Phishers’ Favorites 2023 Report: Facebook is the Most Impersonated Brand, Phishing Emails Hit 1.76 Billion
Todd Stansfield
—February 06, 2024
—7 min read

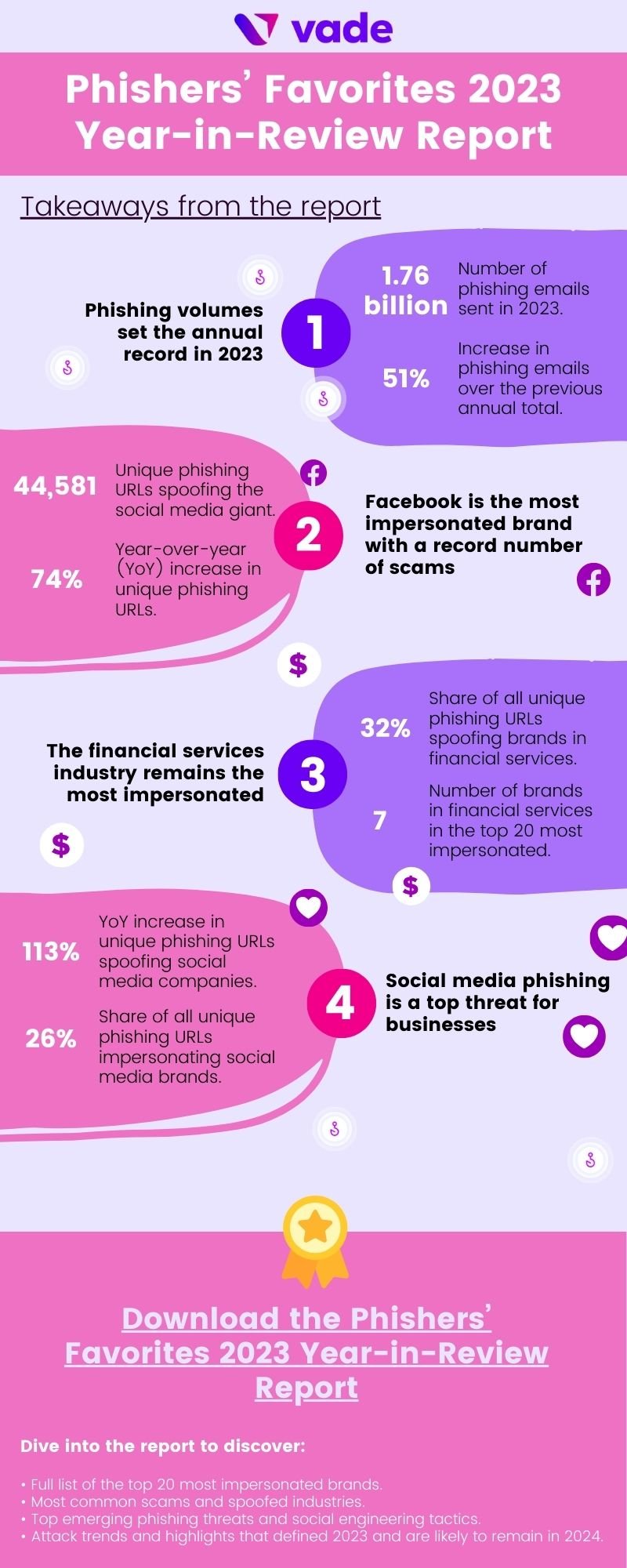
Today, Vade released the Phishers’ Favorites 2023 Year-in-Review Report, an annual analysis of the top phishing threats and trends that defined the period. The year proved remarkable on a number of fronts. Phishing emails broke records. Facebook scams reached their highest mark. Microsoft spoofing remained as popular as ever. Hackers increased attacks on businesses and consumers relying on social media platforms.
In this post, we dive into the highlights from the report and offer the opportunity to download our full analysis.
