Anatomy of a Spear Phishing Email
Romain Basset
—August 01, 2019
—4 min read

When is the last time you scrutinized an email? From the sender’s name to the subject line, time stamp, salutation, body, and signature? If you’re like most busy working people, the answer is probably “never.” Hackers know this, and that’s why spear phishing email attacks are so successful.
A spear phishing email serves one purpose: to defraud individuals and businesses out of money. They do this in several ways and with various schemes, from requesting victims to purchase gift cards, execute wire transfers, pay an invoice, or change bank account and routing information.

Beginning with impersonation and almost always culminating in an urgent request, a spear phishing attack is targeted, personal, and very often, financially devastating. When targeting SMBs, hackers request small transactions over the course of multiple attacks. This makes the attacks less likely to set off alarms and therefore increases the chances of success.
As difficult as it can be to identify a spear phishing email, there are some defining characteristics that each of them share:
Sender address
Email senders are not always who they seem. This is thanks to email spoofing, a technique in which cybercriminals impersonate an email address. There are several ways to spoof email addresses.
- Display name spoofing: The sender’s name is spoofed, but the email address is not. With this tactic, the sender appears to be someone you know, such as a colleague, but the email address is different. Also known as display name spoofing, visible alias spoofing is the most common type of spoofing. It requires virtually no technical skill, is extremely easy to carry out, and is effective because people most often look at the sender’s name but not the email address. It can also confuse employees because executives will use their personal email addresses from time to time. On mobile devices, email address are often not visible at all, and users don’t typically expand the sender’s name to reveal the email address.
- Domain spoofing: More sophisticated but easier to detect, domain spoofing allows cybercriminals to specify an email address to use as the sender’s address. In this case, there would be no way for a user to know that an email isn’t coming from a trusted source, such as a colleague. SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain Message Authentication Reporting & Conformance) protect against exact domain spoofing by blocking senders who are not included on a public list of trusted senders.
- Cousin domains: With close cousin spoofing, the email address is nearly identical to a legitimate email address, with a slight modification. For example, the domain mycomany.com becomes mycompany.ltd.com or mycompanyglobal.com. The hope is that the user will not look closely at the email address and miss this slight anomaly. SPF, DKIM, and DMARC cannot protect against close cousin domains.
A spoofed email address is step one in a successful spear phishing email. If a victim doesn’t look closely at the email address, or if the email address is an exact replica of a real address, the victim has already been lured.
Subject line
Pay close attention to the subject line of your emails. Spear phishing attacks often include subject lines designed to cause the victim to react quickly, including flag words like “urgent” and “time sensitive.” When the email supposedly comes from a top executive or other powerful figure in the company, these flag words are especially motivating. This can cause the victim to ignore warning signs and delve immediately into the email to satisfy a superior.
Pretexting
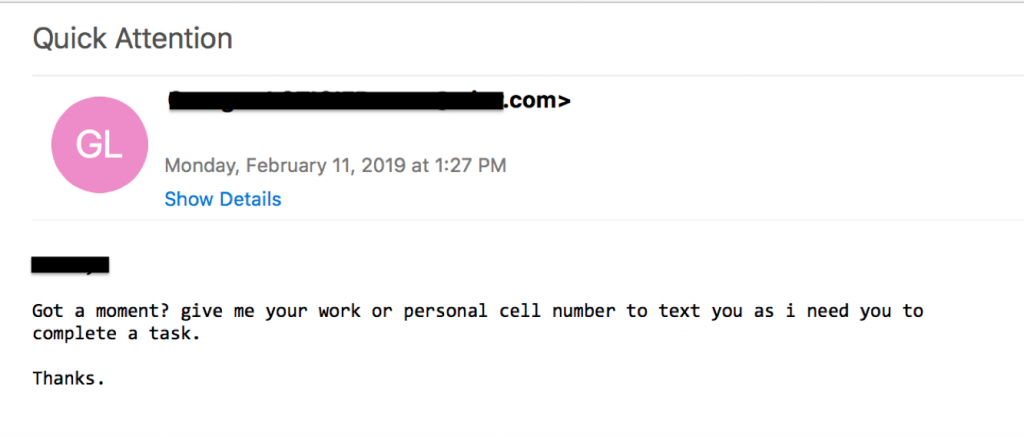
Not all spear phishing attacks include pretexting, but sophisticated hackers are increasingly using this tactic to prime their victims. Pretexting is a form of social engineering in which a hacker converses with a victim over the course one or more emails to prime them for the attack.
