How to Spot a Phishing Email
Adrien Gendre
—October 05, 2023
—4 min read
It’s Cybersecurity Awareness Month, and that means it’s an important time to acquire the knowledge that can help protect you, your organization, and your clients from cyberthreats. Phishing is the most common cyberthreat and the top cause of initial compromise. In this post, we examine how to spot a phishing email, and what should happen when you do.
What is phishing?
Phishing is a cyberthreat that impersonates a well-known brand to trick recipients into divulging account credentials or downloading malware onto their local endpoint. Phishing lures users into clicking a malicious link or downloading a harmful attachment. Historically, phishing has targeted victims indiscriminately. In recent years, however, phishing campaigns have grown more targeted, personalized, and limited in scope.

Phishing email detected by Vade
Why is phishing so menacing?
From the perspective of hackers, phishing offers the benefits of convenience, efficiency, and scale. By impersonating a brand rather than an individual known to the victim, hackers can deploy campaigns that target a mass audience.
Successful phishing attacks can result in credential harvesting, account takeovers, malware or ransomware infection, spear phishing, and more. They can also lead to data breaches, supply chain attacks, and other costly consequences.
Advancements in technology have also made it possible to automate the personalization of the attacks—and at scale. Phishing kits can customize phishing emails and webpages to display victims’ names, email addresses, breached password credentials, and more. This helps create the appearance of legitimacy without requiring additional effort from hackers, making attacks more convincing and harder to diagnose.
Phishing is also commonly used in multi-phased campaigns either to facilitate an initial compromise or subsequently inflict more damage.
How to spot a phishing email
Phishing is a menacing threat, but that doesn’t mean you can’t take measures to protect against it. You can—starting with learning how to spot a phishing email. Here are seven features to look for and avoid becoming a victim.
1. Look for spoofing
Attackers use spoofing to hide their true identities. Three types of spoofing exist: domain, display, and close cousin spoofing. Domain spoofing replicates the exact domain name of a legitimate sender. Thanks to authentication protocols like domain-based message authentication, reporting, and conformance (DMARC), Sender Policy Framework (SPF), and DomainKeys Identified Mail (DKIM), domain spoofing is less common. These authentication protocols are effective at catching domain spoofing and preventing the email from ever reaching you.
Close cousin spoofing is like domain spoofing, except it doesn’t replicate the exact address. Instead, it reproduces it with a slight deviation; for example, example@arnazon.com or example@app1e.com. In most cases, the human eye can detect cousin name spoofing.
Display name spoofing is a common technique used by hackers and spoofs the display name of the email. Because it doesn’t impersonate the domain name, display name spoofing can bypass detection by authentication protocols and prey on victims that don’t take the time to verify the domain address. Mobile devices make this process of verification more difficult by automatically hiding the domain.
When opening an email, always be sure to double check the domain and display names. If you’re using a mobile device, this requires you to expand the hidden domain so it displays. It costs you extra effort, but it could save you significant time, headache, and money in the end.
2. Analyze the subject line and tone
Hackers want you to make a mistake—whether clicking a malicious link or downloading an infected attachment. What better way to coerce a response than use enticing, urgent, or threatening language? Phishing emails often stoke a sense of curiosity, fear, or greed in their intended victims, and they do this via a catchy subject line and emotionally charged language.
So, pay attention to the subject line and tone of the email. What is it trying to convey? Is it describing a deal too good to be true? Is it informing you that you only must act now to avoid a penalty or consequence?
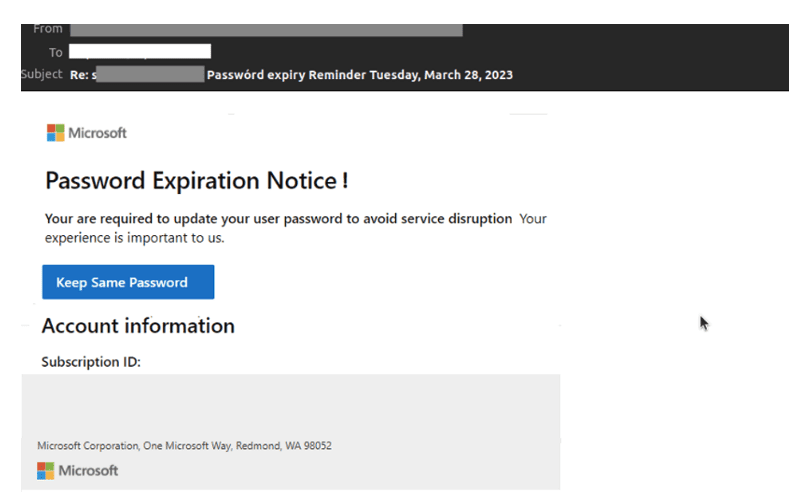
M365 phishing email detected by Vade
-
3. Read the greeting
Phishing emails target a wide swath of intended victims. As a result, they often use generic greetings. Emails that begin with “Dear customer” or “Hello” warrant greater scrutiny.
In recent years, generic greetings have become less common in phishing emails. As referenced earlier, phishing kits now automate the personalization of phishing emails and webpages.
