BEC Scam: How to Avoid Becoming a Victim
Adrien Gendre
—December 15, 2022
—6 min read

Imagine your employee receives an email from you instructing them to pay an outstanding vendor invoice. You’re traveling and don’t have time to go through the proper channels, but the employee is reliable, and the situation is urgent. Listed in your email are instructions to wire the funds and an account number.
The employee, recognizing the urgency of the situation, carries out your request expeditiously. Only there’s a problem: you never sent the email. A hacker spoofed your email address and tricked the employee into transferring funds to a fraudulent account. You’re a victim of business email compromise (BEC). A BEC scam like this one isn’t an imaginary threat, but a very real problem that exploits businesses like yours across the world.
According to a study by IBM and Ponemon Institute, BEC scams cost businesses on average $4.89 million (USD) globally in 2021, making it the second most expensive type of cyberattack. BEC attacks, also known as spear phishing, accounted for 6% of all data breaches during that period.
While BEC scams affect organizations of all types and sizes, small-to-midsized businesses (SMBs) and managed service providers (MSPs) are especially vulnerable. SMBs and MSPs lack the cybersecurity resources and teams of larger enterprises, making them a preferred target for hackers seeking a monetary reward. Nearly eight out of 10 SMBs rely on the basic email security offered by their email provider. This helps explain why, in the past 12 months, 69% of SMBs experienced a serious data breach that bypassed their email security.
In this article, we examine the threat of a BEC scam, the common techniques used by hackers, and the solutions needed to keep your organization safe from exploitation.
The threat of a BEC scam
Unlike a phishing or malware attack, a BEC scam presents a different but equally dangerous cyberthreat. A BEC scam is a cyberthreat that uses email-based social engineering techniques to coerce victims into taking a desired action, often with financial implications.
BEC scams don’t impersonate brands like phishing emails, nor do they contain malicious links or attachments. They impersonate individuals known to the victim, use text-only threats, and often rely on research to carry out highly targeted attacks.
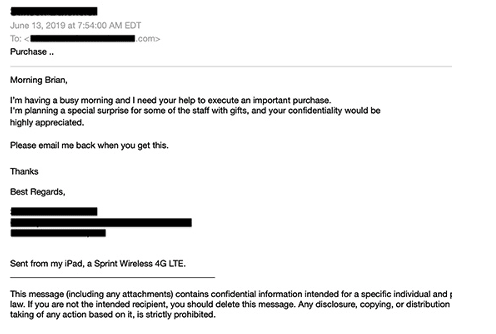
Example of spear-phishing email
Several factors contribute to the cost and devastation of a BEC scam, including:
- 1. Detection. Because a BEC scam doesn’t contain malicious links or attachments, it’s more difficult for email security tools to filter.
- 2. Context. A BEC scam preys on the professional and social pressures inherent in the workplace, making victims more susceptible to exploitation. For example, employees often desire to outperform the expectations of their supervisors and peers. When presented with an urgent request from a superior, they may feel obligated to fulfill the request without questioning the nature of it. The fear of reprisal also limits the chances victims voice any concerns.
- 3. Legitimacy. A BEC scam also generally tends to appear more legitimate to victims than other email-borne threats. Hackers may achieve this through common spear-phishing techniques, which we review later in this article. Also, the absence of links or attachments may lure recipients into a false sense of security. And BEC scams often use compromised accounts, allowing hackers to weaponize legitimate email addresses and gain access to prior correspondence for contextual background on their targets.
BEC scam types
As mentioned previously, several types of BEC scams exist, each taking a different approach to exploiting an individual or organization, including:
- 1. Wire transfer fraud. Also known as CEO fraud, this form of BEC scam impersonates an executive and requests that the victim wire money to a fraudulent account. The hacker may ask the victim to pay a vendor or make a significant purchase.
- 2. Gift card requests. In this attack, hackers impersonate an executive or high-level manager and request the victim to purchase gift cards for the email sender.
- 3. Direct deposit fraud. This attack targets HR employees and aims to divert employee paychecks to a fraudulent account controlled by hackers.
- 4. Tax fraud. Also known as W-2 fraud, the attack also targets HR professionals and requests employee tax forms. Hackers commonly impersonate executives or high-level managers in this scheme.
BEC scam techniques
While several forms of BEC scams exist, all rely on a proven set of techniques to socially engineer an exploitation, including:
- 1. Pretexting. The practice of sending a seemingly innocuous email to lower victims’ guard and gain their trust. Hackers often ask an open-ended question to elicit a response from victims. Once a victim replies, the hacker’s email address becomes whitelisted (assuming it’s spoofed and originating from outside the organization’s network). The technique seeks to establish rapport with the victim, which hackers can later leverage for exploitation.
