Recent Phishing Attacks Target Japanese Companies
Vade Experts
—December 21, 2023
—4 min read

Over a five-day period in November, Vade detected numerous phishing attacks targeting companies in Japan—including global manufacturers and automotive companies. The recent phishing attacks provide a glimpse of the modern threats and techniques not only commonly affecting Japanese organizations—but those across the world and every sector. Notably, all three malicious campaigns bypassed detection by Microsoft.
In this post, we detail three phishing attacks including their techniques and methods.
Recent phishing attack #1
On November 16, Vade detected a phishing email from the domain address of a manufacturing company. The email display name includes “DocuSign” to give the appearance of a system generated message.
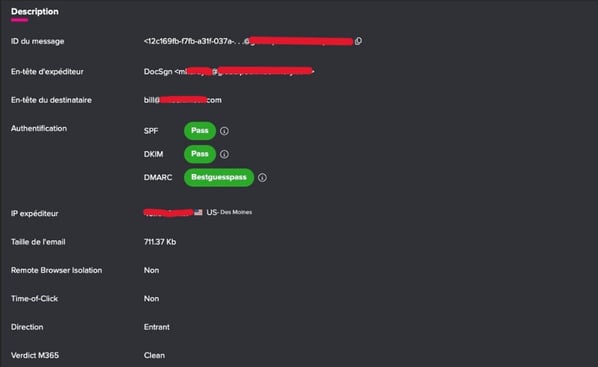
Vade email log details of phishing threat
The email subject line contains the email address of the intended victim with the call to action, “Sign Now.” The email originated from an IP address located in the US and passed the authentication checks of SPF, DKIM, and DMARC.
The email contains a phishing link that points to a resource on Strava, a global fitness app for tracking exercise activities and competing with other athletes. Included in this link is an original URL that redirects to Baidu.com, the Chinese search engine. The fragment at the end of the URL appears to be an anchor, but its meaning depends on how the targeted site interprets it.
Once the intended victim arrives on Strava, they’re redirected to Baidu.com momentarily. The scheme then abuses Baidu’s redirect feature to send the user to the destination phishing page.
During this process, the intended target encounters several intermediary pages, which serve to prevent further analysis by email filters. Hackers often use intermediary pages—which lack fields or phishing links—to trick email filters into deeming an email as safe. At the same time, these pages also make the campaign appear more legitimate in the eyes of the intended victim.
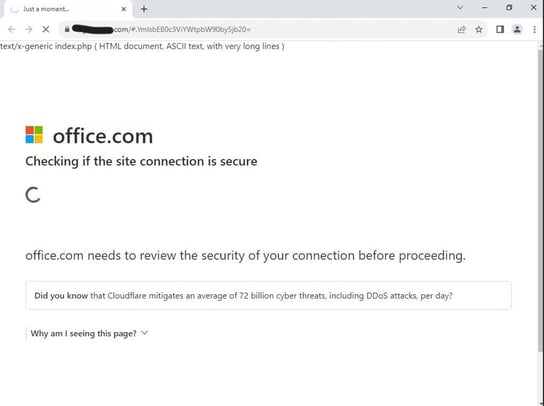
Fake Microsoft security scan
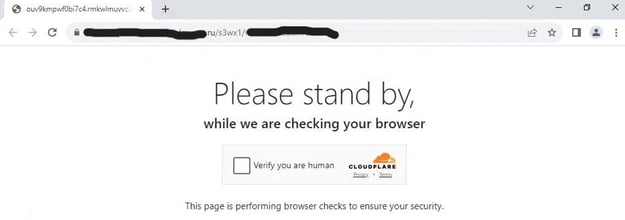
Cloudflare security check
The cover pages simulate fake security scans by Microsoft and Cloudflare. Like other attacks observed by Vade, the phishing page is hosted by Cloudflare, allowing it to benefit from the platform’s anti-bot mechanisms. These mechanisms mimic human behavior and enable threats to bypass automated bot detection solutions.
Once the security check by Cloudflare is complete, the victim is directed to the destination phishing page. Here, the user encounters a Microsoft Authentication form, which pre-populates their email address. This added touch of personalization creates an air of legitimacy and may distract the user from noticing the domain, which is hosted in Russia.
