Phishers’ Favorites Top 25 H1 2021, Worldwide Edition
Natalie Petitto
—July 22, 2021
—6 min read

Phishers’ Favorites highlights the 25 most impersonated brands in phishing attacks. The list is compiled by analyzing the phishing URLs detected by Vade’s technology. Examples of these URLs and their corresponding pages are available at www.IsItPhishing.AI.
Phishers’ Favorites H1 2021: A Big (Bad) First Half for Banks, a Growing Problem for Social Media Brands
Phishers’ Favorites is Vade’s quarterly analysis of the 25 most impersonated brands in phishing attacks. The ranking is based on the number of unique URLs detected per quarter. A unique phishing URL is a single phishing URL and not the number of phishing emails or times Vade detected the URL in subsequent emails. Our H1 report covers the period from January 1, 2021 to June 30, 2021.
.png?width=478&name=MicrosoftTeams-image%20(77).png)
Three brands dominated the top 25 list, based solely on the number of unique URLs, with two financial services brands and two social media brands in the top five. Microsoft, which consistently ranks at the top of the list, was the sole cloud brand in the top 10.
H1 saw a surge of advanced phishing attacks featuring sophisticated automation techniques and abuse of high-reputation domains. Due to the high level of targeting and automation we have seen in the first half of 2021, we should place less emphasis on the total number of unique URLs detected and more on the nature and quality of the threats received.
Crédit Agricole edges out Facebook for the top spot
Crédit Agricole was the most impersonated brand in H1 2021, moving up 10 spots on the Phishers’ Favorites list with 17,755 unique phishing URLs. Crédit Agricole edged out Facebook for the top spot, with just 2.4 percent more unique phishing URLs than the social media giant.
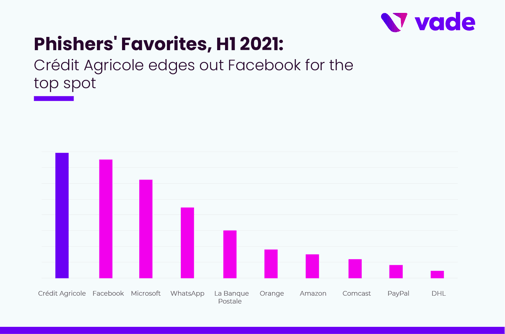
Crédit Agricole’s spot at the top is a first for Crédit Agricole. The spike came in Q2 when Crédit Agricole phishing URLs increased 296 percent over Q1. The single-day high for Crédit Agricole phishing came on May 6, when Vade detected 1,004 unique phishing URLs.
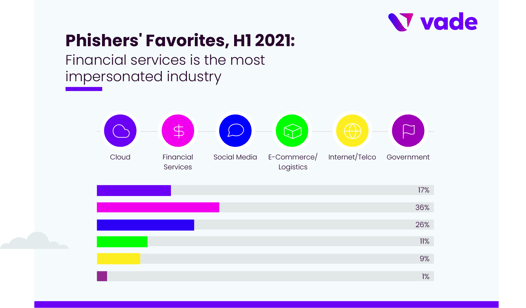
Crédit Agricole’s meteoric rise on the Phishers’ Favorites list from Q1 to Q2 list tracks with the overall trend of financial industry phishing for H1. Financial services represented eight brands in the top 25 and accounted for 36 percent of all unique phishing URLs detected. La Banque Postale was the second most impersonated financial services brand in the top 25, followed by PayPal, Chase, Wells Fargo, Square, HSBC, and Banque Populaire.
Like Crédit Agricole, La Banque Postale saw a dramatic increase in unique phishing URLs, with a total of 7,180 URLs for the first half of 2021 and a 831 percent increase in URLs from Q1 to Q2. The spike caused La Banque Postale to jump 18 spots to #5 on the list.
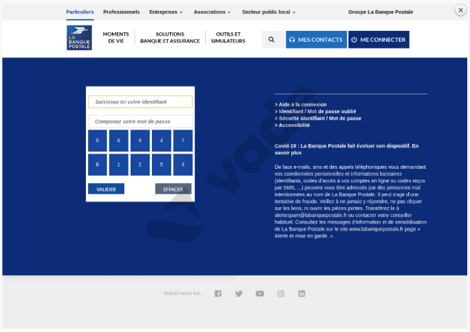
La Banque Postale phishing page
The growth in financial services phishing could be attributed to the impact of COVID-19 on the global economy. At the beginning of the crisis, businesses and citizens around the world took advantage of government-backed business loans and payment deferrals or “holidays” from consumer banks and credit unions.
