Office 365 Security Best Practices
Adrien Gendre
—November 07, 2017
—3 min read

Committing to Office 365 security best practices is crucial for maintaining the integrity of your data. Here are several best practices recommended by Gartner, some or all of which you may already be familiar:

- Secure Email Content: It’s recommended you use multiple antivirus engines to increase detection and prevention of threats. For example, use one antivirus engine at the email gateway and use another for your endpoint systems.
- Review Secure Email Gateways: Review and consider SEGs that scan for URL links and attachments with active content that cannot be blocked by policy (such as PDF and Microsoft Office file types). Strip out or quarantine all executable content from email attachments, and ensure that all email content types and attachments are being evaluated for malware.
- Secure Mobile Devices: Recognize that all mobile devices must be equipped with endpoint security technologies, mobile device security, and secure Web and email gateway services because their network traffic does not pass efficiently through legacy network defenses.
While these best practices are all advisable, many malicious emails contain zero-day attacks with ransomware, viruses, and other malware that have never been seen before. No matter how committed you are to keeping up with best practices, these zero-day attacks can still slip through the cracks.
Vade Augments and Extends Office 365 Security Best Practices
The solution is Vade, a real-time scanner of email threats on a global scale that utilizes threat centers worldwide to analyze millions of messages every day.
Vade full email security solution aligns with many of the best practices described above, offering a way to extend a suggested best practice even further to better defend against cyber threats.

Vade augments several Office 365 security best practices in the following ways:
- We use a webpage exploration engine that protects email recipients from URL-based phishing attacks at the “time of click.” This technique can catch dynamic links as well as “sleeper” malware and phishing pages. Once a user clicks on a link in a message, the webpage is opened in a secure environment (proxy) to further verify its safety. This way, if the link is redirecting to malware, Vade will block it before it infects the user’s device.
- We enhance anti-phishing defenses by developing an overall sense of the user. Proprietary processes enable identification of one-off attacks by matching the style and technical indicators of the alleged sender of any given email with known information about the actual sender. To achieve this goal, our solution looks at multiple elements within every email. Behavioral analysis examines everything from file names and header fingerprints to the code and commands embedded in attachments. This is accomplished by a local machine learning system that complements our global network of machine learning systems in our threat centers.
- The Vade solution can also notify system administrators if users are clicking on suspicious links. The solution keeps track of original URLs, even if they are later changed. This is helpful for long-term security and building a solid email security strategy, as malware links are sometimes clicked in old emails.
Vade: An AI-Enabled Solution that Goes Beyond Signature-Based Protection
Vade recognized several years ago that filtering emails based on known malicious signatures was a never-ending, ever-accelerating game of whack-a-mole.

We knew we had to get ahead of the problem rather than just react to threats as they appeared. So, we developed an integrated artificial intelligence that has been trained specifically to find these zero-day threats. How did we do this?
To start, Vade processes billions of emails every day using Office 365 security best practices.
This gave us a very large data set to start training our artificial intelligence system to learn what malicious emails, phishing sites, and malware look like and how and where they vary.
Today, our system is capable of reliably identifying one-off spear phishing emails, sensitive data requests, and zero-day malware hidden in executable files, PDFs, Office documents, and more.
Vade machine learning is constantly getting better and more complex.
New rules and information pertaining to these threats are constantly being updated into our email security gateways and deployed globally by our 24/7 global threat assessment centers.
In addition to our AI-based security, Vade also offers the following advanced defenses:
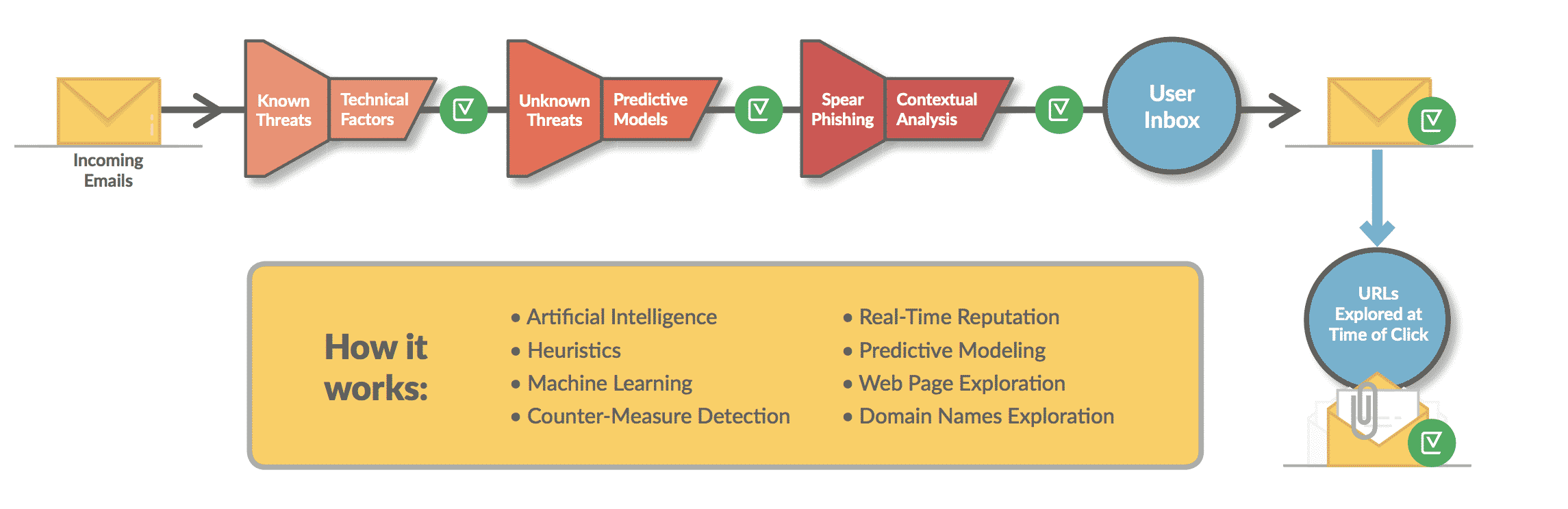
- Initial Filtering: Emails are analyzed for known phishing and malware signatures, including executable files. This quickly weeds out all spam and mass attacks.
- Anti-Malware: We read the code embedded not just in executable files but in Office documents, PDFs, and more.
- URL Sandboxing: All URLs are examined to be sure they do not link to malware, phishing sites, or any other malevolent site. This is done whenever the URL is clicked on… thus avoiding time-bombed URLs.
- Human Intelligence: Vade mans a 24/7 global threat intelligence center with email security experts.
Interested in learning more about our solution design specifically with Office 365 in mind? Download our eBook or contact us.



