Email security predictions 2023: 4 Trends Shaping the Industry
Todd Stansfield
—November 17, 2022
—5 min read

Keeping up with the latest developments in email security is mission-critical for your business. In H1 2022, Vade detected more than 440 million phishing and malware-laced emails, a figure illustrating that cybercriminals remain as active and motivated as ever. To help you strengthen your cybersecurity posture, we reveal our annual email security predictions. Vade’s experts share their insights on the biggest threats and developments that will shape email security in 2023.
1. Phishing attacks will target MFA and legitimate services
Multi-factor authorization (MFA) is no longer a novel concept for organizations, but a widely used security measure that uses at least two different login methods to verify a person’s identity. While MFA is an important cybersecurity solution, hackers have developed techniques to bypass it. This enables them to exploit organizations’ overconfidence in the security of the tool, which they often see as a silver bullet.

According to Romain Basset, Director of Customer Services at Vade, “We’ll see more phishing campaigns that are able to circumvent MFA by acting as a proxy with the real authentication system, or by tricking users who have MFA fatigue.” Basset points to a recent case in September 2022, when MFA fatigue enabled a hacker to compromise Uber’s internal networks.
Basset predicts an increase in phishing campaigns that abuse legitimate services to distribute phishing links. “Recent attacks on a top career service in France is a great example of a legitimate platform being weaponized,” he says. In the attack, hackers applied to job postings and used the platform’s legitimate infrastructure to transmit phishing links to companies recruiting candidates. Vade first detected the phishing scam in September 2022.
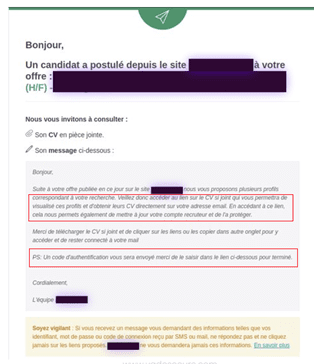 Auto-response email containing phishing link
Auto-response email containing phishing link
While new phishing scams are emerging, the Cyber Threat Experts (CTE) Team at Vade says organizations should also remain cautious of time-tested scams. “Tax-themed phishing campaigns, payment scams, and delivery schemes are still effective, relevant, and common. Attackers will continue to deploy them, while improving the content and techniques of their attacks. They test email security tools and email filtering components daily to find weaknesses and bypass them to deliver their campaigns.”
The CTE Team points to a recent phishing scam that impersonated the partnership between Capital One and Authentify, an online verification service. The campaign started with a phishing email that directed victims to a compromised WordPress website, where they were prompted to upload pictures of the back and front of their state-issued IDs.
 Capital One/Authentify phishing email
Capital One/Authentify phishing email
2. Supply-chain and hijacking techniques will increase
Organizations are investing more in phishing awareness training to strengthen the human element of their cyber defenses, which is their greatest vulnerability to a cyberattack. While improved user awareness is welcome news, Michael Posey, Pre-Sales Engineer at Vade, believes it will force attackers to evolve their methods.
“As users become more proficient at spotting and reporting common phishing scams from well-known brands, we will see hackers adjust their strategy, including impersonating suppliers or customers. I expect more supply-chain attacks and hijacking,” he says.
Supply-chain attacks refer to cyberthreats that infiltrate an organization’s systems by impersonating or compromising vendors with access to those systems. Hijacking, on the other hand, refers to attacks in which hackers use compromised accounts to join existing email communications or create new ones. Once hackers enter those conversations, they deploy phishing or spear-phishing attacks.
Still, Posey believes phishing campaigns impersonating established brands like Facebook and Microsoft will continue. Vade’s Phishers’ Favorites H1 2022 Report, which reveals the top brands impersonated by hackers, supports his prediction. Microsoft emerged as the most impersonated brand in H1 2022, accounting for a total of 11,041 unique phishing URLs. Facebook took the second spot with 10,448 unique phishing links, while Crédit Agricole, WhatsApp, and Orange rounded out the top five on the list.
