4 best email security tools you need in your stack
Adrien Gendre
—October 20, 2022
—6 min read

In the survey for our SMB Cybersecurity Landscape Report, we discovered that 69% of small-to-midsized businesses (SMBs) experienced a serious data breach that bypassed their email security tools. This alarming total confirms an unfortunate reality about one of the most popular and important methods of digital communication in the modern age. Email remains the top vector for cyberthreats, offering hackers the path of least resistance to exploiting vulnerabilities and infiltrating networks. In this article, we'll explore the 4 best email security tools you need to have in your stack.
For SMBs, email-borne threats can cause significant harm. Yet for the managed service providers (MSPs) responsible—or perceived as responsible—for their clients’ cybersecurity, the consequences can be far greater. A single attack can result in financial losses, reputational damage, and legal ramifications.
As hackers continue to fine-tune their techniques and technologies to bypass traditional defenses, MSPs must look beyond legacy technology to solutions purpose-built for the most advanced threats. In this blog, we review the four email security tools you need as an MSP to keep you and your clients protected.
Best Email Security Tools: AI-Based Threat Detection
In the past, email threat detection was a reactive practice: Defending against email-borne threats first required someone to become a victim. Intelligence was then gathered and used to fortify the defenses of traditional threat detection tools like secure email gateways (SEGs), which use reputation- and signature-based scanners. But that gave the advantage to hackers, who could evade detection by making small adjustments to existing threats, such as obfuscating a known phishing link to pass through filters. The result left organizations always one step behind.
Read how hackers use email fingerprint obfuscation to break through defenses.

Advancements in Artificial Intelligence (AI) have neutralized the advantage once afforded to cybercriminals. While hackers continue to introduce more sophisticated threats, AI-based threat detection tools enable predictive defense against all cyberthreats, including those not yet seen in the wild, and stand for the best email security tools to have in your organization.
Still, not all threat detections tools claiming to use “AI” provide equal protection. That’s why you should look for solutions that leverage the following technologies.
1. Machine Learning
A subset of AI, Machine Learning (ML) takes a behavioral approach to email filtering. Rather than base detection on blacklisted IP addresses or known malware signatures, it looks for anomalies and suspicious behaviors in emails, URLs, and attachments. ML algorithms train on massive datasets of malicious and benign emails, allowing them to recognize features consistent with all cyberthreats and making them the best email security tools. For example, Vade’s anti-phishing solution uses ML algorithms to evaluate 47 features of emails and URLs.
2. Computer Vision
Another field of AI, Computer Vision focuses on images and performs an analysis to detect anomalies and suspicious behaviors, such as detecting logos in phishing attacks. Computer Vision can detect common evasion techniques that outsmart traditional filters, such as image manipulation concealing signatures, QR codes hiding phishing URLs, and more.
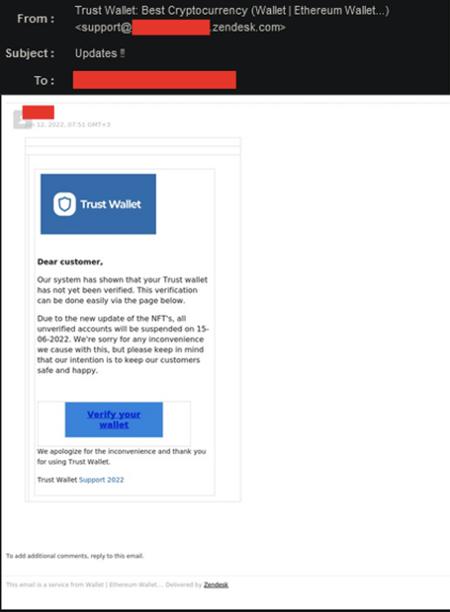
Example of phishing email with image manipulation
3. Natural Language Processing
Natural Language Processing (NLP), another subfield of AI, analyzes text to detect subtle grammatical and stylistic choices that could indicate a threat. NLP models provide necessary protection against spear phishing emails, which don’t contain malicious links or attachments but use text-based social engineering to coerce victims into action. This includes creating a sense of urgency or fear.