Since the beginning of the COVID-19 pandemic, Crédit Agricole processed 211,000 applications for small to midsized business and small business and corporate loans, totaling €315 billion. In February 2021, the bank announced a “return to normal,” with only 93,000 “payment holidays” out of 552,000 still active.
As the world’s largest economies return to normal, the bill is coming due. This is a significant weapon for phishers to wield against businesses and individual citizens who borrowed or deferred and could signal a continuance of the trend toward financial services phishing as payment moratoriums expire around the world.
The second most impersonated industry in H1 is social media, which has four brands in the top 25 and represents 26 percent of all unique phishing URLs. Coming in third is cloud, followed by e-commerce/logistics, which has five brands in the top 25, internet/telco, and government.
Related Content: [eBook] Phishers’ Favorites 2020 Year in Review
Microsoft is the #1 impersonated cloud brand
Dropping two spots from H2 2020, Microsoft landed at no. 3 on the list with 12,777 phishing URLs for H1. Microsoft continues to dominate all others in the cloud category, with 556 percent more phishing URLs than Netflix, which came in at #17, despite being the second most impersonated cloud company on the list.
Microsoft’s strong showing in Q1 and Q2 is a continuation of its longstanding position as a phishers’ favorite. Microsoft has been the most impersonated brand on the Phishers’ Favorites list in four of the last six quarters and the most impersonated brand overall since 2018.
With its Microsoft 365 suite leading the competition in corporate email and productivity software, Microsoft is an alluring target for phishers who want access to the corporate data spoils hosted in Microsoft 365.
In late June, Vade detected a sophisticated Microsoft phishing attack featuring automated rendering of public logo and background images on Microsoft 365 login pages. When a victim clicks on an email phishing link, they are taken to a waiting page, the purpose of which is to determine if the user is the intended target.
If the user is not the intended target, the phishing page is not shown. If the victim is the intended target, the hacker then makes an HTTP post request for the logo and background image of the victim’s corporate entity.
The victim is then redirected to a custom Microsoft 365 login page with their company’s corporate logo and background image. Below is an example of the dynamic webpage, with Vade’s branding on the Microsoft phishing page. If the victim doesn’t notice the long and complicated URL, then they would have no reason to suspect that the page is a fraud.
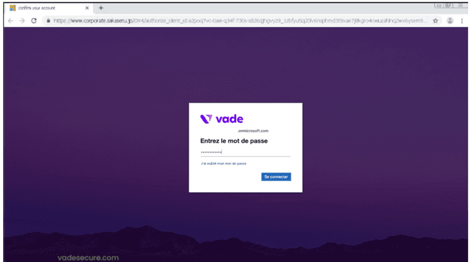
Related Content: [Infographic] Evaluating Microsoft 365 Email Security Solutions
Facebook and WhatsApp dominate social media phishing
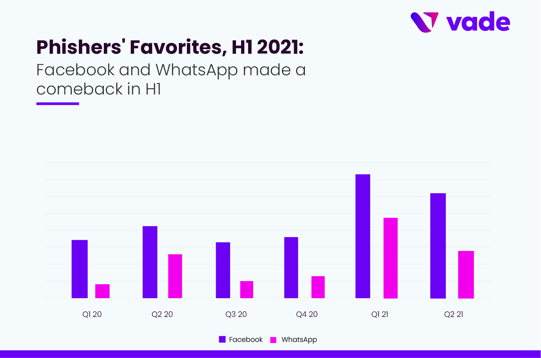
Although social media only accounted for four brands in the top 25, social media represented 25.6 percent of all phishing URLs in H1. Facebook is the most impersonated social media brand on the list and #2 on the Phishers’ Favorites list overall. Vade detected 17,338 unique Facebook phishing URLs, a 146 percent increase from H2 2020. The biggest increase came in Q1, when Facebook phishing URLs increased 137 percent from Q4 2020 to Q1 2021.
After several quiet quarters in 2020, WhatsApp phishing exploded in Q1 2021, driving WhatsApp up six spots on the list to #4. WhatsApp phishing URLs increased 441 percent from Q4 2020 to Q1 2021, then fell 58 percent in Q2, though it was still well above the trend from H2 2020.