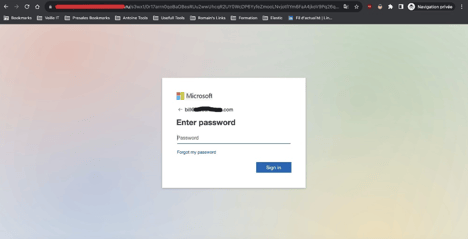
Destination phishing page – Microsoft authentication form
As seen on VirusTotal, no security vendors deemed the phishing link malicious.
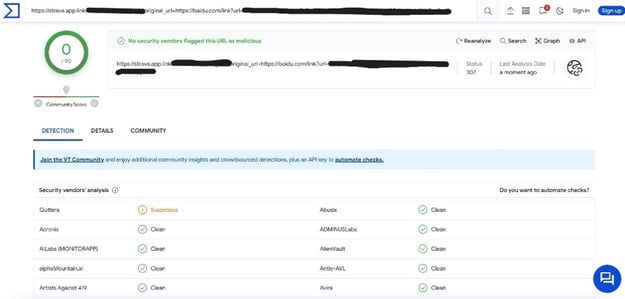
VirusTotal analysis of phishing link
Vade researchers believe the email used to send the phishing campaign was likely compromised.
Recent phishing attack #2
On November 20, Vade detected an attack that targeted a large Japanese automotive manufacturer. The phishing campaign appears to come from a logistics company in Vietnam. The email originated from an IP address based in the US and passed all the authentication checks of SPF, DKIM, and DMARC.
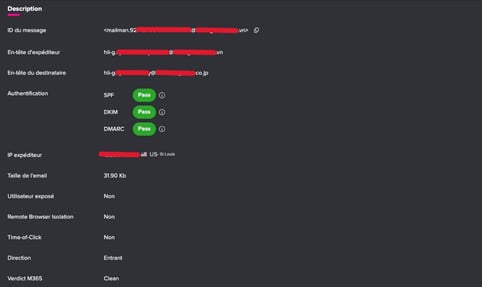
