Q3 2022 Phishing and Malware Report: Phishing Volumes Increase 31%
Todd Stansfield
—October 27, 2022
—4 min read

In the fast-moving world of cybercrime, staying abreast of the latest trends is necessary to maintain good cybersecurity posture. To help you keep pace, we present our Q3 2022 Phishing and Malware Report, which gives you insight into the new activity and techniques of hackers as they try to exploit organizations like yours.
This quarter’s report reveals several key takeaways and broad themes. Overall, phishing volumes saw a more than 31% increase QoQ, after finishing Q2 with one of the most active months in 2022. Meanwhile, malware volumes tapered off from the blistering totals set in H1 2022, but they still more than doubled the levels reached in Q3 2021. Let’s unpack the findings of the latest report.
Phishing and malware trends: phishers were more prolific in Q3
Phishers made a strong showing in Q3, sending 203.9 million emails compared to 155.3 million the previous quarter. Phishing volumes fluctuated throughout the quarter, peaking in July (79.2 million), dipping in August (57.5 million), and rebounding in September (67.2 million). Excluding June (77.6 million), Q3 phishing volumes outperformed Q2 totals for every month. If Q3’s pace continues through Q4, phishing volumes in H2 are set to exceed those reached in the first half of the year (315 million).
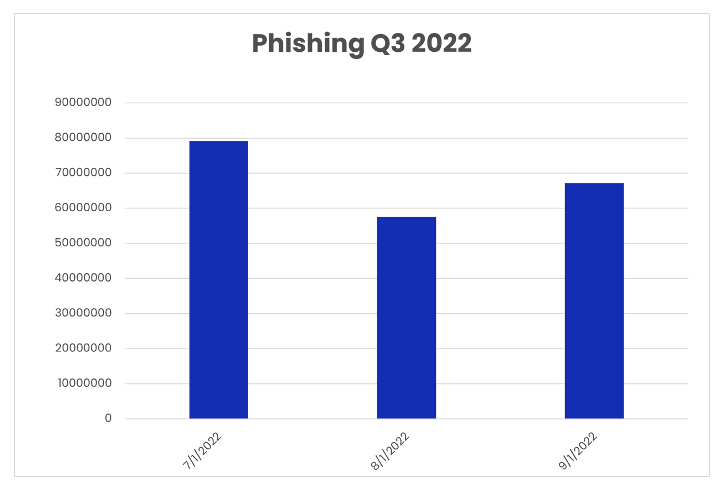
Phishing volumes, Q3 2022
Phishing and malware trends: malware is still a menace
Through the first three quarters of the year, 2022 malware volumes (177.5 million) surpassed levels seen in 2021 (121.7 million). Malware emails in Q3 2022 (52.5 million) also accounted for a 217% increase compared to same period the previous year (24.2 million). Still, malware totals (52.5 million) show a modest decline from Q1 (56.5 million) and Q2 (68.6 million). Malware volumes reached their peak in July (19.2 million), before month-over-month declines in August (16.8 million) and September (16.5 million).
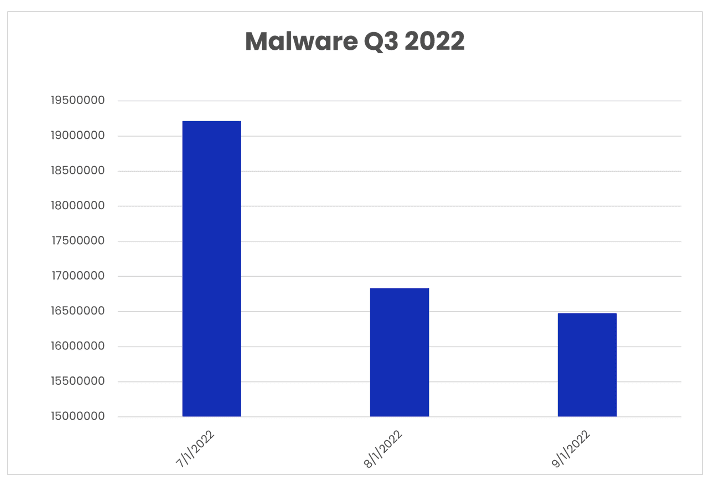
Malware volumes, Q3 2022
Phishing and malware trends: Phishers are still impersonating well-known brands
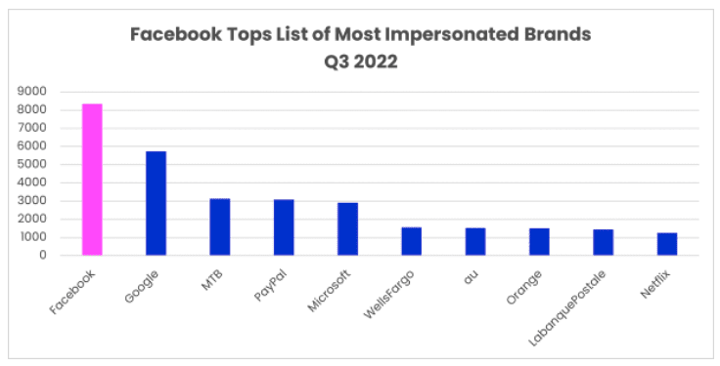
While their activity fluctuates from quarter-to-quarter, hackers appear committed to using one of their most reliable strategies: impersonating trusted and established brands. Vade detected numerous phishing schemes exploiting some of today’s most established companies. Q3’s phishing results saw Facebook emerge as the top impersonated brand for the second consecutive quarter, followed by Google, MTB, PayPal, and Microsoft to round out the top five.
