Are You in the Office? The Spear Phishing Attack You Won’t See Coming
Adrien Gendre
—March 17, 2022
—2 min read

Everyone has been the recipient of a phishing email. Most have been the target of an attempted spear phishing attack. But as both end users and email security solutions have gotten better at recognizing phishing, threat actors have been forced to change tactics. Perhaps the least well-known is the “initial contact” email.
In science fiction movies, aliens make initial contact during a harmless exploration visit, assessing the earthlings before the full invasion. It’s the same concept in spear phishing. The threat actor wants to legitimize contact with a target before going in for a full-on attack.
What is an initial contact spear phishing attack?
Initial contact emails don’t contain any malicious content—no links to follow or attachments to download. They tend to be short and to the point, with a question such as “Are you available?” “Are you in the office” or “Can you help me with a project?”–anything that grabs attention and prompts a response from the recipient. Once the user has responded, they anticipate a request of some sort—they’ve been primed for the assault.
The goal of initial contact spear phishing is to bait the user into responding to the email so that the email address will be whitelisted by the email security filter. The user’s response effectively legitimizes the conversation and clears the way for further communication.
Examples of initial contact spear phishing
In a recent spear phishing attack featuring initial contact, threat actors used COVID-19 as the lure. Hackers targeted medical and infectious disease researchers by impersonating a journalist from a well-known publication.
According to UCLA news, “after initial contact, it seems the cybercriminals start a back and forth communication with anyone who responds. The attacker may even set up a phone conversation but ultimately, they send a malicious Microsoft Teams-like link. Once the user accepts the link, malicious code attempts to execute on the user's system which has resulted in a compromise of the system as well as the user's personal and financial information.”
That the hackers may have used or spoofed Microsoft isn’t surprising. According to research from Vade, in Q4 2021, 56 percent of spear phishing emails targeting US Microsoft 365 tenants were classified as initial contact spear phishing, compared to 9.4 percent classified as CEO fraud. For Microsoft 365 tenants in Europe in Q4, 63 percent of spear phishing emails were classified as initial contact spear phishing, compared to only 6.2 percent classified as CEO fraud.
Because Microsoft cloud products are widely used within enterprises, its users are an easy target for threat actors. By spoofing an address of someone in management within the Microsoft cloud environment, finding a likely victim is that much easier. An initial contact spear phishing attack is the gateway in because it doesn’t look like spam and contains no malicious links or attachments.
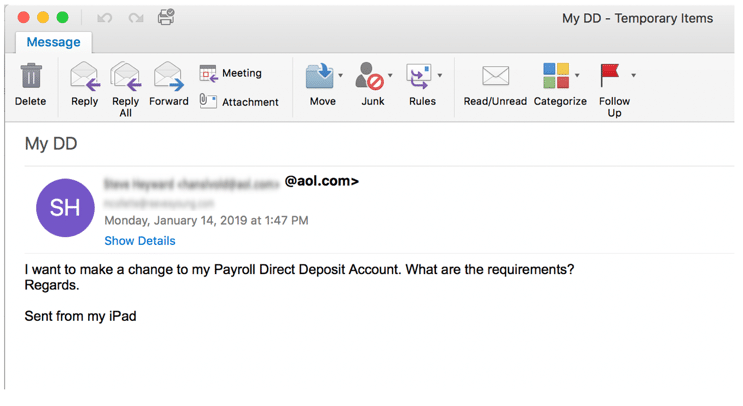
Initial contact spear phishing also helps the threat actor target the user who will be most helpful to them. Often, an initial contact email is an exploratory exercise in which the hacker is searching for the perfect contact. For example, the hacker might be searching for an employee who can authorize wire transfers or pay invoices, or the appropriate HR contact who can change bank accounts and routing numbers for payroll direct deposits.
This type of scam— priming the user before the full attack—works because it relies on layers of trust. The recipient trusts the sender. The communications aren’t out of the ordinary, so the user trusts sending a reply.
Despite the trust, corporate email, especially in cloud-based platforms, is easy to spoof and a “very low barrier to entry,” CRN pointed out. Anyone who receives dozens of emails per day knows that each email gets a quick glance before a decision is made about whether or not to take action. If there is nothing in that initial contact email that looks out of sorts, the user will reply.
It’s an easy win for threat actors, one that the user never sees coming until it is too late. Until users are offered user awareness training to increase their awareness of initial contact spear phishing, they’ll continue to respond and put organizations at risk.