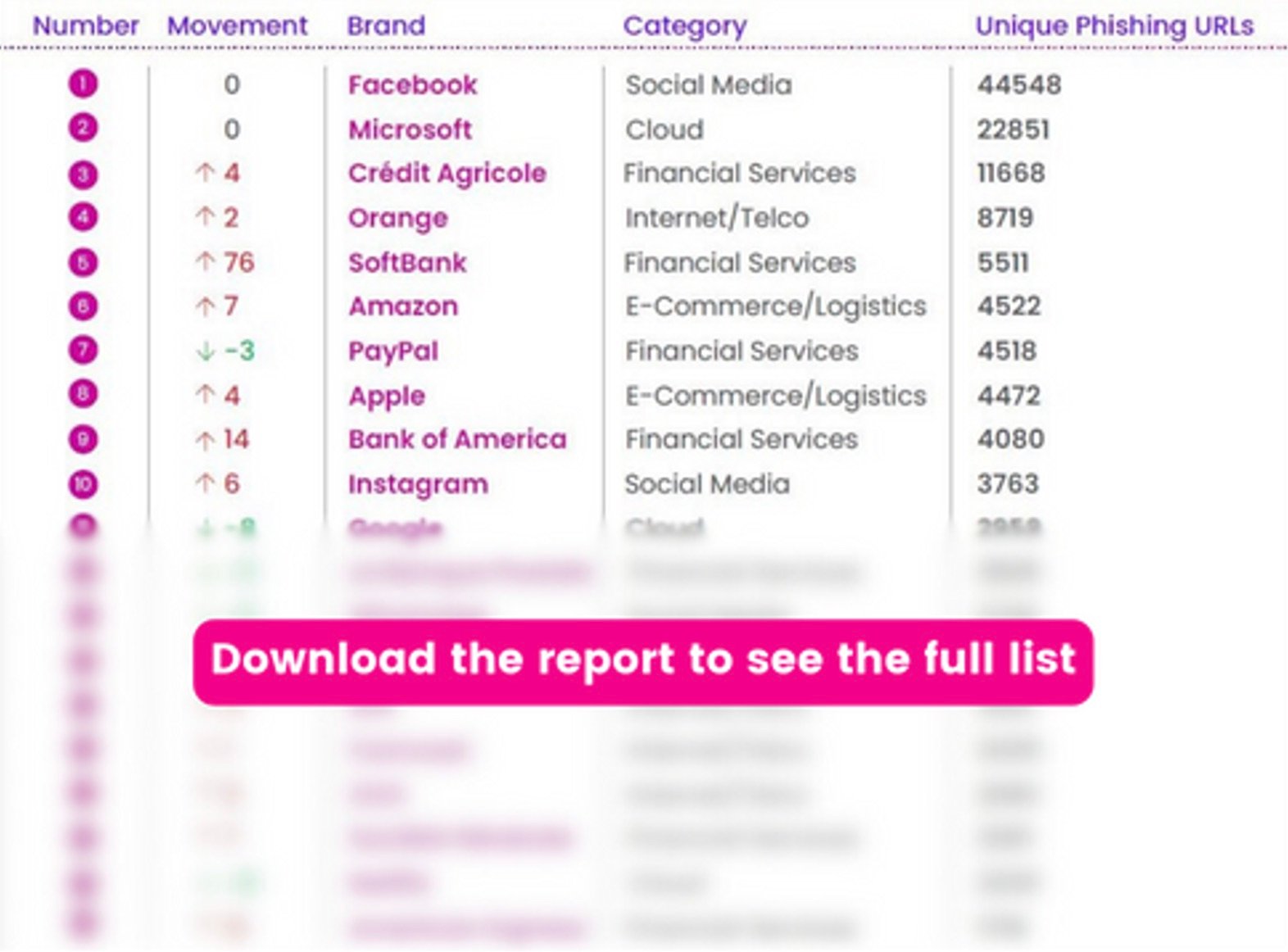
The top 20 most impersonated brands in phishing attacks
In 2023, brands featured in the Phishers’ Favorites report accounted for more than 197,000 unique phishing websites. While the uniqueness decreased by 28% year-over-year (YoY), the figure accompanies a period that saw the highest annual total of phishing URLs sent globally on record (more than 1.76 billion).
For the third straight year, Facebook was the most impersonated brand, nearly doubling the unique phishing URLs of the runner up on the list, Microsoft. Facebook accounted for more than 44,000 branded phishing websites—representing 23% of phishing URLs from this year’s list. The brand also set an organizational record, eclipsing any other year to date since Vade began tracking these statistics. While impersonation attempts increased 74% YoY, most of this increase happened during H2. In Q3, Facebook saw a 169% increase in unique phishing URLs QoQ. In Q4, volumes held steady, falling slightly by 5%.
This year's figures only further strengthened Facebook's reign as the most impersonated brand, continuing the trend for the third straight year. The brand's popularity among hackers illustrates the prominence of social media phishing as a vector.
While Facebook’s phishing stats stand out, Microsoft also finished 2023 as a perennial phishers’ favorite. Since 2022, the cloud leader saw a slight increase (1% YoY) in unique phishing URLs to finish at more than 22,000. Microsoft accounted for nearly double the total of the next place finisher.
