Types of Email Fraud SMBs Should Watch Out For
Adrien Gendre
—May 30, 2019
—4 min read

A major cyberattack against a large corporation leads to reputation damage, financial loss, customer churn, and lawsuits. Most large corporations, however, have the resources to recover from various types of email fraud. For small to midsize businesses (SMBs), and particularly small businesses, the damage could be unrecoverable.
Why cybercriminals target SMBs
According to a 2019 report by Switchfast Technologies, 51 percent of SMB leaders said they do not believe their business is a target for cyberattacks. Lacking the revenue—and notoriety—of large corporations, SMBs might not be the most lucrative target for attacks, but they are the most vulnerable. With smaller budgets and fewer IT resources, SMBs are the perfect target for cybercriminals looking for quick, easy wins, and email is the weapon of choice.
With a single email, cybercriminals can easily fool employees and gain access to an SMBs most critical—and sensitive—resources. Here are the most common types of email fraud you should look out for:
Phishing
The first phishing emails were easy to spot and typically featured bad grammar combined with laughable requests and demands. While amateur phishers continue to make the same mistakes, phishers have become so sophisticated that they easily bypass the email filters designed to stop them.
Today, phishing emails and web pages are often indistinguishable from the real thing. They typically impersonate companies that the victim does business with, including credit card companies and banks, or services they use to run their businesses, such as Dropbox and Office 365. In highly targeted attacks, phishers identify a business’s vendors and then replicate the vendor’s emails, using the vendor’s fonts, logos, images, email signatures, and even disclaimers. This level of sophistication is relatively new, and many SMBs have not kept pace. Sixty-five percent of SMB employees, the Switchfast report says, have never received a phishing test during their time with their current company.
Can you spot a phishing page? Take the phishing IQ test to find out.
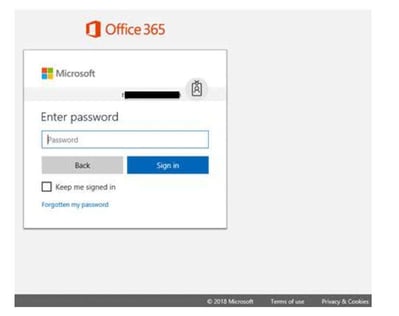
The hallmark of a phishing email is a malicious link. A typical phishing email will ask a victim to click on a link to log into an account, such as a productivity suite like Office 365 or a human resources platform. The link directs the victim to a phishing page that looks like an exact replica of the vendor’s webpage. Once they’ve been lured in, the victim enters account credentials or personally identifiable information.
When it comes to brand impersonation, banks are a phisher’s favorite, but cloud services are even more popular. Microsoft has been the #1 impersonated brand for four quarters, topping popular targets like Bank of America and even technology companies known for housing millions of bank account numbers, including PayPal.
Below are just a few of the most common types of email fraud perpetrated by phishers:
- Office 365 credential phishing: The victim receives an email from Microsoft asking them to log into Office 365, whether to access a shared file, update their account information, or retrieve a voice message. A link leads the victim to a replica Office 365 page. Once the victim enters their credentials, the phisher harvests the credentials and gains access to the entire Office 365 suite.
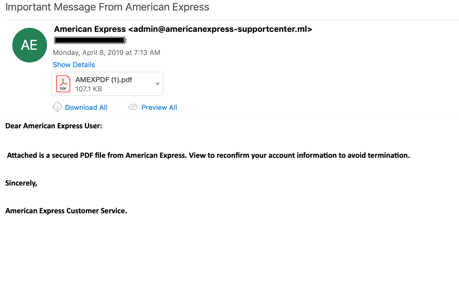
- Fake invoice attached: In this variation of the scam, phishers send a fake invoice via email, along with a link to cancel the purchase. The link leads to a phishing page where the victim is told to enter their account credentials, which are again harvested.
- HR phishing: Impersonating an HR software platform, the phisher sends an email to an employee asking them to log in to the HR portal to update their personal information. Once the victim’s credentials are stolen via a phishing page, the phisher has access to all the employee’s personally identifiable information, including birthdate, social security number, and bank account information for direct deposits.
- Update payment attack: The email alerts the victim that their account or subscription has been cancelled or suspended and asks them to log in to their account to provide payment details. These attacks typically impersonate banks and technology companies like Amazon, Netflix, Apple, and Microsoft.
Spear phishing
The difference between phishing and spear phishing is subtle but effective. Spear phishing emails do not include links and instead rely on social engineering to trick the victim. With social media platforms housing a victim’s most personal information, cybercriminals have access to intimate details of a person’s life that reveal their attitudes and behaviors. Armed with this information, the cybercriminal proceeds to craft spear phishing emails in a way they know will activate an immediate response.
Many spear phishing emails impersonate high-ranking employees, such as CEOs, and target employees in lower ranks. Getting a request from a CEO creates a visceral response in the victim, a desire to act quickly and complete the requested action. It’s highly targeted and extremely effective. Victims often say they feared consequences of not completing the action or simply wanted to look like a good employee for completing an urgent request.
Because spear phishing emails impersonate individuals rather than companies, the emails are easier for the cybercriminal to create, requiring only an email address spoofing the purported sender’s name. The hope is that the victim will react to seeing a message from the sender and not check the email address.
Here are some of the most common spear phishing attacks seen by Vade:
- Gift card requests: In many cases, the purported CEO first asks the employee if they’re available to complete the request. If the victim bites, the attacker then asks the victim to purchase gift cards and send them the codes on the back of the cards. There is always an urgency to this request. It’s designed to convince the employee that they must act quickly, which could lead them to fear consequences if they don’t complete the request.
- Direct deposit changes: A variation on the phishing scam, the spear phishing version impersonates an employee and targets an HR representative. In the email, the purported employee asks the HR representative to change their bank account information for their direct deposit. On payday, the paycheck goes into the cybercriminal’s account.
- Wire transfer orders: Also known as business email compromise (BEC), this spear phishing attack is the most costly. The cybercriminal poses as a top executive and targets someone in the business who has access to the company’s finances. The attacker requests an urgent wire transfer to be sent to a client or vendor, and the victim unknowingly transfers funds to a fraudulent bank account.
- Invoice attached attack: This variation on the phishing attack uses no links in the email but spreads malware through an attachment. The cybercriminal sends a fake (urgent) invoice to an employee. Once opened, the file executes malware or ransomware, which spreads throughout the system, often for the purpose of recording account credentials and keystrokes.
Protecting your SMB from email fraud
Employee awareness is critical for any business, but especially SMBs that have fewer IT resources. Providing regular security awareness training sessions not only educates new employees about different types of email fraud but keeps security awareness top of mind for employees who have been with your company for some time. Additionally, training should be provided on-the-fly when employees have clicked on phishing links or responded to spear phishing emails. This connects the incident directly to the training.
Invest in an email security filter that scans for unknown threats. Reputation and signature-based email filters can only identify and block threats that are known, including blacklisted IPs and phishing URLs. These outdated methods of threat detection are no match for the sophistication of today’s hackers, who use a variety of techniques to slip past filters, including using redirects on clean URLs, creating cousin domains, and changing the characteristics of malware code. With 72 percent of SMBs reporting that exploits and malware evaded their existing protection systems, it’s more important than ever to have advanced threat protection.



