Facebook Phishing: Why Social Media is a Phisher Favorite
Adrien Gendre
—May 28, 2020
—3 min read

For the second straight quarter, Facebook was the second most impersonated brand in phishing attacks in our quarterly Phishers’ Favorites report. Facebook’s 2.6 billion active users makes it a top target for cybercriminals, and since the social media giant has ventured into a seemingly endless string of business ventures, from social app acquisitions to VR, Facebook phishing has surged.
Why Facebook?
There’s no shortage of potential victims in the social media space. Social media platforms host billions of usernames, passwords, personal data, and financial information, all willingly supplied by us, the users. But unlike most other platforms, Facebook is the behemoth—the undisputed, not necessarily loved, social playground nearly everyone has explored at one point or another—whether we want to admit it or not.
Size is only one factor in Facebook phishing. The scale of Facebook is enormous. As of late 2019, Facebook owned the four most downloaded apps in the world, including Facebook, Messenger, WhatsApp, and Instagram. This has earned Facebook the distinction of being called, among other things, a “data monopoly.”
In addition to all that lucrative data, the Facebook Login API connects third-party apps directly to Facebook accounts. While tech-savvy users might keep track of the apps connected to their Facebook accounts and even remove them when they’re no longer useful, the average user likely has no knowledge of how many third-party apps they’re using or the data they’re freely sharing with both Facebook and the third party. When those parties are hacked, Facebook user data is the payday and the weapons that are used to execute Facebook phishing.
Common types of Facebook phishing
The best way to convince a user to click on a phishing link is to scare or entice them. Facebook phishing scams tend to follow these basic tenets. But even more important than a convincing email is a phishing page, and Facebook has those in abundance. In Q1 2020, Vade detected 3,733 unique Facebook phishing URLs, while total phishing emails impersonating Facebook was much higher.
Types of Facebook phishing range from security alerts to password-reset requests, while nearly all are focused on stealing login credentials. Below are just a few common Facebook phishing scams we’ve seen.
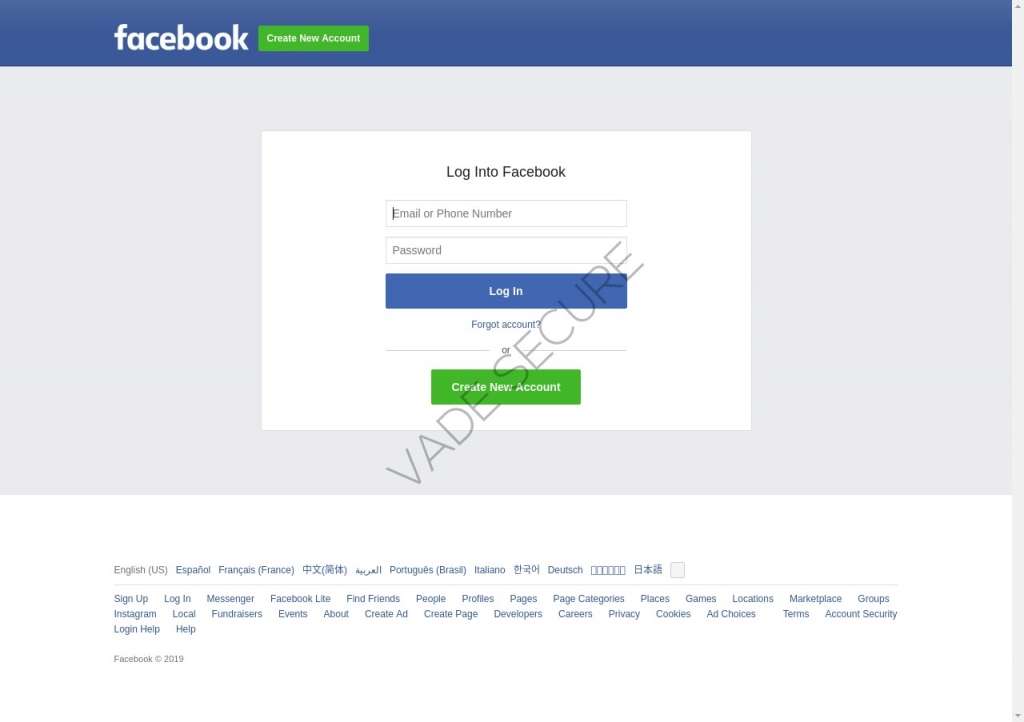
Confirm your account
Getting locked out of a social media account sends chills through power users, especially of the influencer type. So it only makes sense that this is one of the post popular tactics phishers use to harvest data from social media users. In the below example, the phishing page warns the user that their account will be blocked if they don’t update (divulge) their password. Note that the phisher asks a bonus question (birthdate) that they will likely use in the future.