Vade email logs of phishing threat
The subject line of the phishing attack notifies the victim that their message to an undisclosed email address is awaiting “moderator approval.”

Link redirect to fraudulent phishing page
The email contains a phishing link that appears to point to the URL of the logistics company. However, the link contains a redirect that sends the victim to a fake cPanel WebMail login page.
 Fake cPanel WebMail login page
Fake cPanel WebMail login page
The login page belongs to a domain address hosted in Vietnam.
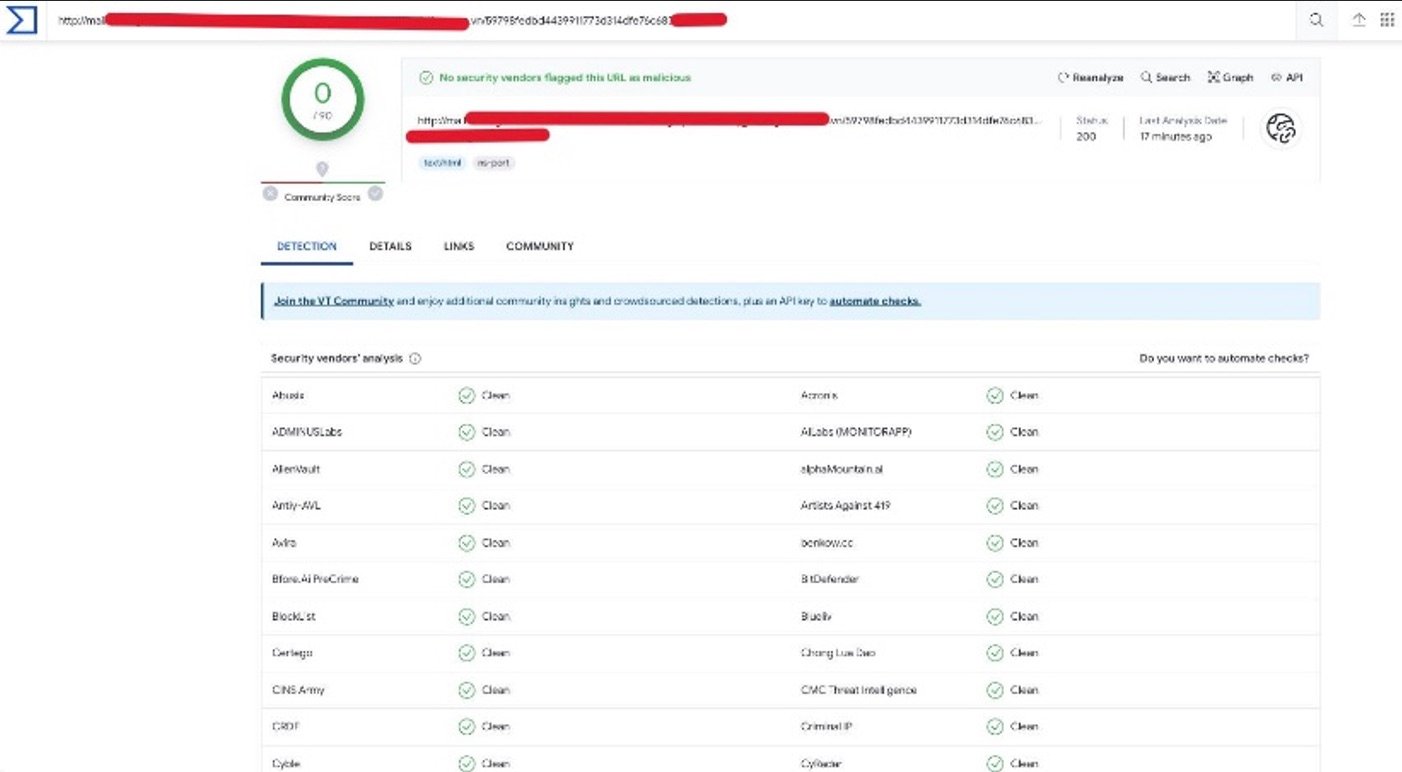
VirusTotal analysis of phishing email
Like the previous attack, no security vendors found the link to be malicious according to VirusTotal. An analysis by urlscan.io also found the phishing link to be safe.
