What is a phishing attack?
Adrien Gendre
—July 12, 2018
—4 min read

In this article we explain what phishing is, how these attacks are everybody’s business, what the repercussions for businesses are, and how to detect them.
Spotting phishing
It's time to seriously educate users about the dangers and detection of phishing, before they make a new victim – your business. Unless it’s already too late, as it is with 76% of all organizations!
The images shown in this article are real phishing emails.
Nobody is safe from phishing. It’s a real threat that’s continuing to grow and becoming more and more sophisticated. Phishing attacks are corrupted emails that hide under false identities to deceive Internet users and invite them to click on a fraudulent link in order to steal personal or professional information.
In 2017, there was an increase in phishing attacks of +65% compared to the previous year (1). These threats are all the more serious as more than 80% of users fail to detect a malicious email. Worse yet, when it comes to a sophisticated spear phishing attack (a kind of CEO impersonation fraud), which targets people in particular using a social engineering approach, the rate of deceiving individuals reaches 97% (2)!
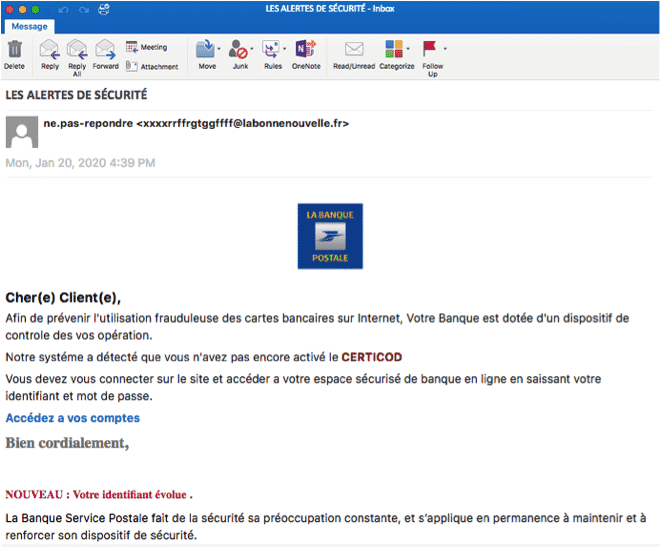
Why should you be afraid of phishing?
Phishing attacks are not direct. They are based on impersonation and the credulity of Internet users who are asked to open the door by clicking on malicious links. What’s more, the threat is posed in an environment where the Internet user is certainly the most vulnerable – "between the chair and the office"; on his mailbox that he believes is defended by his computer, his antivirus and the firewall. This is how hackers will use camouflage techniques, mainly brand spoofing, to appear harmless or serious and trick us into dropping our guard.
As a result, all security is useless if the user is not vigilant and clicks on the link. And don't think that it only happens to others – 76% of all companies were victims of a phishing attack in 2017 (3).
But the worst is yet to come: 30% of all phishing messages would be opened by the recipients, and 12% of them would click on fraudulent links (4). This is how the employee opens a gaping breach in the company's security, by opening a message whose threat he could have spotted, and by giving in to temptation by clicking on a dubious link. This is a very simple scenario, which, in its most sophisticated version (spear phishing), is at the origin of 95% of attacks on corporate networks (5).
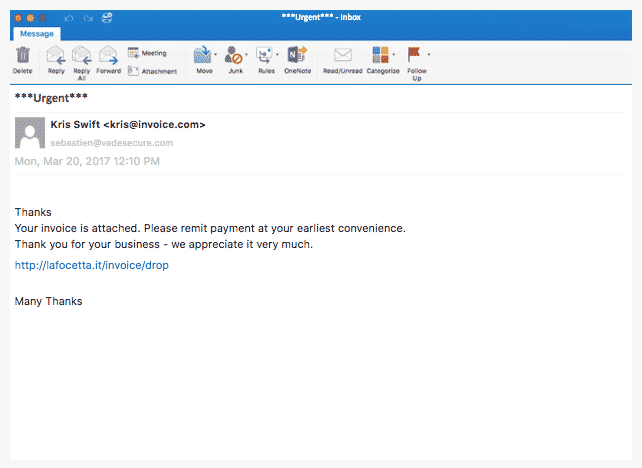
Raising awareness of the company and its employees
Should the company be made aware of the threats phishing poses to it? Its leaders tend to point the finger at their employees, but they are like them: they receive messages and are just as likely to yield to the temptation to open and follow the links. Let’s repeat it: nobody is safe from phishing!
