What is email security?
A Complete Guide to Threats, Protocols, and Protection
Table of Contents
- Email security definition
- Common email security protocols
- Why is email security essential to businesses?
- Types of email security threats
- How malicious emails can affect your organization
- Benefits of email security
- Email security best practices
- What is an email security policy?
- How to choose the right solution for your business needs
- Protect your inbox with Vade
- Explore our email security solutions
- Learn more about email security
- FAQs
Email security definition
Email security is an important field in cybersecurity that is dedicated to protecting email communications and accounts from cyberattacks. It encompasses a broad collection of technologies, best practices, and standards designed to secure the communication channel.
As a practice, it encompasses the protection of email inboxes, securing communication that relies on email as a channel, and protecting accounts from unauthorized access, compromise, or even full account takeovers. More than just securing the email account itself, email security also includes safeguarding links included in email contents, identifying malicious or spam messages, and even classifying emails into subcategories such as newsletters or receipts.

SPF (Sender Policy Framework)
SPF is an authentication protocol that allows administrators to designate senders who are permitted to deliver emails from a domain. Authorized senders are added to a DNS record for the domain. In theory, SPF should block unauthorized IPs from sending emails from the domain; however, SPF is limited and requires additional protocols to be effective.

DKIM (DomainKeys Identified Mail)
DKIM is an authentication protocol that can detect forged or spoofed email addresses. DKIM creates a digital signature linked to a domain name for outgoing messages. This signature verifies to the recipient that the domain has not been modified.

DMARC (Domain Message Authentication, Reporting, and Conformance)
Also an authentication protocol, DMARC enables domain owners to validate their domains by publishing a DMARC record into a DNS record. A DMARC policy is published in a DNS record and indicates what action should be taken if an email fails either SFP or DKIM authentication.
When used together, SPF, DKIM, and DMARC provide a more comprehensive email security framework. SPF prevents unauthorized senders from using a domain, DKIM verifies the integrity and authenticity of the email, and DMARC provides a policy framework for handling failed authentication. This combination helps protect against email spoofing, phishing attacks, and domain impersonation.
The National Institutes of Standards and Technologies (NIST) recommends organizations, including small-to-midsized businesses (SMBs), adopt SPF, DKIM, and DMARC protocols to improve email security.
While DMARC is a free and open standard, its adoption has remained slow. By some accounts, only roughly half of email senders are using the protocol, and among those who are, only 14% have set enforcement policies for it. Enforcement policies determine how emails are handled if they pass or fail authentication. Without them, DMARC delivers all emails regardless of their authentication status.
While organizations can implement DMARC standards on their own, many organizations rely on third-party vendors for this service. Organizations like Global Cyber Alliance provide a list of vendors, as well as tools and resources for implementing DMARC.
While SPF, DKIM, and DMARC are effective email security protocols, they are not foolproof. They rely on proper implementation and configuration by domain administrators. They also don’t protect against cyberthreats that don’t involve direct impersonation of a legitimate sender. That’s why best practice is to augment these protocols with other measures like advanced email security and user awareness training.
Why is email security essential to businesses?
As the top vector for cyberthreats, email presents significant cybersecurity risks. According to Deloitte, 91 percent of all cyberattacks begin with a phishing email. Email is also the primary channel for some of the most common and costly types of cyberthreats such as phishing and spear phishing.
Without a dedicated email security solution, organizations risk falling victim to a variety of cyberthreats. Traditional email platforms often lack robust security features, leaving them susceptible to phishing attacks, business email compromise (BEC) scams, malware infections, and more. These risks can have severe consequences, including financial losses, reputational damage, and legal liabilities.
The security community and respected institutions such as Gartner recommend that organizations adopt an integrated, third-party email security solution. This technology supplements the native security features of email platforms while providing more advanced and layered protection against cyberthreats.
Types of email security threats
Organizations face numerous email security threats that can have devastating consequences if not properly addressed.
- Phishing: Phishing is the practice of impersonating well-known and established brands to trick recipients into clicking a malicious link or downloading an attachment infected with malware. Phishing can be used for credential harvesting, account takeovers (ATO), and more.