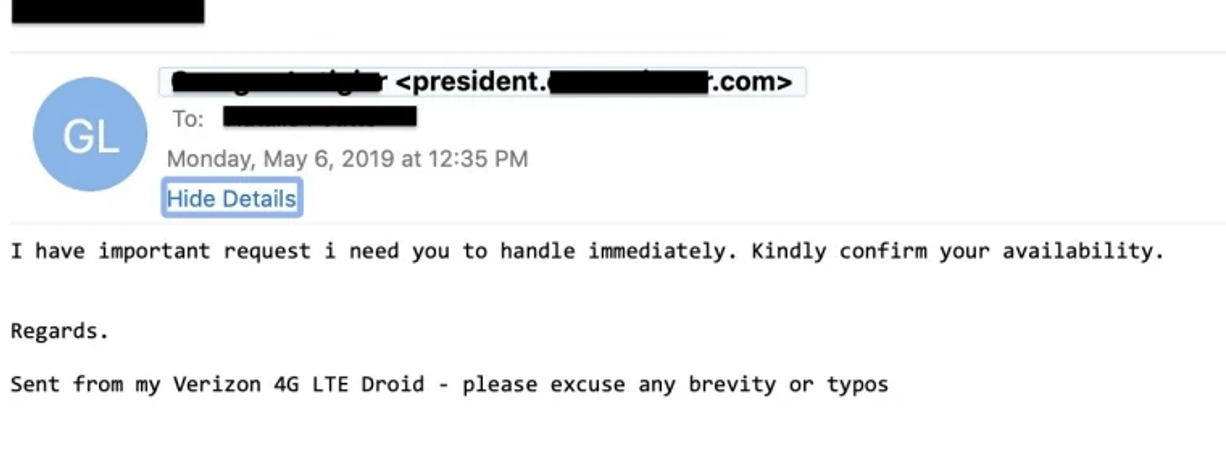 Example of spear-phishing email
Example of spear-phishing email
4. Continuous feedback
AI-based threat detection requires data—and lots of it. This information is key to enabling AI models to train themselves in detecting the threats that evade traditional defenses and offer the best email security tools. But the quality of data is also important. AI tools need to continually learn from data that are current and taken from a geographically representative sample.
For example, Vade’s AI-threat detection engine uses real-time intelligence—both automated and user-reported—gathered from 1.4 billion mailboxes globally. This enables threat detection to safeguard against cybercriminals’ latest threats and tactics, while minimizing the potential for false positives (legitimate emails get filtered) or false negatives (cyberthreats bypass filters).
Best Email Security Tools: Unified Threat Management and Response Engine
Even with the advancements in AI, perfect detection is not a realistic aim when it comes to email security tools. Some cyberthreats will eventually bypass initial defenses, which is why you need a solution to quickly remediate them when they do. A threat management and response solution provides another layer of email security, enabling you to rapidly identify and neutralize cyberthreats post-delivery.
Like AI-threat detection, not all threat management and response tools provide equal protection. The best email security tools will possess these two essential features.
1. Post-delivery scanning and automatic remediation
In the Q2 2022 Phishing and Malware Report, Vade detected a combined 440 million phishing and malware emails worldwide, a figure on pace to surpass 2021 totals.When new threats emerge and the potential for exploitation increases, you need protection to last beyond the moment a threat reaches a users’ inbox.
Threat management and response technology that features post-delivery scanning and automatic remediation continue the function of AI-threat detection within your internal network. They continually perform a behavioral analysis of delivered emails and automatically remove threats without manual intervention.
Like threat detection, these solutions rely on the same core set of AI technologies explored earlier and continuous intelligence from a large set of current and relevant data. Threat management and response solutions that fit this description decrease your risk of getting exploited, improve internal security, and free up scarce IT resources.