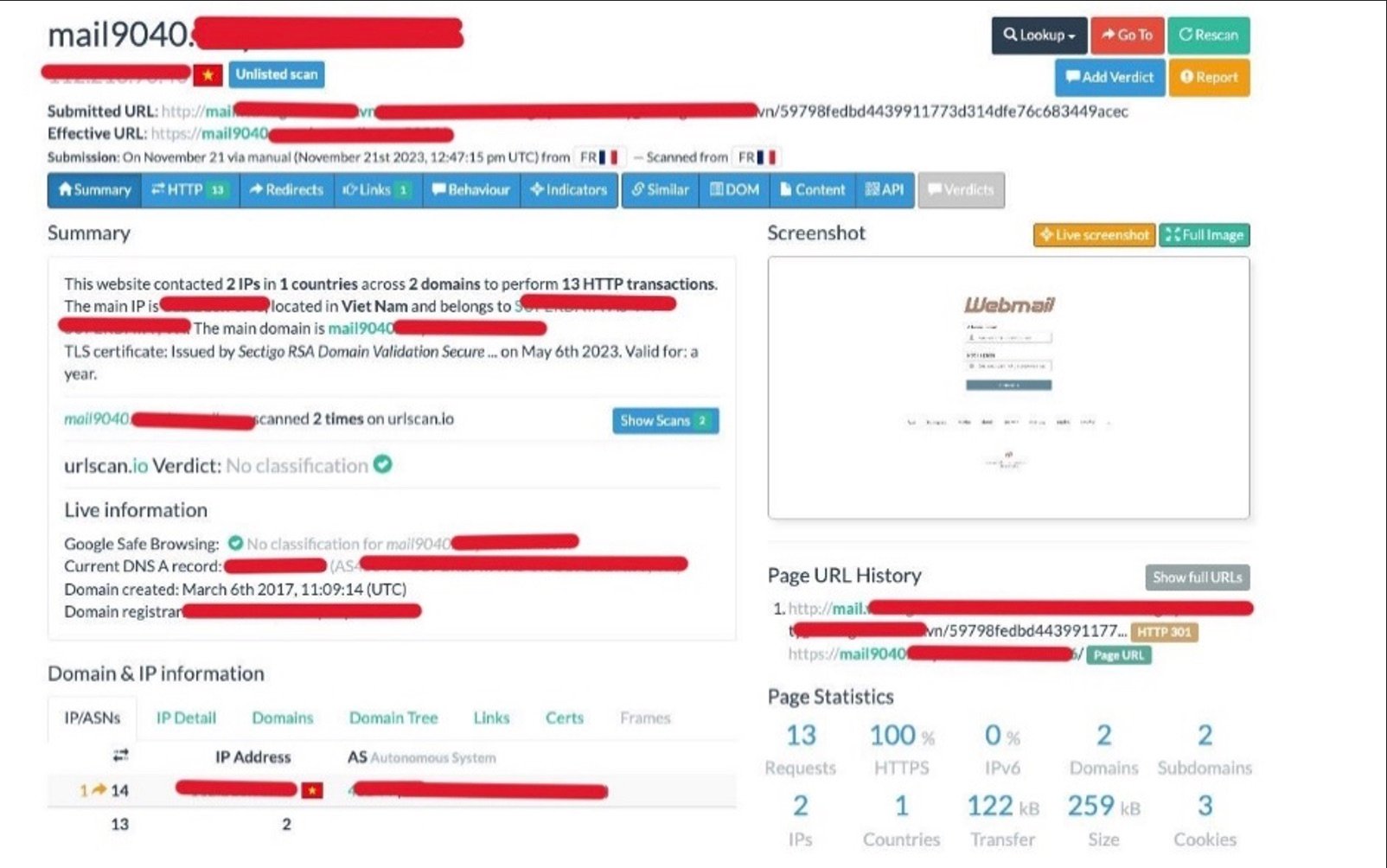
urlscan.io analysis of phishing email
Recent phishing attack #3
On November 21, Vade detected a phishing attack on a manufacturing company in Japan. The threat targeted an employee at the company to harvest their password.
The attack uses display name spoofing to create the appearance of legitimacy. The display name lists an email address that appears to belong to an employee of the organization and a colleague of the intended victim. Hackers commonly use this technique to gain the victim’s trust and pass the checks of SPF, DKIM, and DMARC. It also remains highly effective when targeting