- Spear phishing: Spear phishing, also known as business email compromise (BEC), is a targeted email threat that impersonates an individual known to the intended victim. Unlike phishing emails, which contain malicious links or attachments, spear phishing attacks typically rely on text-based content to exploit victims. For this reason, spear phishing scams are often harder to detect and defend against.
- Malware: Malware refers to malicious software. Email is the most common method of distributing malware, which hackers can embed in email attachments or destination phishing pages. The threat can compromise systems, steal data or credentials and more.
- Man-in-the-middle (MitM) attacks: MitM attacks happen when hackers intercept the legitimate email correspondence of two parties, allowing attackers to eavesdrop or manipulate information. MitM attacks can compromise user information and allow hackers to bypass security controls such as MFA.
- Ransomware: Ransomware is an invasive type of malware designed to encrypt files so hackers can demand a ransom for their release. Email remains the top method of distributing ransomware.
Phishing
One of the oldest forms of email security risks, often jokingly referenced in terms of Nigerian Prince scams. While it can also be delivered via text, chat, and other methods, phishing is typically delivered via email. Modern phishing emails impersonate a known brand with the purpose of tricking a recipient into clicking on a malicious URL. The URL leads to a phishing page that looks legitimate and includes a form designed to capture a user’s login credentials. When a user fills out the form, their account information is stolen by the phisher.
These attacks are most often used en masse and for relatively low stakes such as hacking consumer streaming accounts or social media sites. It becomes a much more significant threat when a successful phishing attack occurs on a business device, or an account that shares an email or password with a user’s business account. Phishing attacks are relying on the law of numbers to succeed, and to utilize the information gained for more sophisticated attacks, such as spear phishing (detailed below).
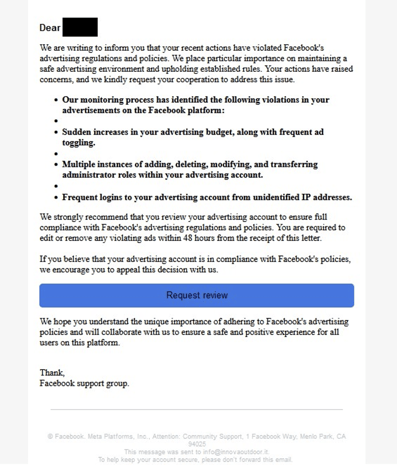 Facebook phishing email detected by Vade
Facebook phishing email detected by Vade
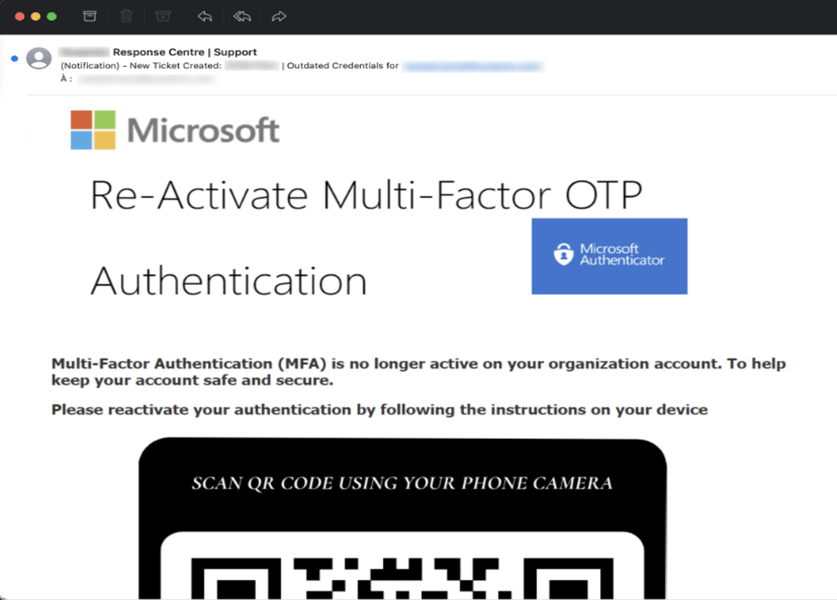
QRishing email
Spear Phishing
Unlike phishing, spear phishing, also known as business email compromise (BEC), attacks are highly personal and targeted email attacks designed to trick users into fulfilling a request. Spear phishing emails tend to impersonate people rather than brands. Often, spear phishers impersonate colleagues, business partners, vendors, and other acquaintances.
