Spear Phishing Attacks 2024: A Mid-Q1 Review
Todd Stansfield
—February 22, 2024
—4 min read

Vade recently analyzed a wave of spear-phishing attacks targeting organizations across EMEA and the US. The in-depth analysis reveals important findings about the current state of spear phishing, including the most common scams, impersonated employees, targeted roles, and more.
In this post, we examine the results of the analysis and present recommendations for staying protected.
What is a spear-phishing attack?
Spear phishing is the costliest cyberthreat and a highly targeted email attack. Often financially motivated, the attack impersonates someone known by the victim and uses effective social engineering techniques to exploit them. Spear-phishing attacks commonly use text as their only malicious payload, making them easy to create for hackers and hard to detect using human and technological means.
Vade researchers analyzed a recent batch of spear-phishing emails to better understand the nature of current attacks. Below is what we found.
What were the most common spear-phishing attacks?
Our analysis revealed that Initial Contact was the most common classifier, or category, of spear phishing, followed by Payroll Fraud, Banking Fraud, and CEO Fraud. Initial Contact happens when hackers contact victims with a request or question that aims to solicit a response. The attack attempts to establish a history of communication with the victim, which may lower their guard and prevent some email security solutions from flagging subsequent emails as malicious. Often, Initial Contact threats precede other classifiers of spear phishing.
Meanwhile, Payroll Fraud occurs when a hacker impersonates an employee and alerts someone in the HR or finance department about a change to their bank account. The attacker tries to reroute direct deposits from a legitimate account to a fraudulent one.
Banking Fraud is a catch-all category that includes any scam related to a banking operation. This includes fraudulent requests for wire transfers, payments of scam invoices, and more. Hackers impersonating internal employees as well as banking representatives fit into this category.
CEO Fraud occurs when hackers impersonate a senior executive and target employees with requests or demands that most commonly attempt to make them carry out a financial action.
Lawyer Fraud, the least common threat in our sample, is when hackers impersonate an attorney or law firm and demand payment of a scam invoice. Lawyer Fraud can also involve a hacker spoofing a senior executive and acting on a law firm’s behalf.
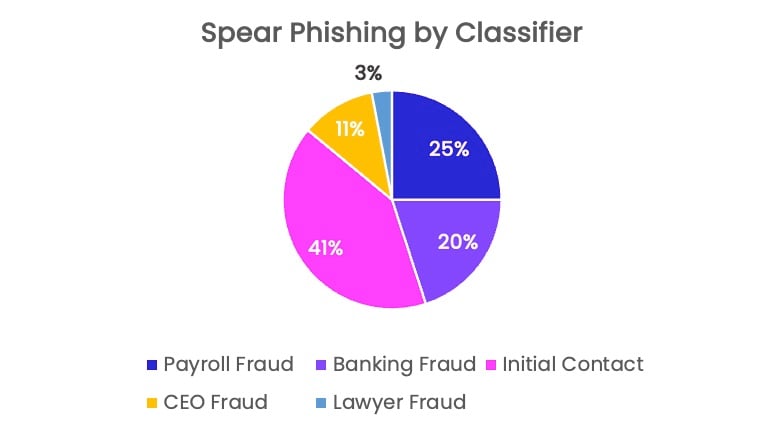
Spear phishing by classifier
What sized companies were most targeted in spear-phishing attacks?
Most spear-phishing attacks targeted small companies, followed by mid-sized and large organizations.
Two factors may help explain why. Globally, small businesses account for 90% of all organizations (99.9% in the US) and represent the vast majority that hackers can target. Additionally, small organizations tend to lack the cybersecurity resources or personnel to defend against cyberthreats, making them more attractive targets to hackers. A recent study in the US found that more than half of small companies (59%) don’t provide security awareness training, while 43% lack even a basic firewall.
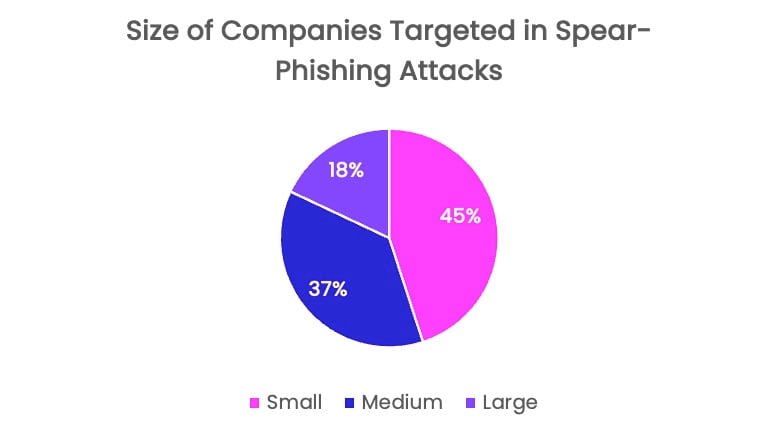
Size of companies targeted in spear-phishing attacks
What industries were most targeted in spear-phishing attacks?
Looking at the industries most targeted by hackers, Professional Services and Local Government surpassed all others. These two industries accounted for more than 3 in every 10 attacks, while organizations in Construction, Retail, and Manufacturing were among the most affected.
For local governments, these figures aren’t surprising as they tend to present low resistance and high reward for hackers. In France, for example, 75% of local governments spend less than €2,000 annually on cybersecurity, more than half admit to needing cybersecurity solutions, and 42% consider themselves at risk of cyberattacks. Local governments tend to rely on outdated systems and technology, and have no recourse but to pay ransom demands if attacked successfully.
Industries classified as “Unknown/Other” represented the highest share of spear-phishing attacks. This category served as a catch-all for niche industries or those that couldn’t be verified.
![]()
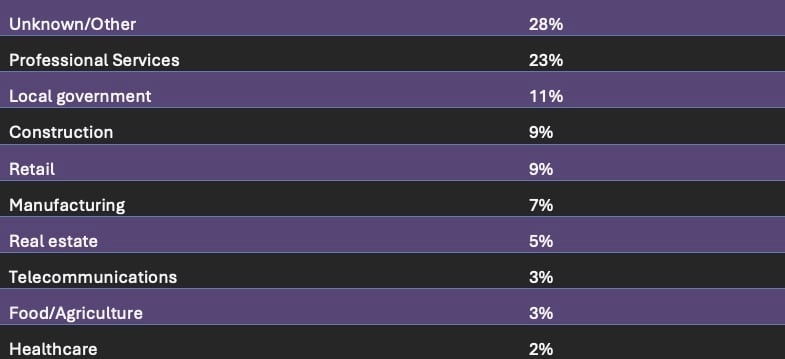
Industries Most Targeted in Spear-Phishing Attacks
Which roles were the most targeted in spear-phishing attacks?
Notably, nearly a quarter of all attacks targeted the Finance Treasurer of the company, the individual responsible for managing the cash flow and financial assets of the organization. The role of Accountant, either internal or external, claimed the second spot, followed by Payroll Officer/Manager, HR Directors/Manager, and the Chief Financial Officer. These figures are not surprising, considering that these roles can directly achieve the typical aim of a spear-phishing attack. That includes making payments, transferring money, or divulging sensitive information, such as employee tax forms.