The WhatsApp brand was associated with several high-profile phishing cases in H1 2021. One scam involved senior Australian politicians and diplomats who were duped into clicking on WhatsApp phishing emails that asked them to validate either their WhatsApp or Telegram accounts. Cybercriminals then accessed the victims’ contact books and sent unsolicited emails to the victims’ contacts, including high profile pro-democracy advocates.
In April, a WhatsApp phishing scam leveraging SMS made the rounds. In early June, another WhatsApp phishing scam targeted thousands of victims with the allure of entering a fake sweepstakes that promised a Rolex watch to the contest winner.
H1 2021 phishing trends
Increased phishing and malware activity
Overall phishing increased dramatically in Q2 2021, with a significant spike (281 percent) in May and another 284 percent increase in June, for a total of 4.2 billion phishing emails detected by Vade for the month. The increase in May can be attributed to spambot activity, as well as an increase in Amazon and SMBC phishing.
Malware delivered via email peaked in January of Q1 and then gradually declined for the rest of the quarter. In May of Q2, malware emails increased 95 percent, with nearly 21 million emails detected. Malware emails then tapered off, decreasing slightly (5.3 percent) from May to June.
COVID-19
The coronavirus pandemic continued to inspire cybercriminals around the world. In Q2 alone, Vade detected 6.5 million COVID-themed emails targeting corporate email accounts. Overall, 10 percent of all COVID-themed emails sent in the US and EU in Q2 were malicious. With the global vaccination effort in full force, COVID remains a top lure for victims who are still hungry for information about either getting or avoiding the vaccine.
In March 2021, Vade detected 1 million fraudulent COVID-themed emails over the course of three days, each related to various vaccines, including Pfizer, Moderna, and Johnson & Johnson. Subject lines included in the campaign included “Important Pfizer Vaccine Message for you, “Pfizer Vaccine Survey Response Needed,” and “Pfizer COVID-19 Survey Response Confirmation”.

The campaigns used a series of evasive techniques to bypass detection, including inserting random noise into the text to trick email filters, use of remote images to conceal the text, and use of high-reputation domains to host the images or redirect to the final malicious website, including https://storage.googleapis.com.
Top phishing offenders
Brazil led all other countries in phishing in the last month of Q2. Russia was the second biggest offender, followed by Indonesia and Ukraine, a well-known hotbed of cybercrime activity.

Phishers’ continue to rely on recognizable domains from which to deliver phishing emails. Phishers also favor domains that corporate users are accustomed to receiving important messages from, including SharePoint and Salesforce, two high-reputation domains that are regularly abused by phishers. In an analysis of 780,694 corporate email addresses in Q2 in Europe and the US, gmail.com was the most frequently used popular domain to send phishing emails.
Remote image threats
Remote images are increasingly used by cybercriminals to evade detection. Remote images are displayed when the recipient opens the email but are hosted remotely. From Q1 to Q2 2021, Vade blocked 300 million threats using remote images with RIANA (Remote Image ANAlysis), one of Vade’s Computer Vision-based detection engines.
RIANA fetches remotes images, extracts texts, and then applies Natural Language Processing models to detect suspicious textual content that traditional filter engines cannot see. RIANA currently supports detection of suspicious texts in English, French, Italian, German, Dutch, and Swedish.
Keeping up with the cybercriminals
As cybercriminals continue to hone their techniques and find innovative ways to evade detection, Vade is dedicated to finding new ways to stop them, including significant investments in Computer Vision technology. Like RIANA, our Logo Detection engine is based on Computer Vision and designed to analyze images.
Logo Detection extracts brand logos from images to identify phishing, and more generally threats impersonating well-known brands. As Logo Detection is based on Deep Learning models (VGG16, ResNet), it is resilient to image manipulation techniques that cybercriminals leverage to evade detection.
Finally, as HTML and CSS offer endless possibilities to conceal malicious content, it is ideal to render the email as an email software would do, and then analyze the visual content produced. This is the approach taken by ELSA (Email Screenshot Analysis), the latest Computer Vision technology developed by Vade.
ELSA selects emails with suspicious features, renders them into screenshots, and then compares them with graphical renderings of known malicious emails. ELSA is resilient to small changes as it leverages robust feature detection algorithms like ORB and as such can detect variants of known attacks. ELSA is currently blocking up to 1.5 emails per day.
To learn more about the evasion techniques hackers use to bypass detection and how to defend your business, read our eBook, “Phishing Attacks: Advanced Techniques That Evade Detection.”