While Facebook and Microsoft made headlines, Crédit Agricole finished as the third most spoofed brand, after ending 2022 in the seventh spot. The company led all other financial services brands with more than double the number of unique phishing URLs than the next place finisher. This represents the second time since 2021 that the brand has finished as the third most spoofed brand.
Rounding out the remainder of the top ten were Orange, SoftBank, Amazon, PayPal, Apple, Bank of America, and Instagram. Orange and Amazon both ended the year leading their respective industries (Internet/telco and e-commerce/logistics). After ending 2021 and 2022 in sixth place, Orange for the first time broke into the top 5.
Notably, SoftBank, Amazon, Bank of America, and Instagram all finished outside the top 10 in 2022. Among these brands, SoftBank made the biggest jump from 2022 to 2023, moving up 76 spots to finish in the top 5.
Google, which finished 2022 as the third most spoofed brand, ended the year in 11th place.
In other notable developments, SFR and American Express also entered the top 20, while MTB, au, WellsFargo, Rakuten, Credit Saison, Adobe, and Santander dropped out. Meanwhile, La Banque Postale, WhatsApp, DHL, Comcast, OVH, Société Générale, and Netflix all featured among the top 20 for at least the second consecutive year.
Phishers’ Favorites 2023: 20 most impersonated brands
Phishers’ Favorites 2023: 20 most impersonated brands
Social media phishing reaches a new level
Social media phishing has loomed as a top threat for organizations and consumers alike. This year’s data only reinforced that reality, illustrating that it remains a favorite scam among phishers.
In a year when unique phishing URLs decreased for most industries, social media saw volumes increase by more than 113% YoY, with cloud the only other to experience an uptick (4%). Facebook clearly was responsible for social media’s rise, yet Instagram, WhatsApp, and LinkedIn all contributed. Instagram ended the year as #9 on the list, followed by WhatsApp (#13) and LinkedIn (#23). Instagram and WhatsApp are no strangers to the top 20. Their inclusion continued a trend for the third straight year, while LinkedIn made appearances on the list in 2020 and 2021.

Facebook phishing page detected by Vade

Instagram phishing page detected by Vade
While platforms like Facebook and Instagram are often viewed as consumer-focused, it's important to remember they play an important role for businesses. Organizations of all sizes depend on these social media platforms for sales, marketing, recruiting, and hiring. A global survey of marketers found that nearly 90% use Facebook to promote their business, while 80% use Instagram for the same purpose. Unsurprisingly, Facebook’s global advertising revenue is forecasted to reach 127 billion (USD) by 2027, a new record after years of sustained growth.
Meanwhile, LinkedIn remains a popular platform for business-to-business (B2B) sales and marketing, as well as talent management. Recent estimates suggest its ad revenue could nearly double between 2022 and 2027.
Yet the incentive to impersonate social media brands goes beyond the importance of these platforms to consumers and organizations. Compromising social media accounts offers the opportunity to gain unauthorized access to other business applications. Recent reports show that more than 50% of workers globally reuse the same password for all work accounts. And for small-to-midsized businesses (SMBs), this practice tends to be more prominent, as many lack formal security policies or personnel. This increases the risk of hackers using compromised credentials for social media accounts to gain unauthorized access to other important applications.
Phishers’ Favorites 2023 Year-in-Review Infographic
The financial services industry remains the most impersonated sector, with social media making a leap
2023 proved to be another typical year for financial services, with the industry retaining its status as the most impersonated by hackers. The sector led all others in terms of total unique phishing URLs (64,009 or 32% of the overall total), followed by social media (51,183 or 26%), cloud (43,350 or 22%), Internet/telco (19,291 or 10%), e-commerce/logistics (17,882 or 9%), and government (1,903 or 1%). Notably, social media took second place for the first time since 2021, swapping positions with cloud. All other sectors finished in the same spot as the prior year.