The financial service sector once again took the top spot as the most impersonated industry, representing 32% of phishing emails detected by Vade, followed by cloud (25%), social media (22%), and internet/telco (13%).
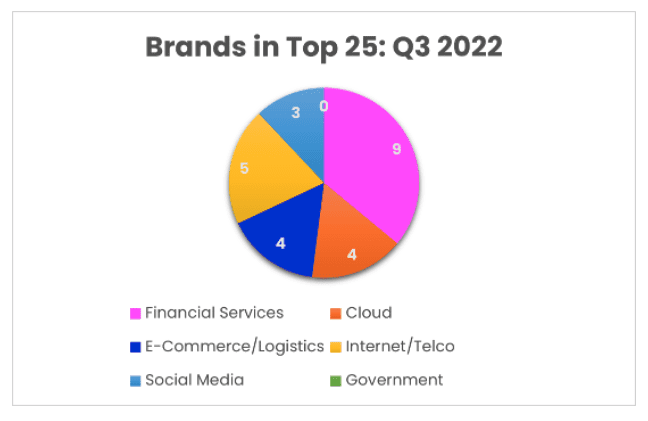
Financial services also accounted for the most impersonated brands with nine among the top 25. Internet/telco came in second place with five, followed cloud and e-commerce/logistics, which each tied at four brands.
Phishing and malware trends: Hackers develop alarming techniques
As hackers evolve the volume and target of their attacks, they also continue to fine-tune their techniques. Here are several new schemes detected by Vade that warrant your attention.
Phishing attacks are becoming more targeted
As phishing increases, hackers appear to be evolving their techniques. While historically phishers focused on launching largescale, indiscriminate attacks, recent campaigns suggest they’ve developed an appetite for more targeted campaigns.
In July, Vade detected a sophisticated phishing scheme that impersonates Instagram and exploits its highly sought-after verification program. The campaign targets victims with emails that display their actual usernames, which create the illusion of legitimacy and show that hackers spend ample time researching their targets before each attack.
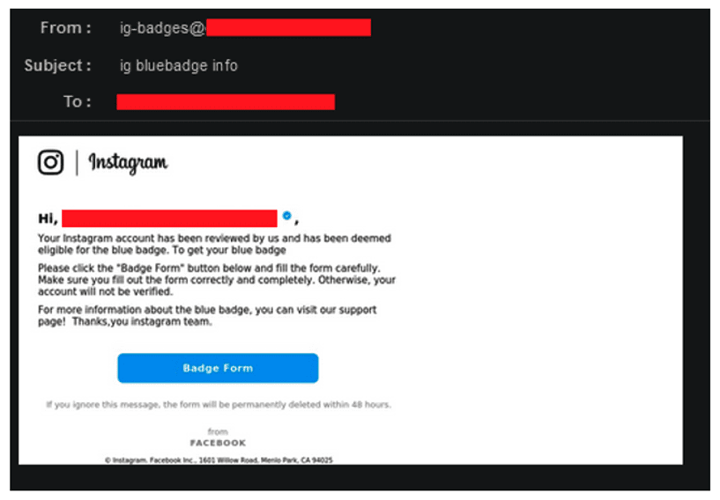
Instagram phishing email
Since the scheme was first detected by Vade in July, the campaign has resulted in a relatively low volume of emails, reaching a peak of 1,000 per day.