victims using mobile devices. That’s because email clients hide the domain address by default, making it more difficult for recipients to verify the identity of the sender.
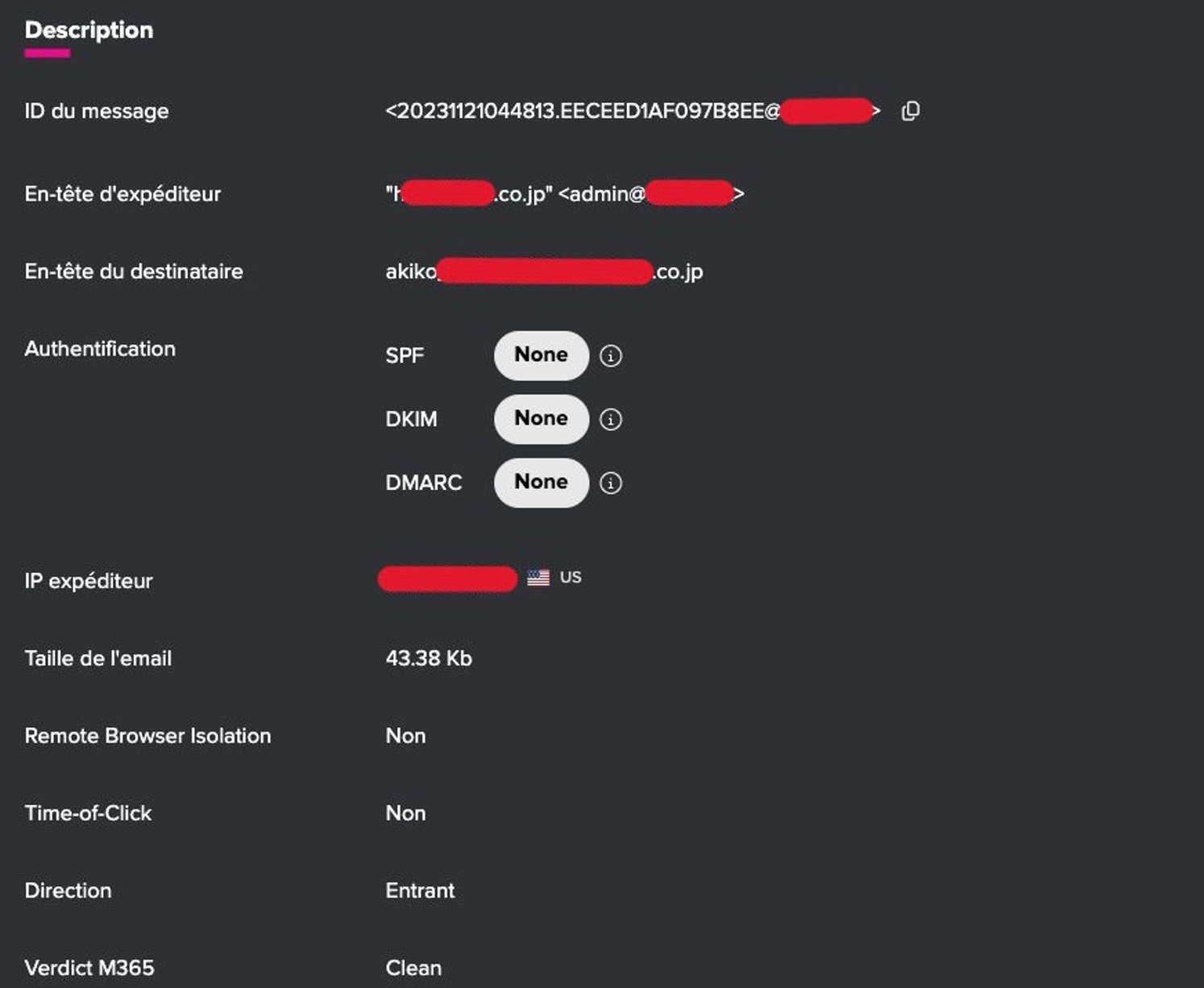
In this case, the actual domain address of the phishing email belongs to a hosting company based in the US.
Vade email logs of phishing threat
The SPF, DKIM, or DMARC checks all returned a “None” status. Unlike a “Fail” status, “None” often indicates the absence of a SPF record, an invalid or misconfigured key in the DNS record, and the lack of an enforcement policy for DMARC.
The subject line includes the email address of the intended victim, an effort to personalize the message. The email