A typical spear phishing email is short and to the point, and includes only text. The most common spear phishing scams include the gift card request, CEO fraud (wire fraud), and tax fraud.
Spear phishing is also commonly referred to as Business Email Compromise (BEC), as gaining illicit access to business accounts is one of the top outcomes of such attack campaigns. In BEC attacks, the spear phishers will often impersonate the CEO of the organization, asking for gift cards, wire transfers, or to simply “reply as soon as you can.” They can also reverse the trend, pretending to be a more junior employee asking for their direct deposit to be re-routed to a new bank.
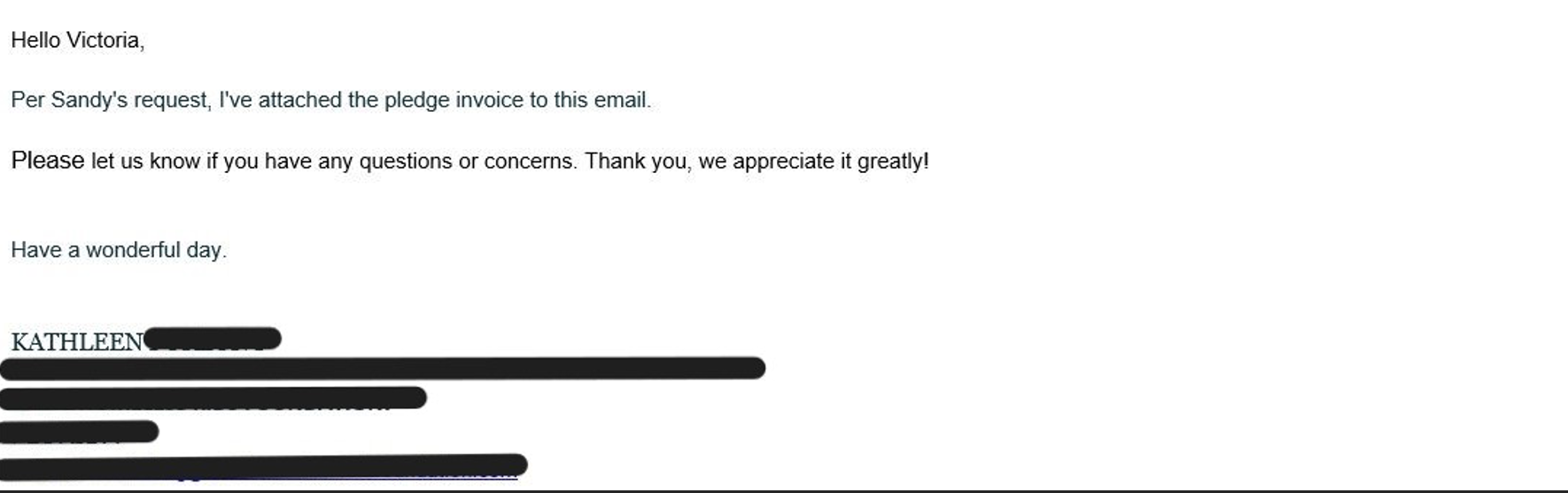
Spear phishing email
Malware
Malware is a catch-all term for computer viruses, which are often distributed via email links and attachments. Malware comes in many forms and with varying levels of sophistication. Most malware viruses are designed to download on a user’s computer without their knowledge or without arousing suspicion. This is often accomplished by disguising malicious attachments with filenames like “invoice” or “pay stub”, or by sending users to a website where the malicious code downloads in the background.
Some malware uses a variation of social engineering by displaying a flashing popup, urging users to download anti-virus software or warning that a virus is on their machine. Of course, once the user clicks the pop up, they install the actual virus.