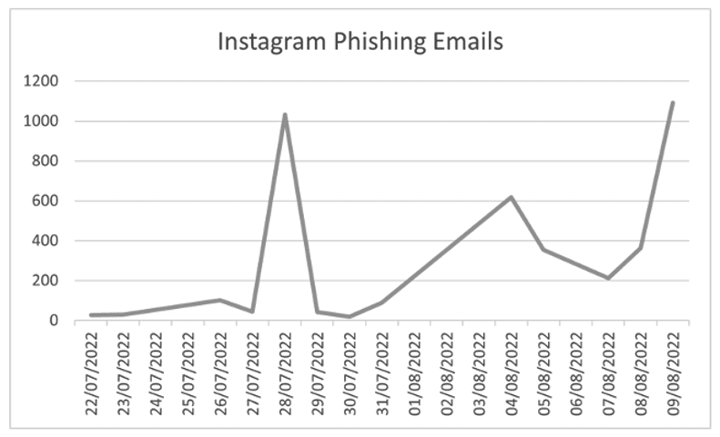
Instagram phishing email volumes
Phishing attacks are weaponizing legitimate services
In one of the most concerning developments in this quarter’s phishing and malware report, hackers began weaponizing a legitimate service to transmit and conceal their phishing attacks. It represents a new attack strategy, one that may become more common in the future.
In September 2022, Vade detected a phishing campaign that exploits a top career website in France. The scheme uses the career platform to distribute phishing links to organizations recruiting candidates to fill job openings.
In the attack, hackers apply to job postings and upload a PDF resume containing malicious links. Once submitted, the platform generates an email containing the malicious PDF, which it auto-sends to the recruiting company for review. The phishing campaign uses the platform's legitimate servers, IP address, and domain name, making it difficult for email filters and victims to detect.
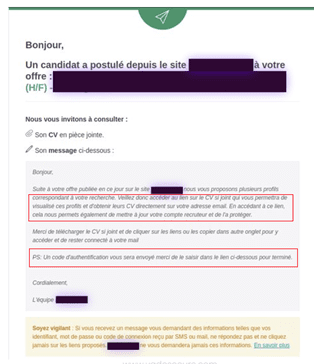
Platform's auto-response email
Once victims open the PDF attachment, they’re prompted to click malicious links that point to a phishing website, where hackers can harvest account credentials.

Malicious PDF attachment
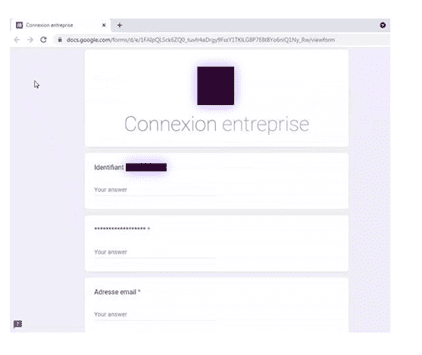
Google Docs phishing form
The consequences of the attack remain significant. If the victim divulges account credentials, it can lead to an account takeover, identity theft, or more. It can also lead to subsequent threats, including spear phishing, phishing, supply-chain attacks, hijacking, and data exfiltration.
The abuse of legitimate services will likely become more common in the future, according to Vade analysts. It saves hackers the time and effort of designing an email that impersonates an organization. It also increases the likelihood of a successful attack by lowering victims’ suspicions of nefarious activity.
Phishers exploit financial partnerships
As shown by the latest phishing results, cybercriminals never seem to miss an opportunity to impersonate a financial institution. When Capital One partnered earlier this year with Authentify, an online verification service used by financial institutions to verify customer identities, it gave hackers an opportunity to plan a new attack.
In July, Vade detected a phishing campaign impersonating Capital One and Authentify. It starts with a phishing email from a corporate email address with the display name, “Capital One.” Likely belonging to a compromised account, the email contains the Capital One logo and a phishing link.

Capital One/Authentify phishing email
Hackers attempt to disguise the link using display text containing the names of Capital One and Authentify. Despite the appearance, the URL is spoofed and points to a compromised WordPress website impersonating Capital One, where users are prompted to upload the front and back of their state-issued ID.