It can also be used to identify the right victim. For example, the hacker might reach out to one user and ask if he or she has the resources to fulfill a request, such as executing a wire transfer, changing direct deposit information, or a making a large purchase. If the user responds that they cannot fulfill the request, the hacker will ask to be directed to the right person in the company.
Body
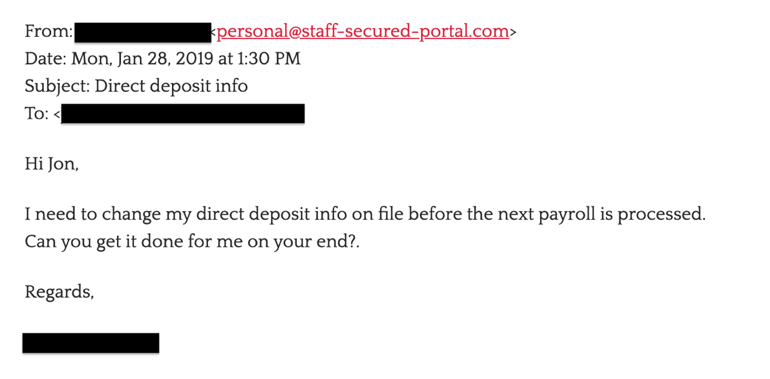
As a general rule, any request that is financially related should scrutinized to ensure that the email is legitimate. If pretexting is part of the scheme, the body of the email will start out friendly and then ease into an eventual request. In the past, spear phishers cut right to the chase, urgently requesting a financial transaction. But like requests for large transactions, this sets off huge red flags, and they’ve learned from their mistakes.
Cybercriminals often make casual conversation based on information they’ve unearthed while researching the victim, such as “How was your vacation?” or “Congrats on the new promotion.” This adds a sense of familiarity to the conversation and helps to lower the victim’s guard.
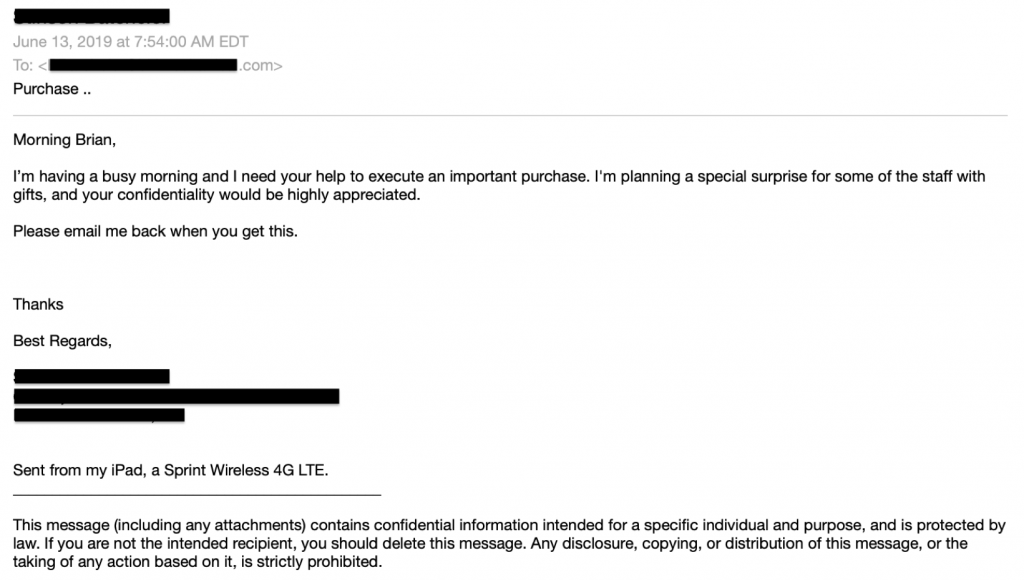
After the initial conversation has been started, the spear phisher will make their request. There is almost always urgency associated with the request. This puts pressure on the victim and causes them to act quickly, without considering that the request might be illegitimate. Requests that purportedly come from a top executive put even more pressure on the victim to act. Fear of consequence and the desire to please are strong psychological motivators that cause victims to overlook red flags.
