Beware of Spear Phishing Scams Using Fake-Forwarded Emails
Vade Experts
—March 19, 2024
—3 min read

Vade has detected a new type of spear-phishing scam that can bypass email authentication protocols and detection by email filters. The exploit uses fake-forwarded emails to provide victims with basis and reason for complying with hacker’s demands, most often taking a financial action.
In this post, we examine the spear-phishing scam, how the novel technique works, and how you can stay protected.
What is a fake-forward spear phishing scam?
Spear phishing is a targeted threat that impersonates a sender known by the victim, such as a colleague or supervisor. The attack also makes an explicit request to take an action, usually financial in nature.
While less common than phishing attacks, spear-phishing scams represent the costliest cyberthreat for victims, accounting for more than $50 billion (USD) globally between 2013 and 2022, according to the IC3.
Vade first observed a new type of spear-phishing scam in late 2023. The scheme sends victims a spear-phishing email that appears to be a forwarded exchange between a legitimate individual the victim knows and the representative of a third-party, often a non-existent organization.
The scam allows hackers to avoid impersonating anyone as the sender, enabling the threat to evade detection by email authentication protocols (SPF, DKIM, and DMARC). Still, the technique uses social engineering techniques common to most spear-phishing attacks including CEO fraud and banking fraud.
How does the spear-phishing scam work?
In January, Vade detected a spear-phishing scam from a non-profit organization soliciting sponsorships for a gala event. The attack begins with an email from a representative of the non-profit, notifying the recipient of an attached invoice and a request made by the recipient’s CEO. The email appears to forward an email thread between the CEO and the non-profit representative, in which the CEO agrees to sponsor the event for $25,000.
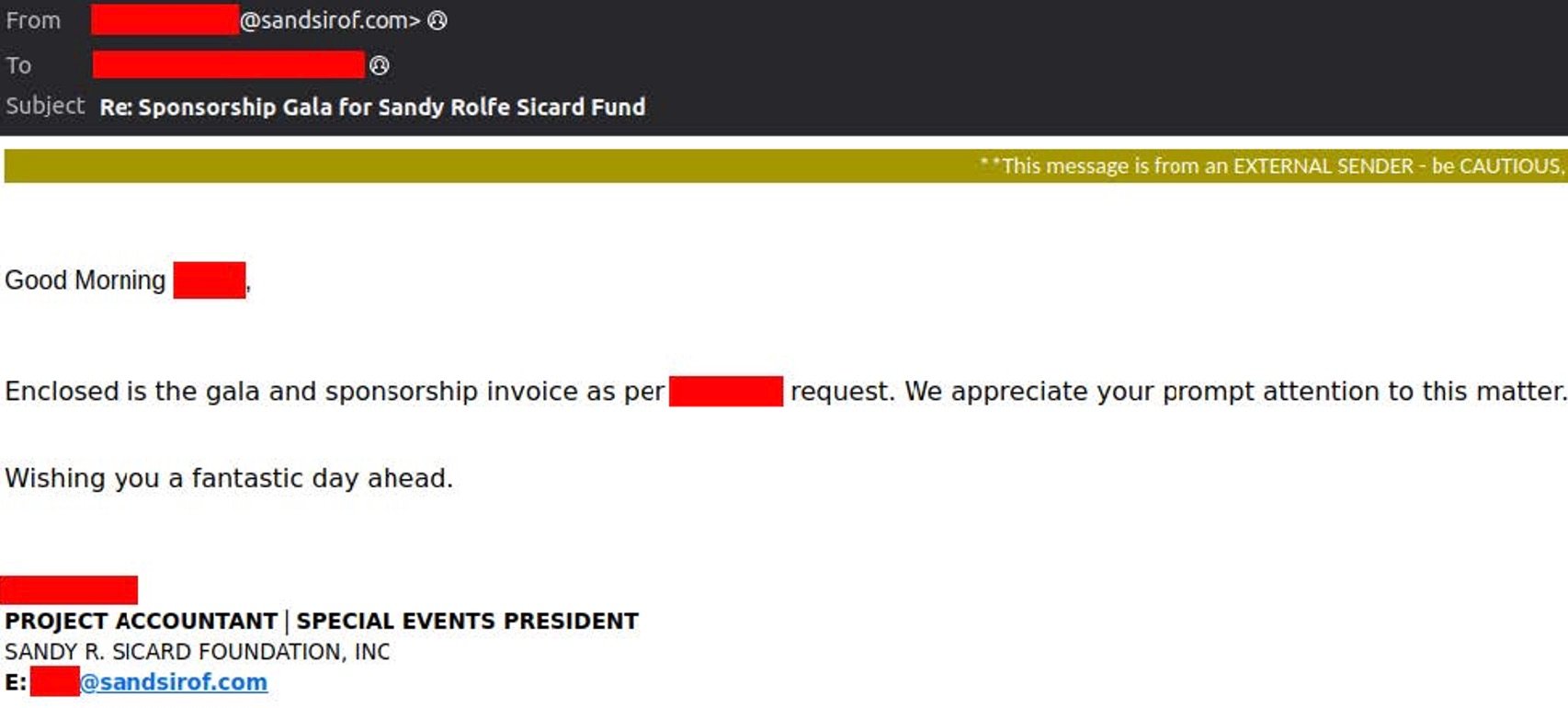
Fake-forward spear-phishing email
Below the email is the email exchange, which consists of three emails that fully contextualize the request and give the recipient motive to comply with it. Despite appearances, the email thread is fake and contained within the body of the message to the recipient.
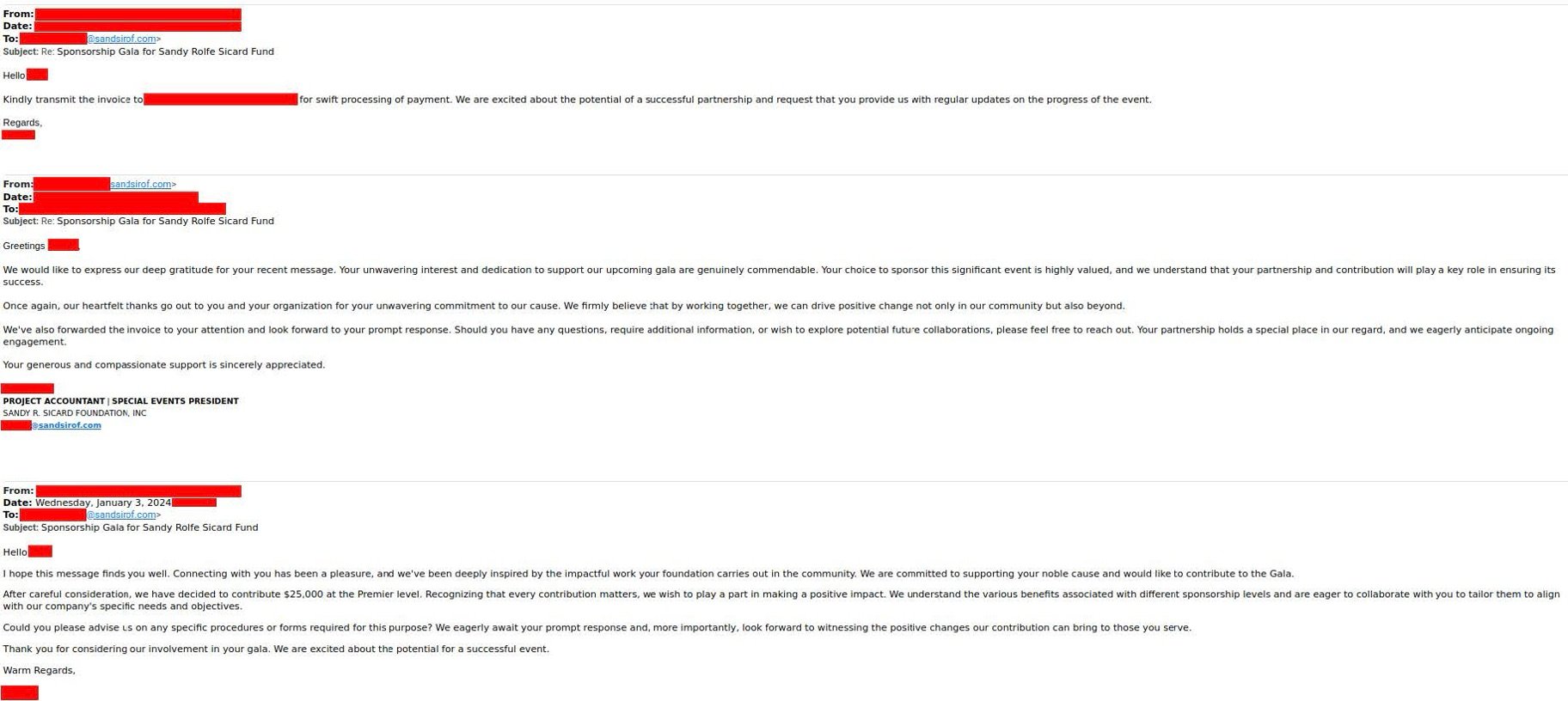
Fake email exchanges
Vade has verified that the recipient had no prior communication with the sender or the sender’s organization. Vade has also verified that hackers fabricated the identities of the sender and non-profit.