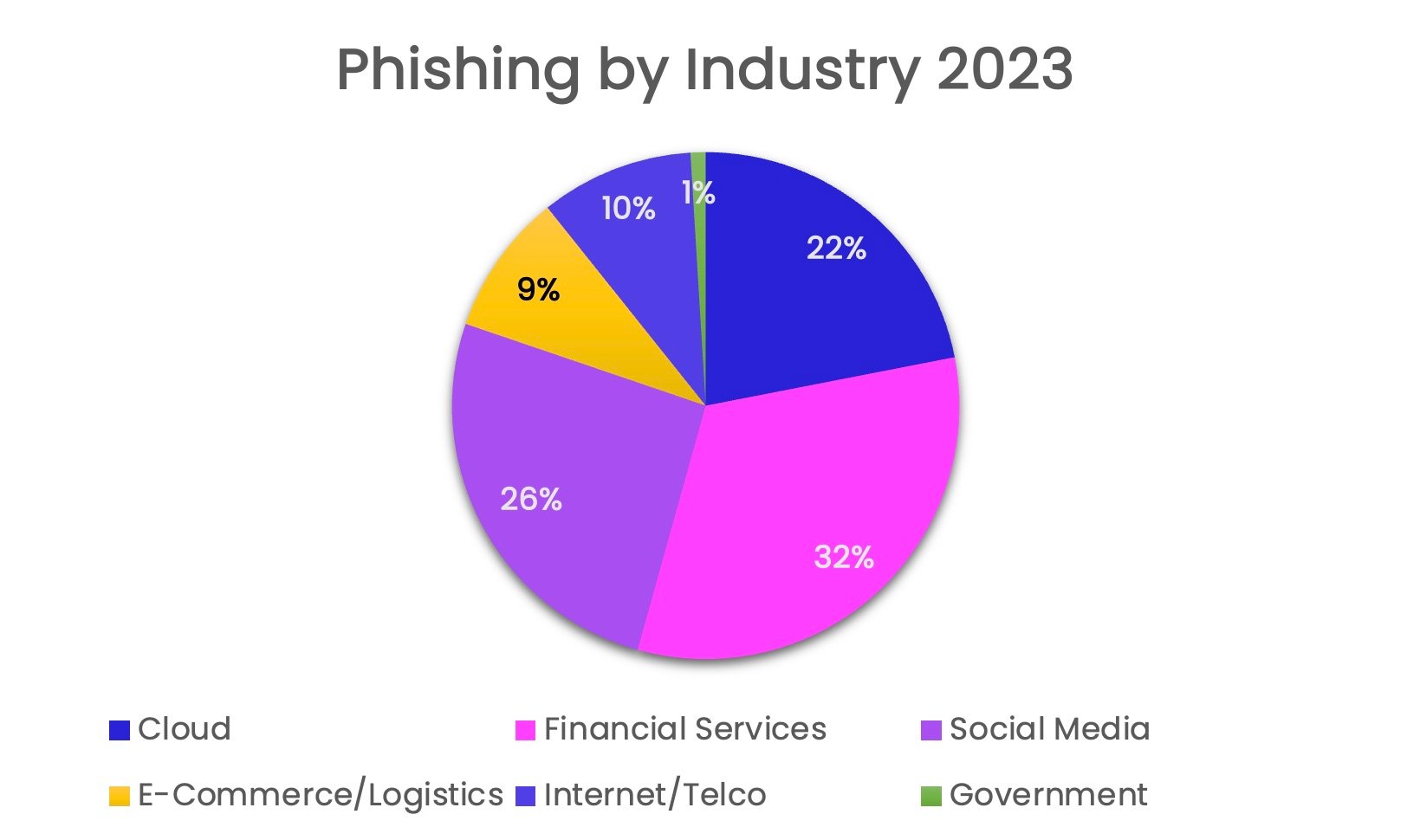
Phishing by industry: 2023
In terms of the top 20 most impersonated brands, financial services also led all industries. It featured the highest number (7), followed by Internet/telco (4), social media, cloud, and e-commerce/logistics (3), and government (0).