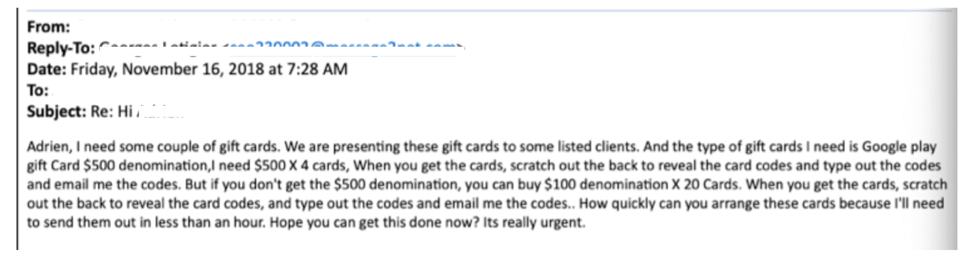
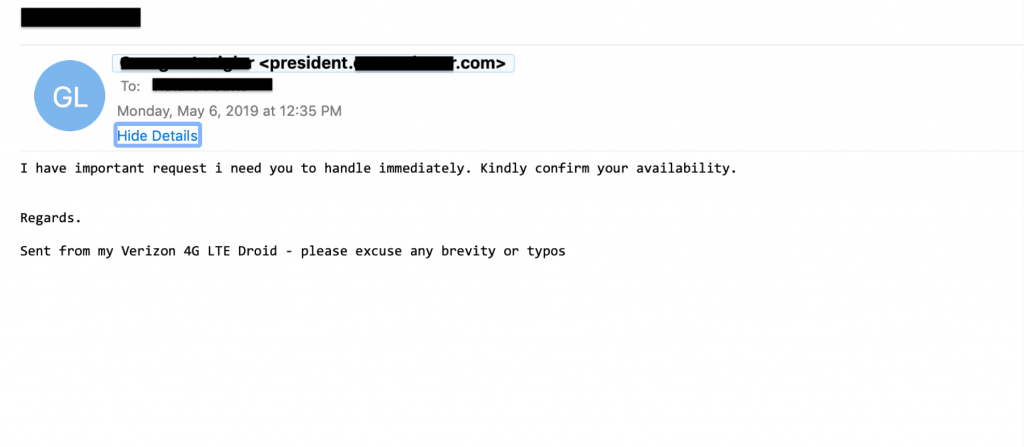
In the below example, a spear phisher posing as the CEO claims he needs to present gift cards to the company’s clients in an upcoming meeting, and he’s running out of time. Notice the flag words “purchase,” “quickly,” and “urgent.” Any of these terms coming from the CEO would make an employee act quickly. These terms are so common in spear phishing that Vade machine learning models are trained to spot these and other flag words while analyzing emails.
Signature
An accomplished spear phisher will use an email signature that matches that of the individual they are impersonating. When an exact match isn’t possible, they’ll add additional information to create a false sense of security. For example, if the cybercriminal can’t create an exact match email address and instead uses a Gmail or Yahoo email address, they’ll add a note in the signature saying the email was sent from a mobile phone or tablet. This makes it slightly easier to believe an executive would send a business email through a personal email address.
Mistakes are also more common when writing from a tablet or mobile phone, so spear phishers will add the “please forgive typos or brevity” in the signature. This makes it more believable that an executive would send a poorly worded email, which is a hallmark of amateur spear phishing.
Protecting your clients from spear phishing email attacks
Educating your customers about spear phishing is essential to protecting them from email threats. In addition to security awareness training, you should offer a solution that provides on-the-fly training when your customer’s users respond to spear phishing emails to ensure that they’re immediately aware of and learn from their mistake.
Today’s email security solutions have become more advanced when it comes to phishing attacks, but most are lacking at spear phishing protection. The nature of the attacks, including the absence of URLs and attachments, makes spear phishing emails extremely difficult to detect. Vade for Office 365 uses machine learning models to analyze the origin, content, and context of emails. Trained to identify email spoofing and abusive language and behaviors unique to spear phishing, the models are continually trained with new data to stay up-to-date on the latest threats.