Once the malware has been downloaded via a link or attachment, cybercriminals can spy on users, steal account credentials and digital assets, replicate themselves, or spread to other systems.
As with phishing attacks, initial malware attacks are often targeted at gathering information or credentials rather than immediately crippling a user’s system. One example that occurred in large numbers during the COVID-19 pandemic was the installation of cryptocurrency mining software. Malware would install mining software that ran in the background of a user’s machine, leeching resources without the user’s knowledge. For many users, the discovery of this malicious software only occurred after their hard drive or video cards were irreparably damaged.
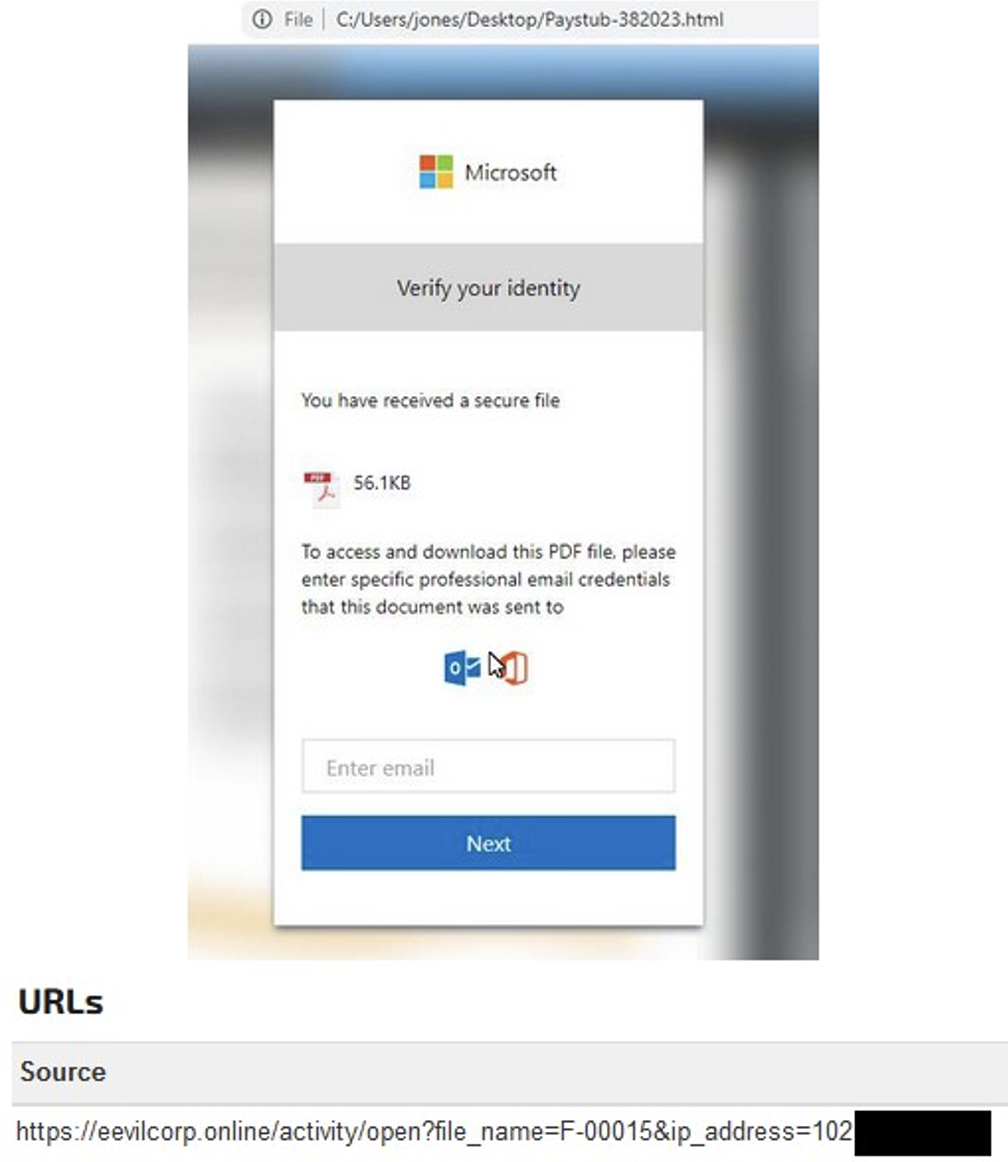
Phishing page spoofing Microsoft and suspected to distribute malware
Man-in-the-middle attacks (MitM)
A MitM attack happens when hackers intercept the communication between two parties and secretly relay or possibly alter the messages exchanged. Hackers can read, modify, or even inject malicious content into emails, potentially leading to data theft, unauthorized access, or the spread of malware.
