or must be updated to continue receiving a service.
Invoice attached
This attack includes an attachment posing as an invoice or other piece of business correspondence. The attachment might include a link to a phishing page, or the attachment might deliver a payload of malware or ransomware when opened. For example, the following malspam distribution campaign impersonates the US Social Security Administration. The email contains a malicious link that automatically downloads malware onto the victim’s device.
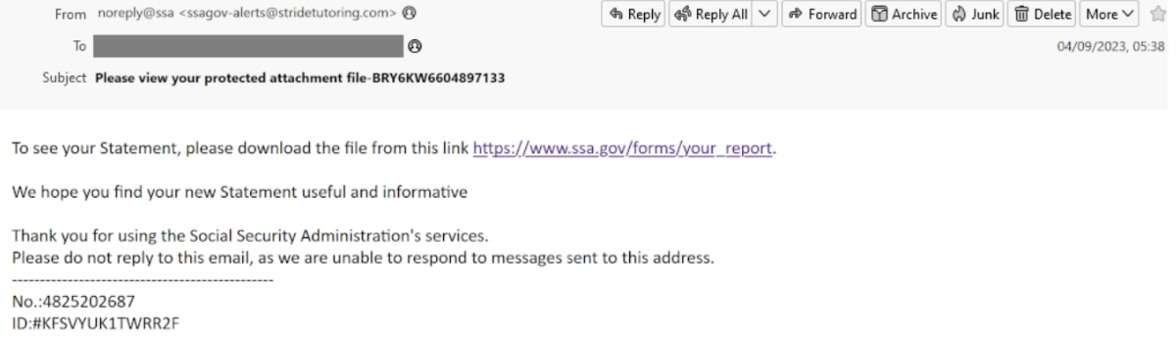
Phishing email impersonating US Social Security Administration
QR code
The body of the email contains a QR code for the victim to scan with their phone. Often, the QR code serves as a substitute for a button and hides the phishing link to make it more difficult for email security filters to detect. While this attack has existed for some time, it has made a resurgence in 2023 and 2024. The following examples include a Quishing attack stemming from the Ashley Madison leak in 2018 and a scam targeting Microsoft 365 users.
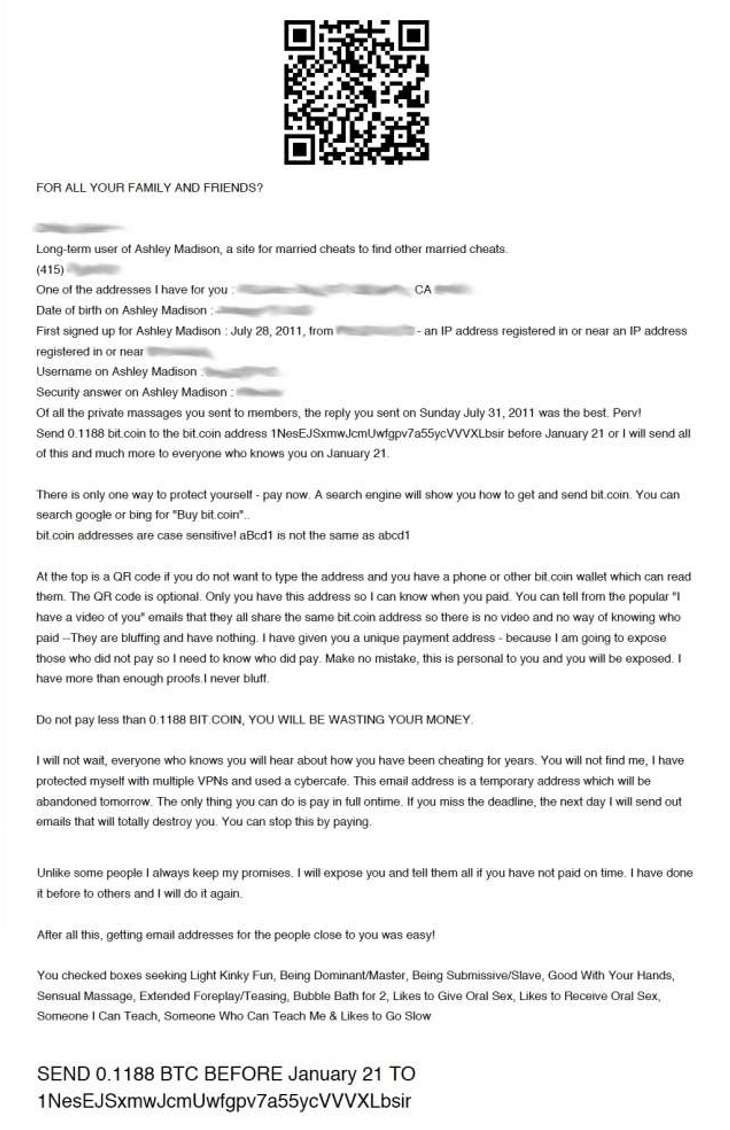
Quishing extortion scam from Ashley Madison leak
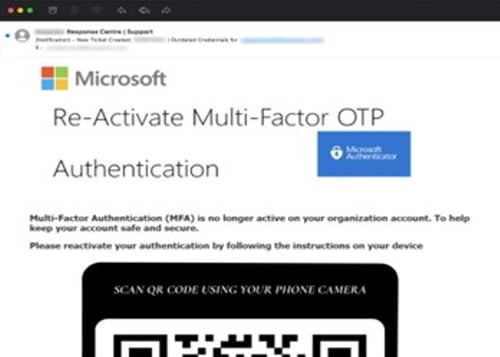
Quishing email impersonating Microsoft 365
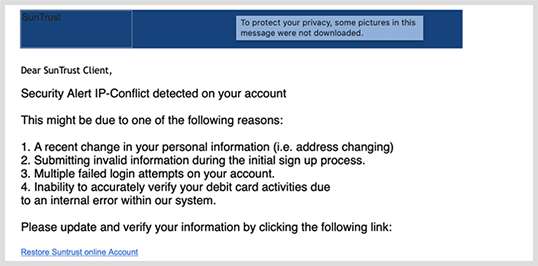
Security alert
The victim receives a security alert notifying them that their password has been compromised, there is suspicious activity on an account, or they recently signed into an account from an unknown device. For example, a user may receive an automated email impersonating Netflix—one of the most spoofed cloud brands—notifying them of unusual account activity. If victim clicks the malicious link, they’re often directed to a phishing page designed to harvest credentials that allow attackers to hack a Netflix account. Pirated accounts from Netflix and brands like Netflix, Hulu, DirectTV, Brazzers and others commonly sell on the dark web.
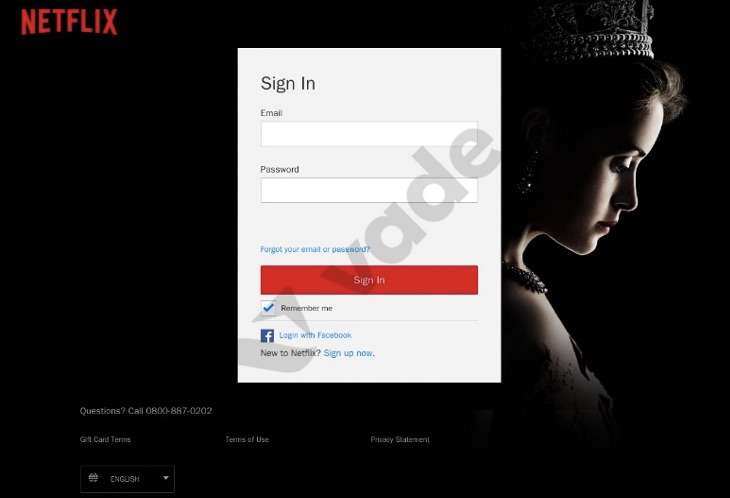
Netflix phishing page detected by Vade
Sextortion