Still, you’ll encounter phishing emails that address you as they would anyone else. That’s why you should analyze the greeting and use it as another data point in your overall analysis.
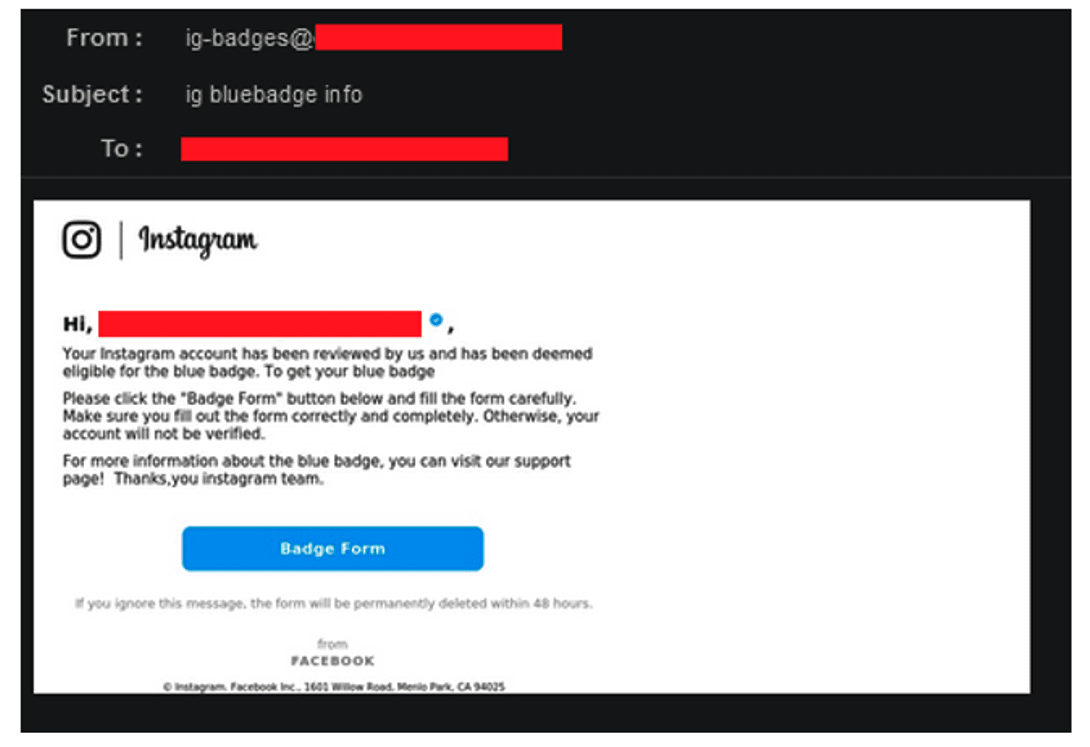
Instagram phishing email detected by Vade
4. Scrutinize egregious errors
Phishing emails often come from attackers who don’t speak your language natively. As a result, their emails may contain a litany of spelling and grammatical errors. If you spot a series of errors in the email, or the non-standard use of language, then be cautious of the message.
While these errors have long served as a glaring indication of a phishing email, they’re becoming less common. Generative AI now enables hackers to instantly create phishing templates in a variety of languages—and do so error-free.
Still, errors in phishing are still commonplace. So, read every email carefully and pay attention to noticeable mistakes.
5. Look for links
Phishing emails try to lure you into clicking one or more malicious links. By hyperlinking text, hackers can hide the true destination of a URL and redirect you to a phishing webpage. They can do the same by using link shorteners such as Bitly or TinyURL.
To inspect links safely, simply hover over them. You’ll see a tool tip appear below each link that reveals its actual destination. If you can’t verify the destination as legitimate, avoid clicking the link.
6. Check for an attachment
Phishing emails may contain one or more attachments to compromise you. Hackers commonly infect attachments with malware to spread the virus on your local computer. They also use attachments to hide or disseminate phishing links. Links inserted into an attachment, rather than the body of the email, can bypass detection by traditional email security tools.
Always check to see if the email contains an attachment. While a common feature of legitimate emails, the presence of an attachment can help you determine whether an email is safe.
7. Pay attention to images
Phishing attacks impersonate well-known organizations, a reason they often feature brand logos, images, and other graphics. These are often indistinguishable from the legitimate versions and create the perception of credibility.
If the email contains one or more images, pay attention to it, and don’t automatically trust the email because of it. Instead, keep this in mind when determining the legitimacy of the message.
Now what? Report it
Let’s say you’ve spotted a phishing email. What do you do now? The answer is to report it to your administrator for remediation. Email clients like Microsoft Outlook and Gmail include a reporting feature that enables you to flag a suspicious email for review.
Reporting is important. Chances are you’re not the only person to receive the email. By flagging it, admins can remediate it across all users in your organization, or across multiple organizations if your company uses a managed service provider (MSP) for IT.
Protect yourself from phishing
You’ve learned how to spot a phishing email. But you can learn more about protecting against phishing and other cyberthreats at vadesecure.com. Here, you’ll find a variety of resources, including eBooks, white papers, webinars, and interactive demos.
You can also download the below infographic as a checklist to use for you or your teams.