Notably, the sender’s email and the fake email exchange appear to be written by native speakers and don’t contain any spelling or grammatical mistakes. This enhances the appearance of legitimacy, making the scam more difficult to spot. According to ZeroGPT, a tool used to detect AI-generated content, the scam was likely produced by a combination of generative AI and human sources. Vade researchers suspect that hackers likely used generative AI to produce a series of email templates before modifying them.
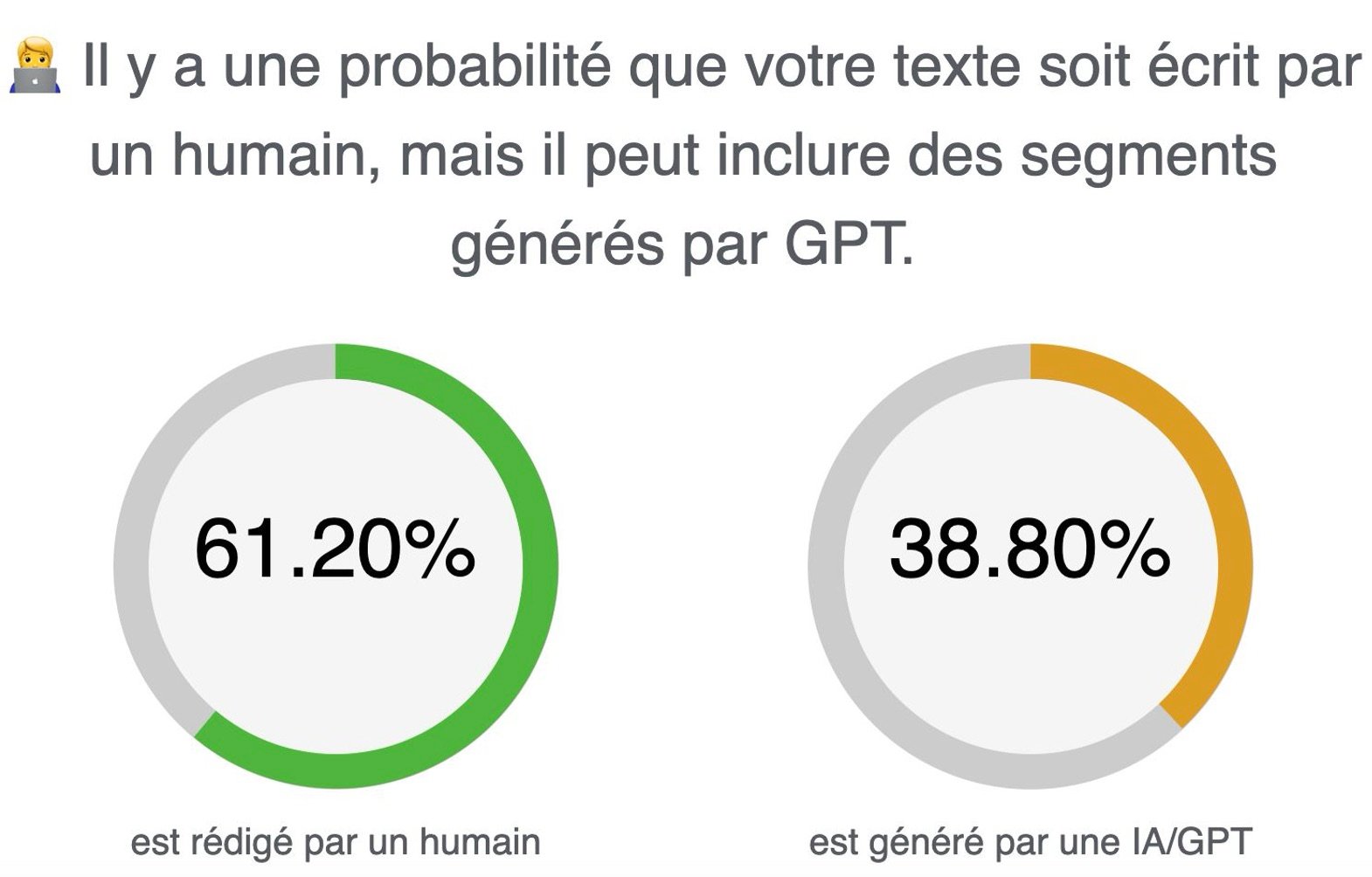
ZeroGPT analysis of email
While sophisticated, the scheme contains several clues that indicate a scam. They remain subtle and illustrate the need for heightened security awareness and attention to detail on the part of users.
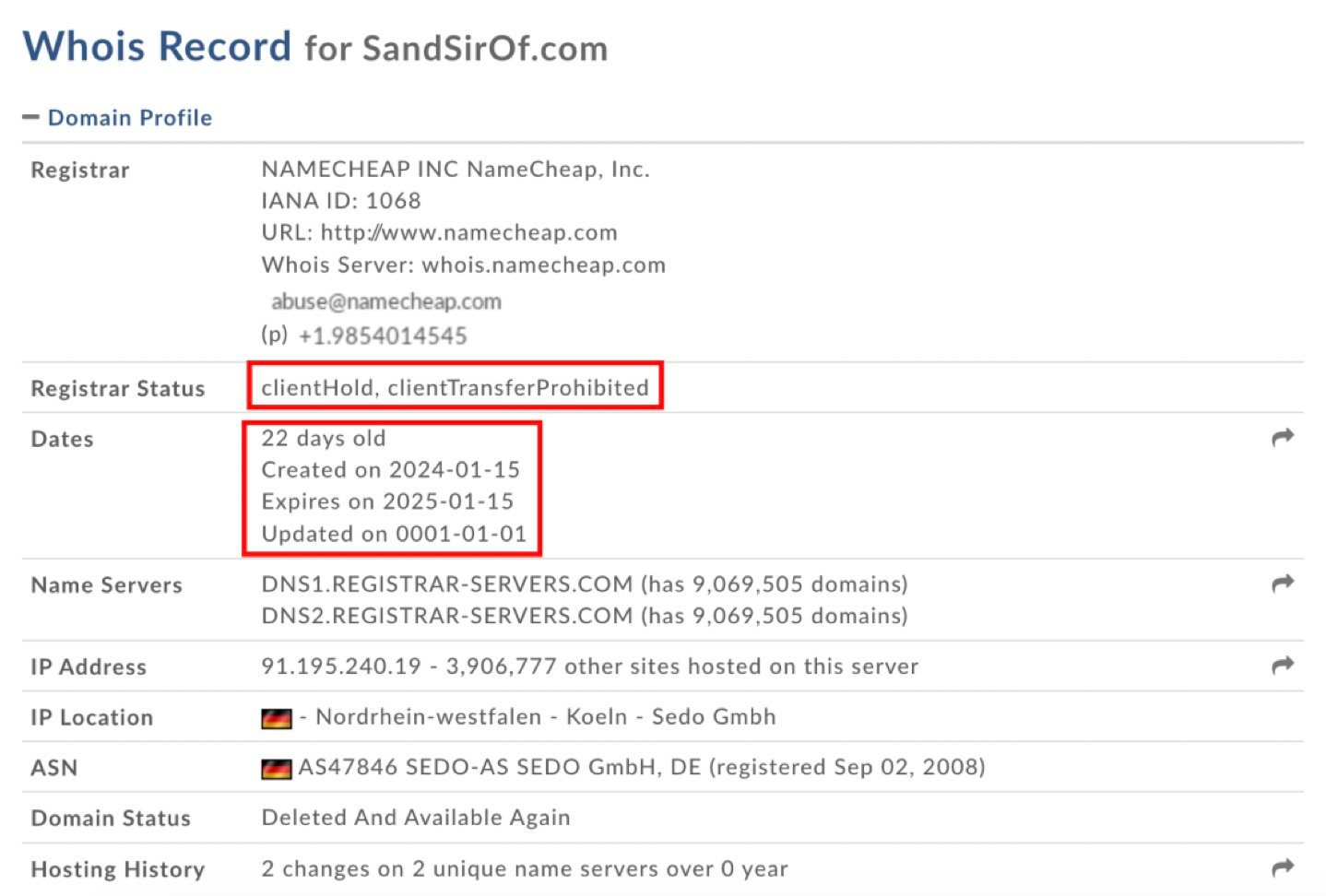
Whois Record of non-profit domain
The domain of the non-profit organization was registered on January 15, approximately two weeks before the sender’s email, and long after the first email between the CEO and non-profit representative (January 3). Since then, hackers have deleted the domain, which is available for purchase at the time of this writing.
