5 Common Phishing Techniques
Romain Basset
—October 03, 2019
—3 min read

Most email security filters are highly effective at ensuring that spam messages never make it to the inbox. However, they’re far less effective at blocking phishing, which has proven to be a more difficult issue to solve. Today’s phishing techniques are highly sophisticated, they’re bypassing email security filters, and they’re targeting your clients and employees.
A well-crafted phishing email is nearly—if not completely—identical to a real email from a known brand. Victims click on phishing links from well-known brands like Microsoft and Facebook, believing they’re logging into a trusted account. In some phishing attacks, victims unknowingly give their credentials to cybercriminals. In others, victims click a phishing link or attachment that downloads malware or ransomware onto the their computers.
The following phishing techniques are highly sophisticated obfuscation methods that cybercriminals use to bypass Microsoft 365 security. In these types of phishing attacks, they’re invisible to the user and easily bypass Exchange Online Protection (EOP) and secure email gateways (SEGs).
1. Using legitimate links
Most email filters scan for known phishing URLs. To evade detection, phishers add legitimate links to their phishing emails. Many email filters will scan a number of legitimate links and assume the email is clean. In recent Microsoft 365 phishing emails detected by Vade, the phisher included a legitimate reply-to email address and legitimate links to Microsoft’s community, legal, and privacy webpages. They also included a link to Microsoft’s contact preferences page, where users can update their preferred communications settings for applications like SharePoint and OneDrive.
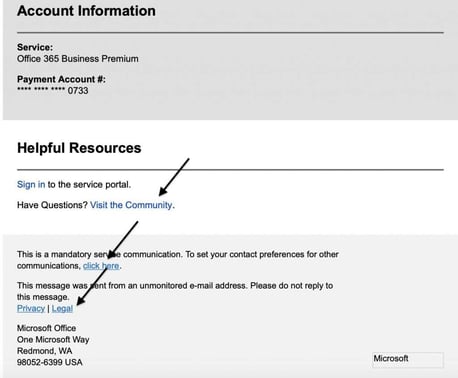
In the below example of a Wells Fargo phishing email detected by Vade, the phisher even included a link to the bank’s fraud information center.
2. Mixing legitimate and malicious code
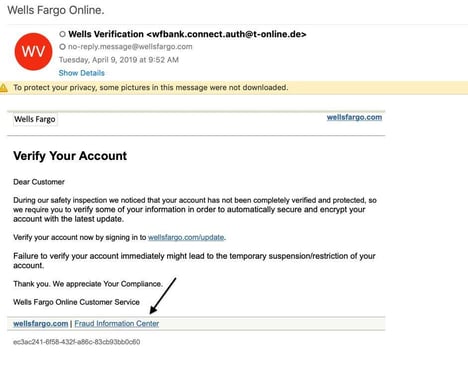
A known phishing email or malware virus contains a signature that can be detected by EOP. One technique for obfuscating the signature is to mix legitimate and malicious code. Sophisticated Microsoft phishing pages, for example, include CSS and JavaScript from real Microsoft webpages, such as the Office 365 login page. Other techniques include encoding characters at random, adding invisible text, inserting white spaces, and assigning random values to HTML attributes. The goal of mixing legitimate and malicious code is to make each email appear unique to the filter, making these types of phishing attacks nearly impossible for signature-based filters to detect.
3. Abusing redirections and URL shorteners
Time is of the essence in phishing. To quell victims into thinking that nothing is awry, phishers will redirect them to a legitimate webpage after the phishing attack. For example, after a user enters their Office 365 credentials on a phishing page, they are directed to Office 365.com or another Microsoft webpage.
Another form of redirect abuse, “time-bombing” is a phishing technique that involves creating a URL redirect from a legitimate webpage to a phishing page. Time-bombing is highly effective because the email includes a legitimate Microsoft link at the time of delivery when it is initially scanned by an email filter; the redirect to the phishing page is only created after the email has been successfully delivered to the victim.
In another phishing technique designed to obfuscate a known phishing URL, phishers use URL shorteners such as TinyURL and Bitly. These free tools transform long URLs into shortened URLs—aliases that have no resemblance to the original URL. Most email filters that are scanning for a signature will not recognize it in a shortened phishing URL.
4. Distorting brand logos
Like other elements of known phishing pages, logos include HTML attributes that can be detected by an email filter that is scanning for signatures. To avoid detection, phishers alter brand logos in ways that are invisible to the naked eye but unique to a filter. For example, by changing an HTML attribute such as color or shape by a single character, the signature will be different from a known phishing page, therefore unique. This slight change is enough to fool an email filter that scans for malicious content but cannot analyze the rendering of an image as a human would.
5. Confusing the filter with little content or excess noise
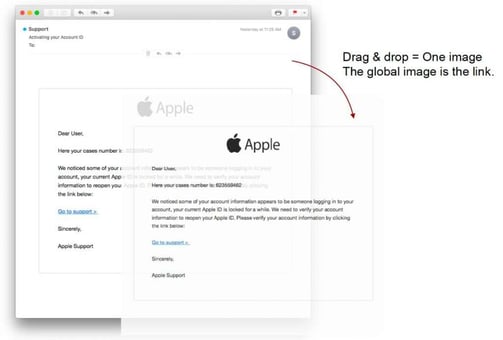
Some cybercriminals evade detection by including little to no content in their phishing emails. One version of this attack that we’re seeing more of is use of an image instead of text, although this is not obvious to the victim. This is a common phishing technique used in sextortion emails, including the mass wave detected in 2018. With no content to scan, the filter could be fooled into thinking the email is safe. In the below example, the text you see is actually an image.
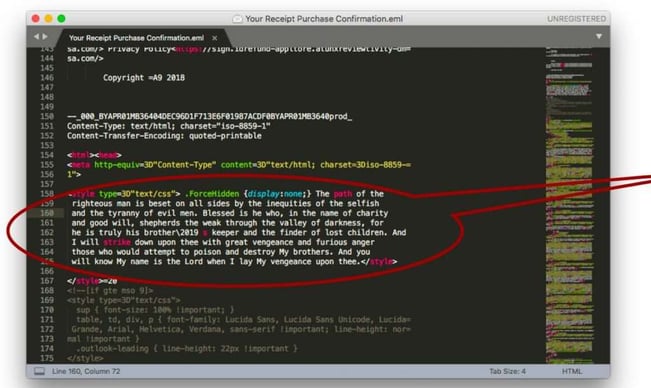
The opposite approach is to stuff an email with excess content or “noise.” This technique works because of the randomness of the code. It has no purpose, no meaning, and therefore confuses the filter. In the below example, the phisher stuffs the code with a line of dialogue from “Pulp Fiction”:
What can you do to protect your clients?
The increasing sophistication of phishing attacks mandates more sophisticated countermeasures. Traditional email filters are not enough. Clients that use Microsoft 365 need to add another layer of phishing protection to protect themselves from these types of phishing attacks.
Vade for M365 scans for the above phishing techniques by crawling URLs and webpages in real-time, identifying the signature obfuscation methods that EOP and SEGs will miss.