But leaders have to face another fear: that of the impact of hacking. For medium-sized American companies who have not put adequate protection in place, the average cost is estimated at 1.6 million dollars per attack (1). Add to that a disastrous effect for business when data theft is made public, which the European Regulation for the Protection of Personal Data imposes on us today.
Following this disclosure, 60% of all customers think about dropping their supplier, and 30% do so (6)!
Raising user awareness is also critical, but it’s a long-term, even permanent, job. The truth is that our attention struggles to focus on the risks of clicking on a link, especially in a work environment considered secure, and at the same time, the imagination of the hackers is limitless. They use ever more sophisticated techniques to constantly seek to circumvent protections and to trick us.
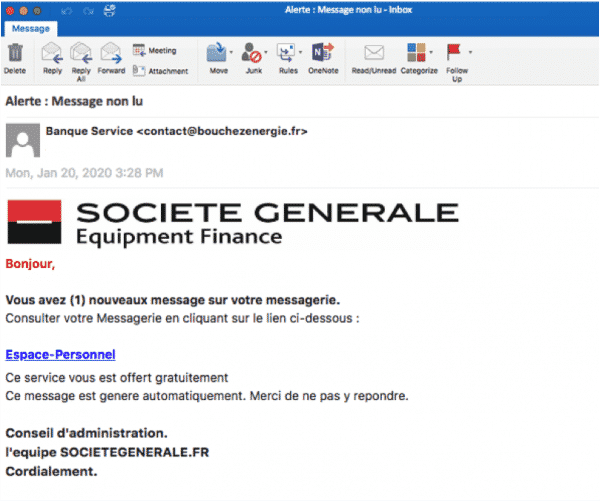
10 tips to detect phishing
The majority of emails with fraudulent content are detected and isolated by your operator and your computer, provided that your company is equipped with the appropriate protection tools. However, we are witnessing a permanent race during which the hackers are trying to get a head start so they can slip past the defense systems with new attacks. For example, pirates constantly change the sender's address and message content so as not to attract attention until they are spotted. Then they move on. Another technique: they send small volumes in order to go unnoticed and not be detected by conventional protection solutions.
The alertness of the email user is therefore needed more than ever. All the more so with social engineering, especially in spear phishing, which is the most sophisticated type, allows message personalization, and thus can more easily deceive the user. Here are 10 expert tips to spot suspicious emails:
1 - Always be vigilant in scrutinizing every email
2 - Look to see who the sender is and if their email address properly matches their name
3 - Beware if you receive an email from someone you don't know
4 - Display the address of the links without clicking on them. Beware addresses starting with “http”; the norm today is “https”.
5 - Isolate emails that are too short from strangers and emails in a foreign language
6 - Beware of emails requesting urgent action under penalty of deleting an account for example: this is often a trick used by pirates
7 - Beware of links in attachments
8 - Never click on a link from a supplier or provider of which you are not a customer
9 - A provider will never ask you to retype your password
10 - If there’s any doubt, always refer to your system administrator
If you had only one keyword to burn into your brain, let it be this one: vigilance.
1 – “Enterprise Phishing Resiliency and Defense Report - 2017 “ from PhishMe
2 – “Phishing Survey" by Intel Security
http://securityaffairs.co/wordpress/36922/cyber-crime/study-phishing-emails-response.html
3 – “State of Phishing” from Wombat Security
https://www.wombatsecurity.com/state-of-the-phish
4 – “Data Breach Investigations Report” from Verizon
https://www.verizonenterprise.com/verizon-insights-lab/dbir/
5 – SANS Institute
6 – Figures released at the “Cyber Security Awards” by Aviva in London




