Phishing Scam Exploits YouTube Attribution Links, Cloudflare Captcha
Todd Stansfield
—April 06, 2023
—4 min read

Vade has detected a new phishing campaign that uses legitimate YouTube attribution links and a Cloudflare CAPTCHA to evade detection. While use of YouTube redirect URLs in phishing attacks is not new, use of YouTube attribution links is a new tactic that could bypass email filters that scan for suspicious redirects.
Intended victims of the attack receive a spoofed email alerting them that their Microsoft 365 password has expired. The email uses display name spoofing to create the appearance of legitimacy and draw attention away from the sender’s email address, which doesn’t match a legitimate Microsoft domain.
The email’s subject line contains the user’s email address followed by the phrase “Password expiry Reminder” and the current date. The use of personalization and contextualization gives the email an added touch of legitimacy.
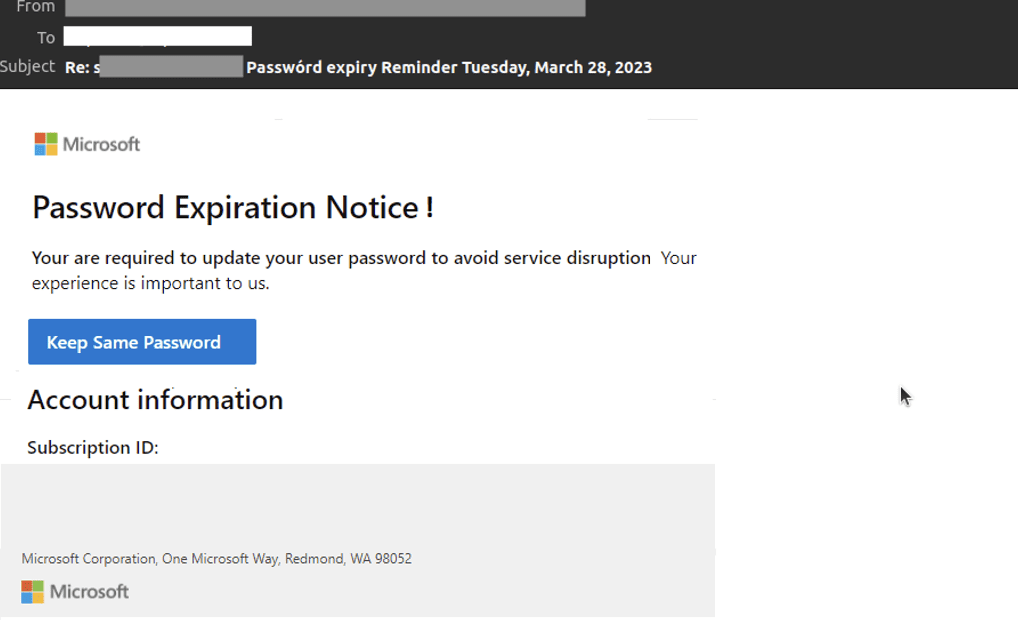
Microsoft 365 phishing email detected by Vade
Featuring Microsoft’s logo and branding, the body of the email alerts the user that their Microsoft 365 password has expired and must be updated to “avoid service disruption.” Notably, the email doesn’t contain misspellings or grammatical errors. A button appears below the notice that gives the recipient the option to keep their current password. The button is hyperlinked to a YouTube URL that contains the phrase, “attribution_link.”
The attribution link shows where the link originally came from—the string will match to the account or IP address or browser fingerprint in a specific database of whoever created the link. It is mainly used to give someone credit for using their content when they require credit.