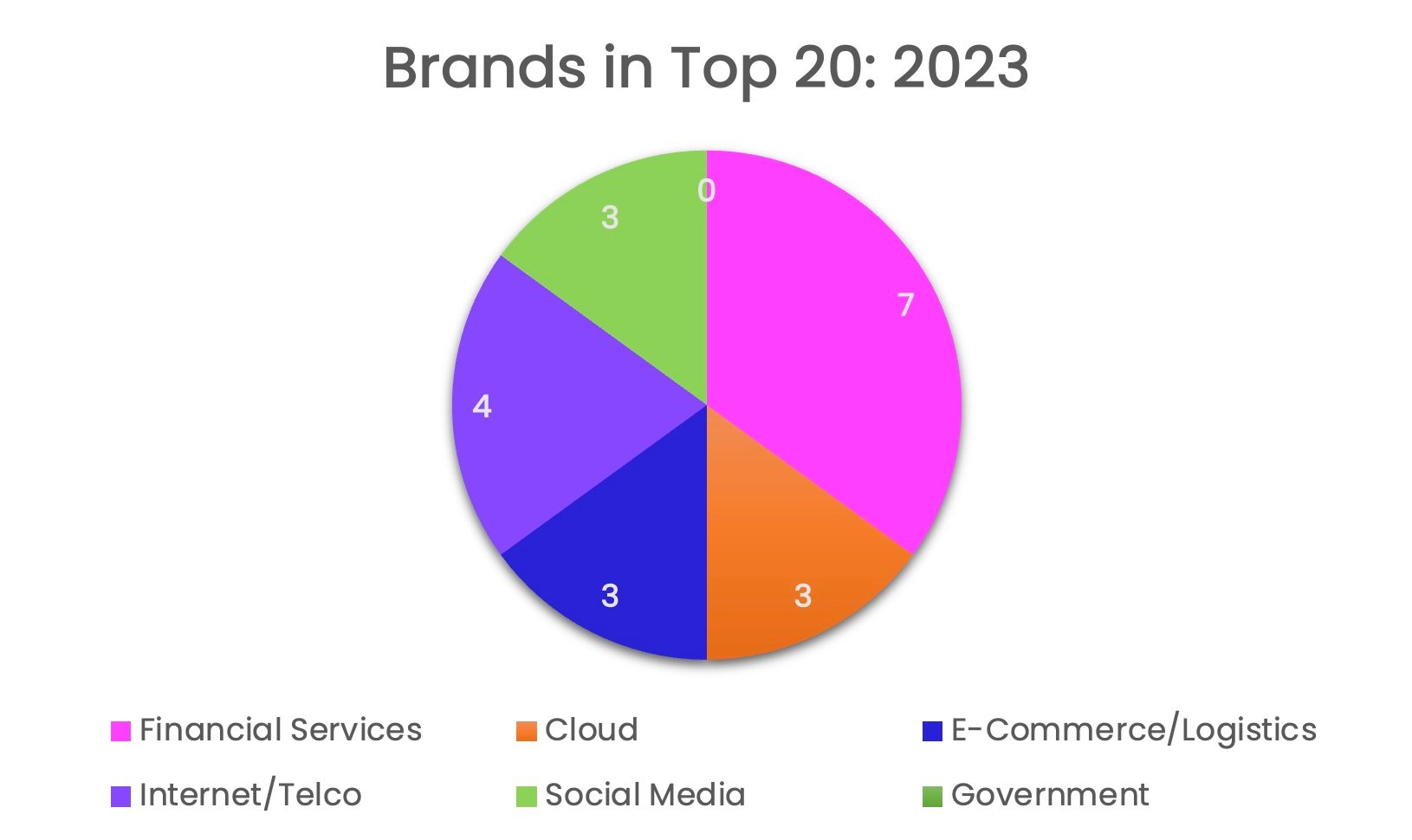
Brands in top 20
These findings illustrate that impersonation attempts in financial services remain relatively distributed among a collection of brands. Meanwhile, spoofing in social media and cloud continues to be concentrated on a handful of companies. Cloud's popularity among phishers, for example, is concentrated on Microsoft, Google, and Netflix.
Financial services’ dominance as the top spoofed sector comes as no surprise. Phishing attacks often aim to accomplish the short-term objective of gaining unauthorized access to a victim’s account. The industry deals with the types of accounts that offer hackers the most lucrative payout, and this makes it very attractive to hackers.
The popularity of social media and cloud are also easy to understand. Social media was covered earlier; it’s an easy avenue to harvest credentials or execute other schemes. But for cloud, we can look to the continued growth of collaboration suites like Microsoft 365 and Google Workspace for answers—not to mention their respective producers, Microsoft and Google.
Microsoft 365, the most popular collaboration suite in the world, announced that it reached more than 382 million paid seats in Q3 2023. That was a marked increase from the 258 million it reached during the same period in 2020. Meanwhile, Google announced this year that more than 9 million organizations pay for Google Workspace. Those executing phishing schemes go where there are users to exploit—and both Microsoft and Google have massive amounts of users.
Businesses rely on these platforms for every aspect of their operations. Users depend on them to communicate, collaborate, and produce—all in a fully and seamlessly integrated environment. That makes these digital suites top targets for hackers. A single compromise can open the door to a seemingly endless list of opportunities to exploit an organization, its customers, suppliers, and users.