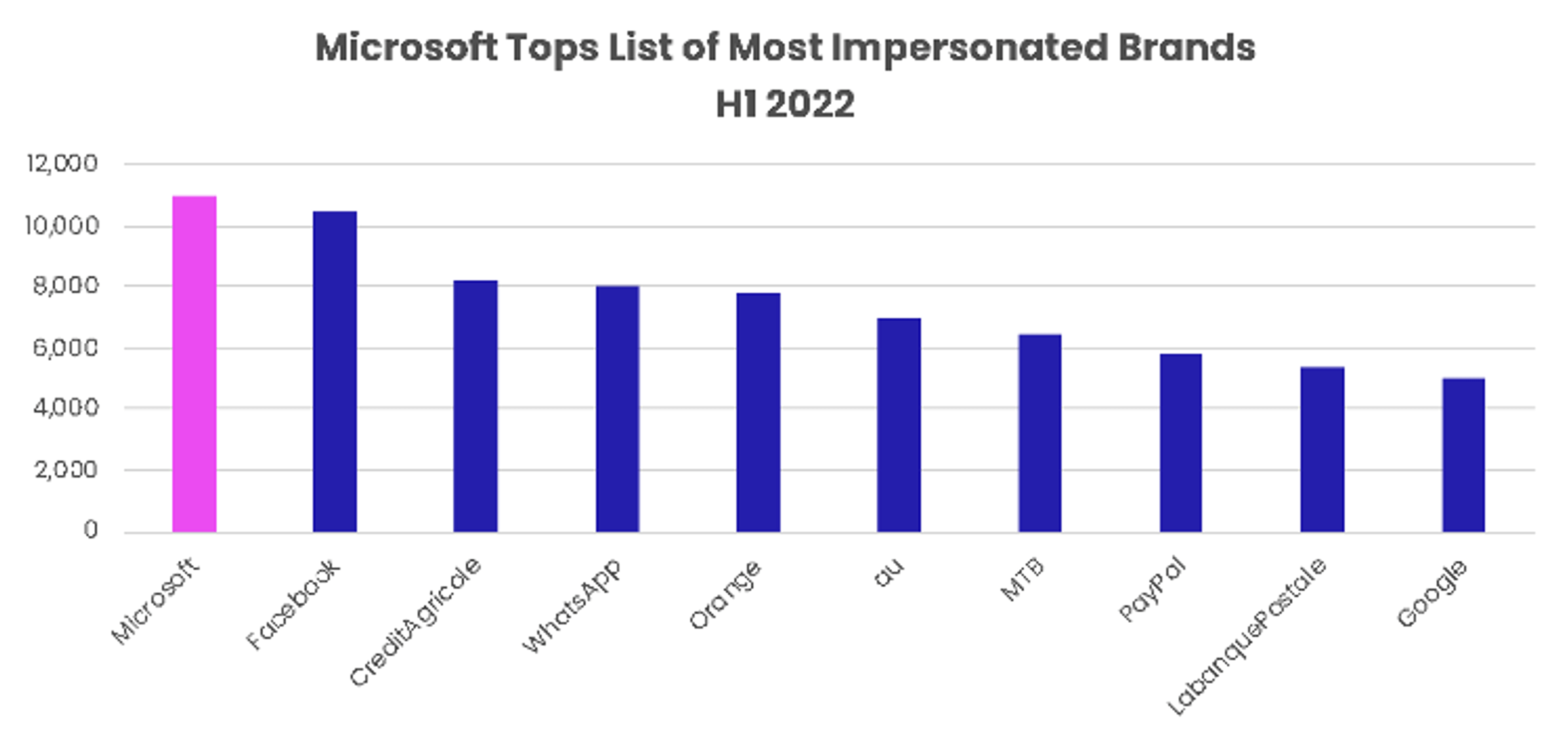
Top 10 impersonated brands in phishing in H1 2022, based on unique phishing URLs
While phishing emails have long been used to victimize users indiscriminately, more recent campaigns reveal a more focused approach. In July, Vade detected a sophisticated Instagram phishing scheme that showed hackers researched their victims before carrying out highly targeted attacks.