In this case, attribution links are used to redirect users to the phishing webpage. If users click the button in the phishing email, it quickly redirects them to Youtube first:
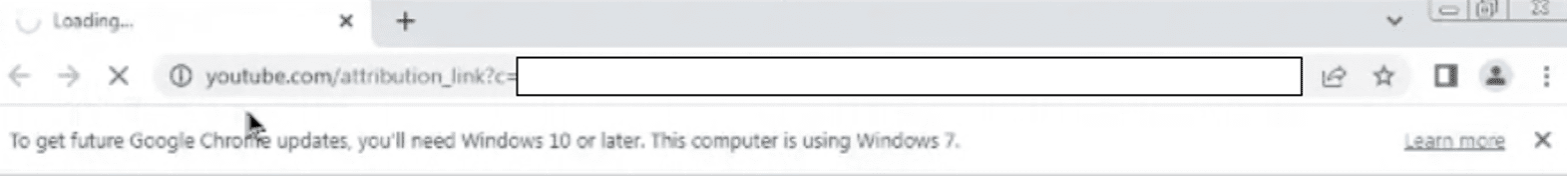
And then to a webpage that features a Cloudflare CAPTCHA. The odds are that the webpage is hosted on Cloudflare, and uses the URL crawling and bot protections.
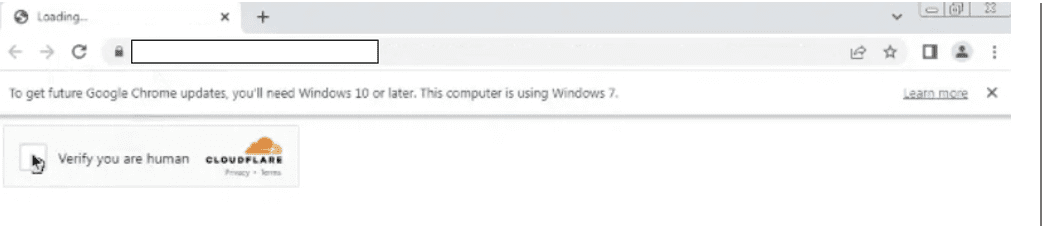 Cloudflare intermediary page detected by Vade
Cloudflare intermediary page detected by Vade
Once users click the CAPTCHA, it directs them to a Microsoft 365 phishing page. Here, the page auto-populates the user’s email address and includes a field for entering their password.
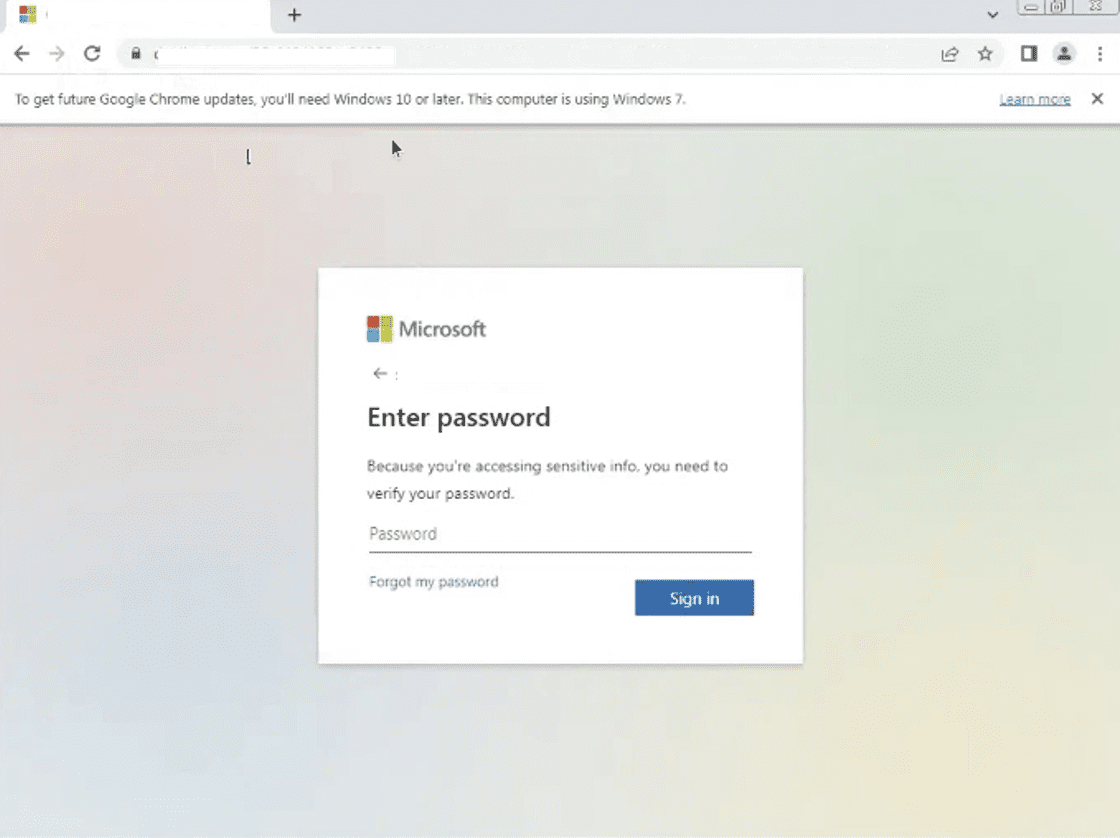 Microsoft 365 destination phishing page detected by Vade
Microsoft 365 destination phishing page detected by Vade
Like the address of the phishing email, the domain of the phishing page doesn’t resemble a legitimate Microsoft URL. However, the personalization of the scheme draws attention away from the obvious signs of phishing and to the features of the webpage that enhance its perceived legitimacy.