These attacks can be prevented by authenticating access through another channel of communication. This is a major reason for multi-factor authentication (MFA), which ensures hackers cannot verify themselves without the user’s knowledge.
Ransomware
Ransomware is a specific type of malware that encrypts a user’s computer, denying access to all applications and data. In most ransomware attacks, the virus triggers a ransomware message on the user’s computer screen, demanding a ransom in return for a decryption key.
When the device that has been encrypted and locked is a recreational tablet, the damage seems minimal, but ransomware attacks have crippled major healthcare networks, government agencies, and large enterprises. At that scale, the ransomware attack is likely orchestrated by a cybercriminal organization. Early successful phishing attacks, spear phishing, or malware installations are often the pathways that hackers use to initiate a truly devastating ransomware attack.
How malicious emails can affect your organization
Malicious emails can have severe consequences for organizations, including financial, legal, regulatory, and reputational. Financially, cyberattacks can result in stolen intellectual property, sensitive data, or funds. It can also lead to downtime or disruptions to business continuity.
At the same time, attacks on organizations can jeopardize the confidence of prospects and customers, especially in the case of high-profile data breaches. In the event customer data is stolen or clients are targeted because of a cyberattack, organizations can also face significant legal liabilities.
Privacy regulations—such as the General Data Protection Regulation (GDPR) in the EU and the Health Insurance Portability and Accountability Act (HIPAA) in the US—can pose stiff penalties on organizations that fail to protect the privacy of consumer data. GDPR, for example, may fine organizations up to 4% of their annual revenue or €20 million for severe compliance violations, whichever is greater.
Overall, the consequences of malicious emails can be far-reaching, making it crucial for organizations to implement robust email security measures to protect against these threats.
Benefits of email security
Implementing email security measures offers numerous benefits to organizations, including safeguarding their sensitive information and protecting their business continuity.
- Protection against most common and costly cyberattacks: Email security solutions are designed to protect against the top cyberthreats for organizations. This includes phishing, which is the most common threat by victim account, and spear phishing, which is the costliest threat according to the Internet Crime Complaint Center (IC3). Email-based threats are a leading cause of security incidents and data breaches. According to IBM’s Cost of a Data Breach Report 2023, the average cost of a data breach has reached record levels, with small to midsized businesses (SMBs) especially impacted. In 2023, organizations with 500 or fewer employees saw their average cost of a data breach rise by 13.4% year-over-year (YoY) to reach $3.31 million (USD).
- Improved remediation of security incidents: Cybersecurity isn’t a perfect science when it comes to detecting threats. Security incidents are inevitable, but only with adequate email security can organizations identify and remediate potential incidents before they can cause more damage. This clearly remains a pain point for many organizations. It takes organizations an average of 217 days to discover a data breach caused by phishing and another 76 days to contain it, according to IBM’s Cost of a Data Breach Report. Overall, only a third of organizations that experienced a data breach in 2023 discovered it internally—likely exacerbating the reputational, financial, and regulatory consequences of the attack.
- Enhanced stakeholder trust: Email security protects against threats that can damage an organization’s reputation in the eyes of their customers, prospects, and partners. This includes limiting the chances of a data breach, supply-chain attack, or compromised account that can be used to target external parties. In 2023, businesses that experienced a data breach incurred losses of $1.3 million on average due to lost revenue from client turnover, weakened sales, and disruptions to business continuity. This figure represented roughly 30% of the overall cost of the breach.
