Account Takeover Prevention: How to Protect Your Organization
Adrien Gendre
—September 29, 2022
—5 min read

As a managed service provider (MSP), protecting your clients’ cybersecurity is the top priority. With cyber threats growing more sophisticated and your attack surface broadening, knowing where to spend your time and resources can prove challenging. Account takeover prevention is an essential focus that every MSP and organization should concentrate on. Without it, you put yourself and your customers at risk of financial losses, liability concerns, reputational damage, customer churn, and more.
Account takeover prevention is a collection of measures that together defend against one of the most costly and devastating forms of cyber threats: an account takeover (ATO). ATO begins by compromising an individual’s account and using their online identity to carry out more malicious attacks. On an individual level, hackers can steal personally identifiable information (PII), extract funds from financial accounts, or use online identities to launch malicious attacks.
On an organizational scale, cybercriminals can launch phishing attacks, spread malware, exfiltrate data, and more—not only against you, but your clients and business partners. In 2021, ATO attacks cost consumers and businesses $11.4 billion (USD), with attacks increasing by 90 percent from 2020. Account takeover prevention thwarts the worst intentions of threat actors, enabling you to concentrate on growing your business.
In this blog, we examine the menace of ATO attacks, how they occur, and measures for account takeover prevention to safeguard your organization and customers.
The menace of account takeover
ATO is an effective and efficient vehicle for scaling malicious attacks. When hackers take over one account, they find an easier path to gain control of others. That’s why hackers rarely see their initial victim as the prime target. More often, they set their sights on organizations and their valuable network of business relationships.
A recent high-profile attack sheds light on the nefarious motivations of ATO actors. In August 2022, cybercriminals targeted customers of Okta, an identity service provider, by sending employees text messages that contained malicious links (a practice known as smishing). The links directed traffic to phishing pages impersonating Okta authentication portals, where hackers harvested credentials including multi-factor authentication (MFA) codes.
This information enabled threat actors to take over accounts, access sensitive data, spy on corporate email, harvest funds, and launch supply chain attacks against other organizations. Altogether, the well-orchestrated and international scheme targeted 136 organizations and compromised nearly 10,000 accounts.
Cases like the attack on Okta customers follow a proven formula often employed by threat actors. Cybercriminals use ATO to launch a more aggressive and malicious attack that commonly takes one of the following forms.
Internal phishing
Cybercriminals use a hacked email account to launch a phishing campaign. They send out malicious messages from an authentic email address, which goes undetected by most email security tools. Unsuspecting victims receive what appears to be a legitimate email and don’t think twice before clicking a malicious link or downloading an attachment containing malware.
Supply-chain phishing
Hackers exploit a compromised corporate email to attack customers and business partners, exposing the infected organization to potential liability and reputational damage. MSPs are more attractive targets for supply-chain phishing because of their access to and control over multiple small-to-midsized (SMB) IT environments.
Spear phishing (business email compromise)
Hackers also commonly use ATO to launch spear-phishing attacks. Spear phishing is a highly personal and targeted threat designed to elicit action from victims. Hackers typically send a concise email containing only text that impersonates supervisors, colleagues, business partners, or other acquaintances. Spear-phishing scams include CEO fraud (wire fraud), gift card requests, and tax fraud.
Subsequent ATO
Hackers also use ATO to gain access to other accounts. They may belong to the initial victim or another target, such as a company executive. In this way, ATO enables lateral movement within a network.
ATO techniques
As we examined, a successful ATO attack opens the door of opportunity for hackers. But first, they rely on several proven techniques to compromise the initial account.
1. Brute force attacks. Hackers use automated scripts to guess account credentials and force unauthorized entry. The scripts cycle through password combinations in a trial-by-error approach.
2. Credential stuffing. Hackers use a list of compromised credentials to gain access to non-compromised accounts using bots. This technique preys on the tendency of people to reuse passwords for multiple accounts. Data breaches and leaked personal data give hackers all they need to launch this kind of attack and exploit people who don’t vary their passwords.
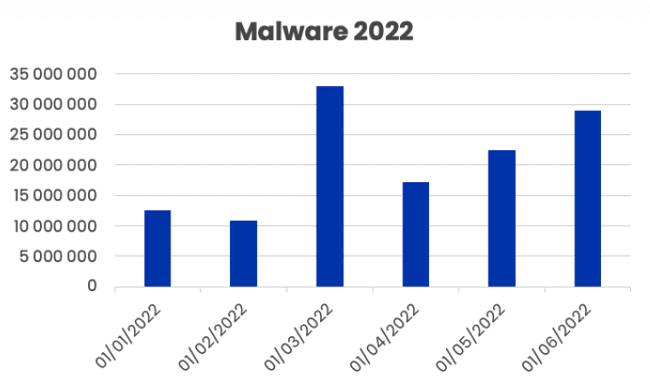
3. Malware. Hackers use malware to gain unauthorized access to other accounts. This includes using spyware like keylogger malware, which records every keystroke made by a victim. Malware attacks continue to rise in popularity among hackers, especially those distributed over email. Vade’s Q2 2022 Phishing and Malware Report shows malware email volumes increased by 21% in Q2, with 28.9 million malware-laced emails detected in June alone.