Top 5 Most Impersonated Roles in Spear-Phishing Attacks
Which roles were the most impersonated in spear-phishing attacks?
When we turn our attention to the roles most impersonated, rather than those targeted, we found that more than 62% of attacks spoofed a member of the C-suite. Spear-phishing attacks often use the authority principle to make victims more likely to comply with demands. The authority principle is a concept in psychology that says individuals are more likely to be persuaded by persons in positions of power.
CEO was the most common role impersonated, followed by President, Mayor, Managing Director, and Lawyer. The role of Mayor figured exclusively in attacks on local governments in EMEA, while Lawyer was the only position among the top five that typically belonged to an external organization.

Top 5 Most Impersonated Roles in Spear-Phishing Attacks
Which departments were the most targeted in spear-phishing attacks?
Of the departments most targeted by hackers, Finance led all others, followed by Accounting, Human Resources, Administration/Operations, Payroll, and C-Suite. This also came as no surprise, as these departments control the financial assets and actions of the organization, as well as sensitive information that hackers can exploit.
Again, Vade classified departments as “Unknown/Other” if they represented niche industries or couldn’t be identified.
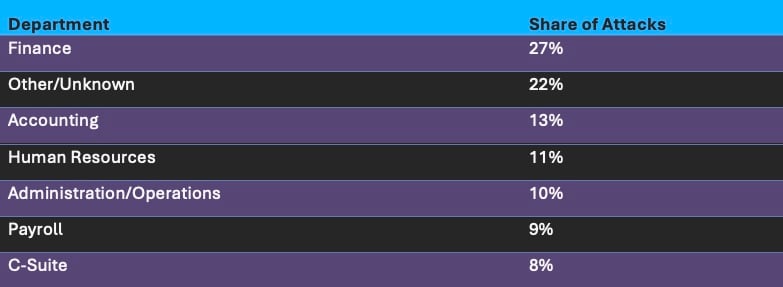
Top Departments Targeted in Spear Phishing Attacks
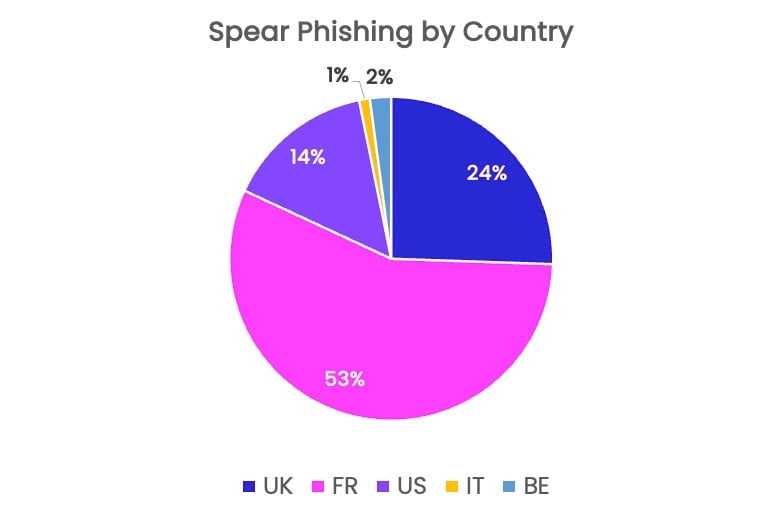
Where did the spear-phishing attacks occur?
Over half of the data set analyzed looked at attacks that occurred in France, followed by the UK, US, Belgium, and Italy.
Top Departments Targeted in Spear Phishing Attacks
Protecting against spear-phishing attacks
Few cyberthreats are more menacing than spear-phishing attacks. Technically simple to produce and difficult to defend against, they present a top threat to organizations of all sizes. To stay protected, your organization needs a combination of advanced email security as well as significant awareness about the latest social engineering techniques and scams.
Vade for M365, a sophisticated email security suite for Microsoft 365, provides advanced protection against spear-phishing attacks. The solution leverages Natural Language Processing (NLP) algorithms, human insights, and email intelligence from more than 1.4 billion protected mailboxes to catch the text-only threats other solutions overlook. Vade for M365 now also utilizes generative AI to enhance protection against threats produced by the technology and skilled hackers.




