Email Security Predictions: Insights & Trends for Businesses
Natalie Petitto
—December 09, 2021
—3 min read

It’s that time of year when we make our predictions about the biggest email security threats that will emerge in the coming year. Vade’s experts weigh in on the threats that will have the biggest impact on businesses in 2022.
1. Remote work will inspire novel attacks
Once a perk offered to the privileged few, remote work has gone mainstream. In some industries, it has become a must-have for attracting and retaining workers. But home offices come with distractions, and those distractions have opened the door for a litany of cyberattacks. Email scams increased exponentially since the start of the pandemic. It remains a tried-and-true tactic that is showing no signs of slowing but raising red flags in the way of novelty.
According to Damien Riquet, Research Engineer at Vade, isolated employees will continue to be targeted with IT and tech support scams. Earlier this year, Vade discovered a tech support scam impersonating Norton, McAfee, LifeLock, and Windows Defender. The emails lured victims with fake invoices and urged victims to call a phone number to stop the payment. Vade filtered one million of these emails during a two-week period, with a single-day high of 200,000.
Nicolas Joffre, TIRC America – Manager at Vade, said the tech support scams continue to this day. “They’re using a number of techniques to bypass filtering,” Joffre said, “including telephone number obfuscation, use of images, and sending from high reputation domains, such as gmail.com.” Joffre anticipates new techniques to emerge as filters get better at recognizing the attacks.
Other scams will focus on the pandemic itself, including vaccines, and use emotional triggers to target remote workers. “Hackers are always waiting for the next controversy or big current event to leverage in their attacks,” said Adrien Gendre, Chief Product and Services Officer at Vade. “They will continue to monitor the evolution of the pandemic, including vaccine efficacy and new treatments.”
2.Phishing’s image problem will get worse
Phishing attacks that use remote images, screenshots, and image manipulation techniques have been on the rise for the last few years. According to Damien Alexandre, R&D Engineer at Vade, as technologies like Computer Vision improve and adapt to recognize image-based phishing, old techniques will evolve and new techniques will emerge.
Below is an example of image analysis in action. Optical Character Recognition (OCR) is used to extract the text from the image, followed by text analysis with Natural Language Processing (NLP). Together, these technologies recognize that this image is hiding something and discover its true purpose.
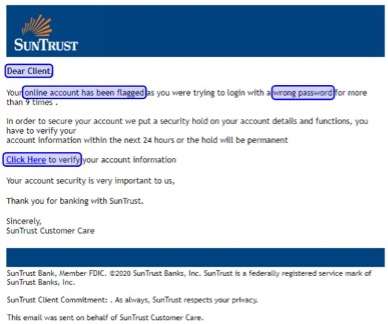
In 2022, hackers will evolve their techniques to get better at concealing image-based phishing emails. “Right now,” Alexandre said, “brand impersonation and procedurally generated graphics are being used to bypass image analysis technology, including using HTML and CSS to display brand logos like Microsoft and Chase.” This "phishing logo" technique is successful because image analysis technology sees code instead of the image, allowing the phishing emails to bypass detection. Image-based phishing, Alexandre said, will become more sophisticated by the day and keep pace with the security technology designed to block attacks.
3.AI will be used against us
The merits of using AI in cybersecurity are clear. What is also clear is that hackers have equal access to the technology and will use it for nefarious reasons. “Targeted attacks have become the norm,” said Gendre, “and hackers are receiving a lot of help from automation. AI has the potential to assist hackers in industrializing their processes, right down to generating the emails.”
Personalization, Gendre says, is one way that AI will assist hackers in launching attacks. “There is a lot of work that goes into creating targeted attacks,” Gendre said. “AI has the potential to change that. AI not only takes the onus off the hacker but also allows the hacker to industrialize the process.”
Cybercrime gangs are already industrializing, operating like traditional businesses with high levels of organization. “We see this with ransomware gangs,” Gendre said. “They have websites and affiliate programs,” Gendre said, “they have technical support and tiered subscription models. With help from AI, hackers can industrialize their businesses and their attacks in ways that we must be prepared to face.”
4.Middle men will be watching
Authentication technology, including MFA, is no longer an option but a requirement; however, MFA isn’t a silver bullet. While MFA is a powerful tool for preventing hackers from gaining access to privileged accounts, hackers have novel techniques for thwarting MFA.
According to Gendre, the prevalence of remote work will lead to an increase in man-in-the-middle attacks. Additionally, Gendre says, thanks to the increase in MFA adoption throughout the pandemic, hackers will hone their techniques to keep pace.
“As the move to the cloud accelerated during the pandemic,” Gendre said, “more businesses adopted MFA in response. As businesses roll out more authentication solutions, man-in-the-middle attacks and techniques will become more widespread.”
Getting ready for the challenges ahead
Supply chain attacks were the story of the year, aided in part by vendor impersonation and compromised accounts, two threats that made our predictions list last year. Both will continue to create enormous cybersecurity challenges for businesses, evolving along with the solutions designed to stop them.
With its ability to predict threats and detect anomalies, AI-based cybersecurity will become a requirement, the difference-maker that should be incorporated into every layer of the security stack. Combined with threat intelligence, AI will strengthen both detection and response capabilities across a variety of solutions, from email security to EDR to XDR.