Sextortion scams are designed to trick victims into believing a hacker is in possession of compromising information, such as webcam video of the victim watching online pornography. These scams often target consumers of sites. The victim is instructed to pay the hacker in Bitcoin to avoid the information being leaked to the public and their acquaintances.
Corporate phishing attacks
Phishing was once considered a consumer problem when it first emerged in the mid-1990s and hackers impersonated AOL employees to exploit users of the Internet service. But as attackers grew more sophisticated, they began targeting businesses, including cloud service providers, financial institutions, and other large corporations relied upon by organizations. By 2013, phishing became the primary vehicle for delivering ransomware, an effective threat for seizing critical data and holding organizations hostage in exchange for a fee.
Phishing: the most targeted industries
- Financial services. The financial services sector is consistently the most impersonated by hackers. By spoofing banks and financial institutions, hackers can trick their targets into divulging sensitive information or credentials. These can be used to directly access online bank accounts or sell on the black market.
- Cloud. The cloud industry is consistently the second most impersonated. While a popular sector for impersonation, spoofing attempts largely focus on a handful of brands—Microsoft among them. The company’s popularity among hackers is due in large part to Microsoft 365 and other Office 365 products. Microsoft 365 is the most popular corporate productivity tool in the world with more than 382 million users. Microsoft, along with Facebook, has remained among the top two most impersonated brands since 2020.
- Social media. Social media is commonly the third most impersonated industry. While only a relatively few brands make up the sector, they commonly rank among the most spoofed by hackers. In recent years, Facebook has emerged as the most impersonated brand across all sectors.