2. All-in-one dashboard for manual remediation
When it comes to threat management and response, time is one of the most important variables. A delay can mean the difference between neutralizing a threat and having it compromise one of your users.
Your threat management and response solution should enable you to track and manage your email security from one place. This solves the slow and challenging task of chasing down a cyberthreat using multiple screens or disparate tools, or manually neutralizing threats one-by-one. For instance, Vade’s MSP Incident Response tool gives you the ability to track and remediate a suspicious email across your clients using one interface and click.
Email-based threat intelligence and investigation engine
If you use Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), or Extended Detection and Response (XDR) technology, then email-based threat intelligence and investigation solutions are an essential and best email security tool.
These solutions enable you to ease the burden of managing multiple cybersecurity tools to monitor and analyze security data from an array of endpoints. You can export email logs, gather forensic evidence, cross-check threats across networks, and develop incident response processes. You can also unify disparate email security data, improve threat visibility, increase productivity, and more.
Like the other email security tools explored in this article, not all solutions provide equal value. Look for email threat intelligence and investigation solutions that offer these three features.
1. Log export
The solution should keep a record of intelligence about all email-borne threats targeting your business and provide the ability to export it in a format compatible with your SIEM, EDR, or XDR.
2. File inspector
The tool should gather intelligence on files and email attachments, including malicious characteristics and elements, including hash, URLs, objects, decoded data, and JavaScript.
3. Email and attachments downloader
Your threat intelligence and investigation tool should allow you to download suspicious emails and attachments from email logs to inspect the content. This provides you with visual evidence, which you can repurpose for user awareness training.
Best Email Security Tools: User Awareness Training
Verizon’s 2022 Data Breach Investigations report found that 82% of data breaches involved a human element. It’s not a surprise hackers view users as the most vulnerable and attractive target across your attack surface.
Yet with the right user awareness training, you can transform users from your greatest cybersecurity weakness into your biggest strength. One of the best email security practices: equipping users with phishing awareness training to spot and respond to cyberthreats, you assemble a formidable last line of defense.

To find effective user awareness, look for programs with these three features.
1. Personalized
Simulated training programs expose learners to hypothetical cyberthreats that rarely match what they encounter in real-life—including the when, who, and what of their email interactions. This characterizes standardized training, in which education remains the same no matter the learner or situation.
Personalized education champions the opposite model. Training reflects the student’s needs and context, giving them the highest chance of successfully applying their learning to achieve a desired outcome.
For user awareness training, the program should teach users how to recognize and respond to email-borne threats using examples they regularly encounter on their own. For example, Vade’s Threat Coach™ delivers on-the-fly user awareness training that mimics the content and context of users’ email interactions.
2. Timely
Cyberthreats happen without notice, and so should training. That means education shouldn’t occur at a predetermined time, but when users need it most: When they encounter a cyberthreat. This kind of training increases retention and improves application, reducing the likelihood a user becomes a cyber victim.
3. Relevant
Cyberthreats are constantly evolving. As cybersecurity vendors develop more sophisticated solutions, hackers respond with enhanced evasion techniques. This ever-evolving dynamic will continue for the foreseeable future, and user awareness training should account for it. That means training should expose learners to the latest cyberthreats based on real-time intelligence of malicious emails across the globe.
Best email security tools: The need for an integrated solution
These four best email security tools can help you protect your clients from today’s most sophisticated email-borne threats. Yet they also provide the added value of helping you to develop and grow a managed security service offering without needing to add to your headcount or divert crucial time and resources away from other areas of your business.
Still, cybersecurity is already overwhelmed with an abundance of standalone technologies. That’s why you should seek solutions that combine all four email security tools into one low-touch solution like Vade for M365.
Learn more about how you can set up the best email security solution in your organization and protect your users: request a demo of Vade.