- Enhanced business continuity and productivity: Email security measures help maintain business continuity by reducing the risk of closures or downtime caused by email-based attacks. They also preserve productivity from time wasted by a successful cyberattack. Ransomware, which is primarily distributed via email-based attacks, resulted in an average downtime of 25 days for businesses in H1 2022. This figure represents the global average.

There are a number of email security best practices that can help keep your organization safe from email threats. While technology plays an important role in defense, people are also critically important to email security and can be the last line of defense when a business is attacked.
1. Deploy an advanced email security solution.
Implement a robust email security solution that uses a combination of AI-powered technology and human insights to protect against sophisticated attacks. Look for solutions that offer comprehensive and robust features for threat prevention, detection, and response. Solutions that utilize machine learning or natural language processing are better equipped to monitor for and detect spear phishing attacks.
2. Implement multi factor authentication (MFA).
Strengthen your security by requiring users to provide multiple forms of verification before accessing their accounts. For example, this may include a password and a unique code sent to a mobile device. This reduces the risk of unauthorized access to email accounts. For the best security, use multi-factor authentication that requires verification through multiple channels of communication (i.e., a code generated on a mobile device to grant access on a desktop). This helps prevent man-in-the-middle attacks and significantly increases the difficulty for credential theft.
3. Enforce strong passwords and frequent password rotations.
Encourage users to create strong, complex passwords to minimize the chances of password-based attacks and unauthorized access to email accounts.
4. Establish a user awareness training program.
Educate users about email security best practices, such as identifying phishing attempts, avoiding suspicious links, and reporting potential threats. A phishing awareness training program can enhance their awareness and reduce the likelihood they fall victim to email-based attacks.
5. Deploy user awareness training software.
Rather than classroom-based instruction, look for simulated training solutions that administer automatically and provide users with personalized instruction tailored to their role and context in the organization. Better yet, implement user awareness training that offers contextual training based on user actions.
6. Hover over links in emails to see the final URL.
Encourage users to hover their mouse over links in emails to view the actual destination URL before clicking, enabling them to identify and avoid malicious links that may lead to phishing websites or malware downloads. If you utilize an email security solution that rewrites URLs to check them for safety, this step can be ignored.
7. Do not open attachments from unknown recipients.
Advise users to exercise caution when receiving email attachments from unfamiliar senders, as they may contain malware or other malicious content that can compromise their systems. When in doubt, instruct your users to forward emails to the cybersecurity team. If the email seems like it could be important, start a new email thread to contact the sender to verify its authenticity. Even better, if you think you know the sender, call them directly (change your communication channel) to verify the email. Remember that Spear Phishing often preys on a user wanting to help the person on the other end, or that they won’t be vigilant.
What is an email security policy?
An email security policy refers to a set of rules and procedures to ensure the safe and responsible use of email with an organization. This includes requirements for how employees should handle sensitive information, report suspicious emails and activities, and adhere to security protocols.
As an example, an email security policy may outline how employees should report phishing attempts or other suspicious emails to their IT administrator.
The email security policy should be clearly written in easy-to-understand language, be easily discoverable by company employees, and be regularly updated with industry best practices. The goal of the policy should be to make it as easy as possible for users to understand how email is protected in the organization, and how they can contribute to email security as an individual within that organization.
By implementing an email security policy, organizations can create a culture of cyber vigilance. This can strengthen their security posture and minimize the chances they experience an incident.
How to choose the right solution for your business needs
When selecting an email security solution for your organization, there are several key factors to consider.
- Integration with productivity suites: Opt for email security solutions that integrate with your productivity suite, as this adds another layer of cybersecurity onto native security features. Other solutions, such as secure email gateways (SEGs), disable these features and their benefits.
- Detection capability and accuracy: Look for solutions that can detect both known and novel or emerging threats and do so while minimizing the rate of false positives and negatives. Advanced AI algorithms, natural language processing, and machine learning combined with real-time data insights from a large statistical sample help in this regard.
- Real-time filtering with no quarantining: To ensure the timely flow of legitimate communication, focus on solutions that don’t quarantine emails to evaluate their toxicity. When a manual evaluation is required, this can add hours of overtime to the IT team’s workload. Instead, opt for solutions that can determine a verdict in real-time.