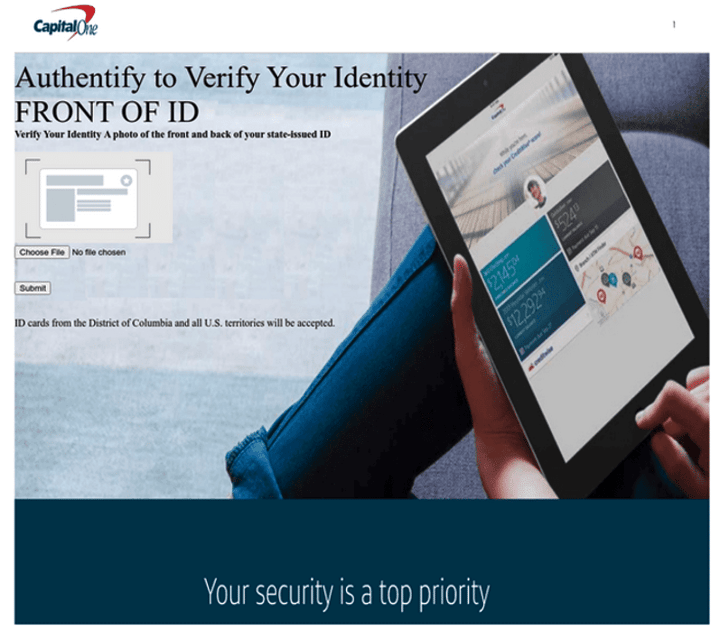
Capital One phishing page 1
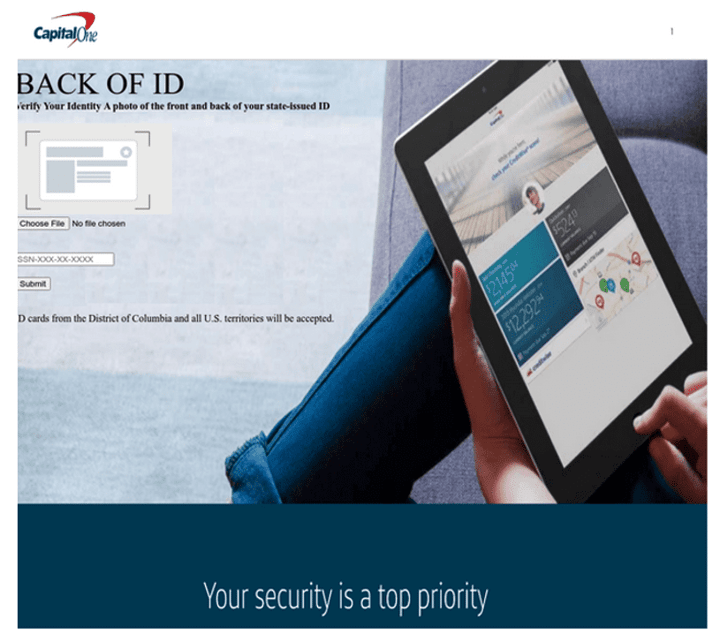
Capital One phishing page 2
The scam began on July 1 with volumes reaching up to 6,000 emails in one day.
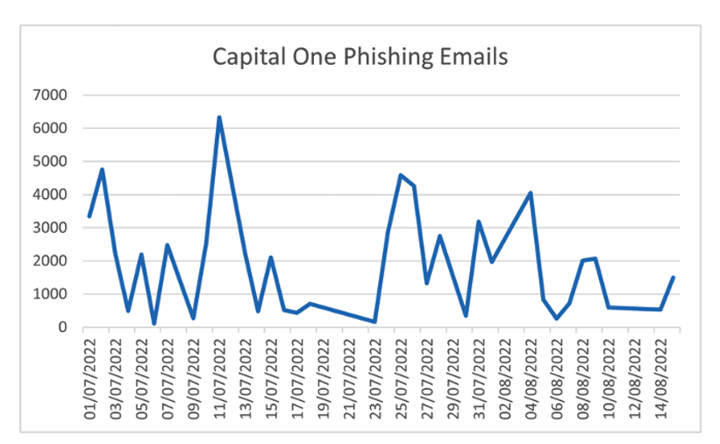
Capital One phishing email volumes
Email remains the top vector for phishing and malware attacks
Email is the preferred attack vector for phishing and malware, giving hackers a direct channel to the weakest link in an organization’s attack surface: users. Today, nearly eight in 10 businesses rely on the basic email security offered by their email provider (e.g., Microsoft 365, Google Workspace). These solutions are no match for today’s dynamic and sophisticated email-borne threats, which are capable of evading detection by traditional defenses like reputation- and signature-based filters. This makes email an effective vehicle for hackers to carry out ambitious attacks.
Still, organization can transform email from a weakness in their attack surface to a strength. Unlike traditional email security solutions, AI-threat detection and response technology enables organizations to protect against all email-borne threats—including the most sophisticated phishing and malware—while saving time and people resources to focus on running their business.