If users enter their password and click Sign In, hackers can harvest the credentials for an account takeover.
By using Youtube, the hacker can trick the user because the latter knows and considers this website as legitimate. Hackers try to use legitimate services to bypass classic email security solutions based on reputation. They are taking advantage of both Youtube and Cloudflare, both of which are potentially whitelisted on many email gateways.
Notice that zero security vendors regard this URL as malicious on VirusTotal:
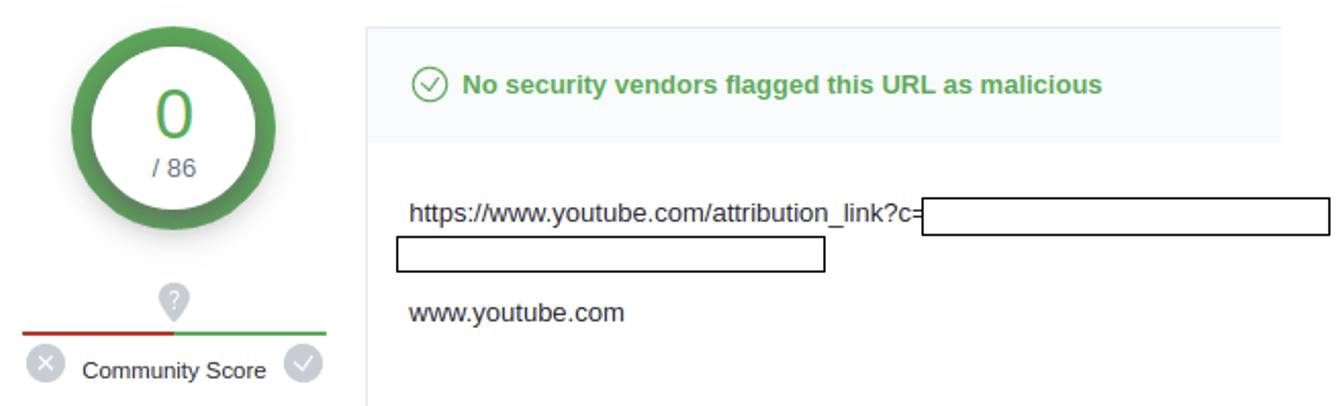
Vade analysis:
There were more than 1,000 emails in the last 30 days regarding this specific campaign. It is possible to create a malicious link at the hand, without using any YouTube service. The threat domain ending with “.ru” was registered four days before the delivery of the threat. This domain also respects protocol checks used in SMTP transactions (SPF, DKIM, ARC...): it is clean from this point of view.