contains a phishing link that directs the user to a phishing page hosted in the US. Here, the intended victim views an authentication form that pre-populates with their email address to personalize the experience and make it appear more credible.
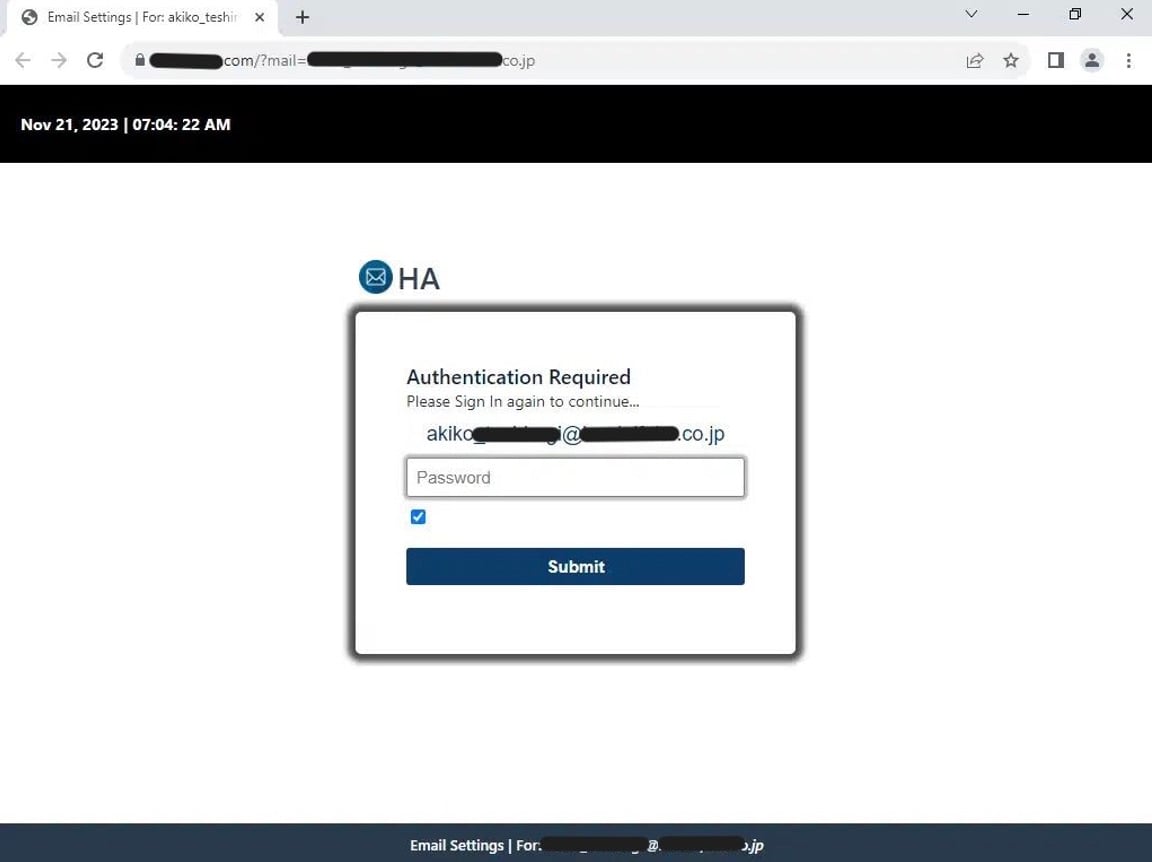
Phishing page
If the user enters their password, hackers then harvest it while the phishing page refreshes and appears to load the user’s settings.
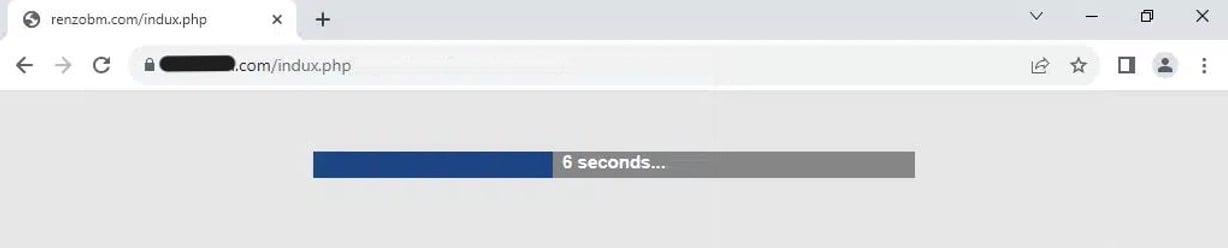
Phishing page after victim’s password is harvested
Notably, Microsoft deemed the email as safe, while other sources flagged it as malicious. This includes urlscan.io, Google Safe Browsing, many security vendors on VirusTotal, and Talos.