- Post-delivery remediation: Cybersecurity moves fast, and new intelligence surfaces every moment. Favor solutions that automatically remove suspicious emails post-delivery based on new findings. Better yet, seek solutions that automatically remove suspicious emails and provide detailed reporting on the emails as to why they were removed. You may be able to identify trends that warrant additional training for users, or can alert at-risk individuals of increases in attempts to spear-phish them.
- Feature set for incident response: Many email security solutions emphasize detection at the expense of incident response. All cybersecurity functions are important, including those that can help protect you at your most vulnerable moments. Look for solutions that allow you to quickly access and remediate user reports of suspicious messages. Also prioritize solutions that enable you to investigate threats safely and securely. This includes detailed email logs and tools for inspecting attachments with no risk to administrators.
- User interface: Opt for solutions that provide you with a single pane of glass view for managing your email security from start to finish, including remediating user reports, investigating forensic evidence, and more. Being able to drill down into the details is important, but equally so is the high-level view that you can take to report to your stakeholders.
- Extended protection for malicious websites: Email is the top vector, but the damage often occurs via phishing pages. Prioritize solutions that enable you to protect users that get redirected from a malicious email link to an unknown website.
- Integration with other cybersecurity solutions: Rather than adopting an all-in-one solution, best practice is to assemble a collection of best-of-breed solutions for your cybersecurity stack. The ability for these solutions to “speak” to one another is paramount to coordinated intelligence and effective response. Opt for solutions that cross-pollinate intelligence across your entire cybersecurity stack, including Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), or Extended Detection and Response (XDR) systems.
By considering these factors, organizations can choose an email security solution that aligns with their specific business needs and provides effective protection against evolving email threats.
Protect your inbox with Vade
Safeguard your mailbox with Vade, a global cybersecurity company that combines AI and human-powered detection and response to ensure secure human collaboration. Vade's comprehensive range of products and solutions protect individuals, businesses, and organizations from a wide array of email-based cyberattacks, including malware/ransomware, spear phishing/business email compromise, and phishing attempts.
With a rich history dating back to 2009, Vade safeguards over 1.4 billion corporate and consumer mailboxes, catering to the ISP, SMB, and MSP markets. Our award-winning products and solutions not only enhance cybersecurity but also optimize IT efficiency, making Vade a trusted choice for protecting your email communications.
FAQs
- What’s the difference between Office 365 email security and Microsoft 365 email security?
While Office 365 and Microsoft 365 email security are used interchangeably, they share slight differences. Office 365 and Microsoft 365 are two different subscription bundles offered by Microsoft to businesses. Both productivity suites include many of the same business applications. Most of their plans also offer Exchange Online Protection (EOP), Microsoft’s native email security solution. However, only Microsoft 365 plans include the option for Microsoft Defender, Microsoft’s more advanced email security solution than EOP.
Despite this difference, most integrated, third-party email security solutions work with both Microsoft 365 and Office 365 plans.
- Is Office 365 email security or Microsoft 365 enough?
The Office 365 productivity suite includes native security features that protect against email threats such as some types of malware. While beneficial, these features don’t provide adequate protection against many of today’s more advanced cyberthreats. That explains why Gartner recommends that organizations augment the security features in Office 365 with an integrated, third-party email security solution. An integrated solution complements the email security of Office 365 and provides additional protection against the threats that Microsoft misses.
- How do I make my Office 365 email more secure?
Use a combination of measures to fortify your Office 365 email security. Start by adopting an integrated email security solution from a reliable third-party vendor. Implement user awareness training to make users proficient at recognizing and handling cyberattacks. Also, encourage your users or colleagues to be vigilant in reporting suspicious emails using Office 365’s reporting features.
- How can I improve my email security?
Adopt an email security solution that integrates with Microsoft 365, Google Workspace, or another productivity suite. This provides the benefit of layered protection onto native security features and can catch advanced threats, including known and unknown. Also, ensure you implement a phishing awareness training program and opt for one that can be delivered electronically and automatically.