Global malware email volumes, H1 2022
- 4. Phishing. Hackers use phishing emails to infect computers with malware or harvest credentials. This can take the form of regular phishing, which impersonates brands, internal phishing, or supply-chain phishing, as examined previously. Phishing remains one of the most popular cyberthreats among hackers. Vade detected nearly 316 million phishing emails in H1 2022.
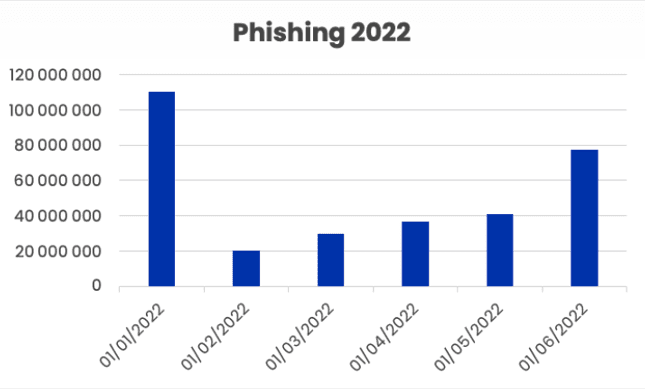
Global phishing email volumes, H1 2022
Account takeover prevention: 5 solutions to beef up your cybersecurity
To explain why hackers are choosing ATO as their weapon of choice, we need only look at changes to the digital landscape. MSPs and other organizations must protect a broader attack surface than ever before. The growth of digital communication, endpoints, and remote work gives hackers more opportunities to infiltrate networks and impersonate victims for more nefarious purposes. That’s why now, more than ever, organizations need to step up their cyber vigilance and invest in a holistic strategy for combating ATO, including these foundational attack takeover prevention measures.
1. Multi-factor Authentication (MFA)
MFA requires users to authenticate their identity using two or more electronic methods, such as sending verification codes to email and text message. MFA provides an additional layer of protection in the event one account is compromised, limiting the ability to takeover multiple accounts owned by the same user. Still, MFA doesn’t guarantee protection. Hackers can still use sophisticated techniques like SIM swapping to intercept verification codes sent by text. Or they can carry out a sophisticated attack like the Okta example explored previously.
2. Password policies and enforcement
Password policy enforcement solutions counteract users’ tendencies to create weak passwords or reuse credentials for multiple accounts. Administrators can set and enforce policies for password length and character requirements. They can also determine the amount of time before users must create new passwords. This limits the efficacy of brute force attacks and credential stuffing.
3. Zero Trust security
A strategic approach to cybersecurity, Zero Trust eliminates the tendency to implicitly trust everything inside an organization’s network. This framework requires all users to be continuously authenticated, authorized, and validated for each digital interaction in a network. Zero Trust relies on authentication tools like MFA, network segmentation, access controls, and other measures to enhance security.
4. User awareness training
Even the best cybersecurity tools can’t prevent users from encountering cyberthreats. That’s why cyber awareness is the last line of defense against cyberthreats. Awareness training can teach users to spot, avoid, or report suspicious threats like a phishing email. The most effective user awareness training is continuously delivered to users when they need it and offers personalized and automated instruction.
5. Email security
Email remains the top attack vector for ATO attacks. With the right email security solution, MSPs and other organizations can effectively detect and respond to the common cyberthreats like phishing campaigns, spear phishing, and email-distributed malware that occur before and after ATO attacks.
For optimal protection, organizations should look for solutions that provide AI-based threat detection and response. Leveraging AI technology, these solutions run a behavioral analysis of emails, links, and attachments to detect anomalies, including those not yet known to reputation- and signature-based scanners.
Vade for M365 combines Natural Language Processing, Machine Learning, and Computer Vision algorithms to detect image- and text-based anomalies used in phishing, malware, and spear-phishing attacks. The solution also continually scans emails post-delivery and remediates threats based on intelligence gathered from 1.4 billion mailboxes globally.
Account takeover prevention starts with good offense
The best defense against an ATO attack is a strong offense. Rather than spending considerable time and money repairing the damage from an ATO attack, invest in a proactive strategy to frustrate hackers and prevent them from getting a foothold in your or your clients’ network.