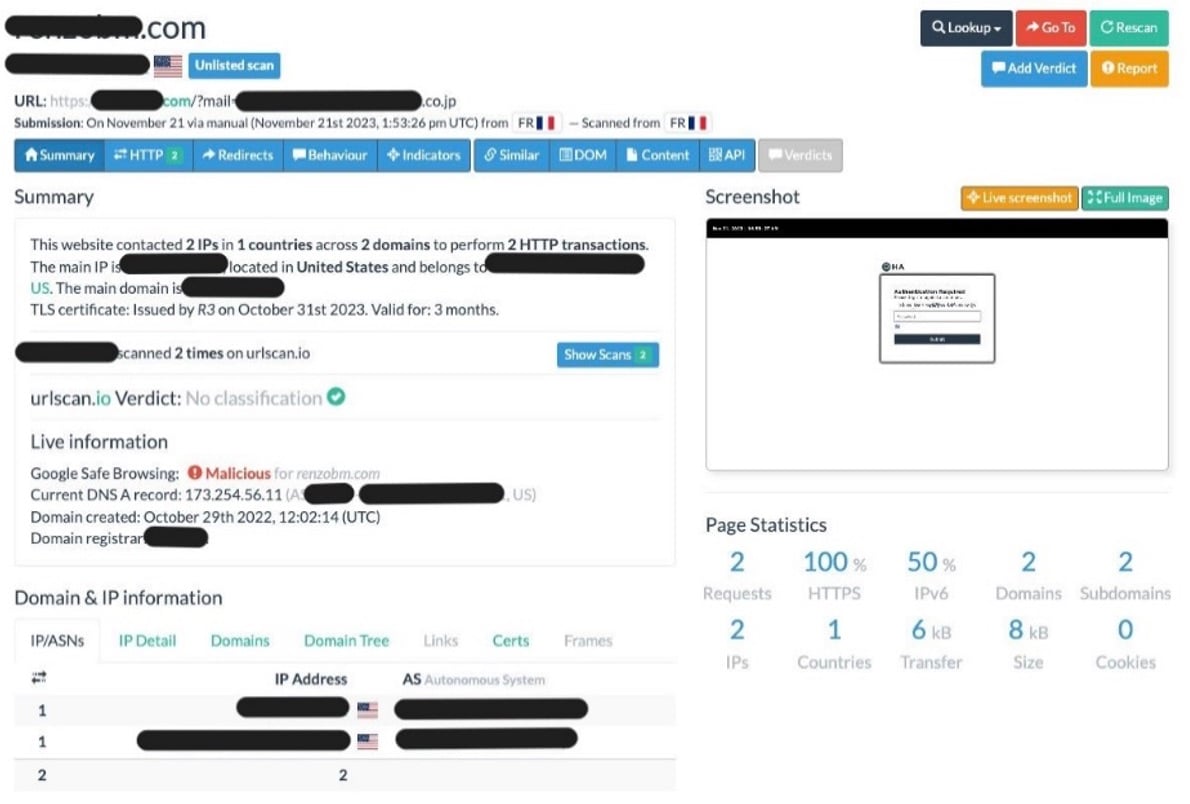
urlscan.io analysis of phishing site
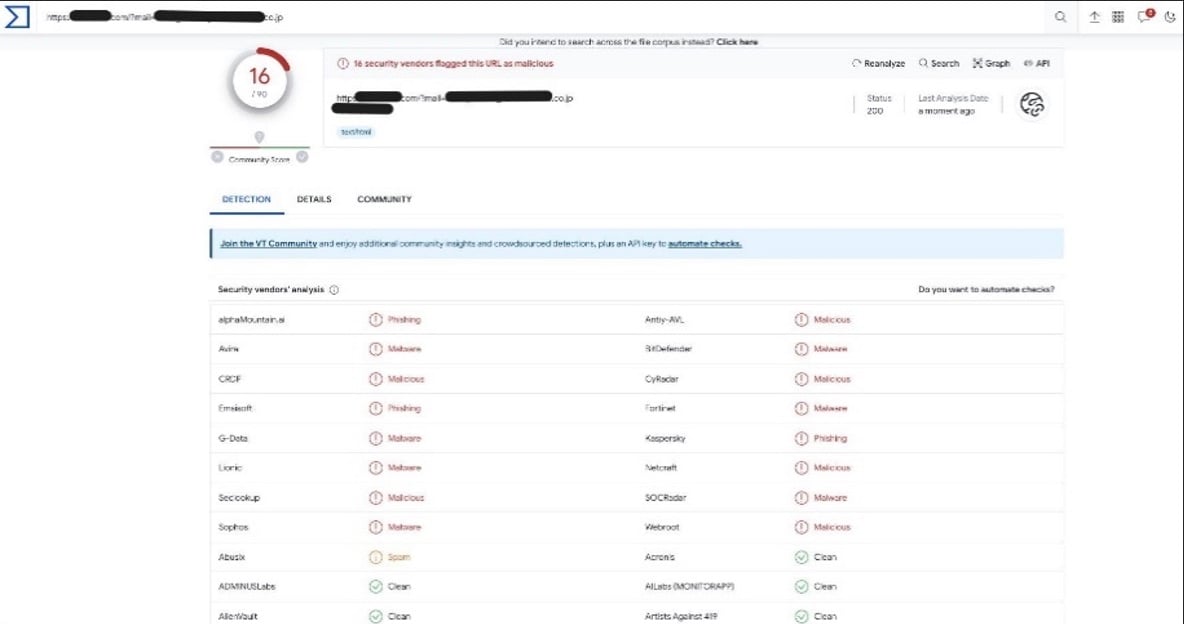
VirusTotal analysis of phishing site
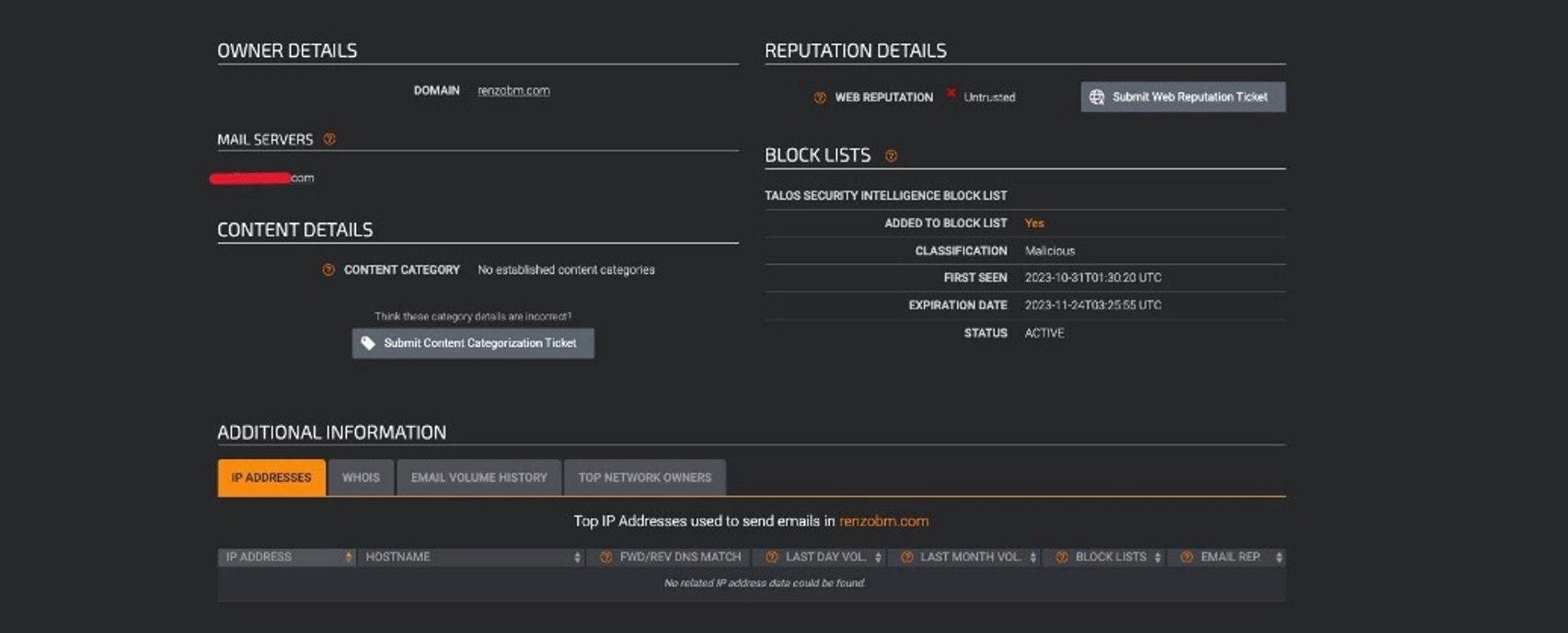
Talos scan of phishing site
Protect your organization from phishing
Phishing remains the most common cyberthreat and a top source of initial compromise. To stay protected against this threat—including the recent phishing attacks examined in this post—Vade experts recommend implementing phishing awareness training. This can make users proficient in spotting the common signs of phishing scams and reporting suspicious emails to administrators for remediation.
Organizations should also look to fortify their email security. Since the release of its Market Guide for Email Security 2020, Gartner recommends that organizations adopt a third-party email security solution to augment the native protections of productivity suites. Gartner reiterated this guidance in 2023 with the release of its latest Market Guide for Email Security.