- Internet/telco. Internet/telco is another commonly impersonated industry. Like financial services, impersonation attempts of this sector are distributed among numerous brands, rather than the select few of social media and cloud.
- E-commerce/logistics. E-commerce/logistics also figures into the list of the most impersonated industries. While attractive for hackers, this sector often attracts fewer spoofing attempts than the others on this list.

Phishing is an email scam that impersonates a business to trick recipients into divulging account credentials or clicking on a malware-laden link. In most attacks, it involves luring a victim with a link to a fake website or including an email attachment laced with malware.
Vade for M365 is an integrated, low-touch email security solution for Microsoft 365 that is powered by AI and enhanced by people. Featuring an intelligent AI engine that continuously learns from a global intelligence network of more than 1.4 billion mailboxes, Vade for M365 blocks the advanced threats that bypass Microsoft. Vade for M365 scans all elements of email, including email addresses, links, images, and attachments, neutralizing threats before, during, and even after phishing attacks.
Most email security filters use signature-based detection methods, including scanning for blacklisted domains and IPs. This makes it impossible for these types of filters to detect unknown attacks or phishing kits that include built-in protections from being identified by URL scanners.
Hackers use a number of techniques to bypass fingerprint and reputation-based filters. With a simple MX record lookup, hackers can see which email security solution is in use and create scripts to bypass MX rules or develop techniques to bypass the solution itself. Below are some of the most common and advanced techniques :
Targeted emails
- Victims are chosen by their job position, experience level, and other factors that indicate their ability to provide access to sensitive data.
- Phishers mine open source intelligence (OSINT) such as social media and past data breaches for information that could assist in personalizing the email and understanding what would motivate a victim to respond to a phishing email.
- Hackers also use OSINT about the target company to learn which brands they do business with, including their business partners, software providers, and banks or other financial partners.
Brand impersonation
- Brand logos and images are downloaded from the web and inserted into emails, adding authenticity and authority to the email.
- CSS and JavaScript are copied from legitimate brand webpages and used to develop phishing pages, making them indecipherable from the real thing.
- Legitimate reply-to email addresses from the brand are added to emails to convince the user that the email originates from the brand.
URLs
- URLs that lead to fake websites are either inserted into the email or hidden in a QR code or attachment, to avoid detection from email filters that cannot parse documents.
- Legitimate URLs that lead to safe webpages are included in the email, along with the link, to fool email filters into deeming the email safe after scanning multiple legitimate URLs.
- Time-bombed URLs are URLs that lead to safe, legitimate webpages and are then redirected to phishing pages once the email has been delivered.
- URL shorteners, such as Bit.ly and TinyURL are used to create aliases of the phishing URL to avoid detection by filters scanning for known phishing links.
Abuse of legitimate services
- Legitimate services offered by reputable entities, such as link redirects or URL hosting, provide hackers the ideal opportunity to evade detection and disguise threats. Hackers often abuse the redirect link feature of brands like Baidu, YouTube, and Google Translate. They also commonly abuse Cloudflare by hosting their phishing page on the platform, which enables them to benefit from the service’s antibot mechanism.
- These services and their providers continue to be top targets for hackers, since they add credibility to attacks, improve the chances email filters will deem threats as safe, and allow them to reach users unencumbered.
Image insertion and distortion
- Slight changes or distortions to images will change their crypotographic hash or “fingerprint.” This can cause a blacklisted phishing email to appear like a new, safe email to a filter.
- QR codes are often inserted in place of phishing URLs to evade filters that cannot extract QR codes.
- Text-based images, such as screenshots of emails, are inserted into the email body in place of text. This avoids content scanning by the email filter, which may deem the email safe if there is no content to scan.
Phishing prevention
To protect against advanced phishing attacks, your organization should look to implement the following measures. These are recommended and endorsed by prominent cybersecurity institutions such as the Cybersecurity and Infrastructure Security Agency (CISA) in the US, Agence nationale de la sécurité des systèmes d'information (ANSII) in France, and the National Cyber Security Centre in the UK.
To assess your organization’s phishing protection, take our free email security benchmark assessment.

- Adopt a third-party, integrated email security solution
Integrated email security solutions are highly recommended for countering modern email threats. According to the Gartner Market Guide for Email Security, businesses should supplement the native features of their email platforms with this technology, replacing traditional solutions like secure email gateways (SEGs). SEGs operate outside an organization’s internal network and rely on technologies that base detection on past attacks, rather than those that have yet to find a victim. Integrated solutions solve these deficiencies. They exist within the internal network and provide protection for external and internal attacks. Many also leverage AI-powered algorithms to detect and neutralize threats that have yet to emerge. The best solutions provide advanced capabilities for threat prevention, detection, and response.