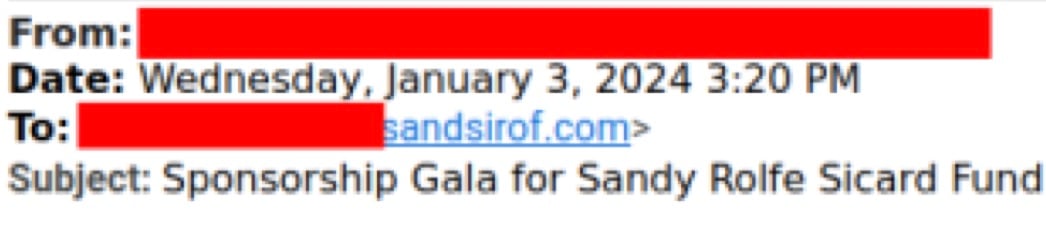 Email header of first fake email
Email header of first fake email
Additionally, the email’s subject line contains a standard reply prefix (“Re:”) instead of one to indicate an email forward (“FW:”), an obvious oversight by hackers.

Warning banner
Also, the sender’s email to the recipient contains a warning banner, which automatically displays when the recipient receives an email from an external sender. This banner doesn’t appear, however, in the correspondence between the CEO and non-profit representative.
Spear-phishing scam takeaways
Creating a fake-forwarded email is not new; it’s a well-established, yet controversial practice used in email marketing.
Yet this appears to be the first time that hackers are using it to exploit victims. In 2020, Knowbe4 reported a similar scheme that used the fake-forward technique in phishing attacks. In those cases, however, the email contained malicious links or attachments to deliver a malicious payload—making it easier for email filters to catch. The attacks also forwarded fake exchanges between two legitimate parties that occurred months to years earlier.
Vade first encountered this spear-phishing scam in mid-2023 and has consistently observed cases to the present day. While they remain relatively infrequent when compared to other forms of email threats, we expect the scam to become more common considering the challenges of detecting it and the ease of creating it.
How to protect yourself
While spear-phishing scams are easy to create and difficult to detect, you can take measures to protect against them. Educate users on the signs, types, and common techniques of spear-phishing scams. Encourage them to never trust the legitimacy of a sender or email without taking measures to verify their authenticity. This may include contacting colleagues in person or by phone to verify financial requests made via email. Also, instruct users to report any suspicious emails to administrators for remediation.
Along with human interventions, fortify your email security with an advanced, AI-powered solution from a third-party provider. Look for solutions that leverage Natural Language Processing (NLP) algorithms, which can detect abusive language patterns, flag words, and malicious phrasing in spear-phishing attacks. Also look for solutions that leverage generative AI to train NLP models to protect against artificially produced threats.