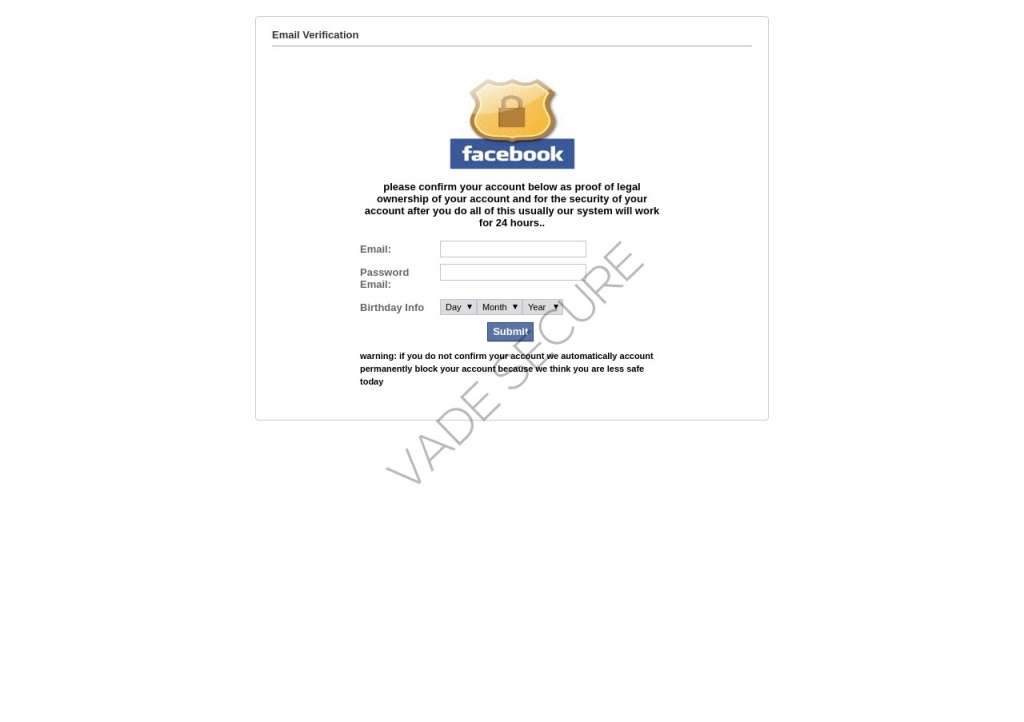
Account abuse warning
In another effort to scare users into believing their accounts will be locked, this scam involves warning users that their account has been reported for abuse and is in violation of Facebook standards. To prove the Facebook page is their own, users are instructed to enter their accounts credentials on this convincing phishing page.
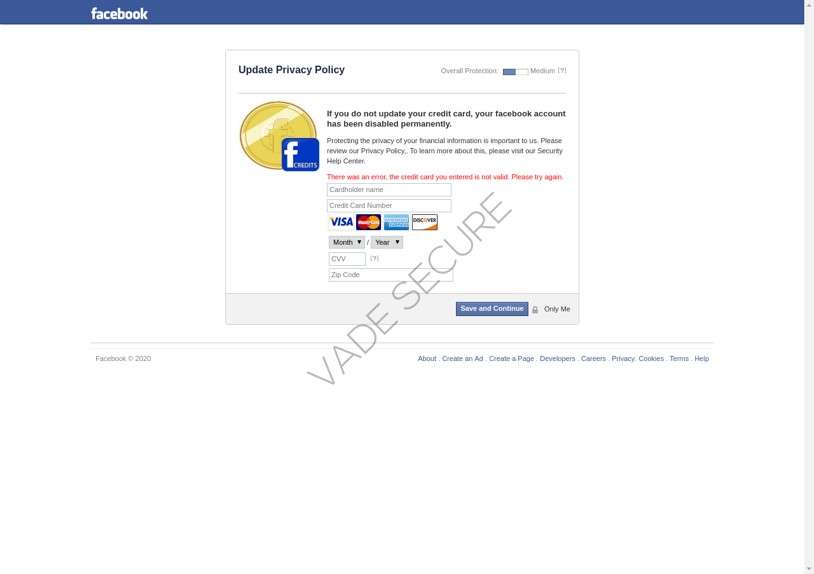
Credit card harvesting
Unlike the above scams that aim to steal account credentials, the purpose of this scam is financial and again uses account closure as a lure. The user is warned in an email that their account will be permanently blocked if they do not update their credit card information. It’s not the most convincing lure, and the page itself features grammar errors. The hacker is counting on the user’s judgment to be clouded by their emotions—the driving factor behind many user errors.
Why Facebook phishing is a threat to SMBs
Unlike phishing scams that impersonate brands like Microsoft and PayPal, Facebook phishing is viewed more as a threat to consumers rather than businesses. A Facebook phishing email, for example, will likely not land in a corporate inbox but will be sent to an employee’s personal email address. But the connected nature of Facebook and other social media platforms means that many hackers are already inside the applications.
With a multiphase attack, a hacker gains access to a user account via a phishing email and proceeds to launch additional attacks, typically phishing and spear phishing emails, from inside a compromised account. Employees who use social media and particularly Facebook on their work computers are at risk of phishing from inside Facebook, both through direct messages sent from hacked accounts or phishing links placed in status updates.
In these types of attacks, phishers impersonate connections and trick users into clicking on phishing links, which could download malware or ransomware onto their work computers. In other cases, they could simply be after credentials. With two out of three people admitting they reuse their passwords, chances are a password an employee divulges via a random Facebook phishing scam could match one they’re using at your business.
Finally, the personal nature of Facebook puts users at risk for highly personalized spear phishing attacks. Facebook users who share personal or professional information reveal everything a hacker needs to know about them to send personalized messages designed to mine for more sensitive data and credentials.
Phishing protection
Protecting your business and your users from phishing requires a combination of cybersecurity vigilance and anti-phishing technology. Today’s attacks are highly sophisticated and the phishing emails we’re seeing today are designed to bypass email filters. Users need to be trained to spot phishing emails and retrained any time they click on phishing links.
Finally, hackers can discover which email filter your using to protect your email via a MX record look-up, and they adapt their emails to bypass those defenses. An anti-phishing solution that doesn’t require an MX record change prevents hackers from identifying your solution. That way, they’re shooting in the dark rather than taking direct aim.
Phishing Attacks: Advanced Techniques That Evade Detection
Discover the methods hackers are using to infiltrate your business—and how to protect yourself.




