Microsoft 365 Phishing Email: Hackers Using a 20-year-Old Text Trick
Antoine Morel
—February 08, 2022
—5 min read

In the email security game between hackers and users, adversaries employ various forms of masquerading with a file to increase the likelihood that a user will open it. While Right-to-Left Override (RLO) attack is an old technique to trick users into executing a file with a disguised extension, this spoofing method is back with new purposes. Vade has detected more than 400 such attacks in the last two weeks using a Microsoft 365 phishing email.
What is a Right-to-Left Override attack?
Right-to-Left Override (RLO) is a non-printing Unicode character [U+202e] mainly used to support Hebrew and Arabic languages. Indeed, this character flips and changes all subsequent text to be right-to-left when displayed, instead of English's left-to-right reading order.
This special character can be found in the character map on Windows and Linux operating systems:
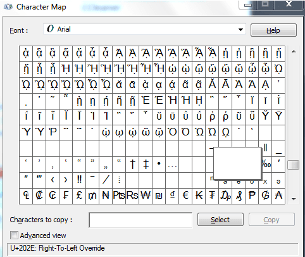
As an example, a file called "HelloVade" with the Unicode character added as "Hello[U+202e]Vade" will be displayed "HelloedaV".
This method was used in the nineties and early 2010s to trick users into executing malicious files, such as corrupted .exe applications, believing they were opening a .txt file:
- abc[U+202e]txt.exe will appear abcexe.txt in Windows, but this is an executable file.
Attackers were using this method to send malware across an organization. This age-old trick was already referenced in 2008 in the Mozilla Foundation and Unicode technical reports known as CVE-2009-3376.
With the emergence of security appliances, most of these attacks were detected, and malicious actors tried to adapt the technique. Indeed, they used the same method and the same files, but compressed into a .zip archive, making the detection more difficult for endpoint security technologies.
This method is still overlooked by email users today, and phishers have been taking advantage of the situation for the last few weeks, tricking users with Microsoft 365 phishing emails.
New Right-to-Left Override trend with phishing websites
While attackers were using RLO spoofing to masquerade malware in attachment, it looks like the purpose has changed and the technique adjusted.
With more than 250 million users, Microsoft 365 is the most used business productivity suite in the world, making it the no. 1 corporate target for hackers. The growth of Microsoft 365 has led to an onslaught of phishing attacks aimed at Microsoft 365 business users whose login credentials prove all a hacker needs to access a business’s data.
Having this in mind, it is not surprising to see an old, overlooked technique being adapted to masquerade Microsoft 365 phishing emails.
A recent phishing wave using a
The RLO spoofing method was combined with a voicemail context. Let's deconstruct this attack:
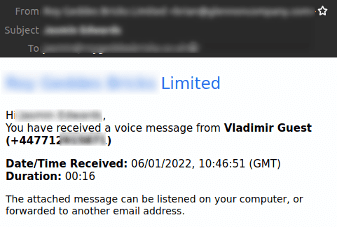
The complete message is a notification inviting the user to access the voicemail in attachment. Some parts of the email have been blurred for security reasons. The subject of the email contains the name of the recipient, and the date and time in the body are consistent with the actual timestamp. All these elements may convince the victim to trust the email and to open the file in attachment.
This kind of scam preys on curiosity of the recipient, who is not expecting a voicemail, and who maybe intrigued enough to click the phishing link in the body of the email or the attachment, which is often an html file. It leads to a phishing webpage encouraging the user to submit their credentials to access the voice message.
However, at first sight, the attachment ends with an .mp3 extension, so in the user's mind the attachment is, in all likelihood, an audio file containing the voice message.
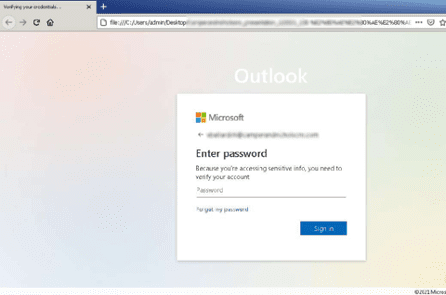
Opening the file in a safe environment leads to a Microsoft login webpage that requests credentials to access "sensitive info". We can see that the email address is already pre-filled, and the address bar actually contains the path to the .htm file saved on the computer. At this point, the user doesn't have the ability to check the legitimacy of this form. In hindsight, the user should have recognized the trap when opening an .mp3 file that leads to a webpage.
On submission of the Microsoft login form, the .htm page send user's data to an external domain, thanks to a "process.php" script:
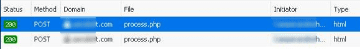
The HTTP POST request to a URL clearly not related to Microsoft actually contains the password filled in the form:
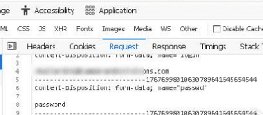
For this campaign, upon form submission, the page didn't redirect to another website but rather displayed that the password is incorrect. However, Vade's cyber analyst team confirms that in some cases, this type of form can redirect to a voicemail message that is readable and contains a generic message. The aim is to make users unaware of the attack they just experienced.