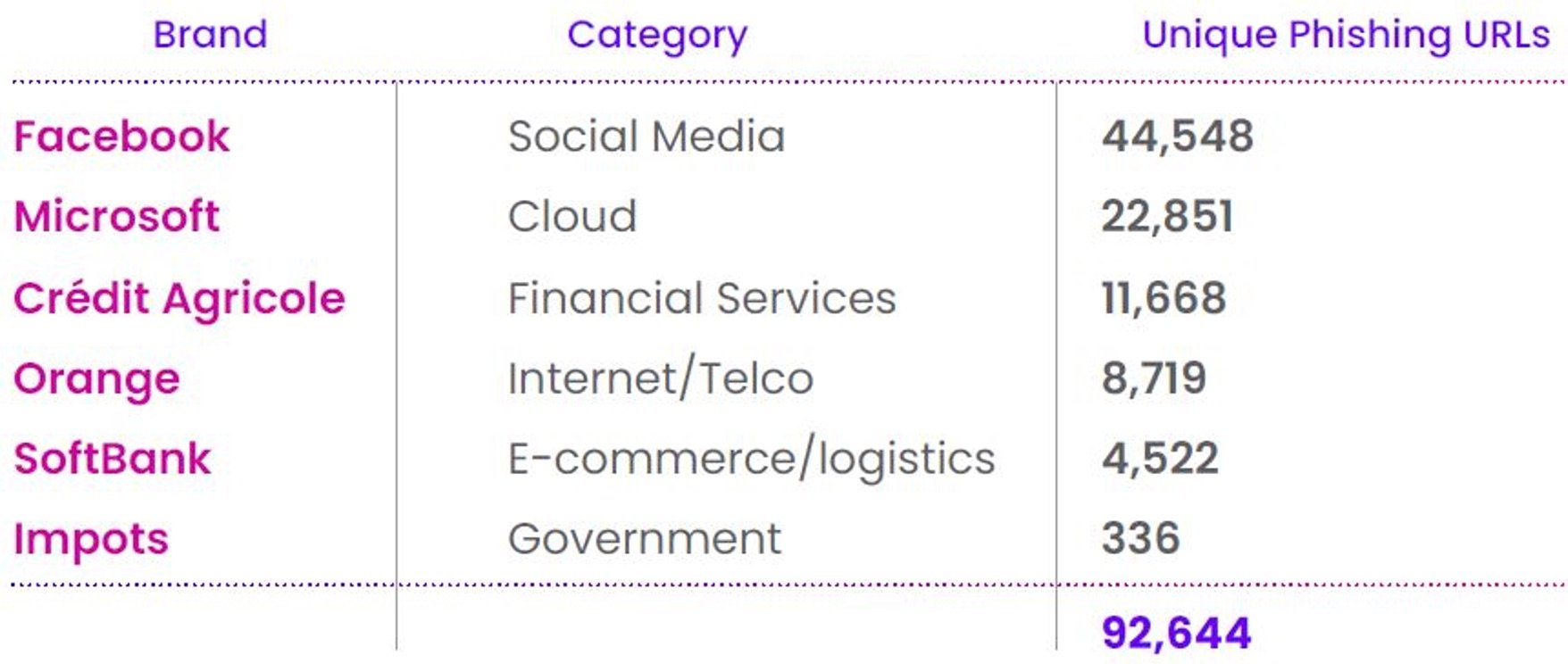 Most Impersonated Brand by Industry
Most Impersonated Brand by Industry
Hackers abuse legitimate services
For hackers, 2023 continued the tried-and-true tactic of abusing legitimate services. We saw hackers exploit multiple popular brands—such as YouTube, Google, Baidu, and Cloudflare, to name a few. And the reasons are clear. Each platform provides significant value to consumers and businesses. Google, Baidu, and YouTube enable consumers and employees to find the information and services they need, and businesses to market and sell their products and services. Meanwhile, Cloudflare enables organizations to provide an optimal and secure online experience, and users to benefit from it. One reality hasn’t changed. The more valuable the service, the more incentive hackers find in exploiting it.
Quishing makes a comeback—and with a vengeance
Quishing, or QR code phishing, isn't a new threat, but it has captured headlines as of late. In quishing attacks, hackers embed a phishing URL in the QR code to make it harder for email filters to detect. While Vade first detected the threat as early as 2017, we observed an alarming increase in quishing attacks in Q2, which continued for the remainder of the year.