- Implement email authentication
Email spoofing is a foundational strategy of phishing scams. Email authentication protocols exist to limit the ability for hackers to impersonate senders. Email authentication protocols, including Sender Policy Framework (SPF), Domain-Keys Identified Mail (DKIM), and Domain-based Message Reporting and Conformance (DMARC)—act as an important layer of security. Detailed recommendations for implementing SPF, DKIM, and DMARC can be found from NIST, and there are numerous resources and vendors available to assist with adopting DMARC.
- Adopt an email and web browsing policy
In addition to user awareness training, an email and web browsing policy addresses the human element of your overall security posture. These policies define the safe and responsible use of email and the Internet within your organization, establishing rules and guidelines for handling sensitive information and adhering to security protocols. You can start by using a respected institution's template and customize it to suit your organization's unique needs. Ensure that the policy is easily accessible and incorporated into employee training.
- Embrace user awareness training
Human error remains the top contributing factor to data breaches, according to Verizon’s Data Breach Investigations Report. User awareness training helps limit the potential for human error by teaching users to identify and properly handle the latest phishing threats and techniques. The best training results come from programs that provide simulation-based instruction electronically, automatically, and on-demand as users need it. Programs should also contextualize training according to the unique role of each user, considering that phishing threats can vary depending on the profession and seniority of a targeted victim. This contrasts with traditional training programs, which use generic simulation scripts, follow a pre-determined schedule, and require direct facilitation by an administrator.
At the same time, user awareness training programs should teach users to report suspicious emails. This gives admins the opportunity to investigate and remediate potential threats.
- Enable Multifactor Authentication (MFA)
Multifactor Authentication (MFA) fortifies your security by requiring users to authenticate their identity through multiple means that each offer a level of security. Institutions like CISA recommend all organizations adopt MFA, especially small-to-midsized businesses. Best practice is to adopt a FIDO or PKI-based MFA, which offers phishing-resistant protection. If these options are not feasible, the next-best alternatives are app-based, SMS, or voice MFA.
- Adopt and enforce strong password policies
Compromised accounts are often exploited in phishing or Business Email Compromise (BEC) attacks. Strong password policies can mitigate the risk of users creating weak passwords or reusing them across applications. To create a robust password policy, require users to set long and unique passwords, as length is more important than complexity, according to the National Institute of Standards and Technologies (NIST). Limit the number of incorrect password attempts allowed and develop and enforce a list of unacceptable passwords that includes dictionary terms, specific names, and breached credentials.
FAQs
- What is a common indicator of a phishing attempt?
A common indicator of a phishing attempt? There are several, including:
- An urgent demand or offer. An enticing warning or offer that is often time-sensitive and elicits an emotional and immediate response from the victim.
- Display name spoofing. A display name that matches a legitimate sender but is inconsistent with the domain name, often an easy-to-create consumer address or one belonging to a recently registered domain.
- Spelling or grammatical mistakes. Egregious errors a native speaker wouldn’t make, though this is becoming less common with the assistance of multi-lingual generative AI tools.
- Suspicious links or attachments. Links or attachments achieve the end goal of a phishing attack, which may include harvesting credentials or infecting a device with malware.
- How to avoid phishing?
To avoid falling victim to phishing attacks, best practice is to take a layered security approach. First, adopt an integrated email security solution, which provides advanced capabilities for threat prevention, detection, and response. Look for solutions that leverage AI-powered algorithms to provide predictive defense against attacks. Additionally, implement email authentication protocols such as SPF, DKIM, and DMARC to limit the ability for hackers to impersonate senders.
Also, establish an email and web browsing policy to define the safe and responsible use of online tools and address the human element of cybersecurity. At the same time, adopt user awareness training, which addresses human error by teaching users to identify and report phishing suspicious emails for investigation. Other practices include enabling MFA and enforcing strong password policies, each adding layers of security that make it harder for hackers to compromise accounts.
- How does phishing work?
Phishing is a common form of social engineering that cybercriminals use to deceive individuals and gain access to sensitive information. In a typical phishing attack, hackers impersonate a trusted business or individual. They send recipients an email that creates the ideal conditions for them to take a compromising action, including clicking a malicious link or downloading an attachment infected with malware. Hackers employ a variety of spoofing techniques to make their email appear legitimate, including display name spoofing, close cousin spoofing, image manipulation, and other techniques.
Typically, hackers aim to harvest sensitive information or credentials by redirecting and convincing potential victims to fill out forms on phishing pages or infect their device with malicious code. Phishing can cause an initial compromise, lay the groundwork for a multi-phased attack, or follow a successful cyberattack.