- 2. Making urgent requests. Hackers create the illusion they have limited time for victims to fulfill their request, such as minutes or hours. This puts additional pressure on victims and may cause them to act hastily without adequately evaluating the request.
- 3. Sending mobile messages. Hackers give the appearance of sending an email from a mobile device, which legitimizes the spelling and grammatical mistakes typically made by foreign threat actors, while reinforcing the urgent nature of the request. To achieve this technique, hackers may claim to be traveling or include mobile signatures in their email, such as “Sent from my iPhone.”
Preventing a BEC scam

As we covered previously, a BEC scam is difficult to detect. Traditional email security solutions often fall short of defending against BEC attacks for three reasons.
- 1. Dynamic and unknown threats. Solutions like secure email gateways (SEGs) rely on reputation- and signature-based scanners for detection. This makes them entirely dependent on historical information and incapable of identifying threats not yet seen in the wild.
- 2. Text-only threats. Traditional email security solutions lack the ability to identify the subtle abusive patterns of a BEC scam, including flag words and phrasing that creates a sense of urgency.
- 3. Internal protection. By design, SEGs sit outside the organization’s internal environment, leaving it exposed to attacks that bypass initial detection or originate from internal accounts.
To protect against a BEC scam, organizations should adopt the following prevention measures.
1. Validate urgent requests through alternative methods
When receiving a suspicious email, such as an urgent request for a wire transfer, victims should contact the sender by alternative means to verify the email’s legitimacy. A phone call or text message can quickly reveal a fraudulent email, saving your organization, clients, or partners from a significant financial loss. While this prevention measure isn’t fail-proof, it provides a layer of protection and should be institutionalized in your policies and practices.
2. User awareness training
As with all cyberthreats, the greatest weakness in your organization’s attack surface is users. They’re also the last line of defense when it comes to stopping a BEC scam. That’s why you should invest in user awareness training that empowers them to spot and respond to BEC attacks in real-time.
Several types of user awareness training programs exist. For the best learning outcomes, you should look beyond generic simulations or classroom-based training offered at predetermined intervals. While these are among the most common education programs, they’re remotely connected to the experience of encountering an actual cyberthreat—in terms of content, context, and timing.
Instead, consider training that is personalized to reflect the content and context of each user’s regular email interactions and automatically self-administers whenever they encounter a real threat. This training reaches users at the time and in the format most conducive for learning, increasing the likelihood they adopt better cybersecurity behaviors and practices.
For example, Vade’s Threat Coach™ delivers on-the-fly education to users automatically when they open an email-borne threat, with learning that mimics their daily email experiences.
3. AI-threat detection and response technology
Organizations need email security solutions that offer predictive defense against a BEC scam and can detect the techniques used by hackers. That calls for technology that goes beyond the capabilities of basic email security tools that rely on reputation- and signature-based filters. Threat detection and response technology that leverages Artificial Intelligence (AI) provides organizations with the forward-looking and superior solution they need.
AI-threat detection and response solutions combine a core set of AI technologies and features to prevent exploitation from a BEC scam, including:
- 1. Machine Learning. Machine Learning (ML) algorithms analyze the context and content of emails to identify abusive patterns in text. ML also builds an anonymous profile that establishes a baseline for normal communication patterns among employees. It uses this baseline to identify anomalies including spoofing techniques and variations in email traffic.
- 2. Natural Language Processing. Natural Language Processing models detect subtle grammatical and stylistic choices in text to identify potential threats, including flag words and phrasing that creates a sense of urgency.
- 3. Feedback loop. A large, current, and relevant dataset of threat intelligence continually feeds the AI technologies to enhance the precision and accuracy of their algorithms.
- 4. API architecture. AI-threat detection and response technology sits within the internal environment and integrates with native applications, providing protection against internal threats and insider attacks.
AI has become one of the most promising fields across all industries. When it comes to cybersecurity, it has also become a buzzword used to market products, regardless of their true capabilities. To ensure your organization adopts a true AI-powered cybersecurity solution, look for products that possess the previous features and capabilities.
For example, Vade for M365 leverages Machine Learning, Natural Language Processing, and Computer Vision to detect and respond to all email-borne threats, known or unknown. The API-based solution also continually uses real-time threat intelligence from more than 1.4 billion mailboxes globally to enhance the precision and accuracy of its detection and response capabilities.
Don’t fall victim to BEC scams
As a financially driven exploit, a BEC scam is among the costliest cyberthreats against organizations. Each year, a shocking number of businesses fall victim to this highly targeted and deceptive threat. But while the abundance of victims highlights the unfortunate reality of BEC schemes, your organization can avoid joining the alarming total. By adopting the prevention measures explored in this article, you can keep your organization, employees, clients, and partners protected.