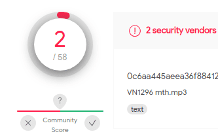
Users should easily detect this scam, especially when opening an .mp3 file that leads to a Microsoft login webpage. But it is also easy for users to fall into the trap if they don't pay attention to the extension. Moreover, you can't rely on security vendors to detect this kind of attachment as malicious— only two our of 58 did, according to VirusTotal:
Below is another example of an Right-to-Left Override spoofing campaign detected by Vade’s filtering engine:
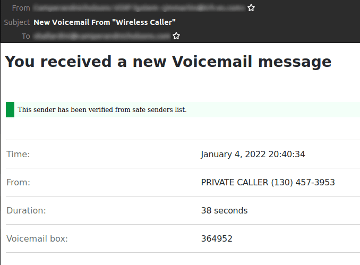
As you can see, the hacker is using the same voicemail context, but this time the caller is "private". In addition, he added a banner indicating that the email's sender belongs to Microsoft's safe sender list. The objective is to provide a false sense of security for users, who may not know that Microsoft would never add this green shield in the body of the email.
Vade Insights on Right-to-Left Override attack
Each RLO spoofing attack is unique, and attackers are using different headers, senders, subjects, and attachments to pass through basic security protection. The masquerade-based phishing was tracked by Vade at the beginning of 2018, but only in small amounts targeting individual businesses.
According to the statistics, it seems that Right-to-Left Override spoofing increased from mid-2020 and even more so in 2021. Most likely attackers are taking advantage of the COVID-19 pandemic, with the expansion of remote working: End users are less protected and prepared for external threats, and many are using their own endpoint security technologies at home rather than those of the company. Moreover, the voicemail context combined with RLO spoofing attachments is more convincing with the lack of interpersonal communication due to teleworking.
Below are some key figures for this particular phishing attack detected by Vade's Threat Intelligence and Response Center (TIRC). As you can see in the below image, more than 400 RLO Spoofing campaigns were seen in the last two weeks:
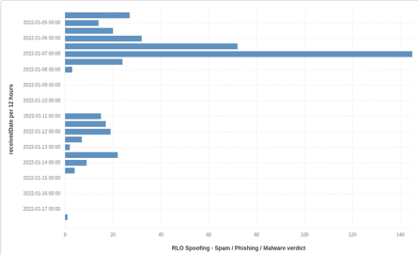
As for the attachments' extensions, two of them stand out from the crowd, according to the statistics:
- (l)mth.wav --> wav.htm(l)
- (l)mth.mp3 --> mp3.htm(l)
Protecting users from these types of spoofing requires an AI-based anti-phishing solution that analyzes not only signatures and reputations, but also behavior, content, and context—the full scope of possibilities and scenarios.
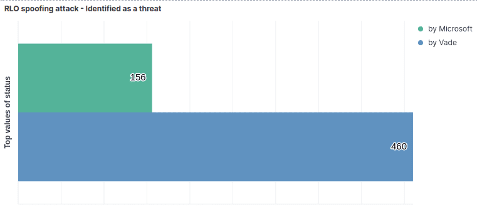
Combined with heuristic rules targeting RLO Unicode character, Vade’s Filtering Engine has excellent results in catching these types of campaigns. Indeed, Vade for M365 shows consistent added value compared to other email security solutions like Microsoft's EOP:
What's next with the Right-to-Left Override technique?
Cambridge University researchers Nicholas Boucher and Ross Anderson found a vulnerability which exploits Unicode control characters to encode potentially dangerous source code. The method named "Trojan Source" was made public on November 1st, 2021 and assigned CVE-2021-42574. This time again, the technique is to masquerade a source code which appears different to a human eye and to a compiler. Attackers can use bidirectional Unicode control characters such as RLO (U+202E) to disguise a file into a trojan.
According to the paper, "this attack exploits subtleties in text-encoding standards such as Unicode to produce source code whose tokens are logically encoded in a different order from the one in which they are displayed, leading to vulnerabilities that cannot be perceived directly by human code reviewers. ‘Trojan Source’ attacks, as we call them, pose an immediate threat both to first-party software and of supply-chain compromise across the industry."
This vulnerability leads to security weakness in code compilers, interpreters, IDE, and source code repositories, forcing organizations to release an update: "Compilers, interpreters, and build pipelines supporting Unicode should throw errors or warnings for unterminated bidirectional control characters in comments or string literals, and for identifiers with mixed-script confusable characters."
Proofs-of-Concept implementing various Trojan-Source attacks can be found on the official Github repository.
Right-to-Left Override is an old technique, but as long as people are unaware of the threat, attackers will continue to use it and reinvent it. One thing is for certain: RLO spoofing technique will keep getting dusted off in the years to come.