3. Ransomware attacks will continue their devastation
As ransomware attacks have regularly made headlines in 2022, the CTE Team predicts this devastating type of cyberthreat to continue to wreak havoc on organizations without adequate email security solutions. “Like last year, we expect ransomware attacks to get more sophisticated in terms of evading detection, adapting, and exploiting new vulnerabilities to spread. Ransomware groups like BlackCat are fine-tuning their methods.”
The CTE team sees two factors maintaining the volume of ransomware attacks: Ransomware-as-a-Service (RaaS) and double extortion. “RaaS is a key source of revenue for cybercriminals. Hackers will remain active as long as that’s the case. It also allows hackers who are less skilled to get their hands on sophisticated ransomware and turn a profit.”
“Double extortion gives hackers additional leverage over their victims,” the CTE Team says. “Data exfiltration and the threat of leaking sensitive data gives organizations more reason to comply with hackers’ demands to avoid regulatory, legal, or reputational consequences. We’ve seen this from ransomware gangs like Hive, particularly in the healthcare sector.”
Consistent with other types of cyberthreats, the CTE Team believes hackers will continue to focus their ransomware attacks on smaller organizations. “Already, we’re seeing attackers target small-to-midsized businesses (SMBs) and managed service providers (MSPs) rather than larger enterprises. SMBs and MSPs lack the same email security and cybersecurity resources and budgets, making it easier for hackers to exploit them.”
According to the CTE Team, hackers appear to be favoring the ease and efficiency of targeting smaller businesses over the larger payouts they may earn by attacking big enterprises.
4. Productivity suite security will supplant email security in 2023
Email is deeply integrated with an organization’s various internal systems, processes, departments, and more. Adrien Gendre, Chief Technology and Product Officer, and cofounder at Vade, believes email security will need to account for this reality by extending protection beyond users’ inboxes and outboxes. “As attacks grow in number and sophistication, SMBs and MSPs will need technology that tightly integrates with modern productivity suites such as Microsoft 365 or Google Workspace and provides comprehensive threat intelligence,” he says.
Unlike secure email gateways (SEGs) that separate email security from internal networks, API-based alternatives are the future of email security, Gendre says. “Organizations need to be able to leverage the threat intelligence from email to protect file sharing applications and other collaborative tools like instant messaging. They also need to be able to leverage information such as user profiles, contacts, and communication patterns to defend against highly targeted attacks, such as those we’re seeing with supply-chain attacks.”
According to the CTE Team, email gives hackers a clear advantage over their victims by disguising cybercriminals’ activities. “Hackers benefit from the sheer volume of emails sent every day, requiring organizations to triage vast amounts of data to detect threats. Coupled with demands to keep their systems free from vulnerabilities and provide around-the-clock protection, organizations struggle to keep pace with hackers.”
Technology will provide organizations a way to overcome this disadvantage. “Organizations will need solutions that can detect low volume threats affecting users or customers and be able to quickly remediate them from one interface. SMBs and MSPs don’t have the bandwidth to manage 15 different products from 15 different consoles all in parallel,” says Gendre.
Strengthening email security for 2023 and beyond
This year saw cybercriminals launch more targeted and creative attacks against their victims. With organizations investing more in cybersecurity and user awareness, we can expect hackers to further enhance their methods, whether through MFA exploitation, hijacking, supply-chain attacks, double extortion, or other malicious activities. No matter their approach, email will remain the top vector for cyberthreats. “The majority of attacks will continue to start with email, since it’s the most efficient and direct path to organization’s greatest IT vulnerability, and that is end users,” says the CTE Team.
To keep pace with hackers, organizations need AI-based threat detection and response technology to defend against known, emerging, and never-before-seen email-borne threats. Importantly, organizations should look for solutions that live within their internal environments and provide protection against threats originating from compromised accounts or flowing freely through their productivity suites. They should also seek technology that equips them with real-time threat intelligence they can operationalize easily and efficiently.