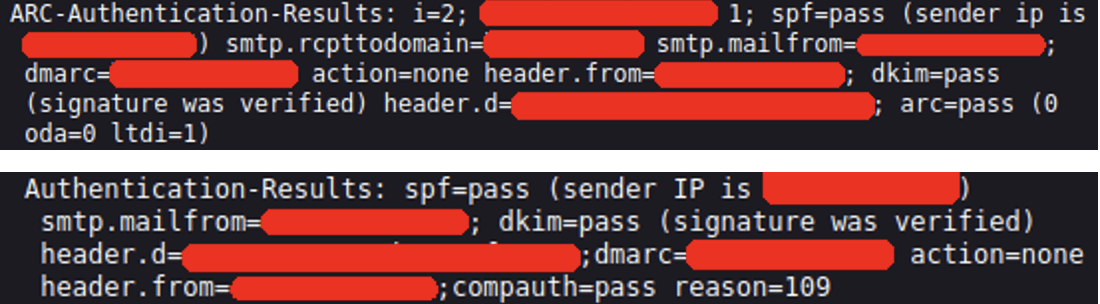
Vade detected this phishing attack from the first email because we do not rely only on reputation filtering, but also provide a mechanism and behavior analysis of the remote URL. In this campaign, the “Open Redirect” system in the threat URL, used to redirect the user to another URL, has been identified and make it possible to block the threat.
Microsoft phishing scam: key takeaways
While this attack presents unique features and techniques, Vade researchers have uncovered similarities to broader themes and trends in phishing. This includes an increase in phishing attacks that spoof productivity suites. Microsoft and Google, producers of the #1 and #2 most popular productivity suites in the world, were the second and third most impersonated brands in phishing attacks last year, respectively.
As highlighted in Vade’s annual Phishers’ Favorites report, Microsoft has been among the two most impersonated brands for five consecutive years. Microsoft’s sustained popularity as a target of spoofing, and Google’s recent emergence as one, directly corresponds to the growth of productivity suite users.
While this helps explain the increase in attacks like this one, so does the importance of email to these platforms. In addition to providing personalized and timely alerts, email gives users direct and efficient access to documents, instant message feeds, and shared files. This appears to be changing users’ behavior, making them more likely to interact with emails and less likely to scrutinize their credibility or origin.
This attack also supports another trend uncovered by Vade researchers. Last year, Vade experts predicted that hackers would increasingly use legitimate services to help facilitate phishing attacks. In this scheme, hackers use an attribution link generated from YouTube to conceal the URL redirect.
Previously documented phishing attacks have also used YouTube links to redirect users to malicious webpages. However, in those cases, the links included the label “redirect,” giving a visual indication that it didn’t match the URL of the destination page.
The use of intermediary pages also appears to be an increasingly popular technique among hackers, because it can prevent the analysis of phishing pages by email filters. In this scheme, the Cloudflare CAPTCHA page is designed to intercept email filters and prevent them from scanning the spoofed Microsoft webpage. If the technique succeeds, the email filters will verify the email as safe because the intermediary page doesn’t contain any fields for phishing.
How to protect yourself against Microsoft phishing and other scams
Phishing attacks like this one will likely only increase in volume and sophistication. The good news is you can take precautions now to stay protected. Encourage and educate your team to adopt good cyber hygiene practices. Always verify the sender of an email and use a separate browser for accessing accounts or updating passwords. Also, if your business is using Microsoft 365, consider an integrated email security solution to filter advanced phishing threats and augment the protection of Microsoft’s native protection. And invest in phishing awareness training to ensure your users are proficient at spotting and handling email-borne threats.