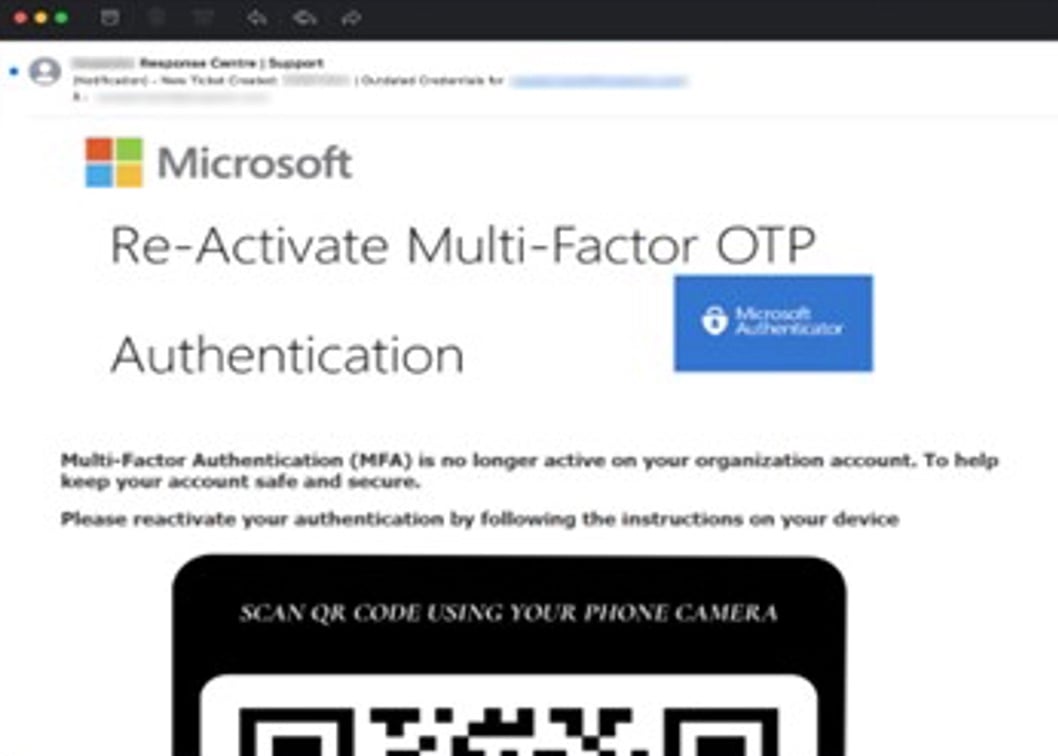
Quishing email impersonating Microsoft
And the reasons are clear. Despite being a well-established threat, some email security filters still lack QR code reading capabilities, preventing them from seeing and analyzing a malicious URL. At the same time, quishing can present challenges for more advanced email security solutions that use Computer Vision. Computer Vision is a type of AI algorithm that can extract malicious links embedded in QR codes.
This could help explain why hackers are sending more phishing emails than ever before. Looking at the past few years, we see a marked trend upward, with volumes reaching their highest level in 2023 since Vade started keeping track in 2015.
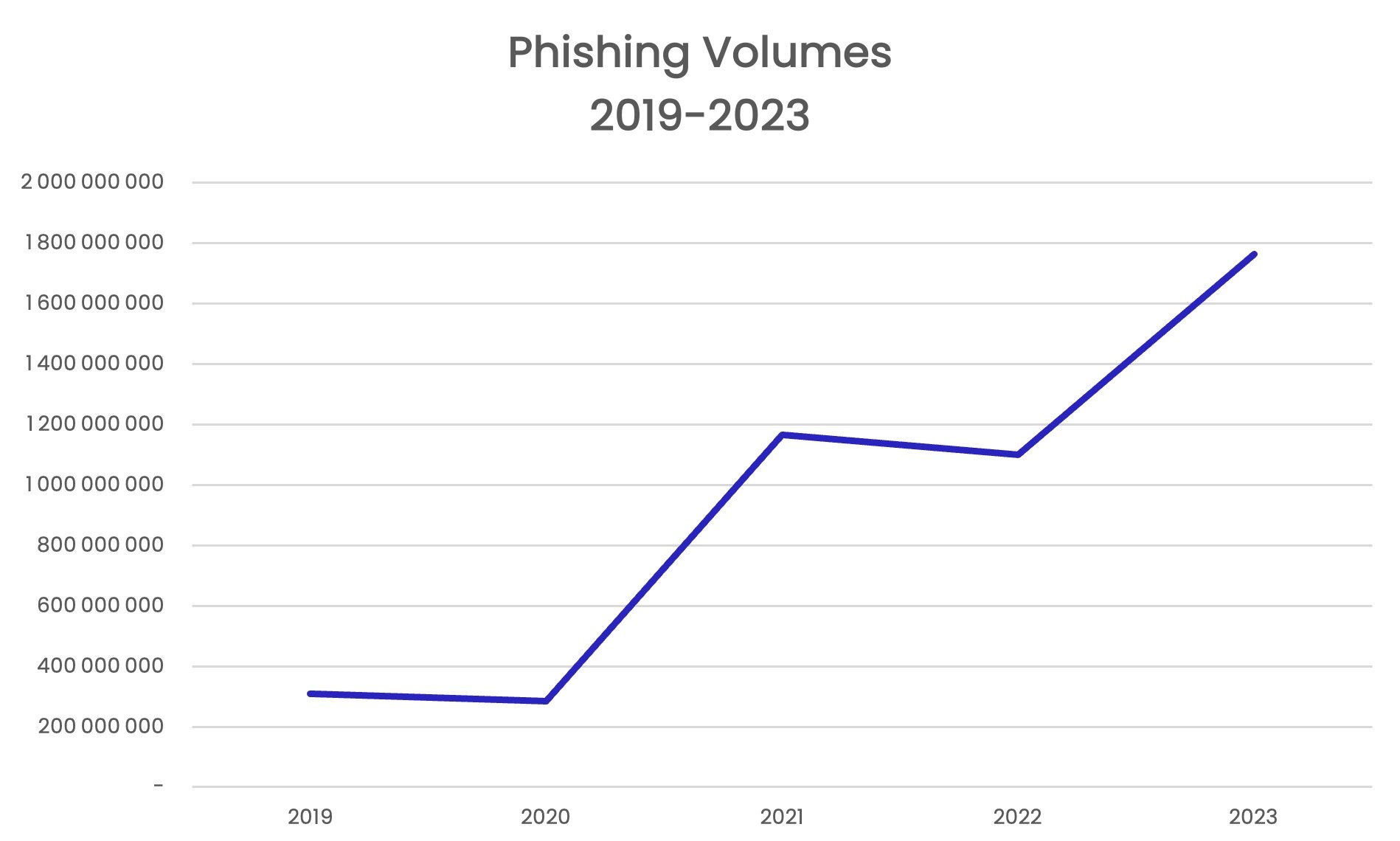
Phishing emails detected by Vade since 2019
“Scama”: unearthing the dark marketplace
Speaking of productivity, phishing kits are a key reason for the increased volume of phishing attacks. Not only do they eliminate most of the legwork of designing, developing, and deploying an attack, but they also lower the barriers to entry for anyone with aspirations of becoming a cybercriminal.
In 2023, Vade analysts revealed an in-depth analysis of scama—another term for phishing kits and a reference to the dark, nefarious marketplace for buying and selling them. The malicious industry exists on platforms like Telegram, where cybercriminals exchange everything needed to launch an advanced phishing campaign. This includes email templates and webpages spoofing legitimate brands and services.
Phishing attacks: dynamic threats call for multi-layered protection
Phishing remains a top cyberthreat for organizations. No other attack method remains as popular or prolific in exploiting victims, as threats continue to become more frequent and sophisticated. For businesses, staying protected calls for a multi-layered approach that fortifies the vulnerabilities in your attack surface.
To protect against today’s most sophisticated phishing threats, look to adopt the following measures:
