Hacker Impersonates TrustWallet in Crypto Phishing Scam
Natalie Petitto
—June 30, 2022
—2 min read

On June 12, Vade observed a wave of more than 50,000 phishing emails sent from a malicious Zendesk account. In one campaign, the phisher impersonates TrustWallet, luring users into divulging their recovery phrases on a sleek TrustWallet phishing page.
The TrustWallet phishing attack
TrustWallet, a ethereum wallet and cryptocurrency wallet store, is a popular platform for storing NFTs (non-fungible tokens). Phishers notoriously develop phishing campaigns around the news cycle, and as NFTs and cryptocurrencies overall have have seen a significant downturn in recent weeks, on-edge investors are likely to react quickly to emails about their crypto accounts.
The phishing email itself impersonates the TrustWallet brand. As you can see from the below email, the TrustWallet logo matches TrustWallet’s official logo and includes a support link titled “Support 2022.” Additionally, Zendesk’s legitimate footer appears at the bottom of the email, giving the email an additional air of legitimacy from a known, trusted brand.
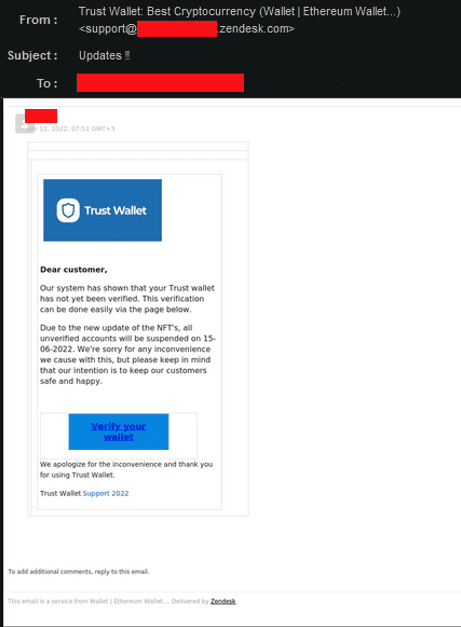
The phishing email informs the user that their wallet must be verified due to an NFT update. Failing to verify the wallets, the email warns, will result in account suspension. The user is encouraged to verify their account by June 15 by clicking on a phishing link with the CTA “Verify your wallet.”
The phishing URL is shortened with s.id., a link shortener and microsite builder that allows the phisher to both obfuscate the phishing link and track the phishing campaign through S.id’s analytics dashboard, which provides statistics on clicks, locations, and more.
The redirected URL leads to a website hosted, and potentially created, on Elementor Cloud, which specialized in creation and hosting of WordPress websites. The phishing website uses a similar design and the same sections as the official TrustWallet website.

TrustWallet phishing page
The phishing page displays a 10-second countdown to “open their secure internet environment.” This message is intended to raise the user’s confidence in the security of the website. After the countdown ends, the malicious page is triggered.
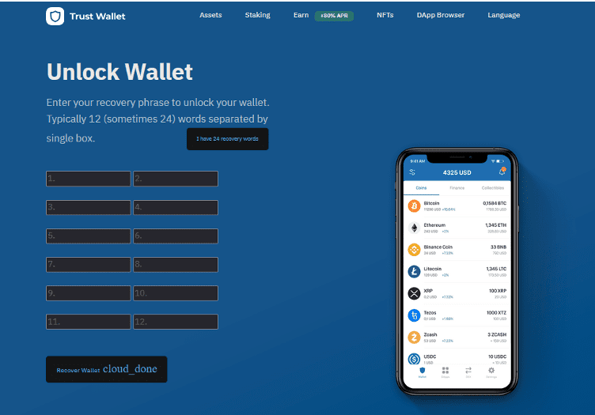 Final TrustWallet phishing page with recovery phrase
Final TrustWallet phishing page with recovery phrase
The user is asked to enter their recovery phrase to unlock their wallet. Most cryptocurrency wallets use 12-word recovery phrases, but in some cases, they may use 24. The phisher has considered this and includes a button to click if the user does in fact use a 24-word recovery phrase. This technique accomplishes two things: First, it makes the phishing page seem more legitimate in the eyes of the user because it has covered both scenarios. Second, the phishing page can accept credentials from either 12- or 24-word recovery phrases, widening the scope of the phishing campaign.
Recognizing phishing from malicious accounts
While inspecting the sender email address is an important step in scrutinizing an email for signs of email spoofing in phishing, it is not always enough to recognize an attack. As is the case in this TrustWallet phishing attack, the email address is a legitimate, albeit malicious Zendesk email, so inspecting the domain is not helpful in recognizing the attack.
The phishing email text is not horrendously ungrammatical, as many lesser phishing emails are, but it is also not perfect. “We’re sorry for any inconvenience we cause with this” is a sloppy construction that most users will recognize as suspicious if they read the email carefully. Training your users to recognize these mistakes could help them identify this phishing email if the email address fooled them on the first pass.
Finally, as filters get better at identifying and blocking known techniques, hackers adjust and develop new ones to bypass detection. As a result, your phishing awareness training should be continually updated to reflect the latest techniques used by phishers.





