Ashley Madison Data Breach: 5 Years Later, New Extortion Scam
Adrien Gendre
—January 31, 2020
—3 min read

In our email security predictions 2020, Vade Tech Evangelist Sebastien Gest posited that data breaches in 2019 would fuel new cyberattacks in 2020. Gest’s prediction is already proving accurate with the exception of one detail: the breached data being used in the latest attack didn’t originate in 2019, but rather way back in 2015.
Vade threat analyst, Damien Alexandre, has uncovered a new extortion scam that leverages user account info from the high-profile Ashley Madison data breach in 2015. Back in August of that year, a 9.7GB file containing details of 32 million Ashley Madison accounts was posted to the dark web. The data dump included names, passwords, addresses and phone numbers; seven years’ worth of credit card and other payment transaction details; and even descriptions of what members were seeking on the affair site. Now, nearly five years after the breach, this data is coming back to haunt users in the form of a highly personalized extortion scam.
Extortion scam personalized with Ashley Madison data breach
The target receives an email threatening to share their Ashley Madison account, along with other embarrassing data, with family and friends on social media and via email. The aim is to pressure the recipient into paying a Bitcoin ransom (in the example below, 0.1188 BTC or about $1,059) to avoid the shame of having this very personal—and potentially damaging—info made publicly available for anyone to see, including spouses.
From top to bottom, the emails are highly personalized with information from the Ashley Madison data breach. The subject includes the target’s name and bank. The body includes everything from the user’s bank account number, telephone number, address, and birthday, to Ashley Madison site info such as their signup date and answer to security questions. The email example below even references past purchases for ‘male assistance products’.
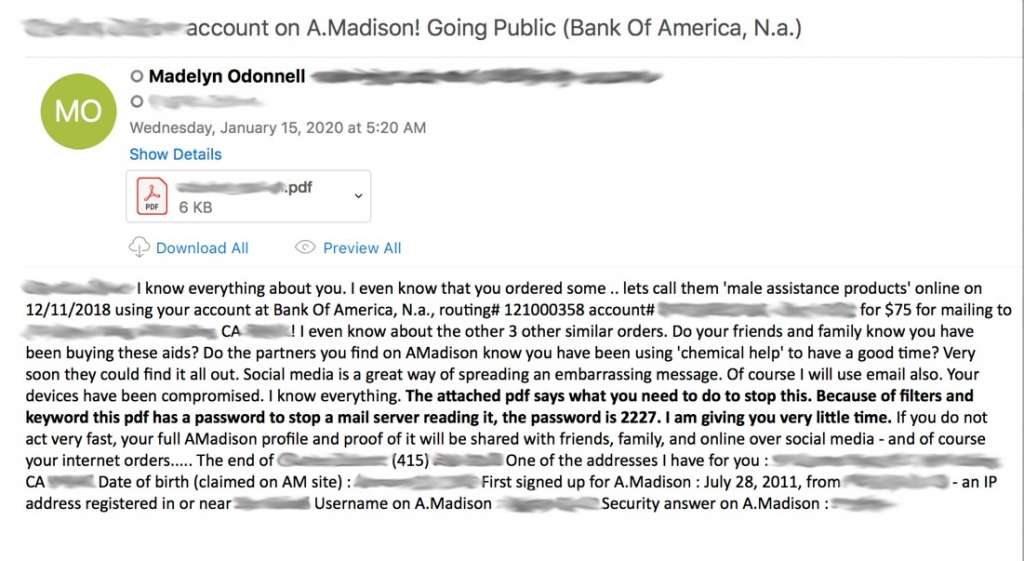
What’s interesting about this extortion scam is that the financial demand isn’t made in the email body itself, but rather a password-protected PDF attachment. As the email itself acknowledges, this is done to avoid detection by email filters, many of which are unable to scan the contents of files and attachments. The PDF includes additional info from the Ashley Madison data breach, including when the recipient signed up for the site, their user name, and even interests they checked on the site when seeking an affair.

Moreover, the PDF file includes a QR code at the top. This phishing technique is increasingly common and used to avoid detection by URL scanning or sandboxing technologies. Computer vision algorithms can be trained to detect QR codes, as well as brand logos and other images used in email attacks, but many email filters do not feature this technology.
Lastly, like other phishing and scam emails, this attack creates a sense of urgency, setting a deadline of six days (after the email was sent) for the Bitcoin payment to be received in order to avoid having the recipient’s Ashley Madison account data shared publicly.
Ashley Madison extortion shares many similarities with ongoing sextortion wave
This Ashley Madison extortion scam shares many similarities with the sextortion scam that has been ongoing since July 2018. Like this attack, sextortion uses breached data (typically an old password) to personalize the messages and convince targets of the legitimacy of the threat. Moreover, while they initially included Bitcoin URLs, sextortion has evolved to include QR codes and even a single image (a screenshot of the plain text email itself) to avoid detection by email filters.
In the last week, Vade has detected several hundred examples of this extortion scam, primarily targeting users in the United States, Australia, and India. Seeing that more than 32 million accounts were made public as a result of the Ashley Madison data breach, we expect to see many more in the coming weeks. Moreover, like sextortion, the threat itself will likely evolve in response to tweaks by email security vendors.
Past breaches will continue to fuel future email-borne attacks
This Ashley Madison extortion scam is a good example that a data breach is never one and done. In addition to being sold on the dark web, leaked data is almost always used to launch additional email-based attacks, including phishing and scams such as this one. Seeing that there were more than 5,183 data breaches reported in the first nine months of 2019, exposing 7.9 billion records, we expect to see a lot more of this technique in 2020.
Stay vigilant and use examples like this to educate your end users about the need for strong passwords, good digital hygiene, and ongoing security awareness training.