- Advanced, integrated email security: Since 2020, Gartner has recommended that organizations protect their cloud-based email with an integrated, third-party solution. In 2023, they reiterated this recommendation. Only an integrated, third-party email security solution can defend against emerging phishing threats, including those known as “zero-day.” For this level of protection, look for solutions that leverage machine learning, natural language processing, and computer vision algorithms. Together, they provide predictive defense against all types of phishing threats, including text- and image-based threats. Also, favor solutions that incorporate human insights, utilize real-time global threat intelligence, and offer robust features for threat prevention, detection, and response. The combination better equips you to monitor for and protect against advanced phishing attacks.
- Robust and unified incident response: Security incidents are an inevitable reality in cybersecurity. When they happen, responding with speed and precision matters. Look for technology that automatically remediates email threats across your tenants or users, allows you to triage and remediate user-reported emails, and enables you to manage cybersecurity from a central location.
- Extended protection from mailbox-to-browser: While email is the top attack vector, often the payload is delivered via the web. Protect your mobile and desktop users with a remote browser isolation (RBI) solution. RBI technology safeguards users from browser attacks by launching a remotely hosted session for every browsing session. For optimal email security, look for solutions that extend this protection from email links to the web, while also allowing you to seamlessly control whitelists.
- Phishing awareness training: Human error remains the leading cause of data breaches. Users seem particularly susceptible to interacting with malicious links and attachments. Phishing awareness training attempts to solve this vulnerability, teaching users to identify potential threats and report them to administrators for remediation. While any form of training can help, look for programs that administer electronically, automatically, on-demand, and according to each user’s role and seniority. These features provide the best results and ensure the training reflects the threats each user is likely to encounter.