Recent Supply-Chain Attack Uses Spear Phishing and Near-Domain Spoofing
Vade Experts
—January 03, 2024
—3 min read

Vade recently detected a supply-chain attack impersonating a large retail company in Europe. The spear-phishing scam uses a combination of clever social engineering techniques and near-domain spoofing to deceive the intended target.
In this post, we examine the supply-chain attack and present the findings of Vade’s security analysts.
Supply-chain attack analysis
Vade recently discovered a supply-chain attack that featured a well-executed social engineering strategy and leveraged compromised credentials. The scheme impersonated a large and well-established retailer in the EU. The attack begins with an email from the spoofed sender requesting payment of an outstanding balance. The subject line includes the phrase, “overdue payment” along with the name of the impersonated vendor. In the body of the email, the hackers indicate that they have received two invoice payments from the targeted organization, but an outstanding balance remains.
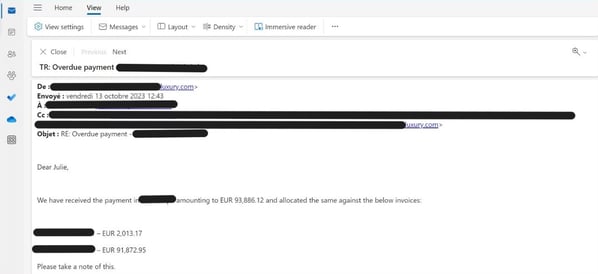
Spear-phishing email used in supply-chain attack
Notably, the spoofed sender’s address is fake and uses close-cousin domain spoofing to create the appearance that email is originating from the legitimate supplier. The real supplier’s domain includes the word, “luxury” with a lower-case “L.” Hackers impersonate the domain using a near replica that replaces the “L” with an upper-case “i.” This subtle difference is nearly indistinguishable to the human eye and only becomes apparent when verified through alternative means.
According to Vade analysts, the email is likely a copy of a legitimate email chain that hackers obtained via a compromised account. The two invoices that the hackers referenced are also likely legitimate, adding credibility to their claim.
Compromised accounts provide hackers with a treasure trove of information to weaponize against their adversaries. Often, attackers reuse previous email correspondence along with social engineering techniques to manipulate victims. These communications are typically financial in nature and establish the appropriate context for soliciting payments.
In the attack, hackers also spoofed the signature of the sender, including their organization’s standard confidentiality and security disclaimers. This attention to detail further creates the appearance of legitimacy in the eyes of the intended victim.
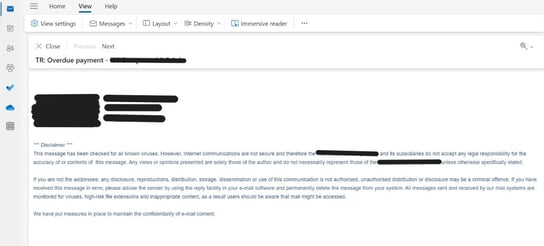
Spoofed email signature
Looking up the legitimate domain information on Whois.com, we see that it was registered several years ago and updated in the past year. We also see that the domain won’t expire for a considerable period. These details offer evidence of a legitimate and established site.
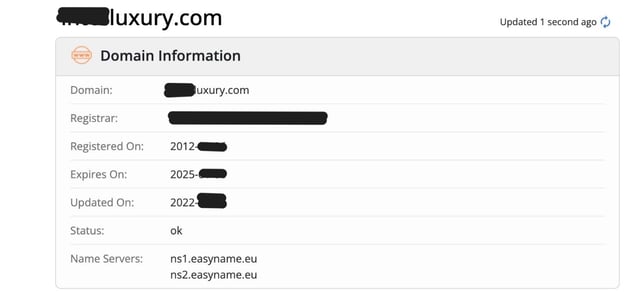
Legitimate domain information on Whois.com
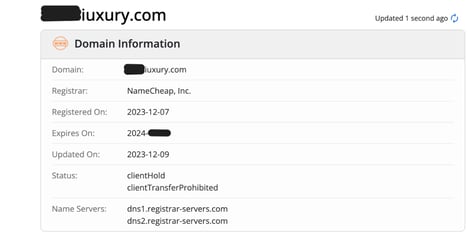
Spoofed domain information on Whois.com
Meanwhile, the same analysis renders different results for the spoofed domain. Here, we see that the close cousin domain was recently registered with a cheap domain service and expires relatively soon. We also find two concerning statuses assigned to the domain, clientHold and clientTransferProhibited. They indicate the DNS records were never activated or have been suspended, possibly for legal reasons. Together, these domain features characterize a site created for nefarious purposes.
Unfortunately, the attack was successful. The spoofed email reached the Director of Finance at the targeted organization, who sent payment for the overdue balance.
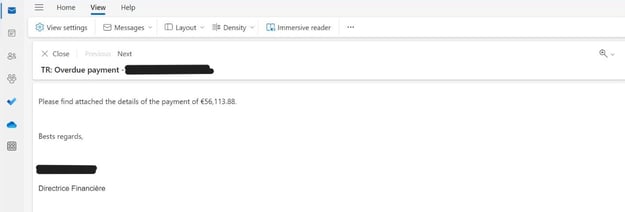
Payment confirmation email from legitimate sender
The menace of supply-chain attacks
This supply-chain attack, while unique in terms of the targeted victims, represents a common and effective supply-chain attack.
Supply-chain scams frequently begin with hackers compromising the legitimate account of an employee in finance, accounting, accounts payable, or another department. Hackers then search their email correspondence, looking for existing conversations about invoices and past due payments.
Once they gather this information, attackers then register a domain similar to the one belonging to the legitimate vendor. After creating new email addresses, hackers then target the vendor’s clients, asking for invoice payments that reuse the real, extracted conversations.
Protect your business against supply-chain attacks
Protecting against this attack requires a combination of measures. Implementing and enforcing password policies, adopting multifactor authentication (MFA), and promoting good cyber hygiene practices can all help limit the risks an account is compromised or subsequently abused.
User awareness training that emphasizes the need for out-of-band communication is also key. This encourages employees to use alternative methods of communication to verify the authenticity of requests.
You should also consider adopting an integrated email security solution. To get optimal protection, look for solutions that provide advanced spoofing and anomaly detection to identify the unauthorized use of legitimate domain names and cousin domains.
Also, favor solutions that leverage Natural Language Processing (NLP), an AI model that detects text-based threats. NLP algorithms can detect and filter threats based on their words and phrasing, including those used to facilitate financial fraud.